Risky Biz News: US government agencies lag on logging compliance
In other news: Windows 10 gets three years of paid security updates; Andariel steals South Korea's laser weapons secrets; and there are still 23,000 backdoored Cisco IOS XE devices online.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Risky Biz News newsletter and podcast will be going on hiatus between December 8 and January 8 for our yearly winter holiday.
An audit of 23 of the largest US federal agencies found that most have failed to implement proper event logging and may be unprepared to respond to cybersecurity incidents, especially during the investigation and remediation phase.
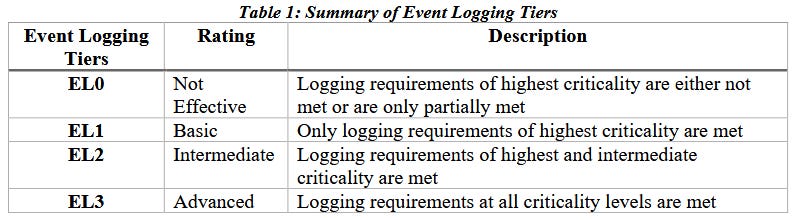
Conducted by the US Government and Accountability Office, the report found that 20 of the 23 agencies did not meet a White House executive order mandating they reached a logging level of EL3 by August 2023.
GAO says that only three agencies reached the proper requirement, while 17 were still at EL0 and had not made any headway toward compliance.
The White House signed Executive Order 14028 [PDF] in May 2021 in the aftermath of Russia's attacks on SolarWinds servers and China's zero-day exploitation of Microsoft Exchange servers.
Investigations into both hacks and their impact on US government systems were seriously hindered by the lack of proper event logs, which made figuring out the original attacks a game of putting a puzzle together with pieces from multiple sources.
EO14028 mandated that US federal agencies improve their cybersecurity posture by deploying EDR (endpoint detection and response) tools across their networks, removing barriers from sharing threat intel, scanning for vulnerabilities, and improving investigation and remediation capabilities by supporting proper logging of network events.
GAO says that while the 23 agencies made serious headway toward deploying EDRs and vulnerability scanning frameworks, they have completely missed the mark on improving their logging capabilities.
The 23 agencies cited a lack of staff and technical challenges that come with proper logging. Below, we're quoting the GAO report on some of the reported technical challenges (emboldened text added by us).
"Specifically, 12 agencies stated that gaps in technology or complexities with existing technical environments (e.g., legacy systems) proved challenging in meeting the requirements.
In addition, 17 agencies cited the need for increased storage capacity to meet event logging requirements. For example, to meet event logging levels, some agencies may need to increase storage capacity for logs. This may be due to a need to capture more granular level details or to capture data on events that were not previously required or captured. One agency official stated that his agency currently collects over 7 terabytes of log data per day with a retention of 1 year. The official stated that in order to be compliant with current logging data requirements, the agency would need to expand logging to 70 terabytes per day. Another agency official stated that his agency already collects over 13 billion logs daily, accounting for almost 15 terabytes of data per day."
In addition, the GAO report also covers the woes some federal agencies have gone through when it came to improved intelligence sharing.
Agencies reported that many feeds either contained old information, overlapped with each other, or included classified information that they couldn't use in some of their unclassified networks.
The GAO report concludes that while federal agencies are now in a better position to spot attacks, the lack of proper logging is still limiting their incident response and investigation capabilities—which, not coincidentally, was also the reason why some US government agencies didn't spot when they got hacked by Chinese hackers earlier this year during the "Storm-0558" hacks. Those compromises, which abused Microsoft infrastructure, eventually led Microsoft to provide more free logs to their cloud customers, showing the importance of logs in modern-day hyper-connected networks.
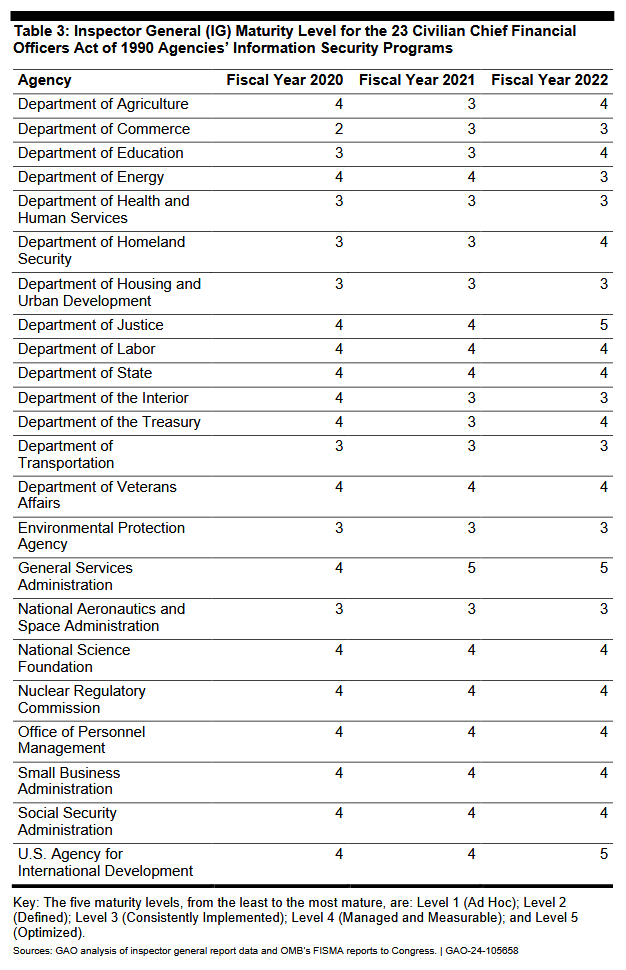
The 23 US federal agencies audited by GAO are listed below.
Breaches, hacks, and security incidents
Andariel hacks: The South Korean government says that North Korean hacking group Andariel has breached and stolen sensitive information from some of its defense firms. Officials believe the hackers successfully stole information on the country's laser-based air defense weapons. South Korean police say the intrusions were part of a larger campaign that also hit local universities, research centers, and financial institutions. The group successfully compromised 14 organizations and also engaged in ransomware attacks. Officials say they seized and recovered $360,000 Andariel operators collected through ransoms. [Additional coverage in Yonhap News and Boa News/English coverage in Korea Times]
UK denies nuclear site hack: The UK government has denied a report that Chinese and Russian hackers breached the Sellafield nuclear site. Government officials say they rebutted the rumors before publication, but the Guardian published its report regardless.
PALIG joins MOVEit list: Pan-American Life Insurance Group (PALIG) has joined the list of companies impacted by the MOVEit attacks. More than 2,600 companies across the world have been impacted by the MOVEit hacks, and the data of 77 million users was stolen in the intrusions.
RailYatri hack: The data of more than 23 million users of the RailYatri travel agency has been leaked online and indexed by HIBP. The Indian state-owned company was hacked in December 2022.
23AndMe breach: It appears that 23AndMe's legal team likes to play with their words. After downplaying their security breach and claiming that hackers accessed the data of 0.1% of its users, it turns out hackers accessed data on 6.9 million, representing almost half of the site's estimated 14 million total users. [Additional coverage in TechCrunch]
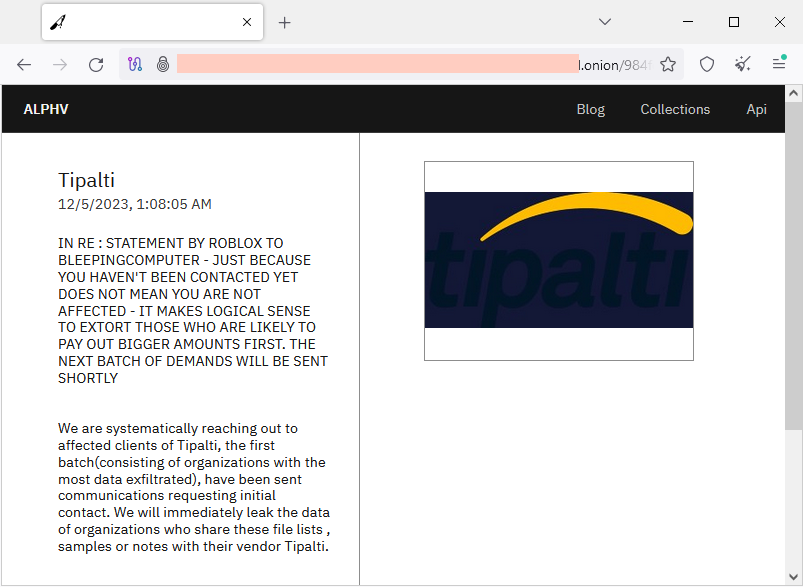
Tipalti ransomware attack: Payments software vendor Tipalti has confirmed it got hit by a ransomware attack after the AlphV group listed the company on its dark web leak site. The incident is unique because AlphV showed its intention to use the Tipalti data to extort some of its customers. The gang hinted at possible extortions of Roblox and Twitch, two of Tipalti's largest customers. [Additional coverage in The Record]

General tech and privacy
Windows 10 ESU: Microsoft will offer three years of paid security updates for Windows 10 users after the operating system reaches its official end-of-support (EOS) date on October 14, 2025. Known as ESU (Extended Security Updates), this is the same type of paid extended support that Microsoft previously made available for Windows 7 users. This is Microsoft's third major ESU program after it announced a similar paid support scheme for Windows Server 2012/R2 users last month.
Zuckerberg buys Harvard's silence: Harvard University muzzled and then gutted a team of academics studying Facebook disinformation campaigns after Meta CEO Mark Zuckerberg donated $500 million to the university. The team was working on the Facebook Files, a collection of internal Meta documents leaked by whistleblower Frances Haugen.
Wikipedia toxicity: An academic paper has found that the rising number of toxic comments posted on Wikipedia is tied to the site's losing some of its volunteers.
Elcomsoft-MKO lawsuit: Thomas Brewster looks at the lawsuit between Elcomsoft and MKO-Systems, two Russian companies specializing in iOS digital forensics services. The lawsuit hints at a possible iOS 16 zero-day used by Elcomsoft products, which Elcomsoft claims has been stolen by MKO. [Additional coverage in Forbes/non-paywall]
Government, politics, and policy
Pegasus case in Mexico: Mexico's former president, Enrique Peña Nieto, has allegedly ordered a spying operation against the country's two largest business figures, investor Carlos Slim and mining mogul Germán Larrea. The spying operation involved the NSO Group's Pegasus spyware, according to the testimony of a whistleblower in a trial that started in Mexico this week. Prosecutors believe the spyware was used to spy on thousands of victims across the private sector and government administrations. [Additional coverage in Expreso/ English coverage in ElPais]
"The information provided by Zeus [the whistleblower] indicated that the espionage campaign had been carried out by a subsidiary of one of the suppliers of Pegasus in Mexico, the KBH business group."
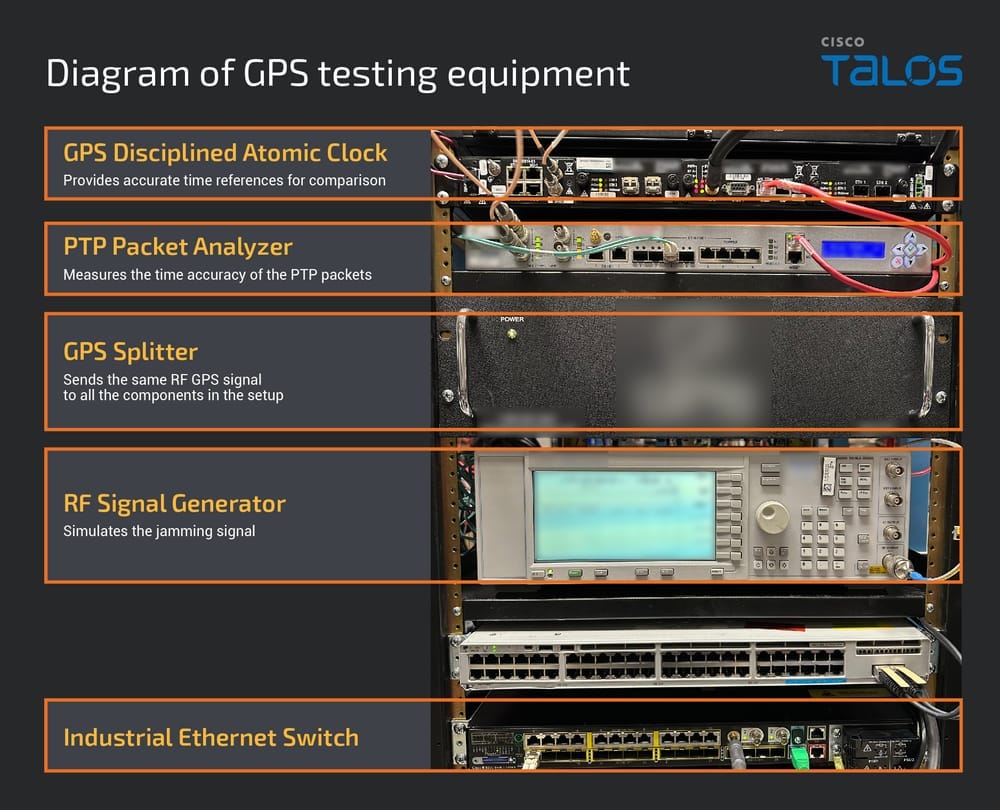
Project PowerUp: Cisco Talos explains how the company helped Ukrainian authorities develop new equipment that can resist Russia's GPS jamming attacks and keep the country's power grid online in the face of mounting Russian electronic warfare.
Risky Business Podcasts
In this podcast, Patrick Grey and Tom Uren talk about how threat actors abusing legitimate tools (aka living off the land or LOLbins) is the new normal. Everyone is doing it, from activists to cybercriminals to nation-states. It's a worry because the defender's standard practices really aren't set up to detect and deal with that kind of behavior.
Cybercrime and threat intel
Raccoon dev extradition case: A judge has ruled that the Dutch government can extradite a Ukrainian national to the US to face charges for developing the Raccoon infostealer. Named Mark Sokolovsky, the suspect has been fighting his extradition since October of last year. His case revolved around claims that US authorities would treat him inhumanely and violate his human rights, accusations the judge found implausible. Sokolovsky was detained in early 2022, and his sudden disappearance following his arrest led to a hilarious situation where fellow malware developers thought he died in Ukraine following Russia's invasion.
Money mule arrests: Europol, Interpol, and law enforcement agencies from 26 countries have arrested 1,103 money mules in one of the largest crackdowns against money laundering operations. Officials say they also identified almost 11,000 money mules and their recruiters. More than 2,800 banks and financial institutions helped law enforcement in tracking down money mules and their networks.

Spyro1d: A new Android RAT named Spyro1d is being sold online somewhere. There were some rumors that it already got leaked on GitHub, but I could not find it. Instead, I found this new Windows infostealer named Laze.
Iranian hacktivism: Check Point says that Iranian hacktivist groups are expanding their activity beyond Israel to target international targets in the context of the Israel-Hamas war. The four are Cyber Av3ngers, Haghjoyan, Cyber Toufan, and the YareGomnam Team.
Zarya attacks: SANS ISC researchers have spotted the Zarya pro-Kremlin hacktivist group hunting for unpatched Microsoft Sharepoint servers.
Backdoored Cisco IOS XE devices: Almost two months after the attacks were disclosed, there are more than 23,000 Cisco IOS XE devices that are still infected with a backdoor named BadCandy. The number of infected devices is down by just 46%, despite calls from several national CERT and cybersecurity teams to patch devices and remove the backdoor. The devices were infected at the end of September after a yet-to-be-identified threat actor used a combination of two zero-days (CVE-2023-20273 and CVE-2023-20198) in Cisco's IOS XE operating system.
Malware technical reports
macOS proxy malware: Kaspersky researchers have spotted a proxy trojan targeting macOS users disguised in cracked macOS software.
P2PInfect: Cado Security has spotted a new version of the P2PInfect botnet targeting MIPS-based devices.
BlueSky ransomware: The DFIR Report team looks at attacks with the BlueSky ransomware, deployed on networks following brute-force attacks on MSSQL databases.
DanaBot: OALABS researchers have published IOCs and TTPs for the DanaBot malware.
SpyLoan: ESET looks at a class of Android spyware apps it calls SpyLoan that disguise themselves as loan apps. The apps were downloaded more than 12 million times and generally targeted users in Southeast Asia, Africa, and Latin America.
Sponsor Section
In this product demo, Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray.
APTs, cyber-espionage, and info-ops
Bluenoroff's RustBucket: Kaspersky researchers have looked at a macOS malware loader named RustBucket that has been used by North Korean hacking group Bluenoroff in its recent operations. See similar reports from Elastic, Sekoia, Jamf, and SentinelOne.
Doppelgänger: Recorded Future has spotted new info-op activity from Russian group Doppelgänger. The recent campaign targeted audiences in Ukraine, Germany, and the US using AI-generated content on fake news sites and social media accounts.
APT28 Outlook/Exchange attacks: Russian hacking group APT28 has continued to relentlessly exploit a former Outlook zero-day (CVE-2023-23397) throughout the year, even after Microsoft rolled out patches for the bug in March. APT28 used the zero-day to steal NTLM passwords from unpatched systems and then pivot to internal networks from one single compromised host. Besides the Outlook zero-day, the group also used password spraying attacks to gain access to Exchange email servers and steal inbox content. According to reports from Microsoft, Proofpoint, and Poland's Cyber Command, the campaign targeted a wide range of organizations across Europe and North America and didn't appear to have lost any steam after Microsoft rolled out patches. The APT28 group has been linked to Russia's GRU military intelligence service.
Vulnerabilities, security research, and bug bounty
Android security updates: The monthly security updates for Android smartphones are out. The December update includes fixes for three zero-days Qualcomm reported under attack in October. Qualcomm also released details and patches for the three—tracked as CVE-2023-33106, CVE-2023-33107, and CVE-2023-33063.
Apache CouchDB security update: The Apache CouchDB team issued a rare security update, recommending that all users patch immediately.
Cisco vulnerability: Cisco has patched a Firepower VPN bug that was leaked online. No exploitation has been seen in the wild yet.
PsFree: A developer named CelesteBlue has published PsFree, a WebKit-based exploit for rooting PlayStation 4 and 5 systems.
Outlook attack vectors: Check Point researcher Haifei Li analyzes the attack surface of Microsoft Outlook.
Fake Lockdown Mode: Jamf researchers have developed a technique that can be used to fool users into thinking they enabled Lockdown Mode on their iPhones.
MTG Arena bug: SpecterOps researcher Daniel Mayer has found a bug in the Magic: The Gathering Arena game that could be abused to force opponents to concede games.
Train PLC research: A German security researcher named Q3k has found hidden code inside the Newag smart trains that would show bogus errors and lock up the train when it was serviced at third-party workshops.
Thirdweb vulnerability: Web3 software vendor Thirdweb has asked developers to take steps to mitigate a vulnerability the company found in its smart contract SDK. Thirdweb says the vulnerability impacts more than 20 popular smart contracts. Any company that deployed a smart contract with the Thirdweb SDK before November 22 is considered vulnerable and exposed to crypto-asset thefts. The company says it has not observed any exploitation of the bug prior to its disclosure.
MW WP Form vulnerability: Wordfence researchers have found an unauthenticated file upload vulnerability in the MW WP Form plugin that can lead to arbitrary code execution. Tracked as CVE-2023-6316, the vulnerability has a severity rating of 9.8/10. The plugin is currently installed on more than 200,000 WordPress sites, making it ideal for mass exploitation.
ColdFusion exploitation: A threat actor is exploiting an Adobe ColdFusion vulnerability patched in March to gain access to US government systems. CISA says the attackers have compromised and backdoored two servers in operations in June and July. The ColdFusion vulnerability was a zero-day (CVE-2023-26360) when it was patched in March, but it's unclear if this is the same original attacker.
SLAM: VUSec researchers have published details on SLAM, a new Spectre-like side-channel attack on Intel, AMD, and Arm CPUs.
EXOS vulnerabilities: Rhino Security has found and helped patch four vulnerabilities in EXOS, the operating system running on ExtremeNetworks switches.
"At the time of these findings, there were over 1000 devices exposed to the internet running the vulnerable EXOS versions, determined using a Shodan search."
ownCloud vulnerabilities: French security firm Ambionics looks at the technical details behind two recent ownCloud vulnerabilities that are being exploited in the wild.
Hugging Face token leaks: Lasso Security has found more than 1,600 API tokens for the Hugging Face AI development service exposed on the internet via GitHub repositories. The tokens allow attackers to access ML and AI-based tools developed using the Hugging Face service. Lasso says that some of the tokens belonged to large companies such as Microsoft, Meta, Google, and VMware.
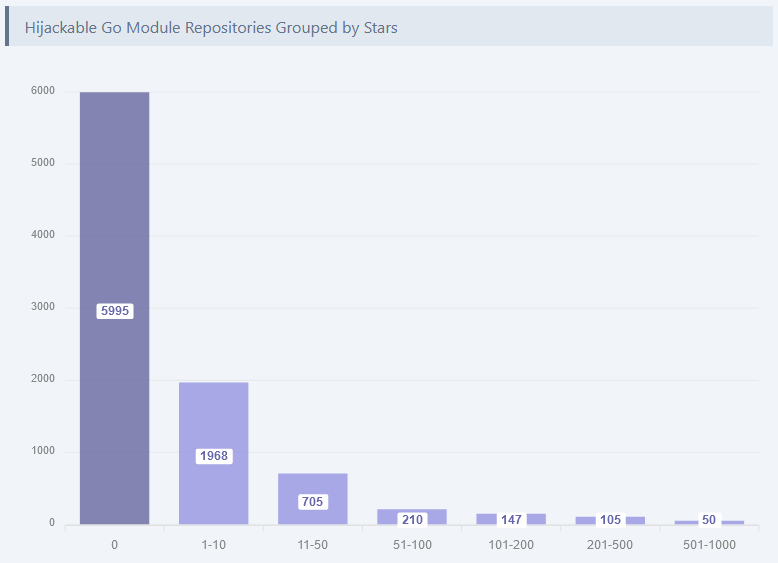
Go repojacking: More than 15,000 Go libraries are managed through GitHub accounts that are vulnerable to repojacking attacks. According to security firm VulnCheck, more than 9,000 repositories are vulnerable to repojacking due to GitHub username changes, while another 6,000 are vulnerable to repojacking due to the original owner's account deletion. VulnCheck says that the 15,000 GitHub repos support more than 800,000 versions of Go modules, including some popular ones.
"Unfortunately, mitigating all of these repojackings is something that either Go or GitHub will have to take on. A third-party can’t reasonably register 15,000 GitHub accounts. Until then, it’s important for Go developers to be aware of the modules they use, and the state of the repository that the modules originated from."
Infosec industry
HIBP reaches 10 years: The Have I Been Pwned database is celebrating its 10th anniversary. Pwnage count is 731 databases and 12.8 billion accounts.
Acquisition news: Cloud security firm Wiz has acquired Raftt, a startup that provides easy-to-use developer-centric Kubernetes environments.
New tool—ADOKit: IBM's X-Force team has open-sourced ADOKit, a toolkit that can be used to attack Azure DevOps Services by taking advantage of the available REST API. A whitepaper is also available [PDF].
New tool—FARA: Security researcher Bart Blaze has released FARA, a repo with purposefully erroneous Yara rules, meant as a training vehicle for new security professionals.
New tool—Sonicwall-NSV-Decrypter: Security firm Praetorian has released a tool named Sonicwall-NSV-Decrypter that can be used to jailbreak Sonicwall NSv virtual firewall appliances and decrypt LUKS partitions.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about recent hints that the Ukrainian government has figured out how to make use of the IT Army.




