Risky Biz News: Raccoon Stealer dev didn't die in Ukrainian war; he was arrested in the Netherlands
In other news: Sigstore reaches GA; PayPal deploys passkeys; "freejacking" is now a thing.

This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Back in March, the administrator of the Raccoon Infostealer malware announced they were shutting down their service after "a friend and a great developer" who was responsible for maintaining critical parts of their infrastructure had been "lost" following Russia's invasion of Ukraine, a month earlier.
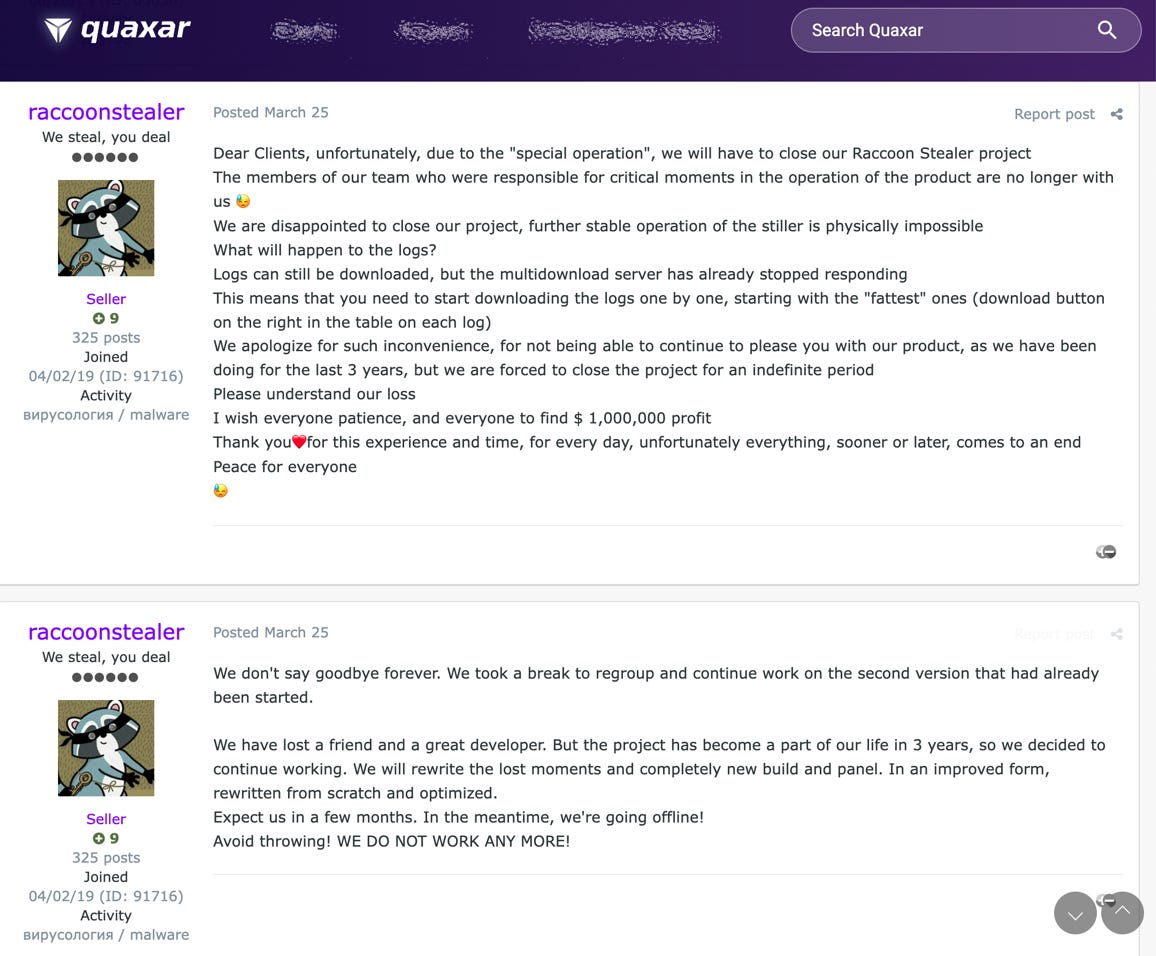
But—surprise, surprise—it turns out that the developer didn't die in the war, and he stopped responding to his co-workers because he was arrested in the Netherlands at the request of the FBI.
All of this came to light yesterday when the US Department of Justice unsealed charges against Mark Sokolovsky, 26, a Ukrainian national, for his role in maintaining the Raccoon Infostealer (also known as Raccoon Stealer) malware-as-a-service (MaaS).
The DOJ said that together with Dutch and Italian authorities, the FBI also seized servers operated by the Raccoon gang, effectively taking offline that older version of the Raccoon operation.
The Raccoon gang made a comeback three months later, in June, with version 2.0, most likely after they found a replacement for their "departed" colleague.
DOJ officials said the FBI found approximately 50 million unique user credentials stored on the seized Raccoon Infostealer servers, representing credentials stolen from the browsers of users infected by the Raccoon gang and their MaaS customers.
Authorities said they don't believe they have the entire list of stolen credentials pilfered by the Raccoon operation, but they are making the entire data set searchable via a dedicated website, so users and companies can see if any of them got infected by the malware in the past and proceed to change credentials.
Breaches and hacks
L2DAO crypto-heist: Ethereum investment project L2DAO confirmed on Monday that a hacker drained 49,950,000 L2DAO tokens from its project, worth around $234,000, at the time of the incident. The company said the hacker dumped the funds, but they were able to repurchase 31,239,677 L2DAO tokens ($146,000) with its own treasury.
Binance hack investigation: Binance CEO Changpeng Zhao said the company is narrowing down the identity of the hacker behind the recent $570 million hack of its BNB Chain platform earlier this month.
E-Pal breach: E-Pal, a web service dedicated to helping gamers find free or pro teammates for their favorite games, has disclosed a security breach that took place earlier this month. The company's data, leaked online, was also added to HIBP.
ePal, a website dedicated to finding friends on Discord, was breached by individuals on Breached Forums. The individuals behind the breach exfiltrated data and defaced the website.
— vx-underground (@vxunderground) 1:22 PM ∙ Oct 1, 2022
It appears they are unhappy with the research conducted by some individuals in Threat Intelligence
General tech and privacy
First FTC ruling of its kind: The US Federal Trade Commission reached a settlement with online alcohol delivery service Drizly relating to its 2020 security breach that exposed the personal data of more than 2.5 million of its users. The settlement requires that the company, which has since been acquired by Uber, destroy unnecessary data it collected about its users and further restricts Drizly from similar broad data collection in the future. In addition, the settlement is the first of its kind, as it also includes a clause against Drizly CEO James Cory Rellas. [More extensive coverage in The Record]
"Notably, the order applies personally to Rellas, who presided over Drizly's lax data security practices as CEO. [...] Specifically, Rellas will be required to implement an information security program at future companies if he moves to a business collecting consumer information from more than 25,000 individuals, and where he is a majority owner, CEO, or senior officer with information security responsibilities."
Interserve fine: The UK Information Commissioner Officer levied a massive £4.4 million ($5 million) fine against Interserve, a Berkshire-based construction company, for failing to update software and train staff, which eventually led to a ransomware attack during which the data of its employees was stolen by cybercriminals.
Sigstore reaches GA: Sigstore, a system for cryptographically signing software releases to protect users against supply chain attacks, has reached general availability. More from GitHub and Chainguard.
"To date over 4 million signatures have been logged using Sigstore and two of the world's largest open source communities, Kubernetes and Python, have adopted Sigstore's wax seal of authenticity by signing their production releases with Sigstore. Most recently, npm announced they are actively working to integrate Sigstore, so all npm packages can be reliably linked to their source code and build instructions."
PayPal to support passkeys: After announcements from all major browser vendors, PayPal said it would also add support for passkeys as a way to log into its service.
"The new PayPal log in option will first be available to iPhone, iPad, or Mac users on PayPal.com and will expand to additional platforms as those platforms add support for passkeys."
Chrome EOL on Win7/8.1: Google announced this week plans to end support for its Chrome browser on Windows 7 and Windows 8.1 next year, on January 10, 2023.
"With the release of Chrome 110 (tentatively scheduled for February 7, 2023), we'll officially end support for Windows 7 and Windows 8.1. You'll need to ensure your device is running Windows 10 or later to continue receiving future Chrome releases."
Government, politics, and policy
More cybersecurity coordination needed for K-12 sector: A report from the US Government Accountability Office (GAO) found that while there are three federal agencies that assist K-12 schools in protecting against cyber threats, there are no formal channels for how agencies coordinate with each other or with K-12 schools to address cybersecurity risks or incidents; hence more coordination is needed between all players to improve the K-12 cybersecurity stance across the board.
Ransomware in Singapore: The Singapore government convened an inter-agency Counter Ransomware Task Force (CRTF) to develop and make recommendations on possible policies, operational plans, and capabilities to improve Singapore's counter-ransomware efforts.
Sponsor section
RunZero (formerly Rumble Network Discovery) is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Dutch hacker arrested: Dutch police detained a 19-year-old from the town of Krimpen aan den IJssel for hacking into the network of a healthcare software supplier and stealing files containing user data. Authorities said they are still investigating to see if the teen had resold any of the data. While authorities did not name the victim of this incident, Dutch healthcare provider Nedap disclosed a security breach of its Carenzorgt.nl portal on the same day as the Dutch police announcement.
Alfa-Bank ATMs defrauded: A Russian criminal group stole roughly 60 million rubles ($975,000) from the ATMs of Russian bank Alfa-Bank by abusing a glaring design flaw that allowed them to insert counterfeit cash into the ATMs and later withdraw legitimate currency.
KEV update: CISA has updated its KEV database with six vulnerabilities that are currently being actively exploited in the wild. The list includes two Cisco vulnerabilities from 2020 and four GIGABYTE vulnerabilities from 2018.
More KakaoTalk phishing: This is an analysis of a threat actor campaign that used the lure of a major fire at one of KakaoTalk's data centers to distribute malware to users impacted by the downtime.
DEV-0832: Microsoft published a report on a threat actor it tracks as DEV-0832, a group that began by distributing versions of the BlackCat, QuantumLocker, and Zeppelin ransomware strains but is now managing the Vice Society operation. The group has gotten a lot of media attention lately due to its sustained campaign targeting the education sector.
PurpleUrchin freejacking campaign: Researchers from cloud security firm Sysdig published details on PurpleUrchin, a threat actor that registers free or trial accounts on CI/CD platforms to mine cryptocurrency using their servers. Abused services include GitHub, Heroku, Buddyworks, BitBucket, CircleCI, Semaphore, and others. The company called this technique "freejacking."
Carding op leaks data: Group-IB researchers said they identified a misconfigured server that was hosting the control panels for two point-of-sale malware strains named MajikPOS and Treasure Hunter. According to the researchers, the two panels were holding details for 167,000 payment cards—worth on the carding underground an estimated $3.34 million.
Abuse of legitimate RATs: Synacktiv researchers have published in-depth research on how threat actors are abusing legitimate remote access tools in their attacks. The research covers apps like Teamviewer, AnyDesk, Atera, and Splashtop.
Increased CLDAP exposure: Lumen's Black Lotus Lab warned this week that they've observed that the number of CLDAP servers exposed on the internet has increased by 60% to more than 12K distinct IPs over the last 12 months. More worrisome is that some CLDAP servers have been seen being abused in DDoS attacks, with one single instance reflecting and amplifying traffic for the attackers of up to 17 Gbps.
We’ve seen one CLDAP reflector emit 17 Gbps 👀 Are they all this strong? If so, just 10% of them could generate a full 1+ Tbps attack
— Black Lotus Labs (@BlackLotusLabs) 12:14 PM ∙ Oct 25, 2022
Malware technical reports
Magniber ransomware: Magniber—the ransomware strain that is exclusively targeting South Korean users—has continued its evolution, with new updates being spotted by AhnLab, after similarly observed updates over the past month [1, 2, 3].
LV ransomware: Trend Micro has a report out on an attack carried out with the ProxyShell vulnerability to deploy a version of the LV ransomware on the network of a Jordanian company.
APTs and cyber-espionage
Kimsuky's Android arsenal: South Korean cybersecurity firm S2W Talon published a report on FastFire, FastViewer, and FastSpy, three Android malware strains they linked to Kimsuky, one of North Korean state-sponsored hacking groups.
APT activity targeting EU bodies: CERT-EU, the EU agency that provides incident response to official EU agencies, said that almost two-thirds (63%) of the threat alerts it sent in Q3 2022 were related to cyber-espionage activity. The agency said of the 11 "top threat actors" they are tracking, they detected direct attacks against EU bodies from three groups—but no successful breach. The full report is here [PDF].
Vulnerabilities and bug bounty
Microsoft SharePoint vulnerability: Singapore-based security firm StarLabs disclosed on Tuesday a vulnerability in Microsoft SharePoint Server 2019. Described as a post-auth SSRF, Microsoft fixed the issue but refused to assign a CVE identifier for StarLabs' finding/work.
@GossiTheDog A Microsoft "CVE" is a "Security update with associated MSRC write-up".
— Will Dormann (@wdormann) 10:59 AM ∙ Oct 25, 2022
Using this definition, as opposed to how the rest of the world uses CVE, is what allows them to say "this isn't worth a CVE" and mean it.
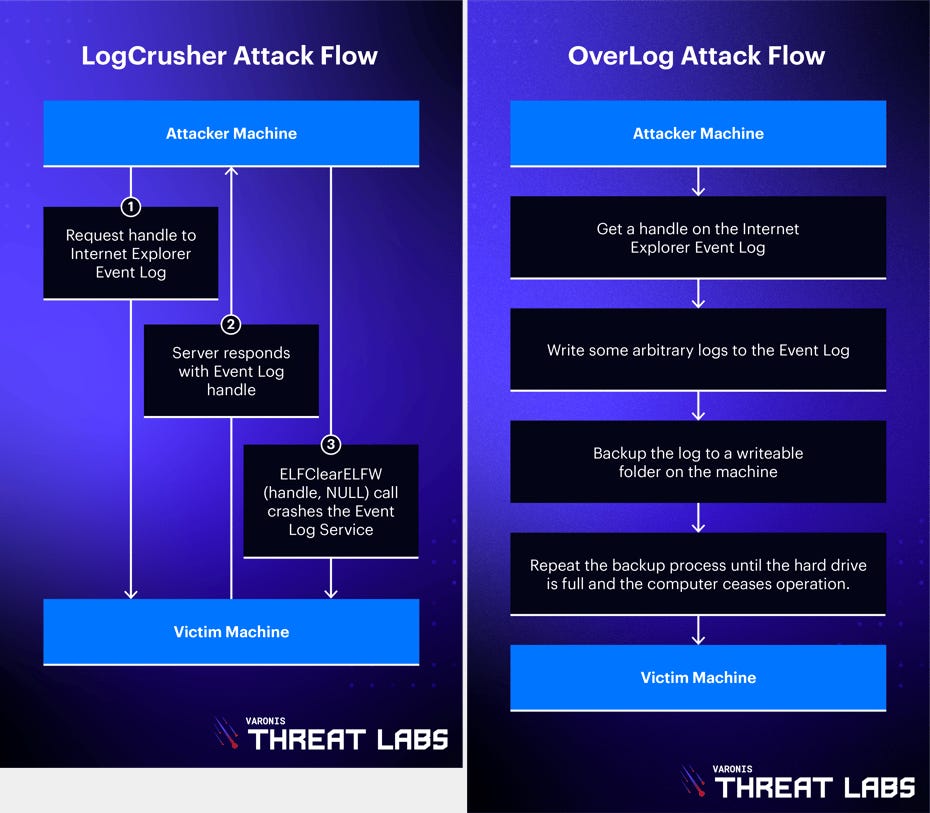
LogCrusher and OverLog: Varonis researchers published details on LogCrusher and OverLog, two Internet Explorer vulnerabilities.
- LogCrusher, which allowed any domain user to remotely crash the Event Log application of any Windows machine on the domain.
- OverLog, which causes a remote denial-of-service (DoS) attack by filling the hard drive space of any Windows machine on the domain. (CVE-2022-37981)
Varonis said that even if Microsoft retired IE this June, the two vulnerabilities still impact user systems because IE components are still present in core Windows apps.
Apple security updates: Apple released security updates for its products on Monday, including iOS 16.1, which includes a fix for CVE-2022-42827, a vulnerability that Apple described as being exploited in the wild. The issue impacts the iOS kernel, and it is unclear if this has been used to jailbreak smartphones or actively exploited by a threat actor to deploy malware.
Aukey router zero-day: Code White security researcher @esj4y has published a proof-of-concept exploit for an RCE vulnerability in Aukey router model WR-R01. The researcher said he published the exploit after the vendor failed to respond to his disclosure and because they don't seem to manufacture or sell the model anymore.
Was quite fun to go from buying router, desoldering chip, extracting firmware, static analysis to vuln and eventually exploit. Has some mem-corruptions too, maybe will find some time later to have a deeper look at them.
— esjay (@esj4y) 6:06 PM ∙ Oct 23, 2022
22yo SQLite vulnerability: Trail of Bits disclosed this week CVE-2022-35737, an arbitrary code execution vulnerability in the SQLite database engine. The vulnerability affects all SQLite versions released since October 2000.
Upcoming OpenSSL critical update: The OpenSSL project announced a major critical-rated security update for its library for next week, on November 1.
This will be OpenSSL's first "CRITICAL" vulnerability since 2016. Examples of "CRITICAL" vulnerabilities include "significant disclosure of the contents of server memory (potentially revealing user details), ...
— Andrew Ayer (@__agwa) 2:37 PM ∙ Oct 25, 2022
Infosec industry
Snyk layoffs: DevOps and cybersecurity unicorn Snyk is set to sack 198 employees, representing roughly 14% of its workforce.
VirusBulletin 2022 videos: Some of the recorded talks from the VirusBulletin 2022 security conference, which took place earlier this month, are available on YouTube.
Some nice tutorial: Crowdstrike's John Halon will be releasing a browser exploitation series on Google Chrome. Part one is already out.
Today I am finally releasing a new 3-part browser exploitation series on Chrome! This was written to help beginners break into the browser exploitation field.
— Jack Halon (@jack_halon) 11:05 PM ∙ Oct 22, 2022
Part 1 covers V8 internals such as objects, properties, and memory optimizations. Enjoy!
(ISC)² drama: Security certification body (ISC)² is being widely criticized by current and former members for passing organization-wide changes despite complaints from its members. According to The Daily Swig, the organization has changed its mission, has eliminated its Ethics Committee, and is readying to change the process for electing the board of directors to a process controlled by current members—in what former members have described as "a coup by governance."
Reading about the proposed change of bylaws @ISC2 & the open letter from @wimremes, as a previous member (CISSP, ISSAP) & SME for ISSAP, I can only say I am glad I chose to leave the organization.
— Per Thorsheim (@thorsheim) 8:02 PM ∙ Oct 23, 2022
If you don't listen to your members, even alienate them, you are doing it wrong.




