Risky Bulletin: US raids SIM farm in New York
In other news: EU airport disruptions caused by ransomware; thieves steal gold from French museum after cyberattack; SonicWall firmware update removes rootkit.

This newsletter is brought to you by SpecterOps, the experts in Attack Path Management. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
The US Secret Service has raided and dismantled a SIM farm operating at five locations across the New York tri-state area.
Officials seized 300 SIM servers running more than 100,000 SIM cards.

Officials began investigating the SIM farms after they were used earlier this year to make anonymous threats against senior US officials. According to the NYT, two White House and one Secret Service official were on the receiving end of some of those threats.
The Secret Service press release is very vague in one particular sentence, where they claim they found a nation-state involved. It's unclear to me if the nation-state was involved in setting up the SIM farm or if they were using it to hide communications inside the US, but I'm heavily leaning on the latter. An intelligence service won't set up a SIM farm this large if they didn't want to get spotted.
"While forensic examination of these devices is ongoing, early analysis indicates cellular communications between nation-state threat actors and individuals that are known to federal law enforcement."
The Secret Service says the SIM farm was one of the largest they've seen in the US and had the capacity to spam almost all US phone numbers in the US in a few minutes, and even crash the local telco network and sabotage communications in times of emergency.
The SIM farm also operated close to the UN headquarters and could have provided threat actors with an anonymous, encrypted comms channel for operations targeting UN officials.
Officials took down the SIM farm hours before the UN General Assembly held a meeting this week, where US President Donald Trump attended and gave a speech on Tuesday on "uncontrolled migration."
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Airport disruptions caused by ransomware: A ransomware attack is responsible for the huge disruptions at European airports over the weekend. The EU cybersecurity agency said it identified the type of ransomware, and law enforcement is investigating. The attack targeted Collins Aerospace, which manages self-check-in kiosks across hundreds of airports. The kiosks went down on Friday, and some airports were still canceling or delaying flights on Monday. Disruptions are expected throughout the rest of the week. [Additional coverage in the BBC]
French History Museum theft aided by hack: A group of thieves has stolen gold nuggets worth €600,000 from the French Natural History Museum. The thieves took advantage that the museum's alarms and camera surveillance were down because of a cyberattack weeks before. According to investigators, the thieves appear to have known about the hack and the lack of surveillance. [Additional coverage in Le Parisien] [h/t Zahid S.]
Jaguar Land Rover fallout extends into October: UK carmaker Jaguar Land Rover has extended its production pause until next week, October 1. The company stopped all production after a ransomware attack on September 2. The incident is expected to impact statistics for the entire British economy. Several of the company's suppliers have also warned they face possible bankruptcies. Jaguar has lost between £50m and £100m since the attack. [Additional coverage in CybersecurityDive]
Stellantis breach: Hackers have stolen the contact information of Stellantis customers. The data was stolen from a third-party service provider and only impacted the company's North American customers. Stellantis is the parent organization of some of today's largest car brands, such as Peugeot, Chrysler, Maserati, Citroen, Opel, Jeep, Alfa Romeo, and Fiat.
DCS security incident: The operator of a network of EV charging stations has notified customers of a security breach. Employees at a third-party customer service provider viewed customer data without valid reasons on multiple occasions. DCS also notified BMW and Kia EV owners. Both brands use DCS charging points for their charging networks.
MTA hacked: The Maryland public transport agency is investigating a breach of its internal IT network. The incident took place last week and did not impact any public transportation. It mainly impacted call centers used for on-demand mobility and paratransit services. [Additional coverage in Fox Baltimore]
Circle K hack upends Hong Kong operations: A cyberattack has disrupted almost 400 Circle K convenience stores across Hong Kong. Payment, email, and loyalty systems have been down since the weekend. Circle K stores remained open but only took payments via Hong Kong's custom Octopus payment cards. [Additional coverage in The Record]
South Korean asset management firms hacked: Hackers have stolen financial data from around 20 asset management companies in South Korea. The hack took place earlier this month. The data was stolen from the cloud account of a common IT contractor. The Qilin ransomware group took credit for the incident. [Additional coverage in the Korea Herald]
Sophos phishing incident: UK security firm Sophos says that one of its employees got phished in March, but the breach was limited and contained.
UXLINK crypto-heist: A hacker has breached the UXLINK crypto platform. The attacker stole almost $30 million worth of assets and minted trillions of the platform's custom coins. They then lost $48 million shortly after the hack, after they fell for a phishing attack. [Additional coverage CoinTelegraph and Coinfomania]
Seedify crypto-heist: Hackers have exploited and stolen $1.2 million worth of assets from the Seedify cryptocurrency platform. [Additional coverage in Crypto Briefing]
Cancel the Hate app leaks user data: An app for reporting and doxing individuals who spoke ill of Charlie Kirk has leaked its users' data. The Cancel the Hate app allegedly leaked email addresses and phone numbers. The app was taken offline last week after reporters reached out. [Additional coverage in Straight Arrow News]
"I never thought my personal info would be exposed" say members of the exposing people's personal info app
— Ailyn (@zybilna.bsky.social) 2025-09-22T19:06:24.797Z
General tech and privacy
GitHub to improve npm security: GitHub will require a FIDO-based two-factor authentication method to publish updates to npm packages. The new requirement is part of the company's overhaul of npm security after a major supply chain attack and self-propagating worm hit the npm repo last week. The company will also deprecate legacy long-lived npm tokens and roll out new ones that last only seven days.
AMO rollback feature: Mozilla has added a "rollback" feature to the Firefox extension portal to allow developers to quickly roll back their code to a previous version in the event of hacks or botched releases.
MAX userbase: MAX, Russia's newly anointed official national messenger, now has 32 million users, per Kommersant.
WhatsApp message translations: Meta has added a message translation feature so you can read all your spam messages in peace.
TikTok to retrain algorithm: TikTok's new ownership will retrain the app's algorithm based on US user data, and the recommendation system will be audited by tech giant Oracle. The US and Chinese governments reached an agreement on the sale of TikTok's US division last week, most likely to a group of censorship-happy pro-Trumpers. [Additional coverage in the BBC]
I'd start informing your friends and loved ones they're going to need to get off of TikTok it's indisputably going to be converted into yet another right wing surveillance and propaganda machine
— Karl Bode (@karlbode.com) 2025-09-22T14:17:50.654Z
the Trump Supreme Court has lobotomized any federal regulatory agency that might hold a MAGA owned TikTok accountable for privacy violations or anything else literally zero constraints on surveillance and pushing race-baiting propaganda
— Karl Bode (@karlbode.com) 2025-09-22T14:25:02.892Z
Government, politics, and policy
Russia prepares to amp up the persecution of its own citizens: Russian officials are floating the idea of creating a database of citizens who continue to visit and consume content from what the Russian government calls "foreign agents." These are foreign news outlets that don't parrot the government's falsehoods. The list would be accessible to police, and people on it would be branded "terrorists and extremists." [Additional coverage in News.ru] [h/t Y.R.]
Russia wants to minimize data collection: Russia's Ministry of Finance is working on regulations to force companies to restrict what type of data they collect from users, in the hopes of minimizing future leaks of sensitive data following hacks. The proposed rules are similar to legislation already active in the EU and China. [Additional coverage in RBC]
CISA 2015 renewal loses hope: Per CyberScoop, it looks like Congress will not reauthorize and extend the 2015 Cybersecurity Information Sharing Act in time, a law that lets the private sector share cyberattack data with the government without legal complications and consequences. CISA 2015 is set to expire at the end of the month. America is going cyber YOLO!
EU looking to reduce cookie popups: The European Union is looking to simplify its cookie consent popup law. The changes will aim to reduce the cases where consent must be obtained. The law was passed in 2009 and filled the internet with stupid popups, even in countries where it didn't apply. [Additional coverage in Euractiv]
Romania warns of crippling Russian cyber-attack: Romania's national bank governor warned against the transition to a digital euro without a cash alternative or proper cybersecurity defenses. Mugur Isărescu says that a Russian cyber-attack could block all payments in the country within three days. [Additional coverage in HotNews]
Poland threatens hack-back operations: Poland has threatened to hack back any country that cripples its critical infrastructure. Minister of Digital Affairs Krzysztof Gawkowski says the country has the possibilities to respond. Gawkowski said this while responding to questions about the recent attacks that crippled airports across the EU and an attack that tried to shut down water supply to a Polish city. Poland joins Romania in non-typical cyber actors to threaten hack-back operations. [Additional coverage in Portal Samorzadowy] [h/t Lukasz Olejnik]
Sponsor section
In this Risky Business sponsor interview, Catalin Cimpanu talks with Jared Atkinson, CTO at SpecterOps. They discuss how SpecterOps is using classifying identities under two categories, identities at rest and identities in transit, what they are, and how they should be treated differently.
Arrests, cybercrime, and threat intel
Crypto-fraud gang dismantled: EU authorities have dismantled a crypto-fraud ring operating out of Spain and Portugal. The group has been operating since 2018 and allegedly stole more than €100 million from victims across Europe. Five suspects were detained, and bank accounts were frozen in multiple countries.
GitHub malware campaign: LastPass' security team has spotted another collection of malicious GitHub repos claiming to provide free macOS software that actually contains malware, most the Atomic infostealer.
LOL AitM campaign: Orange's cybersecurity team has spotted a clever AitM phishing campaign abusing several online services to hide its malicious code and infrastructure. The campaign primarily targeted European users and abused npm, GitHub, and several smaller public CDNs.
PyPI phishing campaign: The Python Software Foundation warns of a phishing campaign targeting PyPI users. The phishing domain is pypi-mirror[.]org, a variation of the main pypi[.]org domain.
CISA's IR lessons: CISA has released a guide with lessons from one of its incident response engagements. The report is from a breach at an unnamed federal civilian agency that was hacked using a GeoServer exploit.
npm package abuses QR codes: Socket Security has discovered a malicious npm package on the official repo that uses a QR code to store the URL of payloads it needs to download and run.
Operation Rewrite: Palo Alto Networks has published a report on Operation Rewrite, a Chinese hacking group that is manipulating Google search results using hacked IIS servers. This appears to be the same thing that ESET spotted as GhostRedirector earlier this month.
New DDoS record: Cloudflare says it mitigated a new record DDoS attack of 22.2 Tbps. The attack was almost double the previous record, which also targeted its infrastructure at the start of the month. Cloudflare says the attack lasted only 40 seconds. These recent incidents are so large that Cloudflare is now calling them hyper-volumetric DDoS attacks, due to their sheer size.
Cloudflare just autonomously blocked hyper-volumetric DDoS attacks twice as large as anything seen on the Internet before — peaking at 22.2 Tbps & 10.6 Bpps. Can your mitigation provider’s scrubbing capacity handle that scale?
— Cloudflare (@cloudflare.social) 2025-09-22T21:49:16.387447016Z
Malware technical reports
Elons ransomware: Yarix researchers have published a report on Elons, a new variant of the Black Shadow ransomware.
Gunra ransomware: Threat intel analyst Rakesh Krishnan has published a technical report on Gunra, a new ransomware operation that can target both Windows and Linux environments with double-extortion schemes.
Block Blasters analysis: G Data has released an analysis of the malware hidden in the update of Steam game Block Blasters. The malware delivered a crypto-drainer that stole victims' crypto-wallet assets.
Node.js backdoor: The Walmart security team has published a report on a long-lived campaign that distributes apps laced with a Node.js-based backdoor that enrolls users in secret proxy networks.
Malware in qbittorrent Docker container: Software engineer Alessandro Pogliaghi has found a cryptominer in the hotio/qbittorrent Docker image.
YiBackdoor: Zscaler has identified a new malware strain named YiBackdoor. The malware launched in June and has "significant" code overlaps with IcedID and Latrodectus.
Zloader: The same Zscaler team has also published an analysis of recent updates to the Zloader malware.
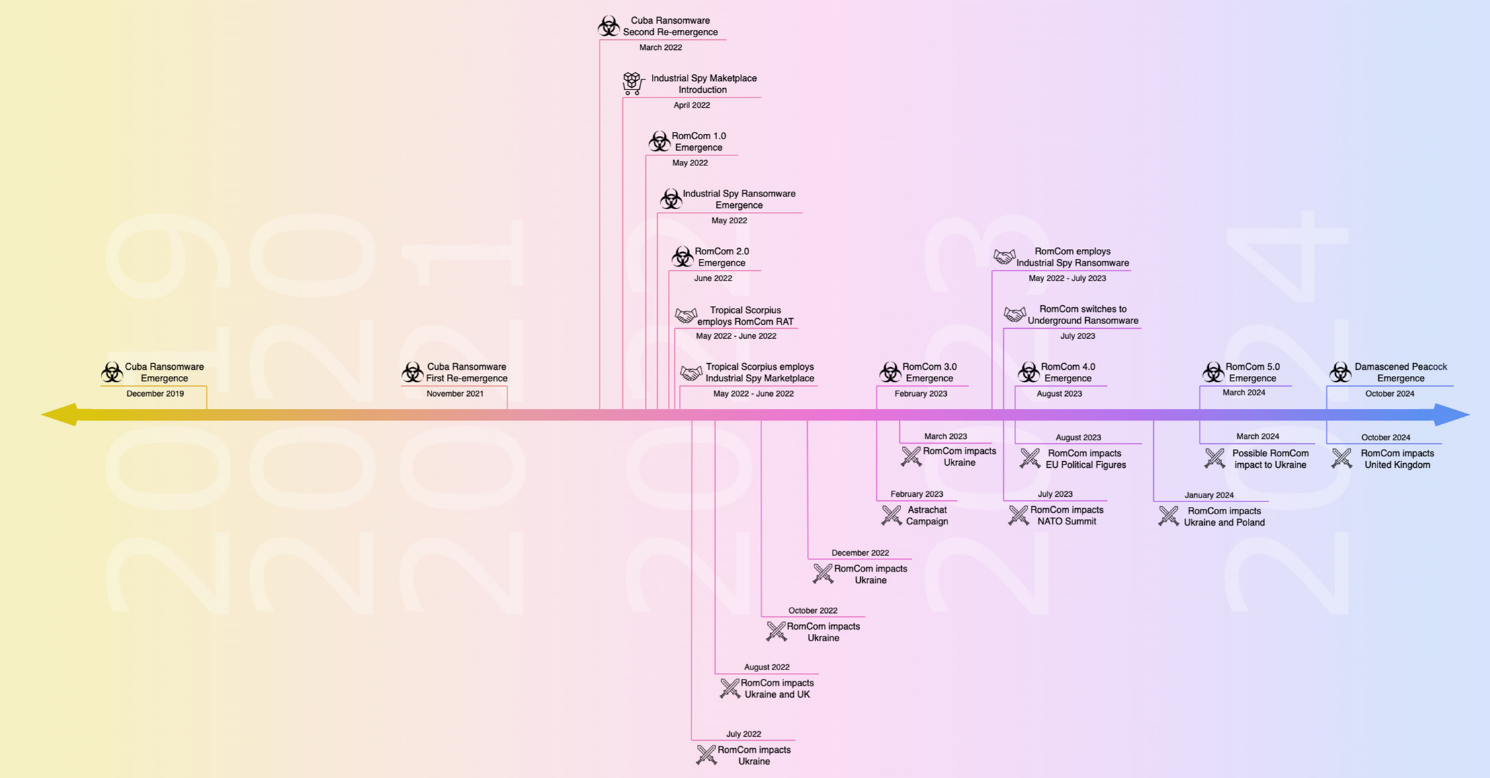
RomCom: AttackIQ has published a report on the evolution of the RomCom malware, covering up to v5 of the tool, which others also call SnipBot and SingleCamper. The malware started out as an e-crime MaaS, but is now often used for APT ops against Ukraine and Europe.
Sponsor section
Justin Kohler, VP of Product at SpecterOps, shows how BloodHound Enterprise can be used to find and fix Active Directory (mis)configurations that could let attackers easily own your entire enterprise.
APTs, cyber-espionage, and info-ops
New Naikon ops: Cisco Talos appears to have stumbled over a new espionage campaign linked to the Naikon APT. This one has been active since 2022 and has targeted the telecommunications and manufacturing sectors in Central and South Asia.
Kimsuky's sex offender campaign: North Korean espionage group Kimsuky used "sex offender notices" to lure victims into running its malware.
Nimbus Manticore: Check Point has a report on an Iranian APT targeting the EU telco, defense, and aerospace sectors. Check Point tracks them as Nimbus Manticore. They are also known as UNC1549, Smoke Sandstorm, and Subtle Snail. It's the same group from this Prodaft report last week.
Russia's Moldova info-ops: The AP, Bloomberg, Silent Push, and ISW have published reports of Russia's disinfo and info-ops designed to attack and destabilize Moldova's pro-EU government ahead of the country's parliamentary elections this weekend. It's basically a flood of AI-based fake news sites imitating Western news outlets, all promoted by engagement farms out of Africa, most likely countries where Russia has staged coups and installed puppet regimes. DFRLab has linked one of them—the REST magazine—to a US Treasury-sanctioned Russian disinfo company named Rybar. According to Politico, something similar is also happening in the Czech Republic.
Vulnerabilities, security research, and bug bounty
New DELMIA Apriso bugs: Two new vulnerabilities can allow hackers to take over factories remotely. The bugs impact Dassault's DELMIA Apriso manufacturing line management platform. The vulnerabilities allow remote attackers to create privileged employee accounts and then use them to upload webshells. Both issues are likely to be exploited. CISA warned earlier this month that hackers are already exploiting another DELMIA Apriso bug to compromise factories.
New Chrome extension loading technique: Synacktiv researchers have documented a new technique to load Chrome extensions for malicious purposes by altering Chromium internal preference files and their JSON MAC property.
SonicWall update removes OVERSTEP rootkit: SonicWall has released a firmware update designed to remove the OVERSTEP rootkit from its SMA appliances. The rootkit was used in a campaign targeting SMA devices since October last year. According to Google, the hackers abused compromised passwords to deploy the rootkit and later ransomware.
Libraesva ESG zero-day: Libraesva has released a security update to fix an actively exploited zero-day in its email security gateways. The company says the bug was exploited by a "foreign hostile state entity." Tracked as CVE-2025-59689, the vulnerability is a command injection bug. Attackers can run malicious code on Libraesva email servers by sending a malicious email containing a specially-crafted compressed attachment. [h/t cr0w]
Proton VPN audit: Proton has released a security audit of its no-logs policy.
Infosec industry
Threat/trend reports: BMC, Bugcrowd, Forescout, and VikingCloud have recently published reports and summaries covering various threats and infosec industry trends.
m0leCon 2025: Talks from the m0leCon 2025 security conference, which took place earlier this month, are available on YouTube.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at a new Center for Strategic and International Studies report—A Playbook for Winning the Cyber War.
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about why it is good news that US investment in spyware vendors has skyrocketed. They also discuss the in-principle agreement for TikTok to remain in the US. It's a win-win: a win for China and a win for TikTok, but not so much a win for US national security.




