Risky Biz News: Romania to hack-back foreign APTs
In other news: Apple patches Triangulation zero-days; EU states want an exemption to spy on journalists; and facial recognition on some modern smartphones is still useless.
This newsletter is brought to you by Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Romanian government will hack back the command and control servers of foreign APT groups targeting the country, General Anton Rog, the head of CyberInt, the cyber division of the Romanian Intelligence Service, said this week at an IT conference in Bucharest.
Gen. Rog says the purpose of hack-back operations will be to acquire malware samples, share them with partners, and disrupt operations.
The agency's new approach is part of a new national cybersecurity strategy adopted in December 2021, which also contains an offensive component that would facilitate such operations.
The new strategy also includes a name-and-shame public attribution, which explains why Romania's Foreign Ministry has often echoed and reinforced public APT campaign attributions coming from NATO allies over the past two years.
This new approach comes after Romania has found itself in the crosshairs of an increasing number of APT campaigns over the past years, and Rog gave quite a few examples.
For example, Russia's Viasat hack, while it may have targeted Ukraine, it also hit Romania's military infrastructure. The Romanian official says the hack cut off communications with some isolated military bases. The outage lasted only for a day while a local telco ran a fiber optics connection to the affected bases.
Chinese espionage group Hafnium (APT40) has also targeted and tried to recruit Romanians via LinkedIn.
"In Romania, 150 specialists were targeted, being asked small things in the beginning, and after that, harder and harder, until they were asked to attack infrastructure," says Gen. Rog. "We processed each one, all the 150. We approached them and explained they were dealing with the Chinese and told them to mind their business, which is what happened. But it took a while."
The only recent happy case was the SolarWinds hack, although maybe not that happy. The official says the supply chain attack didn't impact Romania because local organizations didn't pay their support license.
Romania would not be the first state to go after foreign APT infrastructure. Countries such as the US, the UK, and the Netherlands have already conducted such operations. Many more have offensive components in their national strategies, and others—Romania included—have hacked back against cybercrime operations.
By making its intentions known, the Romanian government is signaling to foreign adversaries. The problem is that the foreign adversaries don't care. Their governments are just gonna put out some lame press release denying everything, have their APT groups retool, and start over. You haven't seen APT28 call it quits after the US shut down their VPNFilter botnet, have you!?!
A video of Rog's talk is available below, in Romanian, obviously. See 1h20m mark.
Breaches and hacks
Washington OAG sues T-Mobile: The Washington Attorney General's Office has sued T-Mobile after the company failed to cooperate in an investigation into its security practices. The OAG started an investigation into the company after its 2021 data breach that exposed the personal information of more than 80 million current and past customers. [Additional coverage in the Seattle Times]
UPS data breach: Shipping company UPS says a threat actor used a vulnerability in one of its package lookup tools to discover the phone numbers of some of its customers. The obtained information was used in smishing and phishing campaigns that targeted customers. The company says the attackers posed as official UPS accounts to demand payment from customers before their packages could be delivered. UPS is currently notifying affected customers. According to Emsisoft security analyst Brett Callow, the breach notification letters appear to have been deliberately crafted to hide the breach and look like materials educating customers about the dangers of smishing and phishing.
Progress sued over MOVEit vulnerabilities: Progress Software has been sued in a class-action following the recent exploitation of a zero-day in its MOVEit file-transfer appliance that has impacted hundreds of organizations. [Additional coverage in CybersecurityDive]
Ransomware attack on cancer center: The US Department of Health and Human Services says a ransomware gang named THT (TimisoaraHackerTeam) has hit a cancer treatment center in the US. The attack took place this month and "significantly reduced patient treatment capability," according to the HHS. The gang has been active since at least 2018 but has not been as active as other ransomware operations. The gang also has a history of hitting US healthcare facilities. More in the HHS security alert [PDF].
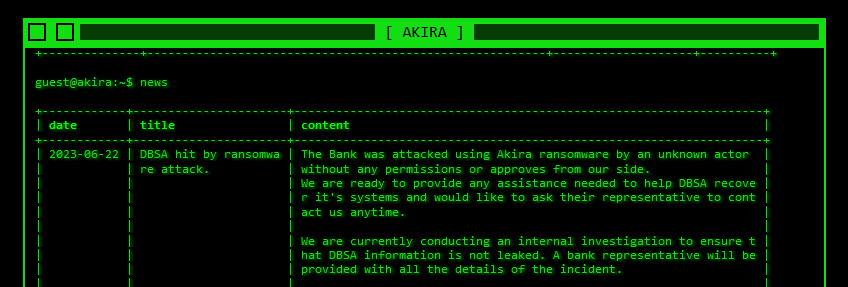
Akira denies DBSA: The Akira ransomware gang has denied breaching and encrypting the Development Bank of Southern Africa (DBSA) in an attack at the end of May. The group claims the bank's systems were attacked by an "unknown actor" who used its ransomware without permission. Akira has now offered to help the bank recover its systems. It also promised to "ensure" that the bank's stolen data is not leaked online.
General tech and privacy
Opera One: Opera Software's new desktop browser, known as Opera One, is now publicly available. Get ready to read a press release with the word "AI" sprinkled everywhere. AI is the new blockchain for tech bros.
Passkeys on Apple.com: The apple.com website now supports passkeys, but only for beta versions of iOS 17, iPadOS 17, and macOS Sonoma.
Google tattles on Microsoft: Google has sent a letter to the FTC accusing Microsoft of using anti-competitive and monopolistic practices in its cloud business. The letter was sent in response to an FTC request for comment on anti-competitive practices in the US cloud market. Google says Microsoft—and Oracle, to some degree—use contracts that lock in customers into their cloud services and harm the cloud market. [Additional coverage in CNBC]
Another FTC action against Amazon: The FTC has filed a complaint against Amazon, accusing the company of forcibly enrolling customers in its Prime program. The FTC says Amazon engaged in the practice for years and intentionally made it difficult for customers to cancel subscriptions. This marks the third FTC against Amazon this month. The FTC filed complaints against Amazon for violating US children's privacy COPPA laws by keeping children's Alexa voice recordings and personal data for years, and another complaint for Amazon's poor security practices at its Ring home security camera division.
Government, politics, and policy
EU, spyware, journalists: Several European governments are pushing the EU to add an exemption in its upcoming European Media Freedom Act (EMFA) to allow member states to continue spying on the electronic communications of journalists under the guise of "national security." The effort is being led by French, German, and Dutch officials. The push comes after the EU's own PEGA commission has advised the EU to add more safeguards to protect democracy and the rule of law in the EU against the abuse of spyware tools. In a report last year, the PEGA commission said several EU countries were abusing surveillance technologies to illegally spy on their own citizens, journalists included, under vague explanations of "national security." More than 60 journalist organizations and civil society groups have now signed a joint letter to the EU Council advising against weakening the upcoming law and giving governments a spying carte-blanche. [More from Netzpolotik, EDRI, ECPMF, IPI, and Investigate Europe]
Streaming sites in Russia: The Russian government is considering lifting bans on foreign online streaming services. Russian banned services like Netflix, Disney+, HBO Max, and others as part of what it calls "counter-sanctions" after the services pulled out from Russia. [Additional coverage in RIA]
Russian disinfo campaign blames Ukraine for dam explosion: Russian officials are using Twitter bot accounts to push a false narrative that Ukraine and Western governments are to blame for the explosion that led to the collapse of the Kakhovka dam earlier this month. According to a report from the German Marshall Fund, the recent effort is one of Russia's largest disinformation campaigns carried out since the start of its Ukrainian invasion. Investigators say the campaign was larger than similar efforts carried out after the Bucha genocide and NordStream pipeline explosions. Despite more accounts participating in the effort, the campaign had far fewer engagements. This might be explained by the general public's awareness of Russia's tendency to lie about almost everything but also by Twitter's downfall into a right-wing cesspool and propaganda echo chamber.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritization.
Cybercrime and threat intel
Lemmy bot attacks: As Lemmy-based communities are popping up across the internet as Reddit replacements, the admins of some of these instances are reporting a sudden influx of automated bot account sign-ups.
Ransomware in May: 436 victims have been posted on ransomware leak sites in May 2023, according to new research from NCC Group. The figure is a 24% surge compared to April's 352 victim count. The Lockbit gang was responsible for 18% (78 victims) of all May attacks and remains the most active threat actor in 2023. Second was 8Base, a ransomware group that began operations in April.
Crypto.biz profile: Brian Krebs has a profile on Cryptor[.]biz, a malware crypting operation that has serviced some of the world's largest cybercrime gangs.
Hacker groups on Facebook: Check Point has a look at the rising number of Facebook groups serving as a home for various scamming and hacking groups.
PyPI malware: SecDevOps firm Sonatype has a report looking at recent malware uploaded on the PyPI portal.
KEV update: CISA has updated its KEV database with six new vulnerabilities that are currently being actively exploited. The list includes three Roundcube email server bugs exploited by Russian GRU hackers, a recent VMWare zero-day, and Firefox and Windows 2016 vulnerabilities.
BlackLotus guidance: The US National Security Agency has issued guidance on how organizations can mitigate and protect systems against BlackLotus, a bootkit linked to APT operations.
"BlackLotus exploits a known vulnerability called 'Baton Drop,' CVE-2022-21894, which bypasses security features during the device's startup process, also known as Secure Boot. The malware targets Secure Boot by exploiting vulnerable boot loaders not added into the Secure Boot Deny List Database (DBX)."
IoT exploitation: PAN's Unit42 has a summary of the recent IoT vulnerabilities exploited by DDoS botnets in the wild.
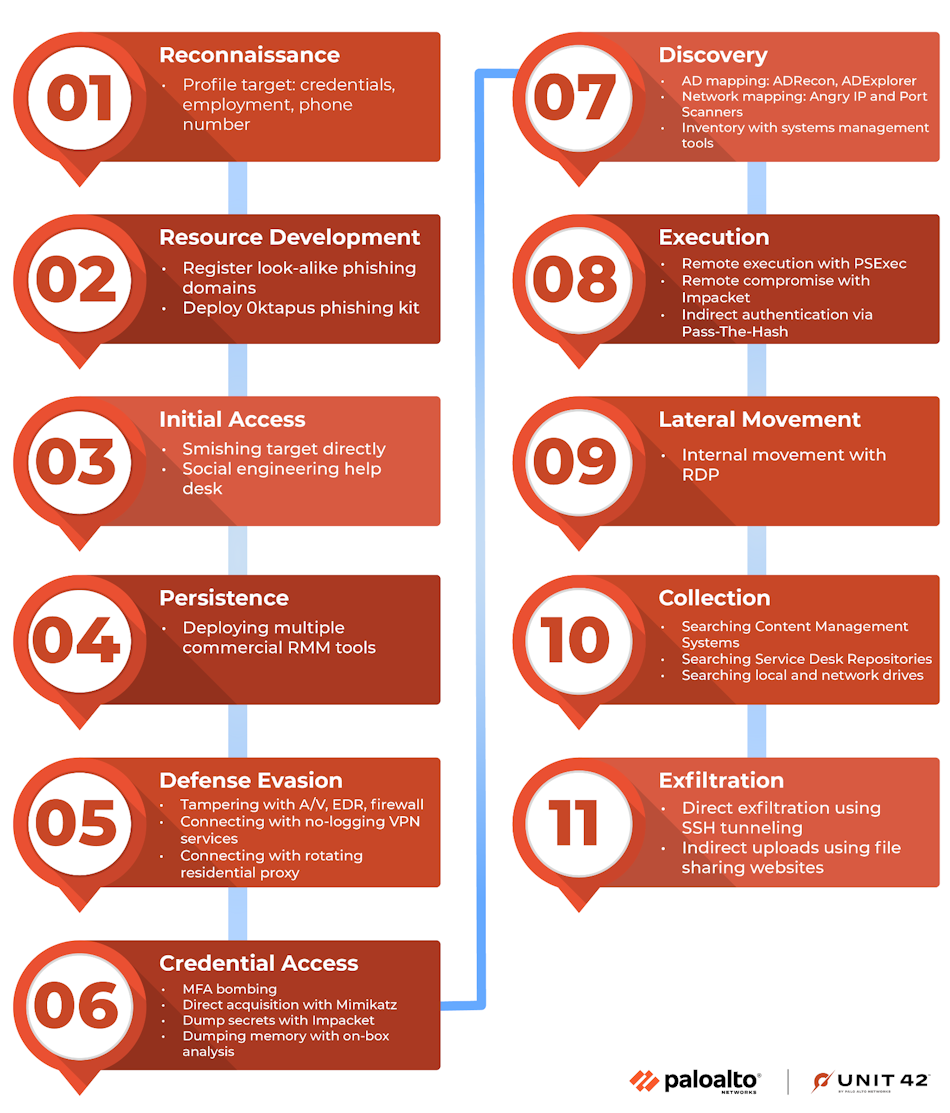
Muddled Libra group: A new threat actor named Muddled Libra has been conducting phishing campaigns against large outsourcing firms serving high-value cryptocurrency companies. The group has been linked to more than half a dozen incidents from mid-2022 through early 2023. According to Palo Alto Networks, the group employs a phishing toolkit named 0ktapus, the same toolkit also used by groups such as 0ktapus, Scattered Spider, and Scatter Swine.
"While these have been treated in the media as three names for one group, in actuality, it's likely multiple actors using a common toolkit. Muddled Libra is a subset of these actors."
Malware technical reports
RedEnergy: Zscaler researchers say the RedEnergy infostealer is now providing a Stealer-as-a-Ransomware option for its customers, where it is offering file encryption modules to allow its "customers" to lock systems they've managed to infect.
DeepBlueMagic ransomware: Varonis has published an analysis of DeepBlueMagic, a ransomware operation that conducts targeted attacks and uses LOLbins and legitimate tools for its intrusions. For example, Varonis says the gang abuses Microsoft's native disk encryption utility BitLocker, and the Jetico BestCrypt utility for the actual encryption process.
Gh0stBin RAT: ANY.RUN has published a breakdown of a previously unseen version of Gh0stBin, a popular RAT from the Chinese scene.
AhMyth RAT: SecurityScorecard's Vlad Pasca has a breakdown of the AhMyth Android remote access trojan, first spotted by ESET this spring.
FluHorse: Fortinet has a report on FluHorse, an Android banking trojan that's currently being deployed across Southeast Asia. Also, check out CheckPoint's report on the same strain from May.
MULTI#STORM: Securonix has published a report on a phishing campaign they're calling MULTI#STORM that aims to infect users with the WarzoneRAT.
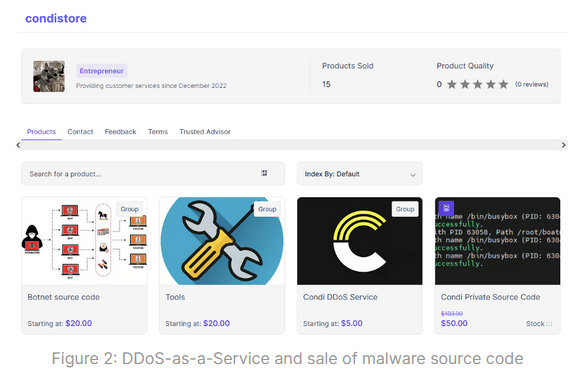
Condi DDoS botnet: Fortinet researchers have discovered a new DDoS-for-hire service named Condi. The service launched this year and was built on top of a new IoT malware modified from the old Mirai strain. Fortinet says the botnet grew exponentially since the end of May after exploiting a recent vulnerability (CVE-2023-1389) in TP-Link Archer routers. Access to the botnet and even its source code is currently provided via a Telegram channel. Similarly, Akamai has also observed exploitation by another Mirai DDoS botnet of a vulnerability (CVE-2023-26801) in LB-Link routers, although Akamai didn't attribute these attacks to the same botnet. Both vulnerabilities were patched in March.
Risky Business Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
Flea (APT15, Nickel): The Flea Chinese APT group has been deploying a new backdoor named Graphican in a cyber-espionage that has targeted ministries of foreign affairs in the Americas. The campaign ran from late 2022 into early 2023. According to Broadcom's Symantec division, the new Graphican malware is an evolution of an older Flea backdoor named Ketrican, which itself was based on a previous malware named BS2005.
Camaro Dragon: Check Point has discovered new malware associated with the Camaro Dragon Chinese APT group. Named WispRider and HopperTick, the malware can spread via USB devices. It's the latest in the group's growing arsenal, which also includes a web shell named HorseShell deployed via a firmware implant and a Go-based backdoor named TinyNote.
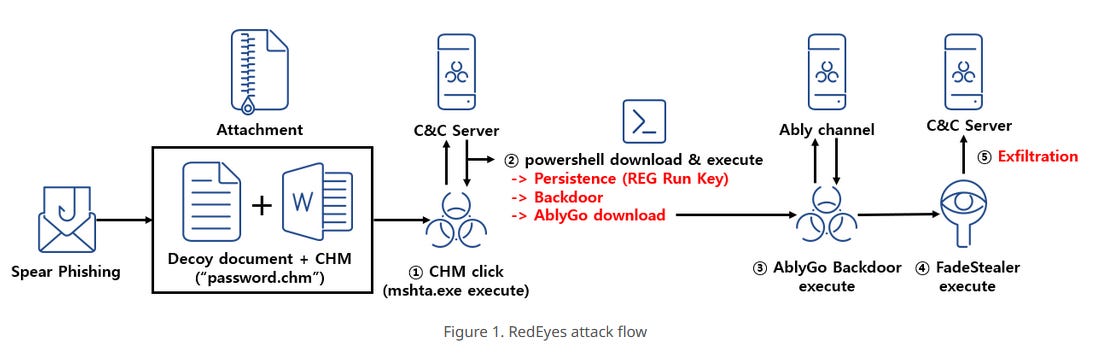
RedEyes: A recent AhnLab report looks at a recent campaign from the RedEyes (APT37, Scarcruft) group targeting North Korean defectors, human rights activists, and university professors. The campaign deployed new malware, such as AblyGo and FadeStealer.
Bitter: Chinese researchers at Th0r Security have published an analysis of recent malware employed by the Bitter APT.
Midnight Blizzard (Nobelium, APT29): Microsoft has observed an increase in activity from the Midnight Blizzard Russian cyber-espionage group. The new campaign leverages residential proxy services to carry out password spraying and credential brute-force attacks. The group has also used stolen session keys acquired from underground marketplaces to access cloud infrastructure. Microsoft has identified the targets of recent attacks as governments, IT service providers, NGOs, defense industry, and critical manufacturing organizations.
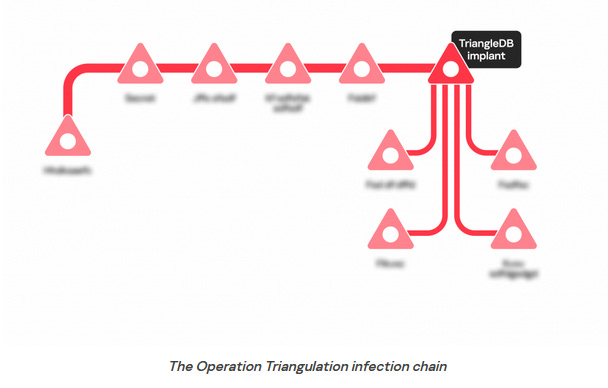
Apple patches Triangulation zero-days: Apple has released security updates that patch three zero-days across iOS and macOS, including two zero-days that were exploited in an attack known as Operation Triangulation. The operation targeted Russian government officials, foreign diplomats working in Russia, and Kaspersky employees. Russia's FSB intelligence service linked the attack to the NSA and claimed Apple cooperated with the American spy agency. Apple denied the FSB's claims. The two Triangulation zero-days are tracked as CVE-2023-32434 and CVE-2023-32435. They were discovered by Kaspersky researchers, who also published an analysis of TriangleDB, one of the malware strains installed on compromised iPhones.
"The implant, which we dubbed TriangleDB, is deployed after the attackers obtain root privileges on the target iOS device by exploiting a kernel vulnerability. It is deployed in memory, meaning that all traces of the implant are lost when the device gets rebooted. Therefore, if the victim reboots their device, the attackers have to reinfect it by sending an iMessage with a malicious attachment, thus launching the whole exploitation chain again. In case no reboot occurs, the implant uninstalls itself after 30 days, unless this period is extended by the attackers."
Vulnerabilities, security research, and bug bounty
Google Cloud VRP: Google says it awarded $313,337 in rewards to security researchers via its Google Cloud VRP last year. The largest prize was $133,337 for a suite of LPEs in the GKE Autopilot.
KeePassXC vulnerability drama: The KeePassXC password management application is disputing a recently assigned CVE (CVE-2023–35866) that claims the app is vulnerable to a bug that allows a threat actor to change the master password and second-factor authentication settings.
Enphase Energy ignores CISA request to fix bugs: American energy technology company Enphase Energy has ignored a CISA request to fix two remotely exploitable vulnerabilities in two of its products. CISA has published a security advisory this week warning US organizations that the products are vulnerable to attacks. The vulnerabilities impact Enphase's Envoy communications gateway and its Installer Toolkit Android app.
nOAuth vulnerability: Descope researchers have discovered a vulnerability in Microsoft Azure AD OAuth applications that could lead to full account takeover. Microsoft fixed the issue—named nOAuth—earlier this week.
Fortra Globalscape EFT vulnerabilities: Rapid7 has published details about three vulnerabilities in Fortra Globalscape EFT administration servers, including an authentication bypass (CVE-2023-2989). Fixes were released last week.
RocketMQ vulnerability: Juniper has published an analysis of the recent Apache RocketMQ vulnerability (CVE-2023-33246) that is being exploited in the wild.
LibreOffice vulnerability: Secfault Security has published a write-up on CVE-2023-1183, an arbitrary file write vulnerability in the LibreOffice suite patched last month.
Cisco security updates: Cisco has released two fixes this week. One is for a Cisco email gateway XSS, while the second is for a 2FA authentication bypass in the company's Duo app for macOS.
Smartphone facial recognition is mostly useless: New research carried out by a Dutch consumer protection association has found that facial recognition systems on most of today's mid to upper-tier smartphones can be bypassed using a photo. Researchers bypassed facial recognition on 26 of 60 smartphones. The results are identical to a similar 2019 study, where the same organization bypassed facial recognition using a photo on 26 of 60 smartphones available on the market at the time. This time around, Apple and Samsung devices were deemed much more secure. Researchers couldn't bypass facial recognition on iPhones, and only one of 12 Samsung models failed the test. Fourteen of the 26 smartphones that failed the test are Xiaomi models. Full list below.
- HONOR 70 5G (€380)
- Motorola moto e13 (€120)
- Motorola moto g13 (€180)
- Motorola moto g23 (€230)
- Motorola Moto g72 (128 + 8 GB) (€265)
- Nokia G22 (€195)
- Nokia G60 5G (128 + 4 GB) (€300)
- Nokia X30 5G (128 + 6 GB) (€440)
- OnePlus Nord CE 3 Lite (€300)
- OPPO A17 (€180)
- OPPO A57 (€150)
- Samsung Galaxy A04s (€150)
- Xiaomi 12 Lite (128 + 8 GB) (€355)
- Xiaomi 12T (128 GB) (€500)
- Xiaomi 12T Pro (256 + 8 GB) (€620)
- Xiaomi 13 (€750)
- Xiaomi 13 Lite (128 GB) (€400)
- Xiaomi 13 Pro (€1,300)
- Xiaomi POCO M5 (64 GB) (€190)
- Xiaomi POCO M5s (64 GB) (€210)
- Xiaomi POCO X5 5G (128 + 6 GB) (€265)
- Xiaomi POCO X5 Pro 5G (128 + 6 GB) (€330)
- Xiaomi Redmi 12C (32 + 3 GB) – Blue (€120)
- Xiaomi Redmi Note 12 (128 GB) (€230)
- Xiaomi Redmi Note 12 5G (€230)
- Xiaomi Redmi Note 12 Pro 5G (128 + 8 GB) (€325)
Infosec industry
Google cybersecurity clinics: Google has committed more than $20 million to the creation of cybersecurity clinics at 20 higher education institutions across the US. The clinics will provide free cybersecurity training and hands-on experience for thousands of students. Some Google employees will serve as mentors and trainers at some of the clinics. Google will also provide free scholarships to allow some students to attend its Cybersecurity Certificate program.
"These clinics provide free security services in the same way law or medical schools offer free clinics in their communities. They give students the opportunity to learn and improve their skills, while helping to protect critical infrastructure such as hospitals, schools and energy grids."
India cybersecurity workforce shortage: India is expected to face a shortage of around 3 million cybersecurity professionals by the end of 2023, according to a report from The Times of India.
Metasploit problems: Google is refusing to remove a RubyGems Metasploit-related package from its Safe Browsing naughty list.
New tool—Xortigate scanner: Security firm BishopFox has released a tool that can scan FortiGate SSL VPN instances and see if they are vulnerable to a recently-patched zero-day known as XORtigate (CVE-2023-27997). The tool is available on GitHub.
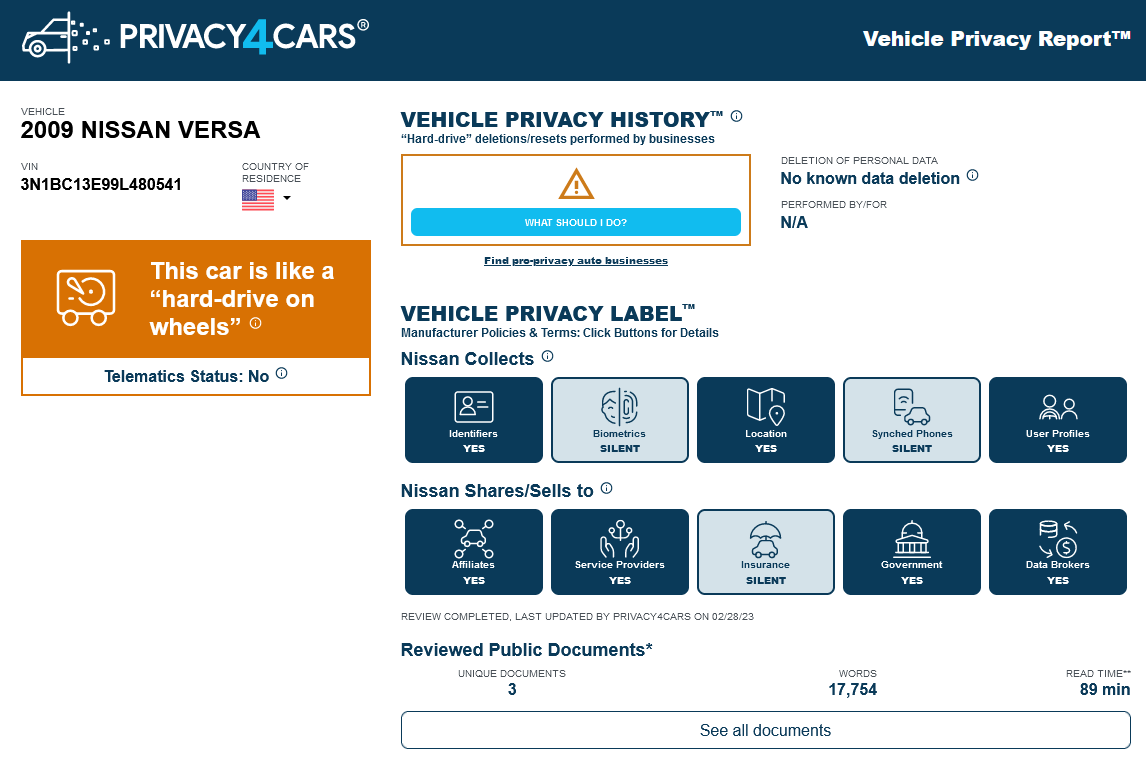
New tool—Vehicle Privacy Report: A newly launched tool named Vehicle Privacy Report shows what type of data carmakers and their cars collect from owners.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at three different state operations that have recently been outed and what these operations tell us about how these states are behaving.




