Risky Bulletin: SmarterTools hacked via its own product
In other news: Dutch DPA and European Commission hacked via Ivanti zero-days; Senegal held for ransom; state actor behind Signal phishing campaign in Germany.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
SmarterTools, the company behind the SmarterMail email server, was hacked via a vulnerability in its own product.
The incident took place at the end of last month, on January 29.
The Warlock ransomware group breached 30 email servers running on the company's office network and inside a data center used for quality control testing.
SmarterTools COO Derek Curtis says the entry point was a virtual machine that was not updated, allowing the hackers to enter its network and then spread to the other servers.
SentinelOne security products caught and blocked the ransomware when it attempted to encrypt data. The company's Portal support center went down as a result of the intrusion, but the exec said network segmentation prevented the hackers from reaching other systems.
SmarterTools didn't specify what vulnerability the hackers used, but the company has had a rough start of the year. Three SmarterMail vulnerabilities were disclosed and promptly added to CISA KEV, a US government database of actively exploited security flaws.
Of these three, CVE-2026-24423 is the only one with a "Known To Be Used in Ransomware Campaigns" tag, and is likely the bug that the Warlock group exploited in the attack.
That vulnerability, an authentication bypass that can be used to reset admin passwords, was discovered by WatchTowr Labs and disclosed a week before the hackers used it to breach SmarterTools itself. It was patched on January 15, two weeks before the SmarterTools breach.
The group behind this intrusion are also a very advanced and skilled threat actor. They are tracked in the infosec community as Gold Salem (Sophos naming) and Storm-2603 (Microsoft naming).
They are believed to be a cybercrime group operating out of China. They began using the Warlock ransomware in attacks in March of last year.
The group was among the three threat actors that initially abused the ToolShell exploit to attack SharePoint servers with a zero-day in July of last year.
According to a Fortinet analysis:
"The group’s tactics blend state-sponsored espionage techniques with cybercrime methods, using DLL-sideloading, DLL-hijacking, the AK47 C2 framework, and the BYOVD (Bring Your Own Vulnerable Driver) to evade detection."
Via Sophos:
"GOLD SALEM had no public footprint until a June 2025 RAMP underground forum post by a persona representing the group solicited exploits for common enterprise applications (e.g., Veeam, ESXi, SharePoint) and tools to kill endpoint detection and response (EDR) systems and other security products. A subsequent post sought cooperation from initial access brokers (IABs) in providing potential victims. It is unclear if the group was seeking access to carry out their own intrusions, recruiting affiliates for a nascent ransomware-as-a-service (RaaS) operation, or both."
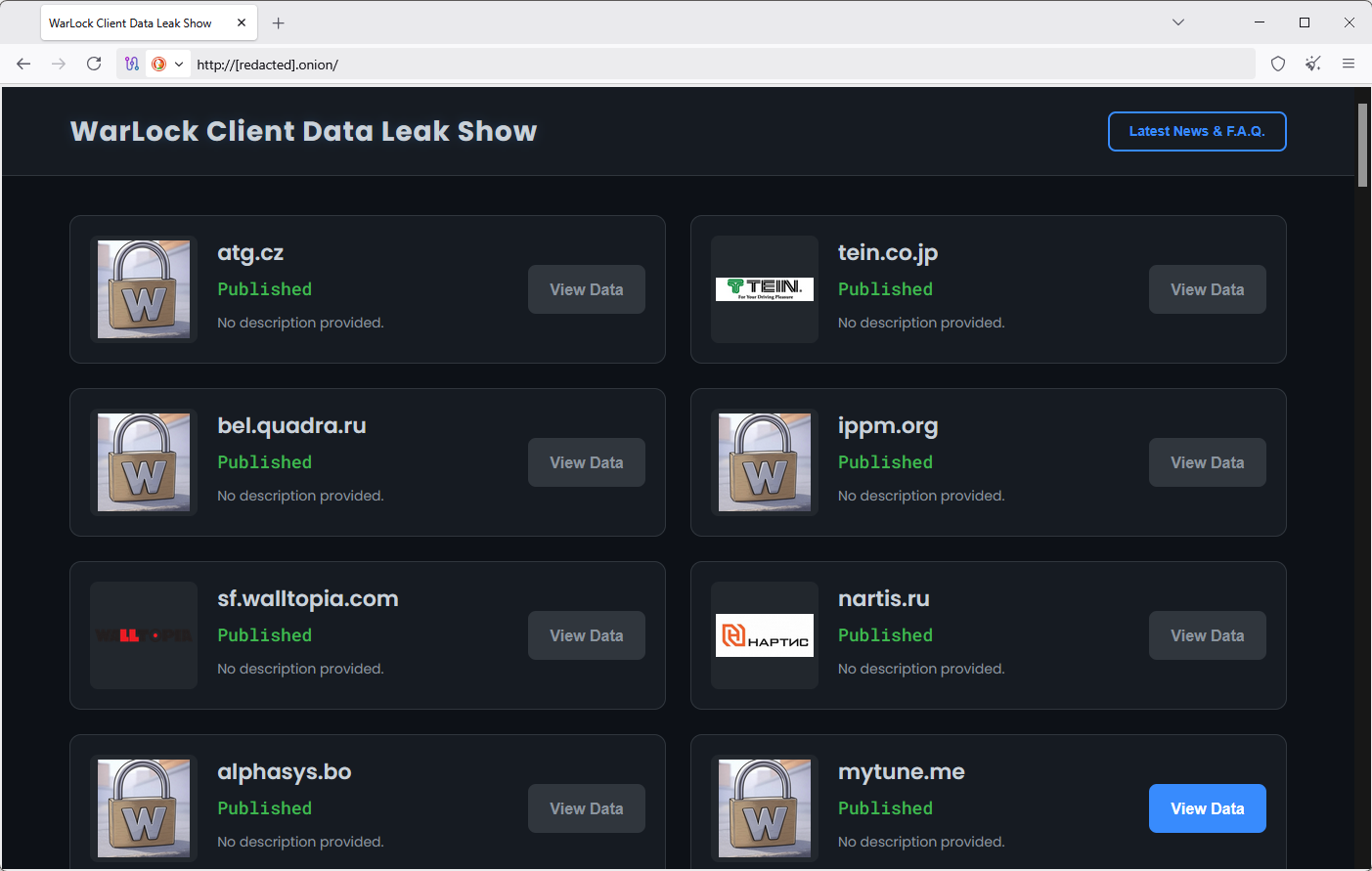
Besides Warlock, the group has also used other ransomware strains, such as LockBit Black (LockBit 3.0), and X2ANYLOCK (AK47). So far, its dark web leak site has listed close to 80 victims.
See here for more technical reports on Warlock: Hybrid Analysis, Quorum Cyber, Trend Micro.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Flickr 3rd party breach: Photo-sharing website Flickr has notified users this week of a security breach. The breach originated at a third-party email service provider used by the company. Flickr says hackers obtained names, emails, IP addresses, and their history on the site. The company says it detected the breach and notified the affected provider.
Dutch DPA hacked via Ivanti gear: The Dutch Data Protection Authority and the Council for the Judiciary have been hacked using two recently disclosed Ivanti zero-days. Both agencies notified the Dutch Parliament last week. An investigation is currently ongoing together with Dutch cybersecurity agencies. Ivanti disclosed the two zero-days on January 29, warning of ongoing abuse.
EU discloses security breach: The same Ivanti zero-days were likely also used to breach the servers of the European Commission. The EC says hackers likely gained access to names and mobile numbers of some of its staff members. The incident took place at the end of last month, on January 30.
Spain Ministry of Science incident: Spain's Ministry of Science has shut down its online university portal following a security breach. A hacker using the name Gordon Freeman claimed online to have obtained the data of thousands of students. Stolen data allegedly includes email addresses, passport scans, and banking details. The ministry took down the portal to investigate the claims. [Escudo Digital]
JLR losses reach $405 million: Jaguar Land Rover and parent company, Tata Motors, have reported losses of $406 million related to a ransomware attack last year. The losses represent $228.5 million in lost sales and a $177.2 million one-time charge related to incident response. Jaguar Land Rover accounts for around 80% of its parent company revenues. [Reuters]
BridgePay ransomware: Payments provider BridgePay has linked a recent outage to a ransomware attack.
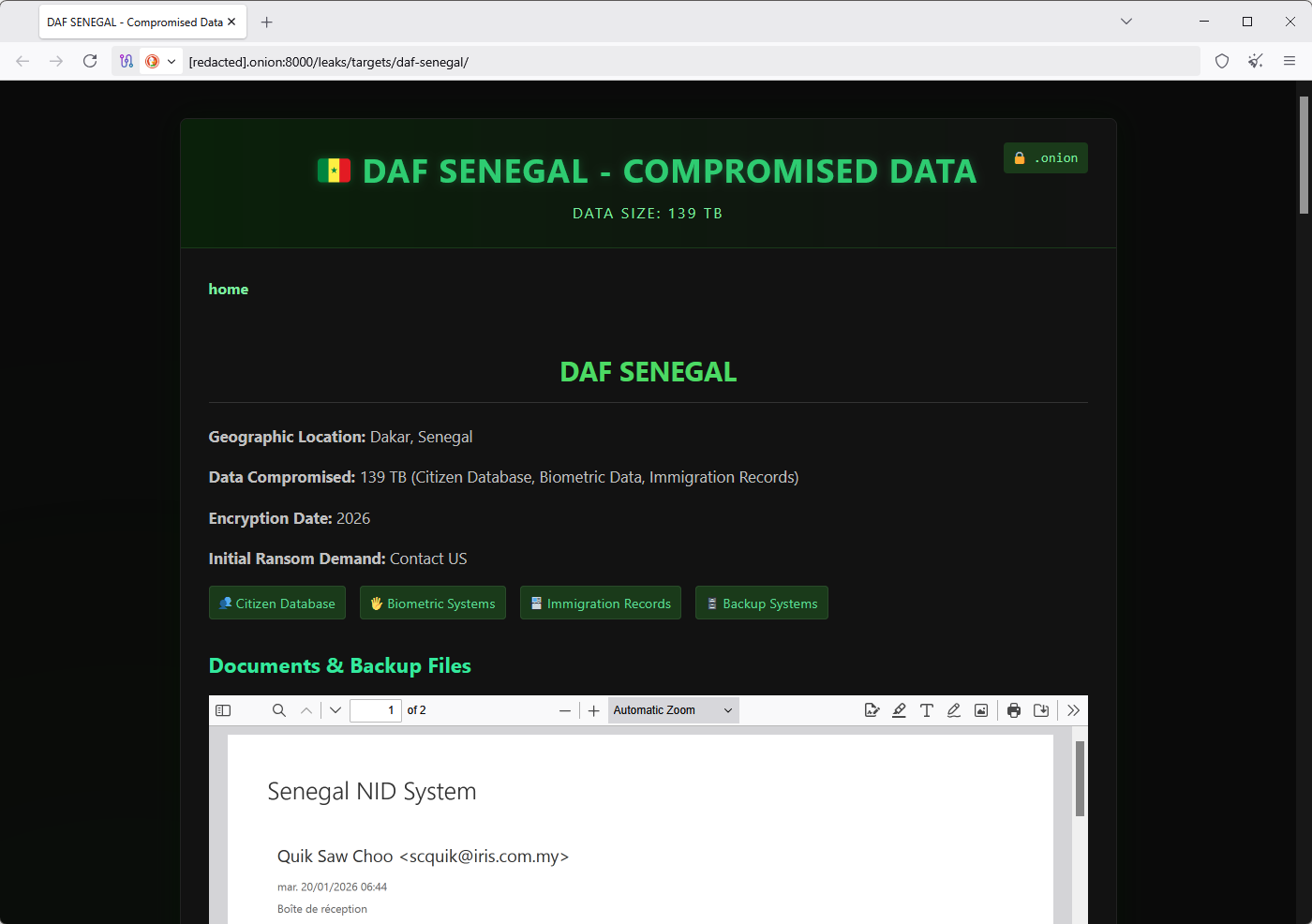
Major Senegal government breach: A newly launched ransomware group is holding Senegal's government for ransom. The Green Blood group claims to have stolen 139TB of data from the country's Department for the Automation of Records (DAF). The agency holds extremely sensitive information on all the country's population. It stores data used for identity, biometric, electoral, and immigration systems. DAF technicians are working to restore affected systems. The country's tax agency was also hit by a ransomware group last October. [The Gambia Journal]
General tech and privacy
Secure Boot-pocalypse: Microsoft held an AMA session and updated its guide to help sysadmins safely replace Secure Boot certificates that are set to expire this June.
ClawHub to scan skills using VT: The ClawHub marketplace for AI agent skills will scan all submitted skills using VirusTotal. The integration comes after security researchers found almost 400 malicious skills uploaded on the platform over the past 10 days. The malicious skills would install malware and steal credentials and cryptowallet data. VirusTotal is also used to scan the Hugging Face platform for malicious LLM models.
Big oopsie at BitHumb: South Korean cryptocurrency exchange Bithumb accidentally sent more than $44 billion worth of cryptocurrency (620,000 bitcoin) to its customers last week. The exchange reportedly meant to send the equivalent of 2,000 won to customers but sent them 2,000 bitcoin instead. Bithumb says it recovered 99.7% of the money, but that still leaves it with a loss of $130 million. [Reuters]
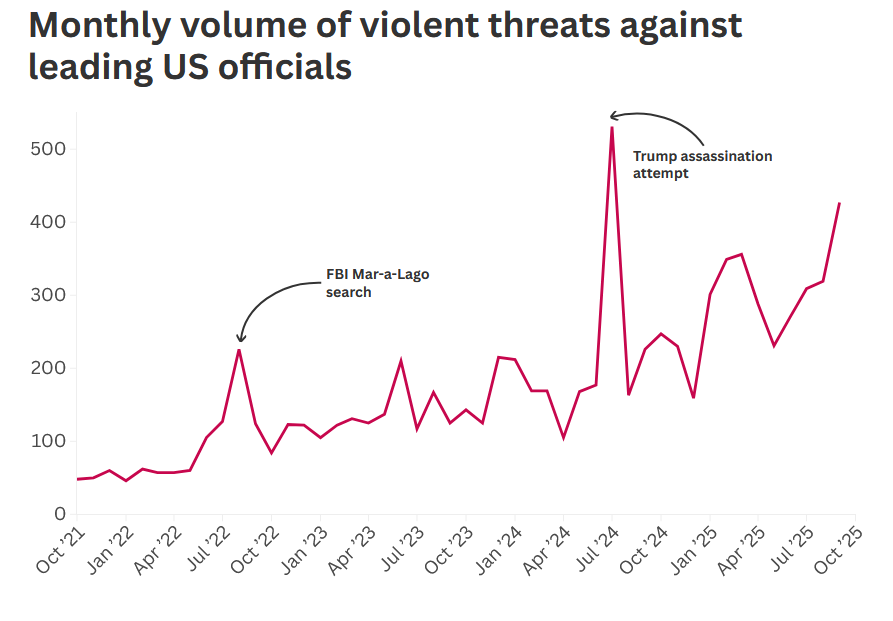
Rise of violent threats on social media: ISD looks at the constant rise in violent threats against US politicians on social media sites such as Reddit, Twitter, BlueSky, YouTube, and others. Around 47% of the recorded threats were against current US President Donald Trump.
Government, politics, and policy
NGOs warn EU against weakening regulation: The EDRi and other NGOs and civil society groups have warned the EU against weakening its privacy laws and other regulation to appease the US and its big tech sector. [Politico Europe]
EU's TikTok investigation: The EU has published preliminary results of its TikTok investigation, which found that the company uses "addictive design" to keep users engaged, in breach of the bloc's Digital Services Act.
Sponsor section
In this Risky Business sponsor interview, Tom Uren talks to Trail of Bits CEO Dan Guido about how Trail of Bits is reworking its business processes to take advantage of AI. Dan talks about what it takes to make AI agents reliable and trustworthy and how that will give the company an edge by making its work both better and faster.
Arrests, cybercrime, and threat intel
China executes scam compound execs: The Chinese government has carried out the death sentences of four individuals who ran cyber scam compounds in Myanmar. The suspects were executed following failed appeals. All were members of the Bai crime family. China also executed 11 members of the Ming crime family for similar offences last month.
DDoSer arrested in Poland: Polish police have arrested a 20-year-old for launching DDoS attacks against popular websites around the world. The unnamed suspect allegedly ran his own DDoS-for-hire service. He has already pleaded guilty to most charges.

Northwestern hacker pleads guilty: An Illinois man pleaded guilty to hacking the Snapchat accounts of almost 600 women. Kyle Svara stole nude images from 59 of those accounts, which he sold or traded online. He also sold his services online. One of the people that hired Svara was Steve Waithe, a former Track and Field Coach at Northeastern University, who paid him to hack his students' accounts.
Nigerian scammer gets 8 years: A US judge has sentenced a Nigerian national to eight years in prison. Tochukwu Albert Nnebocha defrauded elderly Americans through an inheritance fraud scheme. He allegedly made more than $6 million from more than 400 victims. Nnebocha was arrested in Poland last year.
DSLRoot profile: An underground service run by a Belarusian national is paying Americans to host hardware at their homes. The devices are part of a shady proxy network that redirects malicious traffic through US residential IP addresses. The service is named DSLRoot and allegedly ran by a Belarusian man named Andrei Holas.
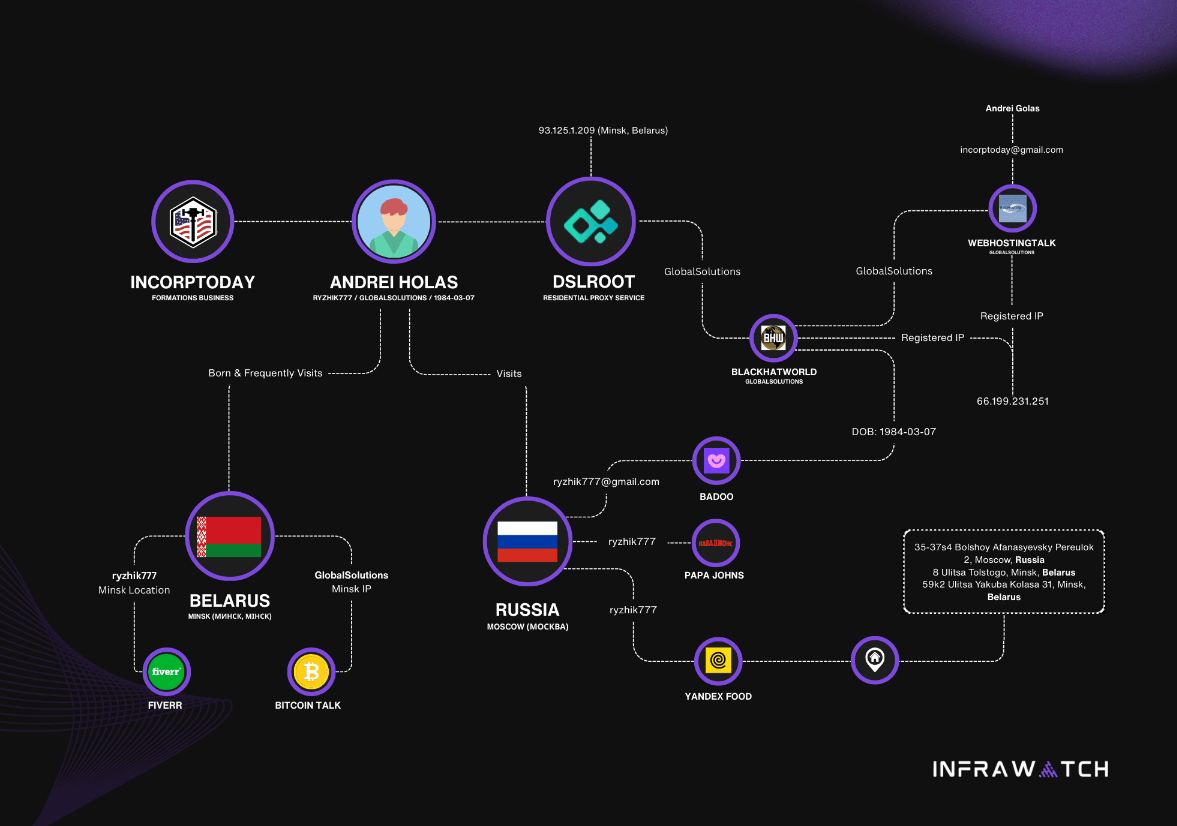
GhostSocks profile: The same Infrawatch also looks at GhostSocks, another residential proxy network advertised to cybercrime groups. This one was closely integrated in the Lumma infostealer to seamlessly update C2 servers on the fly.
DKIM replay phishing: Threat actors are using a technique called DKIM replay attacks to slip phishing emails in users' inboxes. The technique relies on threat actors sending malicious invoices or dispute notifications to their own email addresses, but then forwarding that email to a desired target. Because the email initially originated from a legitimate service, it passes both DKIM and DMARC verifications. So far, Kaseya has seen the technique abused via services like PayPal, Apple, DocuSign, and HelloSign.
Bing malvertising: Just because it doesn't have a big market share, that does mean Bing's search ads are not abused for malvertising. Netskope looks at one of these campaigns, one that leads users to tech support scams.
PyPI and npm supply chain attacks: Socket Security has spotted malicious packages on both npm and PyPI that targeted developers working with the dYdX cryptocurrency protocol.
17% of OpenClaw skills are malicious: Around 17% of all OpenClaw skills published online this month exhibit signs of malicious behavior. According to Bitdefender, malicious skills are often cloned and re-published at scale using small name variations. Most are focused on cryptocurrency theft. Top categories include:
- Wallet tracking tools (14% of all malicious skills)
- Polymarket-related skills (9.9%)
- Solana-related skills (9.3%)
- Phantom wallet skills (8.2%)
- Ethereum and Bitcoin tools (5.2% combined)
A third of open agent skills are malicious: A similar study conducted by Snyk found the number of malicious AI agent skills to be at 36%, but this study also included skills from the skills.sh portal as well, not just ClawHub.
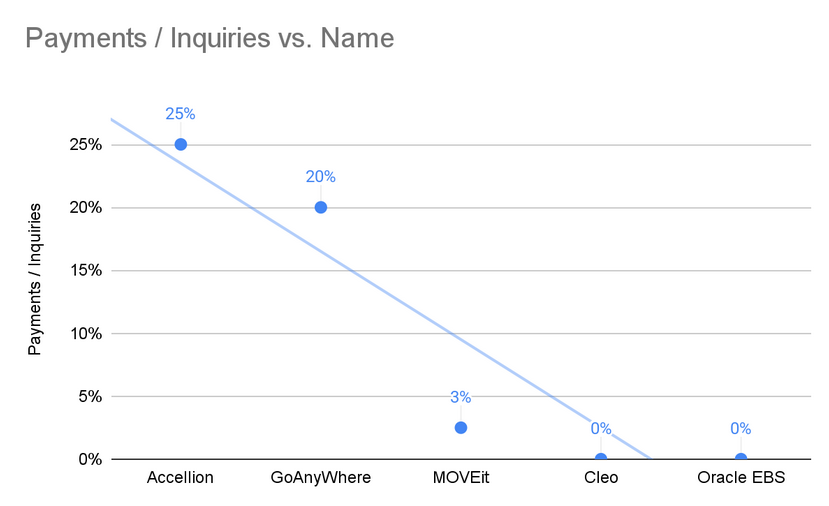
People aren't paying Clop anymore: Most companies aren't paying ransom demands to the Clop group anymore. The group is known for exploiting zero-days in enterprise software, stealing large amounts of data, and then ransoming victims over the course of months. It has been behind zero-day waves that targeted software like Accelion, GoAnywhere, MoveIT, Cleo, and the Oracle E-Business Suite. Security firm Coveware says it is not aware of companies paying the Clop gang for the last two waves of attacks.
Malware technical reports
Prometei: eSentire have published a technical analysis of Prometei, an old botnet known to be focused on credential harvesting and cryptomining.
Sponsor section
In this Risky Business sponsor interview, Casey Ellis chats with Keith Hoodlet from Trail of Bits. Keith is Trail of Bits’ director of engineering for AI, machine learning and application security and he joined Casey to talk about why prompt injection attack techniques that target AI are an unsolvable problem.
APTs, cyber-espionage, and info-ops
Germany warns of ongoing Signal phishing: A state-sponsored threat actor is targeting the Signal users in Germany. According to Germany's cybersecurity agency, targets include high-ranking politicians, the military, and investigative journalists. Two types of attack variants were detected. Both aim to bind a user's account to an attacker's device. While German officials didn't attribute the campaign, both techniques have been used by Russian hackers last year to target the Ukrainian government and military.
Salt Typhoon hacks in Norway: Norway has confirmed that Chinese hacking group Salt Typhoon has breached companies in the country. The group is widely known for breaching major US telcos in a series of hacks in 2024. It is widely believed that the same campaign impacted telcos all over the globe, and not just the US. [Norwegian Police Security Service (PDF) // The Record]
Vortex Werewolf: Russian security firm BI.ZONE looks at Vortex Werewolf (SkyCloak), a threat actor that has attacked Russian government and defense organizations over the past two months.
APT-C-28(ScarCruft, Konni): Qihoo 360 has spotted the APT-C-28 group targeting DeFi developers and Web3 startups with malware hidden in investment proposals.
RokRat updates: S2W looks at another ScarCruft campaign, this one delivering a new version of the RokRat malware.
Vulnerabilities, security research, and bug bounty
Claude the busy bee: Anthropic claims that its newly released Claude Opus 4.6 model has discovered more than 500 high-severity vulnerabilities in open-source projects. Impacted projects included GhostScript, OpenSC, and CGIF. Anthropic says the model found the bugs without task-specific tooling, custom scaffolding, or specialized prompting. The new Claude model was specifically improved for coding tasks.
Git metadata leaks: MysteriumVPN claims to have identified over 5 million web servers that are leaking some sort of Git metadata.
KEV update: CISA has updated its KEV database with two vulnerabilities that are currently exploited in the wild. This includes a recent SmarterMail zero-day and a React Native CLI bug.
SolarWinds Web Help Desk exploitation: Microsoft has published some TTPs from recent attacks exploiting SolarWinds Web Help Desk servers.
Fortinet patches SQLi bug: Fortinet has released a security update on Friday to patch an SQL injection vulnerability in the FortiClient EMS.
TP-Link RCE: The Out Of Bounds bug hunting group looks at a three-exploit chain that can be used for pre-auth RCE attacks against the Dynamic DNS feature of TP-Link routers.
ESET security update: ESET has patched a local privilege escalation in its Management Agent for Windows.
"The vulnerability lies in the way file operations are handled during the execution of commands from the ESET PROTECT Web Console on the Microsoft Windows operating system. The commands are being stored in a predictable and writable location, therefore altering these temporary files allows an attacker with the ability to run code under Administrator privileges to change the commands and have them executed under the SYSTEM account, thus escalating their privileges."
Infosec industry
Threat/trend reports: CompariTech, Coveware, Ruixing, Spamhaus, Storyblok, ThreatMon, and Wordfence have recently published reports and summaries covering various threats and infosec industry trends.
Acquisition news #1: American cybersecurity giant Zscaler has acquired browser security startup SquareX. Terms of the transaction have not been disclosed.
Acquisition news #2: Mobile security firm Guardsquare has acquired Verimatrix's XTD platform and services.
New tool—Augustus: Security firm Praetorian has open-sourced Augustus, an LLM security testing framework for detecting prompt injection, jailbreaks, and adversarial attacks.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about Google's cyber disruption unit taking aim at the IPIDEA residential proxy network. The network was a cybercrime enabler that was used by hundreds of threat actors for crime and espionage.
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the recent Russian attack on Polish electricity infrastructure.




