Risky Biz News: Microsoft will replace Secure Boot certificates to avoid 2026 boot-pocalypse
In other news: Volt Typhoon expands to Africa; Poland's spyware abuse was far worse than previously thought; and Microsoft discloses new Exchange zero-day.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Microsoft has released this week an optional servicing update that rotates digital certificates used by the Secure Boot feature.
The update is likely to unclench some sphincters in the IT administration and cybersecurity community, as the certificates were set to expire in 2026.
Once the certificates expired, Windows systems where Secure Boot was enabled would have failed to boot. The issue would have also impacted some Linux systems that use Microsoft certificates for their bootloader, such as Ubuntu.
The update contains a new Key Exchange Key (KEK) certificate and two new Allowed Signature DB (DB) certificates—one for signing the Windows bootloader itself and the second for signing third-party drivers.
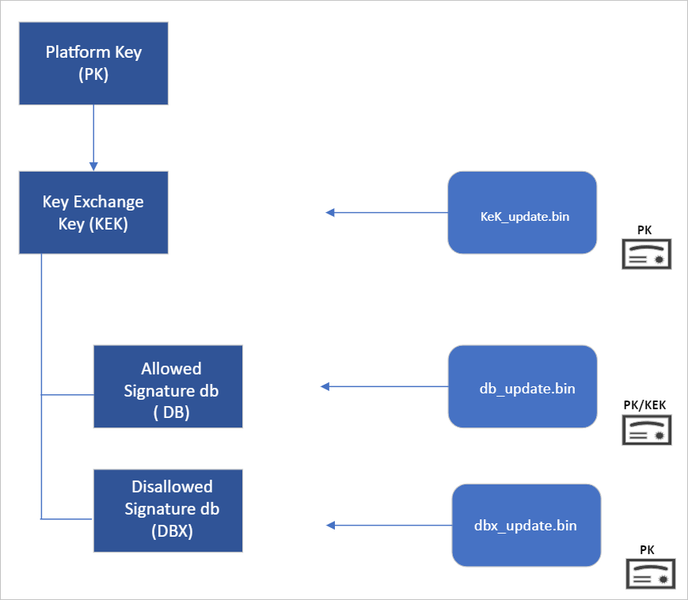
The new certificates were released as an optional Windows update this week, and Microsoft will roll out the update in phases to all Windows systems throughout the year, starting in April.
Before applying the update, Microsoft has recommended that users and enterprise customers back up BitLocker keys. This will come in handy to decrypt the hard drive later on if the certificate rotation fails.
We must say, we're impressed Microsoft has taken such an early approach to rotating the certificates. As how bad things have been at Microsoft lately, we were totally expecting they'd leave this until the last moment.
Breaches, hacks, and security incidents
Varta cyberattack: Battery maker Varta has shut down production at five factories in the aftermath of a cyberattack. The incident took place this week on February 12 and also hit the company's administrative network. The company says it disconnected the affected networks from the internet while it investigates the incident.
US Internet Corp leak: A Minnesota-based ISP named US Internet Corp has leaked years' worth of internal messages and customer emails. The leak originated from the company's Securence secure email service. [Additional coverage in KrebsOnSecurity]
BMW leaky server: And speaking of misconfigured leaky servers, BMW had its own incident, too. [Additional coverage in TechCrunch]
Facebook Marketplace data: A well-known threat actor has leaked a database containing what appears to be scrapped data from Facebook Marketplace users. The database holds more than 200,000 records on more than 20,000 accounts.
General tech and privacy
Exchange Extended Protection: Microsoft has enabled the Extended Protection feature on Exchange email servers by default. The feature was initially announced in August of last year. The feature is designed to bind authentication and TLS data to protect Exchange servers from man-in-the-middle (MiTM) type attacks.
Freenom exits domain business: Domain registrar Freenom has announced its exit from the domain name business. The company previously halted domain registrations in March 2023 after it was sued by Facebook's parent company, Meta. Meta accused Freenom of failing to act on abuse requests and profiting from trademark infringement. [via Brian Krebs]
Apple Vision Pro privacy: Apple has published a PDF document describing the privacy features of its newly launched Vision Pro VR headset.
Apple's EU bitterness: Apple is still bitter it had to give up its iPhone/iOS cash cow in the EU, and the company is now silently breaking all iOS web apps... but in the EU only. [Additional coverage in The Verge]
Abusive data trader exposed: Senator Ron Wyden (D-Oregon) has asked the FTC and SEC to investigate a data broker named Near Intelligence for selling the location data of Americans who visited abortion clinics. Wyden says the data was bought and used by anti-abortion groups to target clinic visitors with misinformation. The US senator says the company should be investigated for making misleading statements about how it handles collected data.
X caught hosting terrorist groups: Privacy researchers have spotted well-known terrorist organizations running Twitter accounts and paying for official checkmarks to boost their reach. But don't worry y'all. Twitter Support is extremely quick to ban journalists' accounts if they write something bad about Musk or Tesla. [Additional coverage in the New York Times]
WhatsApp misinformation: Meta has reduced payments to organizations that fact-check WhatsApp misinformation. The development comes just months before elections are set to take place in tens of countries around the globe. [Additional coverage in The Information] It comes as Meta also fired most of its Facebook election team, cutting staff from 300 to 60. The move is a trend across all major social networks, which appear to have embraced their kingmaker roles. [Additional coverage in the Washington Post]
DSL is back: The Damn Small Linux distro is back with a new version after more than a decade.
Chrome hardware sandbox: Google engineers are looking at the possibility of adding a hardware-based sandbox for Chromium's V8 engine. This is only an exploratory document and might not make it in due to various hardware configurations the browser might need to run.
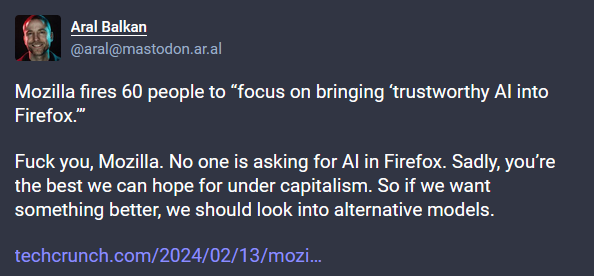
Mozilla layoffs: Mozilla has laid off 60 employees, roughly 5% of its workforce. The layoffs primarily affect the company's product development departments. The company is scaling back work on its VPN, Relay, and Online Footprint Scrubber products. The company says it will refocus development efforts on its mobile browser but also on bringing "trustworthy AI" into Firefox. [Additional coverage in Bloomberg, TechCrunch]
Government, politics, and policy
Estonia intelligence report: After Norway, Estonia's foreign intelligence service has also published its annual intelligence report.
Underage cybercrime: An NCA report claims that one in five British kids is involved in some form of cybercrime online. That's quite the number.
Pegasus in Poland: Polish Prime Minister Donald Tusk says he has obtained official documentation confirming that the country's previous government extensively used the Pegasus spyware. Tusk says the former government targeted a "very long" list of targets. The list is much larger than previous reports, and most targets were opposition politicians. Tusk described the hacking campaign as "illegal." Poland's previous government was led by the right-wing Law and Justice (PiS) party. [Additional coverage in the Associated Press and Gazeta.pl]
South Korean President Office hack: South Korea says North Korean hackers breached the email account of at least one employee of the President's staff. The hack took place ahead of President Yoon Suk Yeol's trip to Europe in November of last year. South Korean officials blamed the hack on the employee, who allegedly used a commercial email service for official duties. [Additional coverage in the Associated Press]
Albania's INSTAT hack attribution: Albania's cybersecurity agency has accused Iranian authorities of a cyberattack that hit its Institute of Statistics at the start of February. Officials say a group named Homeland Justice was behind the intrusion. The group deployed malware on more than 40 computers and successfully wiped data on six. The same group also hit the Albanian Parliament in December of last year and multiple other Albanian government agencies in June of 2022.
DOD breach: The US Department of Defense is notifying roughly 26,000 current and former employees that their data was exposed in a cybersecurity breach. The agency says it exposed employee records on the internet via an unsecured server. Employee data was exposed for more than two weeks in February 2023. [Additional coverage in DefenseScoop]
HUDOC ruling on E2EE: The European Court of Human Rights (ECHR) has ruled that weakening end-to-end encryption undermines basic human rights. The ruling came in a case filed by a Russian national against the Russian government, which tried to force Telegram in 2017 to decrypt the user's encrypted messages as part of an anti-terrorism case. EU MP Patrick Breyer says the ruling may have an impact on the EU's current attempts to force instant messaging providers into weakening encryption. It remains to be seen. [Additional coverage in ArsTechnica]
Russia wants to block anonymous Telegram channels: Members of the Russian Duma are working on new legislation that will force Telegram channel owners to register with the government and obtain a license to post. Officials say Telegram channels that do not register will be blocked. Despite the legislative effort, officials confirmed the government does not yet have the technology to enforce the law if approved. [Additional coverage in URA]
India moves to block ProtonMail: The Indian government has started procedures to block access to the ProtonMail service after an email address registered on the service was used to send bomb threats. At least thirteen private schools in Chennai received threats, according to officials. [Additional coverage in Hindustan Times]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Proofpoint Senior Threat Researcher Greg Lesnewich. Greg explains how a North Korean group is using DMARC spoofing in its efforts to gather strategic intelligence.

Cybercrime and threat intel
Pig butchering scams: Tenable's Satnam Narang has published a two-part series on the basics of pig butchering scams.
Utility scam campaign: Malwarebytes has tracked a network of Google ads promoting utility scams. These are malicious ads where threat actors pretend they're your local utility company in attempts to hijack payments when users search for their utility provider's payment page via Google.
WiFi jamming: Police in Minnesota suspect house thieves are using WiFi jammers to knock out home security systems and security cameras during burglaries. [Additional coverage in KARE11]
Finger abuse: Huntress has confirmed (again) that threat actors are using the Finger.exe utility for covert data exfiltration from compromised environments.
North Korean IT workers: North Korean IT workers based out of China are developing illegal gambling sites for South Korean crime syndicates, according to South Korea's intelligence agency. Besides profiting from selling the sites, the IT workers have also been spotted planting malicious code on the sites and then selling the collected user data.
Meta disrupts commercial surveillance operations: Meta has suspended Facebook and Instagram accounts used by eight commercial surveillance vendors. This includes accounts belonging to Italian companies Cy4Gate, RCS Labs, IPS Intelligence, and Negg; Spanish companies Variston, TrueL IT, and Mollitiam Industries; and UAE-based Protect Electronic Systems. Meta says some of the companies were using the accounts to test exploits and detections for malicious links. Others were either scraping data on Meta users or using IP-logging links to gather intelligence on possible targets. [Report/PDF]
Quarterly reports: HP Wolf Security, Picus Security, and NBIP have published their quarterly threat reports—if you're looking to spot some recent malware and DDoS attack trends.
Malware technical reports
Qakbot: In a Mastodon thread, Sophos researchers take a look at a recent Qakbot campaign, another sign the malware botnet appears to have returned to its full strength after last year's takedown.
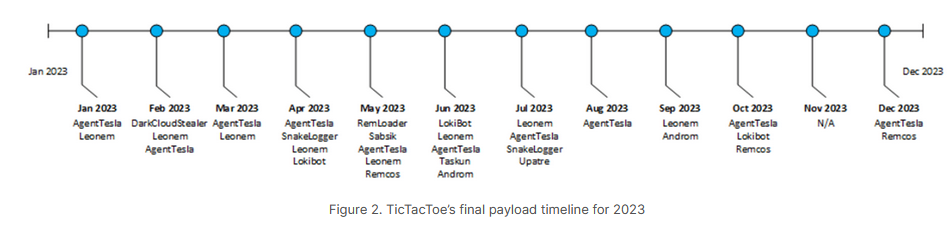
TicTacToe: Fortinet researchers published a report on TicTacToe, a new dropper that appeared in January 2023 and has been used to deploy various payloads across different campaigns.
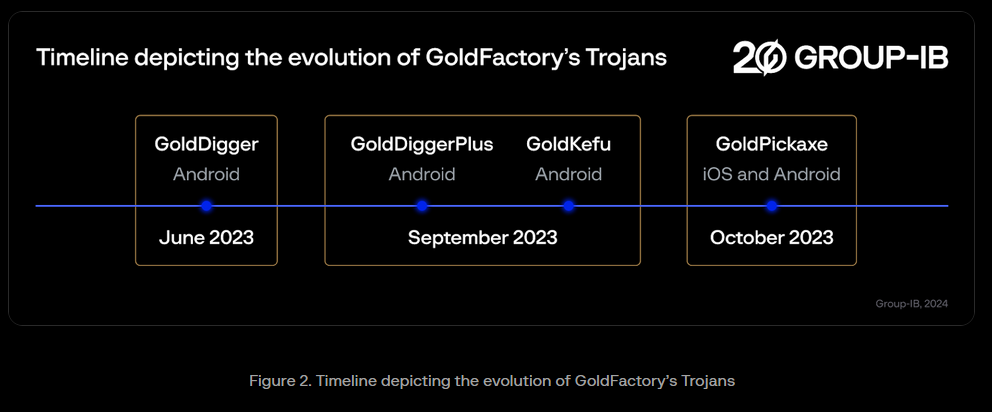
GoldPickaxe: Group-IB researchers have discovered a new iOS trojan that can collect facial scan data from infected devices in case it needs to bypass facial recognition authentication systems. Named GoldPickaxe, the trojan has been distributed in the wild since late 2023. It is being distributed through Apple's TestFlight feature or by social-engineering victims to install a malicious MDM profile. Group-IB says the trojan was developed by a Chinese-speaking cybercrime group named GoldFactory. The same group also developed the GoldDigger Android banking trojan. The group has a history of targeting the users of Thai and Vietnamese banks.
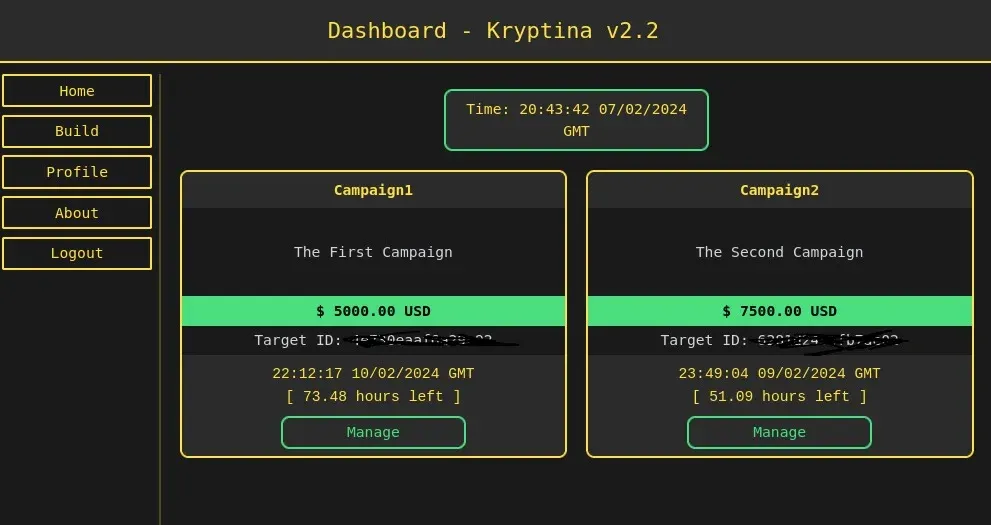
Kryptina ransomware: SentinelOne looks at Kryptina, a RaaS platform that targeted Linux systems. The platform launched in December 2023, but its developer leaked its source code on a hacking forum earlier this month.
Sponsor Section
Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view.
APTs, cyber-espionage, and info-ops
Kimsuky: AhnLab looks at a Kimsuky spear-phishing campaign targeting South Korea and delivering the AppleSeed and AlphaSeed backdoors.
APT groups abuse AI: Microsoft and OpenAI have disrupted five APT groups using their AI tools for cyber operations. The two companies took action against two Chinese groups and APTs from Russia, Iran, and North Korea, respectively. Microsoft and OpenAI say the groups used their AI tools to research and translate content for phishing campaigns, for automation, to understand vulnerabilities, and to research new malware evasion techniques. The APT groups include Kimsuky, Tortoiseshell, APT28, APT4, and RedHotel.
- Charcoal Typhoon used our services to research various companies and cybersecurity tools, debug code and generate scripts, and create content likely for use in phishing campaigns.
- Salmon Typhoon used our services to translate technical papers, retrieve publicly available information on multiple intelligence agencies and regional threat actors, assist with coding, and research common ways processes could be hidden on a system.
- Crimson Sandstorm used our services for scripting support related to app and web development, generating content likely for spear-phishing campaigns, and researching common ways malware could evade detection.
- Emerald Sleet used our services to identify experts and organizations focused on defense issues in the Asia-Pacific region, understand publicly available vulnerabilities, help with basic scripting tasks, and draft content that could be used in phishing campaigns.
- Forest Blizzard used our services primarily for open-source research into satellite communication protocols and radar imaging technology, as well as for support with scripting tasks.
Turla in Poland: Russian APT group Turla has conducted a cyber-espionage campaign targeting Polish non-governmental organizations. Turla targeted NGOs working on improving Polish democracy and supporting Ukraine during the Russian invasion, according to Cisco Talos. Initial attacks launched in November of last year and used a new backdoor named TinyTurla-NG.
US takes down GRU botnet: The US government has disrupted a botnet of SOHO routers operated by APT28, a cyber unit inside Russia's military intelligence agency. The botnet consisted of Ubiquiti Edge OS routers that still used default passwords. The routers were infected by the Moobot cybercrime group before GRU operators leveraged the same malware to deploy their own scripts to repurpose the botnet for their own operations. US officials say APT28 used the botnet to disguise the origin of spear-phishing and other credential-harvesting campaigns. The Justice Department and the FBI say they have taken control of Moobot infrastructure and removed the malware from infected routers. They also deployed firewall rules on the compromised routers to prevent remote management access to the devices.
China and Russia silent on each other's APT ops: Russian foreign and cyber policy expert Oleg Shakirov has published an analysis of how Chinese and Russian cybersecurity firms and governments deal with each other's cyber-espionage operations. The long story short is that they're very much aware of the deluge of operations taking place, but they don't call each other out, focusing on crying about the rare cyber ops they manage to link to the big bad West.
"Both Russia and China are ambiguous about public attribution of cyber attacks. They dismiss Western accusations as baseless and politicized. Yet both countries respond with their own accusations against the United States, essentially engaging in quasi-attribution: for several years, China has been referring to the United States as the 'Empire of Hacking,' while Russian officials claim that the the US Cyber Command as well as other Western agencies coordinate Ukrainian hackers attacking Russia."
VOLTZITE (Volt Typhoon) expands to Africa: Chinese APT group Volt Typhoon has expanded operations in African countries. Industrial cybersecurity firm Dragos has seen the group (which it calls VOLTZITE) target electric transmission and distribution organizations in African nations. In addition, the group has also expanded operations inside the US. After initial attacks on the US defense industrial base and telcos, Dragos says recent Volt Typhoon operations have also targeted organizations in the emergency and satellite services.
SameCoin campaign: A suspected Hamas threat actor is targeting Israeli citizens and organizations with a new data wiper named SameCoin, according to reports from Intezer and Harfang Lab. The campaign spoofs messages from Israel's National Cyber Directorate and urges users to install boobytrapped security updates. The malware has Android and Windows versions and is unique because, before wiping systems, it shows anti-war and anti-Netanyahu propaganda videos. Researchers believe the SameCoin campaign is a new version of HamsaUpdate, a campaign linked to a threat actor known as HandalaHack.
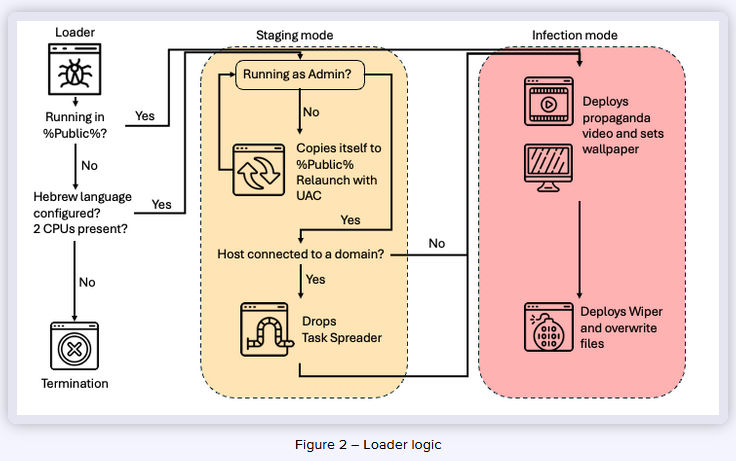
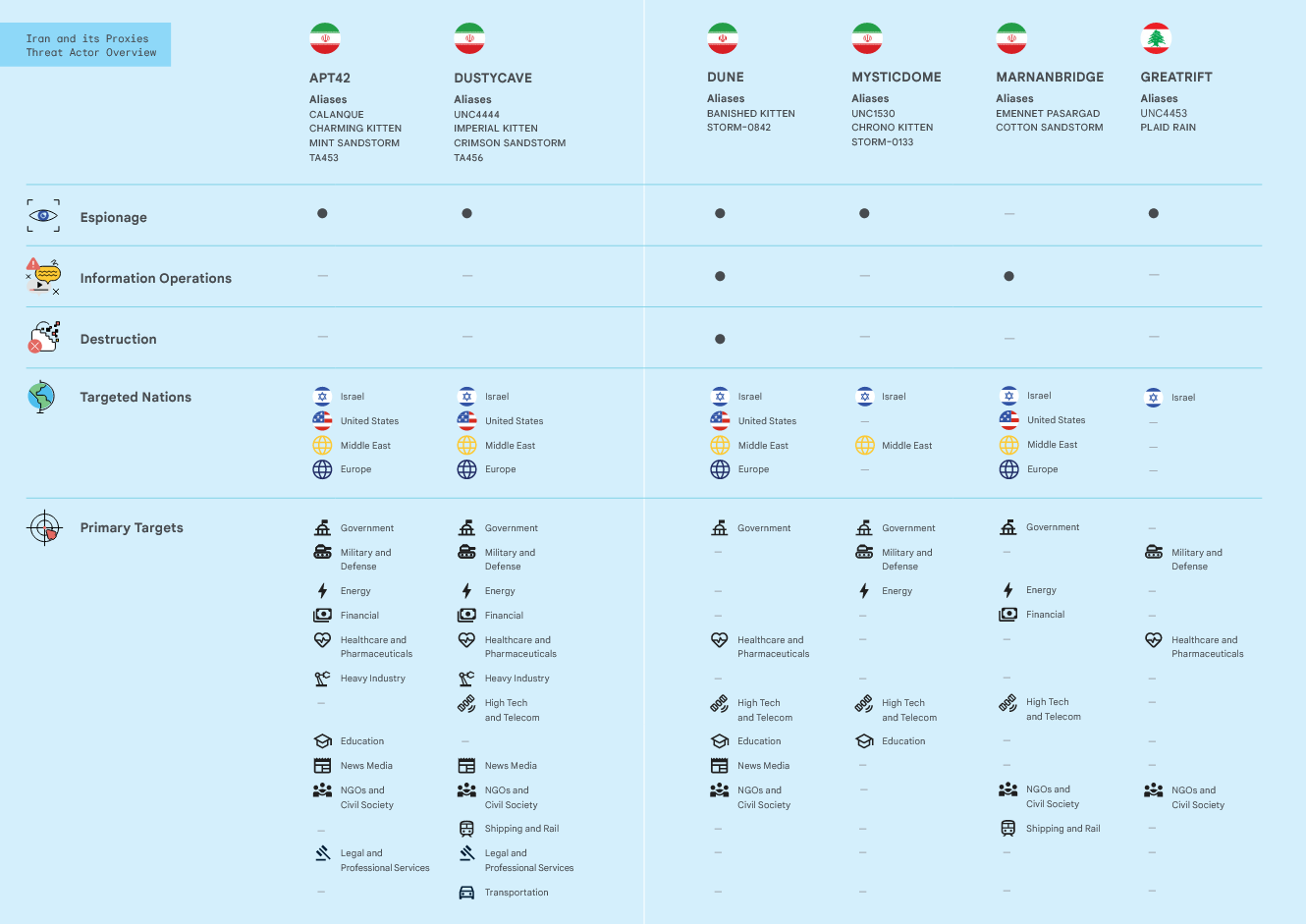
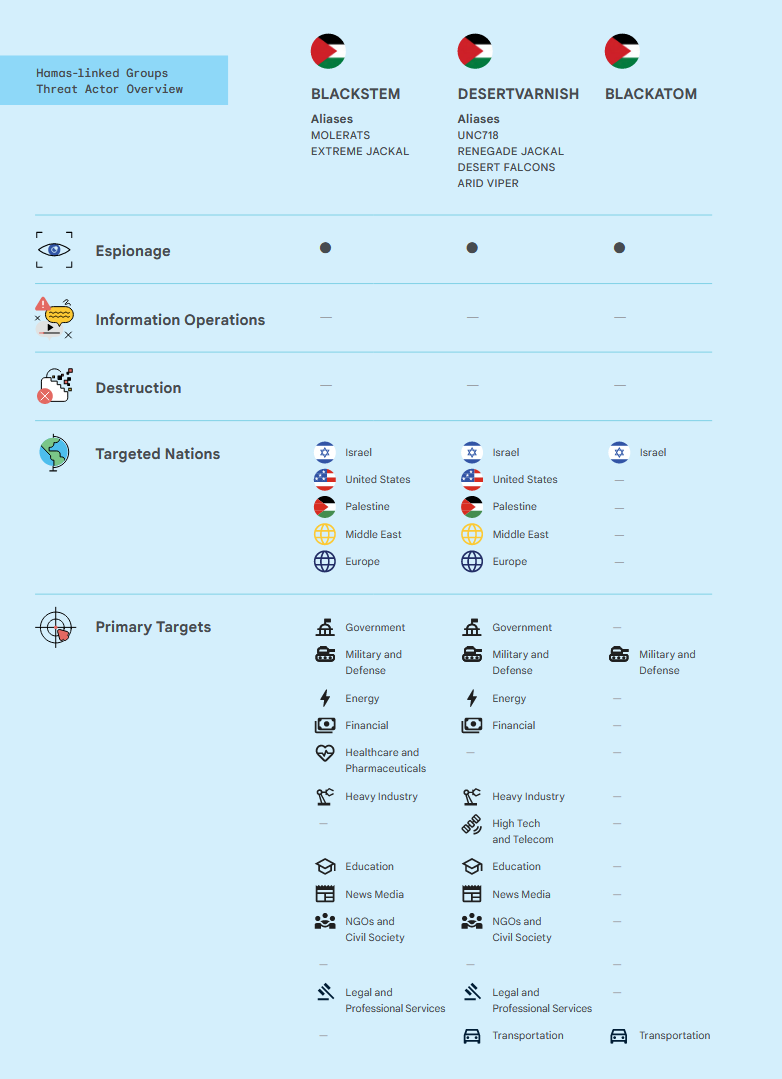
Iran and Hamas cyber activity: Google's TAG and Mandiant divisions have published a joint report [PDF] on its view of Iranian and Hamas APT operations before and after the October 7 attack. It follows a similar report from Microsoft. The most interesting part of the report is a section on BlackAtom, a suspected Hamas group that was using social engineering to lure Israeli software engineers from the military, aerospace, and defense industries to apply for freelance jobs. The final payload was the SysJocker malware, which Check Point had tied to Palestinian APT group Gaza Cybergang.
Vulnerabilities, security research, and bug bounty
Exchange zero-day: Threat actors are exploiting a Microsoft Exchange zero-day to execute NTLM relay attacks and elevate privileges in compromised networks. Microsoft patched the zero-day in this month's Patch Tuesday but did not disclose the attacks until a day after the fix rolled out. Tracked as CVE-2024-21410, the vulnerability is the third zero-day patched in this month's security updates. Evidence suggests Microsoft's security staff might have forgotten to update the vulnerability's exploitation status before the Patch Tuesday updates rolled out. Microsoft tried to correct the mistake a day later but accidentally marked an Outlook bug as exploited instead of the Exchange one before correcting the issue in one big mess. [h/t Simon Tsui]
MonikerLink: And speaking of that Outlook bug (CVE-2024-21413), that's actually a vulnerability that was discovered by Check Point's Haifei Li. The researcher named it MonikerLink, and a technical write-up is available here.
KeyTrap: A team of academics has discovered a vulnerability that can be exploited to take down DNS servers. Named KeyTrap (CVE-2023-50387), the vulnerability can exhaust CPU resources on DNS servers and stall domain name lookups. Exploitation requires only one malicious packet, and some DNS server software can be stalled for as long as 16 hours. Microsoft, BIND, PowerDNS, and most of the major Linux distros have released KeyTrap patches. [h/t Royce Williams]
Ubuntu command-not-found abuse: Cloud security firm Aqua details how Ubuntu's command-not-found utility could be abused to recommend malicious packages.
"[O]ur research indicates that as many as 26% of commands associated with APT (Advanced Package Tool) packages are vulnerable to impersonation by malicious actors. This issue could pave the way for supply chain attacks affecting Linux users and Windows running WSL."
Security Alliance: A group of blockchain security researchers have launched the Security Alliance, an NGO for white-hat hackers dedicated to securing and recovering stolen crypto assets.
WiFi software vulnerabilities: Security researchers Mathy Vanhoef and Héloïse Gollier have discovered vulnerabilities in WiFi software libraries that can allow attackers to bypass WiFi authentication. The authentication bypass attacks work on WiFi security standards WPA2 and even the more secure WPA3. The vulnerabilities impact open-source WiFi network management software wpa_supplicant (CVE-2023-52160) and Intel's iNet Wireless Daemon (IWD) (CVE-2023-52161). wpa_supplicant is used as the default WiFi client on all Android devices and some major Linux distributions. It is also used on ChromeOs. IWD is available as an optional package for most Linux distributions.
Mastodon security update: Mastodon has released a security update to patch an account takeover bug via the change email functionality.
Infosec industry
Nginx fork: A Russian developer on the Nginx web server software has forked the project as Freenginx. The developer claims corporate interference from F5, the project's new owner. The move also comes after Russian authorities have urged Russian software developers to create local alternatives of popular open-source projects, decoupled from "Western interference," in a move similar to what has been happening in China over the past years. (e.g., Gittee instead of GitHub, the Kylin version of Linux, etc.)
Tool update—capa: Mandiant's latest capa version now integrates with Ghidra.
Industry moves: GreyNoise has hired Ash Devata as its new chief executive officer. Devata replaces GreyNoise founder Andrew Morris, who served as CEO since the company's launch in 2018. Devata joins from Cisco, where he served as vice president and general manager of the Duo and Zero Trust divisions.
Cisco layoffs: Cisco has announced plans to lay off more than 4,200 employees, amounting to roughly 5% of its workforce. It's unclear if the layoffs will affect any of the Cisco cybersecurity divisions, such as Talos, Splunk, Duo, and others. [Additional coverage in CNBC]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about what up-and-coming countries should expect from a Cyber Command and whether they should invest in it.





