Risky Bulletin: CA/B Forum approves 47-days TLS certs
In other news: China puts up reward for three NSA hackers; ransomware attack disrupts dialysis clinics; 4chan hacked.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
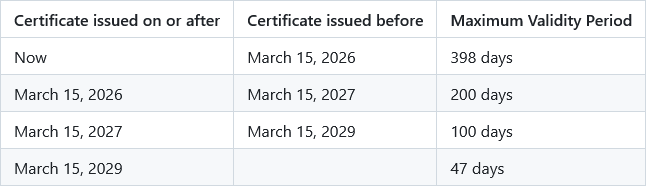
The CA/Browser Forum passed a ballot to reduce the maximum validity of TLS certificates from the current 398 days to just 47 days by 2029.
The ballot passed without opposition, with 28 votes in favor and five abstainers.
The reduction will take place across three phases between March next year and March 2029.
The maximum lifespan of a TLS certificate will be reduced to 200 days next March, 100 days in March 2027, and finally to 47 days for all certificates issued after March 15, 2029.
The ballot is basically a slightly altered version of an Apple proposal from last October that sought to reduce maximum certificate lifespans to 45 days by 2027. The difference is that the new proposal gives certificate authorities (CAs) two extra years to prepare their infrastructure for super-short TLS certs.
As The SSL Store points out, once this goes live, companies will have to rotate TLS certificates for their servers about eight times each year.
Unless CAs migrate to highly automated renewal processes, this will be a giant hassle for their customers going forward—and very likely why CAs asked for the extra two years on top of Apple's original proposal.
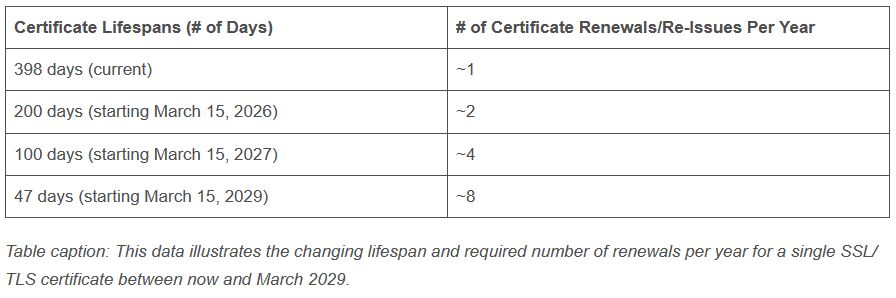
This is the fourth time that the maximum lifespan of TLS certificates is changed. TLS certs went from 5-year validity periods to three, two, and then one.
All of these efforts have been spearheaded by browser makers, who have had to deal with misbehaving CAs and long-lived certificates that nobody bothers to revoke.
In 2023, Google tried to have certificates reduced to 90 days, but its proposal was defeated following pushback from CAs, which argued they weren't ready on the infrastructure side to support such short lifespans.
When Apple proposed its even shorter TLS certificate lifespans last year, the CAs knew it was over and that short-lived TLS certs were here to stay.
That's because, in 2020, Apple unilaterally decided to support one-year TLS certificates on its devices. If CAs wanted their customers to load content on Apple systems, they had to abide by Apple's new rules.
The other (happy) browser makers and the (grumbling) certificate authorities followed suit, but Apple effectively brought the current 398-day certs into existence.
Apple went through the proper procedures this time around, but the writing has been on the wall for CAs for some time, with browser and OS makers constantly pushing the TLS industry to automate procedures and support shorter TLS certs for the sake of security.
In the TLS industry, the big dogs, like Sectigo and Digicert, are pretty happy about this change. The bigger players like them have had the resources to put into automating TLS issuance procedures, and they now see the perfect opportunity to steal customers from the smaller market players.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and former NSA cybersecurity director Rob Joyce.
Breaches, hacks, and security incidents
Crosswalk buttons hacked in Silicon Valley: A suspected hacktivist hacked traffic control crosswalk buttons across Silicon Valley. The hackers altered the devices to play AI-generated audio snippets with the voices of Mark Zuckerberg and Elon Musk. The audio snippets played from Friday to Saturday until they were removed by authorities. [Additional coverage in TechCrunch]
@keagan.19 Menlo Park, home of meta, crosswalk speakers are getting hacked… @Mark Zuckerberg
♬ original sound - Keagan B
Ransomware attack disrupts dialysis provider: A ransomware attack is impacting the activity of DaVita, a major provider of kidney care and dialysis services in the US. The attack encrypted some systems but patient care continues. The company couldn't say when it would fully recover. DaVita is a Fortune 500 company. It operates over 3,000 clinics, provides services to over 760 hospitals, and treats over 200,000 patients every year. [Additional coverage in The Record]
Ukrzaliznytsia only half-recovered after cyberattack: Ukraine's national railway says it restored half its systems following a suspected Russian data wiper attack that took down IT systems last month. [Additional coverage in CyberDaily]
KiloEx crypto-heist: Cryptocurrency exchange KiloEx lost $7 million worth of assets after an attack on Monday. The attacker allegedly exploited a vulnerability in the platform's price oracle system. The attackers exploited Tornado Cash, a service that had sanctions lifted by the US. [Additional coverage in CoinDesk]
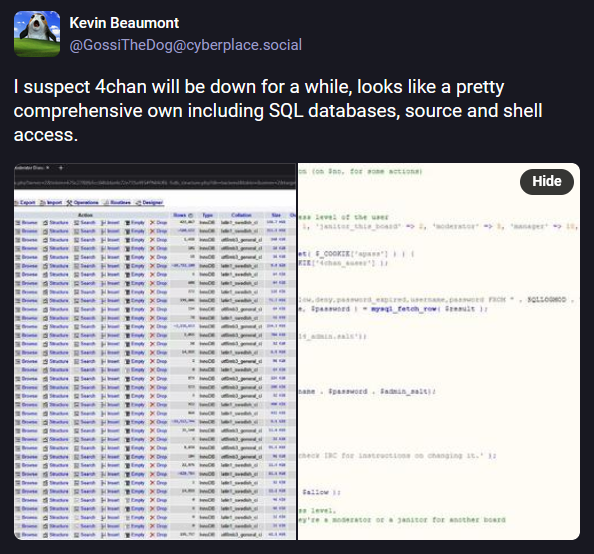
4chan hacked: Hackers have breached controversial internet forum 4chan. The attackers leaked some of the site's source code and posted images of the site's backend and database page. 4chan has not confirmed the breach, but the site was offline all day on Tuesday. The hack was announced on a rival forum named Soyjak Party. This is 4chan's second major breach after a similar incident in 2014.
General tech and privacy
German govt urges Windows 10 migration: The German government has told consumers to migrate away from Windows 10, as the OS is set to reach EOL on October 14, this fall.
Meta to train AI on EU user data after all: Meta will use EU user data to train its AI models after delaying the process for over a year due to the bloc's regulatory concerns. Following negotiations with Ireland's privacy regulator, Meta says it will only use public data to train its models. This includes public posts and any interactions with Meta's existing AI chatbots. EU users will be notified of the change in the coming days, and they can still opt out.
Japan accuses Google of monopoly: The Japanese market regulator has ordered Google to stop abusing its control of Android devices to favor its Search and Chrome apps on mobile smartphones. [Additional coverage in The Asahi Shimbun]
Tate exodus to right-wing platforms: Open Measures looks at how Andrew Tate found a new home on right-wing platforms such as Gettr, Gab, and Truth Social after being deplatformed from YouTube and Meta in 2022.
Google domain redirection: Google says that all its country-level domains will start pointing to its main google.com domain in the coming months. The company says it can now provide "localized" search results through the main site, so the local versions of Google are no longer necessary.
Android auto-restart for locked devices: The feature that restarts Android devices that have been locked for more than 72 hours is now live in the Google Play services. This is part of a broader set of Lockdown Mode features for Android coming later this year.
Government, politics, and policy
Russia looks to ban citizens from mobile services: A proposed Russian law would ban telcos from signing contracts or issuing SIM cards to citizens on government fraud blacklists. [Additional coverage in PNP]
Russia approves crypto seizure procedures: The Russian government has approved a procedure for seizing cryptocurrency linked to criminal activity. They seized crypto before but through longer and theft-prone processes. [Additional coverage in RBC]
Queensland new data breach law: Australia's Queensland region has a new privacy law (IPOLA) that comes into effect on July 1 and which includes a mandatory data breach notification requirement. [Additional coverage in Ashurst]
EU confirms issuing burner phones: Following an FT report, an EU representative confirmed that the bloc provides burner phones to diplomats traveling to the US but said the practice has been long-standing and is not specific or related to the current US leadership. [Additional coverage in The Record]
NATO VCISC: NATO held a cyber exercise earlier this month in Czechia to test its members' ability to respond to major cyber events.
New encryption backdoor law: The EFF is raising the alarm about a new Florida bill that would mandate encryption backdoors for the sake of "child safety."
DOGE accessed unrelated data and hid its tracks: An NPR investigation found that DOGE staff accessed data unrelated to government efficiency efforts at the US National Labor Relations Board, such as legal cases and corporate secrets, and then covered its tracks to hide its actions.
Here's DOGE behaving like an APT or Scattered Spider
— Catalin Cimpanu (@campuscodi.risky.biz) 2025-04-15T13:16:03.784Z
Sponsor section
In this Risky Bulletin sponsor interview, David Cottingham and Peter Baussman, Airlock Digital’' CEO and CTO, talk to Tom Uren about a new Australian Cyber Security Centre guidance about building defensible networks. The pair cover what they like about the document and where it could be improved.
Arrests, cybercrime, and threat intel
Ukraine arrests hackers who breached govt systems: Ukraine's cyber police detained four suspects for hacking into government systems and removing encumbrances from private properties. The scheme aimed to remove restrictions from properties so they could be reregistered for other purposes. Most of the reregistered property was in Kyiv's forest belt region. Officials say the group advertised their service online, and one of the four suspects was a private executor.
Insured companies pay larger ransoms: Companies with cyber insurance pay almost 2.8 times bigger ransoms than non-insured organizations. According to a Dutch Police study, ransomware gangs often look for documents that mention terms like insurance and policy before deciding on the ransom's value. Proper backups were found to be the best defense against ransomware and big extortions. The same study also found that in 95 out of 100 cases, companies were forced to pay the ransom or go bankrupt.
Rise in Node.js abuse: Microsoft's DEX security team looks at the increasing use of Node.js to deliver and run malware on infected systems.
LOTS phishing campaign: Abnormal Security looks at a phishing campaign that uses the LOTS (living-off-trusted-sites) technique to hide parts of its infrastructure on trusted websites, such as Cloudflare, Canva, Lucidchart, and Figma. This campaign also weaponizes Gamma, a relatively new AI-based presentation tool, to deliver a link to a fraudulent Microsoft SharePoint login portal.
Malicious WhatsApp apps: Russian security firm Dr.Web has discovered a cluster of malicious Android apps posing as WhatsApp that infect users with malware that hijacks their clipboard. The malware is designed to intercept and replace cryptocurrency addresses to hijack crypto-wallet transactions. Dr.Web says the attackers run a large cluster of over 60 C&C servers. So far, the group has stolen over $600,000, with one wallet alone gathering over half of the stolen crypto-assets.
Malware technical reports
New PasivRobber macOS spyware: Kandji researchers have discovered PasivRobber, a new spyware strain designed to target macOS systems and steal data from Chinese apps, browsers, and email clients.
New ResolverRAT: Morphisec has identified a new remote access trojan used in the wild named ResolverRAT.
"ResolverRAT is a newly identified remote access trojan that combines advanced in-memory execution, API and resource resolution at runtime, and layered evasion techniques. Morphisec researchers have coined it 'Resolver' due to its heavy reliance on runtime resolution mechanisms and dynamic resource handling, which make static and behavioral analysis significantly more difficult."
New Storm-1811 backdoor: ReliaQuest looks at a new PowerShell-based backdoor used by Storm-1811, a known ransomware affiliate. The report also looks at a new, previously unreported persistence method that leverages TypeLib COM hijacking.
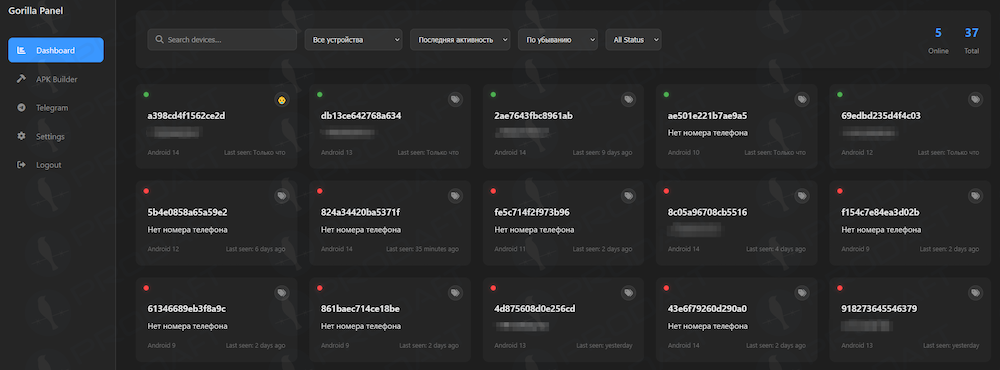
New Gorilla banking trojan: Prodaft has published a report on Gorilla, a Kotlin-based Android banking trojan.
"Gorilla appears to be in an early stage of development, as evidenced by its lack of obfuscation, excessive logging, and unused classes. However, it already implements several stealthy techniques, such as bypassing permission restrictions for installed app enumeration and adjusting its heartbeat intervals for specific manufacturers. Future versions may introduce additional capabilities, such as phishing attacks via WebView or novel persistence mechanisms using USSD codes."
Sponsor section
In this product demo of the Airlock Digital application control and allowlisting solution, Patrick Gray speaks with Airlock Digital co-founders David Cottingham and Daniel Schell.
APTs, cyber-espionage, and info-ops
China offers reward for NSA employees: Chinese authorities have blamed the NSA for cyberattacks against the Asian Winter Games held in the city of Harbin this year. Authorities claim the NSA used front companies to rent servers that attacked the Games' digital infrastructure, seeking to steal participants' personal data. They also claim the NSA tried to use "unknown encrypted data packets" to activate backdoors installed on Windows systems across the region. Harbin police named three NSA employees responsible for the attack—Katheryn A. Wilson, Robert J. Snelling, and Stephen W. Johnson. They also claim they have evidence the University of California and Virginia Tech aided the NSA in the attack. An Antiy report published on the same day appears to describe the supposed attack. China has provided little evidence to support its claims, and the White House has described them as fabricated. [Additional coverage in China Daily/English coverage in Xinhua]
APT29's WineLoader campaign: Check Point looks at an APT29 phishing campaign from January that targeted diplomatic entities across Europe with the WineLoader malware.
DAMASCENED PEACOCK: The UK's cybersecurity agency has published a technical report on DAMASCENED PEACOCK, a Windows malware downloader observed during a spear-phishing campaign in late 2024 targeting the UK Ministry of Defence. The malware is likely the work of an APT group. [Report PDF]
UNC5221's BRICKSTORM: NVISO has published a technical report on BRICKSTORM, a backdoor deployed by a Chinese cyber-espionage group named UNC5221 against European organizations since 2022.
UNC5174: Sysdig has identified new C&C infrastructure used by a Chinese APT tracked as UNC5174.
Earth Bluecow's new BPFDoor attacks: Trend Micro has spotted new attacks with the stealthy and mysterious BPFDoor backdoor. The new attacks targeted the telecommunications, finance, and retail sectors in South Korea, Hong Kong, Myanmar, Malaysia, and Egypt. The company attributed this campaign to a group, for the first time, namely Earth Bluecrow.
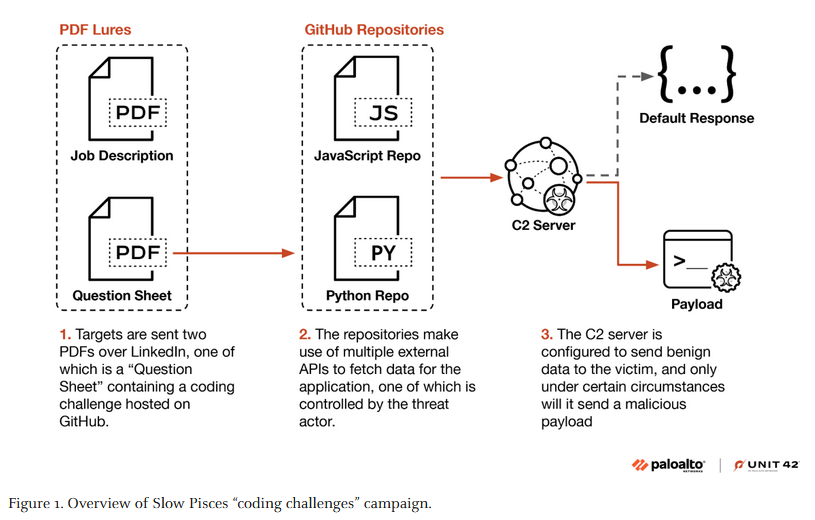
Slow Pisces: Palo Alto Networks looks at Slow Pisces, a North Korean state-sponsored threat group also known as Jade Sleet, TraderTraitor, and PUKCHONG. The company looks at the group's recent campaign that targeted cryptocurrency developers on LinkedIn, posing as potential employers, and sending malware disguised as coding challenges.
Vulnerabilities, security research, and bug bounty
Waiting Thread Hijacking: Check Point security researcher Aleksandra "Hasherezade" Doniec has developed a new process injection technique named Waiting Thread Hijacking, an evolution of classic Thread Hijacking.
Major Apache Roller session bug: The Apache team has released a security update for the Roller blogging platform to patch a major vulnerability (CVE-2025-24859). The patch fixes a bug that leaves user sessions active even after a password change. This allows hackers who stole old cookies to access accounts without a password. The vulnerability has a severity rating of 10/10.
Oracle CPU: The quarterly Oracle security updates are out, with patches for 378 vulnerabilities.
Windows EoP write-up: Compass Security has published a technical write-up on CVE-2025-24076 and CVE-2025-24994, two Windows EoPs. Both were fixed in March.
MITRE's CVE contract ends this week: The MITRE Corporation has sent an email to partner organizations warning about possible disruptions to the CVE database. MITRE says its contract with the US government is set to expire on Wednesday, April 16. If the CVE database goes down, disruptions will impact the vast majority of cybersecurity vendors, vulnerability scanning tools, IR investigations, and more.
BREAKING. From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.
— Tib3rius (@tib3rius.bsky.social) 2025-04-15T17:23:48.000Z
Infosec industry
Threat/trend reports: ANY.RUN, BeyondTrust, Flashpoint, LayerX, and Privacy Journal have recently published reports and summaries covering various infosec trends and industry threats.
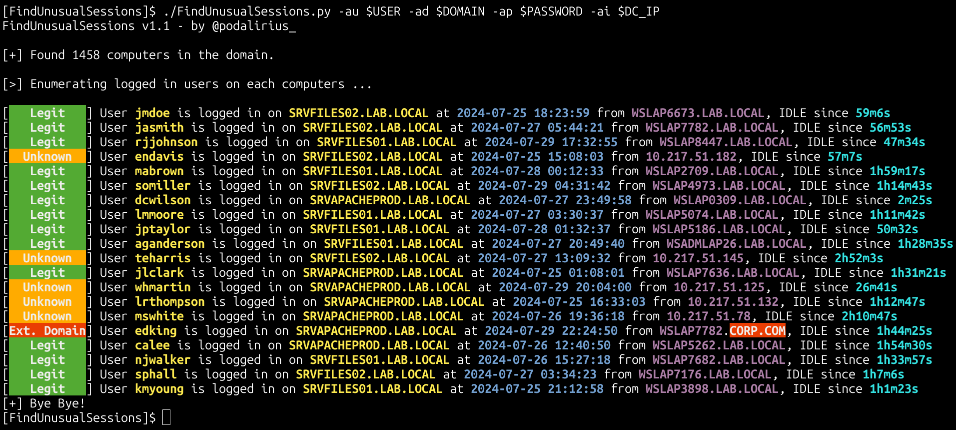
New tool—FindUnusualSessions: Security researcher Remi Gascou has open-sourced FindUnusualSessions, a tool to remotely detect unusual sessions opened on Windows systems.
Risky Business podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of global critical infrastructure. One common example is submarine cables, which are globally important but are vulnerable because they are hard to defend. But what about services from tech giants? Are they global critical infrastructure?
Tom Uren and Patrick Gray discuss Trump's recent firing of General Timothy Haugh, the head of NSA and Cyber Command. Tom dives into the implications and thinks why this is not good news for the agencies.




