Risky Biz News: Volt Typhoon returns with a new zero-day
In other news: Pentagon runs Tinder info-op; Seattle airport still crippled by major cyberattack; evolved malware can wipe security tools off a victim's disk.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Chinese cyber-espionage group Volt Typhoon has used a zero-day in a network virtualization server to breach the infrastructure of US ISPs and managed service providers.
The attacks began in June and are still ongoing, according to internet infrastructure company Lumen.
They target Versa Director [PDF], a type of server that allows companies to virtualize or segment their networks on a large scale—hence why its customers typically include large corporations, cloud providers, and internet service providers.
Lumen says Volt Typhoon used a zero-day (CVE-2024-39717) to upload a malicious web shell on a target's Versa Director server. Lumen named this web shell VersaMem because it ran in the server's memory to avoid detection and leaving clues of a hack on the device's disk.
Once inside the device's memory, Volt Typhoon used the access to intercept authentication processes to collect the credentials of IT staff logging into the device. These were later used to move laterally across their networks.
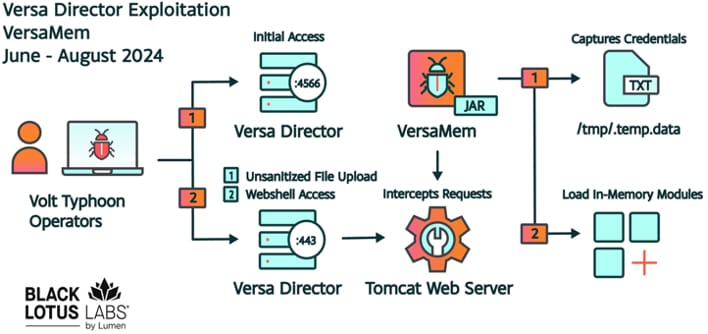
Lumen says the attacks are classic Volt Typhoon attacks that targeted US critical and telecommunications infrastructure for espionage purposes.
The attacks also came from SOHO routers located in the US, through a botnet designed to disguise the threat actor's real location. This, however, didn't fool Lumen since the company previously spent a lot of time mapping Volt Typhoon's mesh of SOHO routers.
The company says it notified Versa of the attacks and zero-day in July, with the company releasing a patch last week. Lumen says Versa treated the report with urgency and sent two private security advisories about the vulnerability and the attacks before a patch was even ready—in late July and then in early August.
Versa's panic on this may come from the fact that CISA and almost all US government cyber officials have been treating and speaking about Volt Typhoon as the next APT devil incarnate.
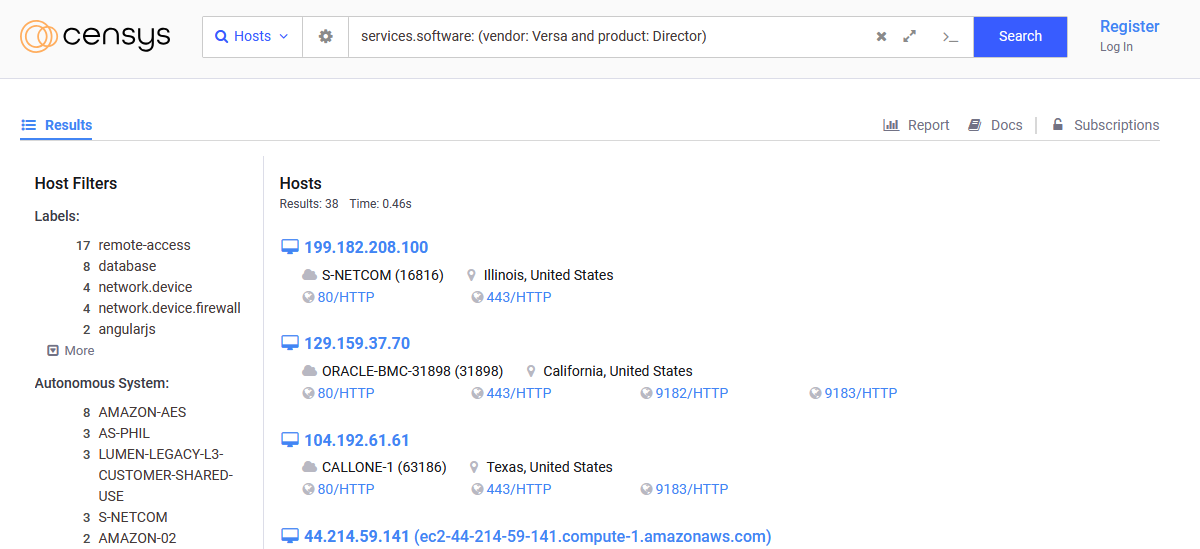
According to Censys, there are around only 150 Versa Director servers exposed online, but what's hiding behind those things is an intelligence gold mine. Ok... there were around ~150. They're now only 38 when we took this screenshot. People are either patching or putting those things behind firewalls. Message received, I guess.
Breaches, hacks, and security incidents
Seattle airport cyberattack: The Seattle-Tacoma International Airport was hit by a cyberattack over the weekend that impacted its website and phone systems. Some airport utilities, such as flight boards and WiFi access, were also affected. Airport staff were still dealing with the incident on Tuesday, four days after the initial intrusion. Officials did not provide any details about the nature of the attack. [Additional coverage in USA Today]
Exotel data breach: Customer service platform Exotel has suffered a data breach at the end of last week. The company says the incident only impacted a subset of its customers. Exotel provides voice and SMS customer support capabilities for businesses. [Additional coverage in Entracker]
TDECU data breach: More than a year after it was breached, the Texas Dow Employees Credit Union (TDECU) has finally sent letters to people who had their data stolen in the Clop gang's MOVEit hacking spree. Better late than never, I guess. The incident impacted more than 500,000 customers, per a regulatory filing.
ServiceBridge leak: Franchise management software maker ServiceBridge has leaked over 31.5 million records via an unprotected database. The database contained contracts, work orders, invoices, proposals, and more from companies worldwide.
Ransomware attack on Malaysia's rail network: Malaysia's national rail operator says trains are running on time after a ransomware attack hit its internal network last week. Prasarana says it's currently working with the country's cybersecurity agencies to investigate and recover from the attack. A ransomware gang named RansomHub took credit for the intrusion. The group claims to have stolen 316GB of data from the operator's network, which it plans to release this week unless a ransom is paid. [Additional coverage in FreeMalaysiaToday]
Timisoara ransomware attack: The Romanian city of Timisoara says it successfully blocked a ransomware attack that targeted the local government's IT network. The attack took place over the past weekend and targeted networks belonging to the city's town hall, police, and fiscal authority. Officials say all public services are operating as normal, and they are now rebuilding internal networks to throw out the attackers. Timisoara is Romania's fifth-largest city by population size.
Durov arrest DDoS attacks: Several hacktivist groups have launched DDoS attacks against what appears to be random French websites as "revenge" for the arrest of Telegram CEO Pavel Durov. Some of the groups involved in the attacks are pro-Kremlin hacktivists with known links to Russia's military and intelligence services. <s>Either way, the Union of the Peasant Confederation is devasted by the attack. We don't know how it will go on!</s> [Additional coverage in Le Parisien]
Ukraine hacks Russian TV stations: Ukraine's GUR military intelligence has hacked the servers of nine Russian TV channels to air more accurate reports about the war in Ukraine. The hack took place last week and hit TV channels like Eurasia, Pervouralsk TV, and Lugansk 24. GUR claims to have aired reports multiple times during primetime before they lost access to the live broadcast feed. The report detailed Ukraine's advances in Kursk and Russian troop losses. [Additional coverage in The New Voice of Ukraine and the Kyiv Independent]
General tech and privacy
Microsoft to meet with EDR makers: Microsoft will hold a private summit with EDR makers on September 10 to work on preventing a future CrowdStrike crash incident. The company plans to discuss new ways of building EDR products that rely more on the user mode and less on kernel drivers. Attendees will also discuss the adoption of eBPF technology and memory-safe programming languages such as Rust. Government representatives have also been invited to attend. [Additional coverage in CNBC]
Dutch DPA fines Uber: The Dutch Data Protection Agency has fined Uber €290 million for transferring the personal data of European taxi drivers to the US. Dutch officials say this was a clear violation of the EU GDPR rules. The same agency also fined Uber €10 million in February because Uber made it unnecessarily complicated for drivers to see how their data was used, shared, and where. Officials say they started an investigation into Uber's practices after receiving complaints from French drivers. The investigation took place in the Netherlands because Uber's EU headquarters are based there.
Telegram app review: Cryptographer Matthew Green goes over the Telegram app design and highlights how the app isn't really encrypted and chat encryption features are buried deep inside profiles on purpose.
"Most recently he issued a scathing criticism of Signal and WhatsApp on his personal Telegram channel, implying that those systems were backdoored by the US government, and only Telegram's independent encryption protocols were really trustworthy. While this might be a reasonable nerd-argument if it was taking place between two platforms that both supported default end-to-end encryption, Telegram really has no legs to stand on in this particular discussion. Indeed, it no longer feels amusing to see the Telegram organization urge people away from default-encrypted messengers, while refusing to implement essential features that would widely encrypt their own users' messages. In fact, it's starting to feel a bit malicious."
Durov charges: French authorities have published the official charges [PDF] against Telegram founder Pavel Durov.
CMG's Active Listening: After media companies and device vendors spent a decade telling customers that microphones baked into their devices aren't secretly recording audio, a leaked pitch deck from the Cox Media Group (CMG) is advertising a new service that can show ads to users based on what they've said near microphones. Google allegedly kicked CMG from its advertising program after 404 Media acquired the slide deck and asked Google to comment.
AI in police reports: The Oklahoma City Police Department is apparently using AI chat assistants to write crime reports. There are now fears these reports won't hold up in court. [Additional coverage in the AP]
Notion blocks Russian users: Productivity and note-taking app Notion has announced that following recent US sanctions, it will block Russian users from its platform on September 9.
Texas police surveillance: The Texas Department of Public Safety (DPS) has signed a five-year contract for Tangles, an AI surveillance tool that can track cell phone movements. The deal has alarmed privacy advocates as the tool can be used to track phones with data for which court orders are not typically required. This includes location data and user IDs acquired from online advertisers and other data brokers. According to the Texas Observer, the tool will be deployed for the use of the Texas State Police. The Tangles contract is worth $5.3 million over five years and is one of the Department's largest.
Government, politics, and policy
Denmark considers E2EE IM ban: The Danish government is considering blocking encrypted instant messaging apps such as Signal, WhatsApp, and Telegram. Officials say they're looking at a possible ban as a measure to fight rising criminal activity inside the country. The ban would be the first of its kind inside the EU. [Additional coverage in Radar.dk]
CISA lauds Microsoft: CISA executive assistant director for cybersecurity Jeff Greene says that Microsoft's decision to open up its logging capabilities last year has helped the agency gain greater visibility into the threats targeting US government agencies. [Additional coverage in CybersecurityDive]
New NIST draft: US NIST has released a new draft of its identity proofing guidelines. [Additional coverage in NextGov]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Haroon Meer, Founder and CEO at Thinkst, about the company's evolution over the past 15 years, its focus on hacker-like internal culture, and the UK NCSC's new deception network.

Cybercrime and threat intel
Another Angler EK member charged: The US government has charged a second Belarussian man with his involvement in the Angler exploit kit. Officials say Volodymyr Kadariya was part of the team that managed the malware, where he was known under nicknames such as Stalin, Eseb, and Baxus. He is the second man to be charged after the Angler gang's leader, Maksim Silnikau. Silnikau was arrested last year in Spain and extradited to the US to face charges. Kadariya is still at large, and the US State Department and the US Secret Service are offering a $2.5 million reward for information that may lead to his arrest.

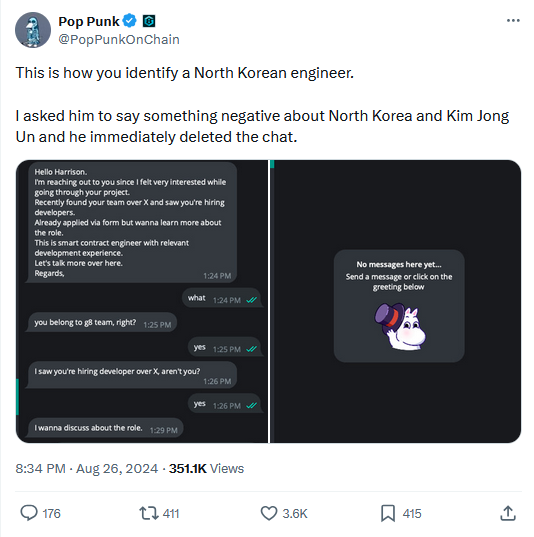
Cinder's DPRK problem: Content moderation platform Cinder says that roughly 80% of job applicants were suspected North Korean IT workers.
"We started filtering out suspected North Korean applicants by doing quick internet searches and closer examinations of job history, profile imagery, and a social media screening. However, our process wasn't perfect, and we still ended up on occasional Zoom calls screening applicants who we would quickly discover, mid-call, had fabricated their career history and only recently created their online presence."
AppDomainManager Injection: NTT has published a report on recent malware campaigns that have abused AppDomainManager injections to deploy malware on compromised hosts.
Microsoft Sway phishing: Netskope says threat actors have been abusing Microsoft's online presentation tool Sway to host phishing infrastructure. The Sway presentations hosted QR codes that redirected users to the actual phishing form. Most of the campaigns targeted owners of Microsoft 365 accounts.
US election cyber threats: Security firm BforeAI has discovered thousands of US election-related websites that are being used for phishing, scams, and spreading voter misinformation. The websites have been registered this year and include terms related to the Trump and Harris campaigns, as well as local election races. Not all domains are active, but those that do redirect voters to phishing sites, try to collect donations or are trying to suppress voter turnout by providing incorrect data on voting requirements, dates, and locations.

Malware technical reports
BlackSuit ransomware: The DFIR Report team has published one of their highly detailed reports—this time on the BlackSuit ransomware.
HZ RAT: Kaspersky says it found a macOS version of HZ RAT, a remote access trojan previously spotted targeting Windows users. DCSO believed the malware was being used by an APT group. Kaspersky says the macOS version closely replicates the functionality of the Windows version.
Angry Stealer: CyFirma looks at the new Angry Stealer, a redesigned version of the older Rage Stealer malware. Very original naming scheme we have here!
AutoITBot: SonicWall's security team looks at AutoITBot, an infostealer and keylogger written in AutoIT.
Poortry: Sophos says that a malware strain named Poortry has received significant updates over the past months that now put it on par with legitimate rootkits. The malware was first spotted in 2021 and was being used by ransomware gangs to disable EDR security tools before encrypting systems. Sophos says Poortry includes the ability to interact with many low-level OS APIs similar to how rootkits also operate. It also comes with a new feature that can wipe security tools completely off the disk as a way to clear the path for a ransomware attack.
Sponsor Section
Thinkst launched earlier this month a new fake mobile app Canarytoken for your smartphone. The token can be configured to look like any app you want and alert security teams when it is opened—an indication the employer's device was either infected with malware looking for juicy stuff or fell into the hands of an unauthorized third party (also looking for juicy stuff).
APTs, cyber-espionage, and info-ops
DEV#POPPER: Security firm Polyswarm has published details on the latest iteration of DEV#POPPER, a North Korean social engineering campaign designed to target and compromise software developers. The campaign uses fake job interviews to lure developers into running malicious code on their systems that install remote access trojans. The access is then used to pivot to current or future employees.
Russian attacks: RT-Solar, the security division of Russian telco Rostelecom, has published a report on two attacks against Russian industrial plants carried out by pro-Ukrainian groups.
Operation DevilTiger: QiAnXin researchers have published a report on Operation DevilTiger, a campaign from APT-Q-12, a threat actor the company links to the Korean peninsula.
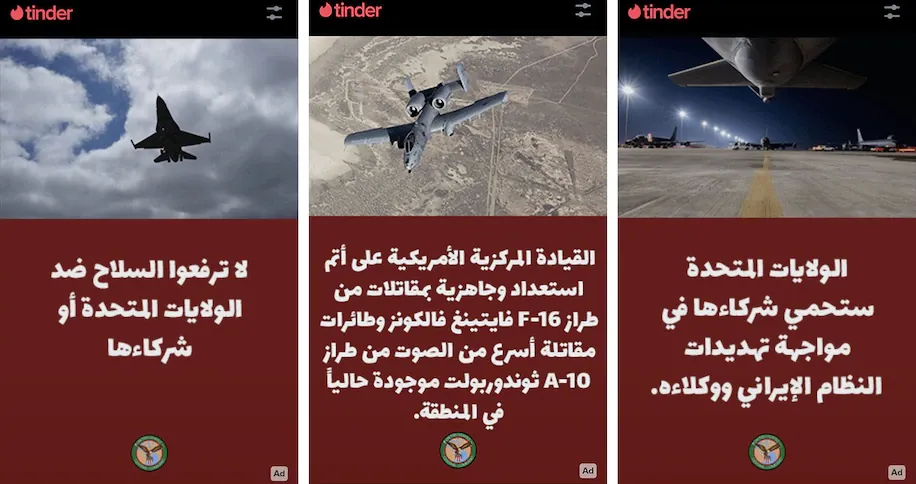
US runs Tinder ads: The US military has used ads on the Tinder dating platform to warn Middle East residents against taking up arms against the US and its partners. The campaign used photos of F-16 and A-10 aircraft "currently in the region." Tinder removed the ad after the Washington Post reached out for comment. The Pentagon declined to comment, saying it generally does not discuss information operations.
Vulnerabilities, security research, and bug bounty
Chrome zero-day: Google has updated a blog post from last week to add details about a second Chrome zero-day (CVE-2024-7965) exploited in the wild that was fixed with last week's patches. This adds to the first zero-day (CVE-2024-7971) spotted in the wild by Microsoft's security team. Both zero-days impact Chrome's V8 JavaScript engine. They are the ninth and tenth Chrome zero-days patched this year.
Intel SGX key dump: Security researchers have found a way to dump the root provisioning key (or Fuse Key0) for Intel SGX. This technique works only on some Intel CPU series that are now all end-of-support. This key can now be used to easily retrieve and decrypt data from the SGX secure mode with Intel's own keys—or plant data inside.
"The breach happened because of a flaw in Intel's microcode (the low-level code that controls the processor). Specifically, Intel's code failed to clear an internal buffer that held all the fuse values, including FK0. This buffer was supposed to acquire these values from the Fuse Controller but was left uncleared, accidentally exposing the key."
Windows IPv6 bug: Security researcher Marcus Hutchins has published a write-up that looks at CVE-2024-38063, that nasty Windows 10/11 RCE via IPv6 packets. tl;dr: No reliable PoC is available (for now), except this one that causes a DoS.
MobSF RCE: The Mobile Security Framework (MobSF) has patched a vulnerability in its mobile pen-testing product that can be exploited via ZIP Slip attacks to achieve remote code execution on a MobSF server. The bug received a 9.8 CVSS score because of its simple exploitation steps. [h/t ScreamingGoat]
Moodle RCE: RedTeam Pentensting has published a report on CVE-2024-43425, a remote code execution vulnerability that was patched in the Moodle LMS last week.
Apache OFBiz PoC: A proof-of-concept exploit was published for CVE-2024-38856, a pre-auth RCE in Apache OFBiz patched earlier this month. Naturally, a day later, this was added to CISA's KEV database of actively exploited bugs.
ASCII smuggling on Copilot: Microsoft has fixed an attack that used ASCII characters to steal customer data from the Copilot AI assistant.
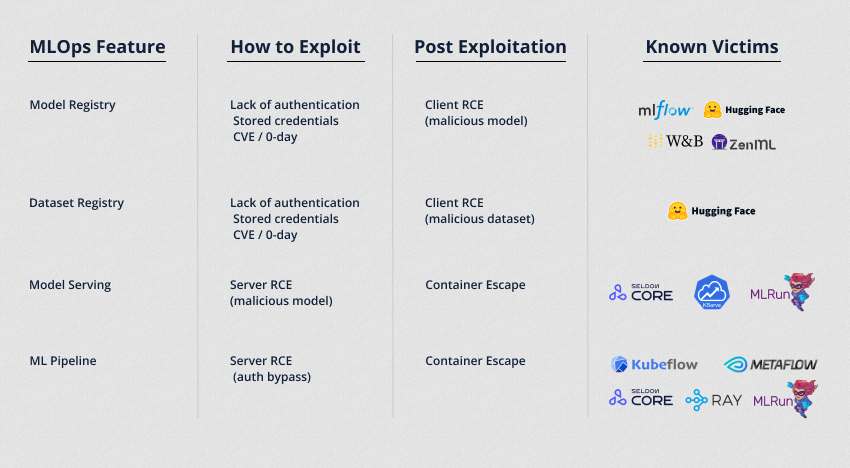
MLOps research: JFrog looks at machine learning platforms and the common types of attacks and vulnerabilities you can expect to find in the new MLOps SaaS model, design, and pipelines.
Infosec industry
Threat/trend reports: AWS (private report), Flashpoint, and VulnCheck have recently published reports covering infosec industry threats and trends.
New tool—SHELLSILO: Security researcher Tarek Ahmed has released SHELLSILO, a tool that translates C syntax into syscall assembly and its corresponding shellcode.
New tool—VeilTransfer: Security researcher Rahmat Nurfauzi has released VeilTransfer, a data exfiltration utility designed to test and enhance detection capabilities. The tool simulates real-world data exfiltration techniques used by advanced threat actors, such as WebDAV, Telegram, SFTP, and others.
New tool—USP: Security researcher Graham Helton has released USP, a tool that establishes persistence on Linux systems by creating an udev rule that triggers the execution of a specified payload. The tool was inspired a newly discovered malware strain named Sedexp.
New tool—Windows Downdate: SafeBreach's Alon Leviev has released Windows Downdate, a tool that can be used to perform downgrade attacks on installed Windows updates. Leviev presented details about this attack at the Black Hat security conference earlier this month.
Tool update—QCSuper: Something we missed from February was an update to QCSuper, a tool to capture traffic from Qualcomm-based phones and modems—now with 5G support.
Acquisition news #1: Check Point has agreed to buy fellow Israeli security firm Cyberint. The company provides threat intelligence and malware analysis services. The price of the transaction has not been disclosed, but Israeli tech outlets claim the deal is valued at around $200 million.
Acquisition news #2: Cisco has agreed to acquire AI security firm Robust Intelligence.
SLEUTHCON 2024 videos: Talks from the SLEUTHCON 2024 security conference, which took place in May, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss the opportunities in phishing and why it is both easy and difficult.
In this podcast, Tom Uren and Patrick Gray discuss an Australian government effort to bridge the gap between online and real identity across the whole economy. It addresses a real need, but Tom doesn't think it will go smoothly.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!





