Risky Biz News: Microsoft feels the heat, gives customers access to more cloud security logs
In other news: Kevin Mitnick passes; 700,000+ TikTok accounts hacked in Turkey; and Adobe patches a new ColdFusion zero-day.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
Microsoft has expanded the number of security logs that customers of the lower tier of its cloud service can access.
Thirty-one log categories have been moved from the premium tier of the Microsoft Purview Audit service into the standard offering.
The log retention policy for the standard tier has also been changed from 90 to 180 days, Microsoft said in an announcement on Wednesday.
The company's move comes after increased pressure from the US Cybersecurity and Infrastructure Security Agency, which previously stated that the lack of security logs for many US companies running Azure infrastructure complicated their response and investigations into the SolarWinds and other incidents.
Last week, CISA credited a federal agency that had access to the extended logging capabilities with discovering a stealthy Chinese cyber-espionage campaign that gained access to the Outlook email accounts of several US government agencies, including the State and Commerce Departments.
Through the past few years, Microsoft has been heavily criticized by some of the cybersecurity industry's top figures for placing many crucial security features in the upper and most expensive tiers of its cloud tiers.
This business practice has resulted in companies across the world moving IT infrastructure to Azure cloud services but being unable to pay for the premium tiers, settling for the lower packages, and remaining naked and blind to cybersecurity threats.
As my colleague Tom Uren highlighted in this week's edition of the Seriously Risky Business newsletter (that incidentally also covered cloud security), CISA Director Jen Easterly has been on a campaign this year to get cloud vendors to stop price gouging security features and provide more logging capabilities to their customers.
Easterly and all others who have been singing this tune are right to push Microsoft on this issue. Providing more security logs doesn't only protect customers but also protects the cloud provider through a secondary effect of crowdsourcing everyone's security detection capabilities. The more eyes on the logs, the more tools scanning those logs, the better for everyone, including Microsoft. If there's one thing the company doesn't need right now, it's more news reports of its cloud service getting rekt for months and crawling with state-sponsored hackers.
In a LinkedIn post, C. Kelly Bissell, CVP for Microsoft's Security Service Line, says there's "much more to come."
Below is Tom Uren and Patrick Gray discussing needed changes to the security practices of cloud providers in this week's edition of the Seriously Risky Business podcast.
Breaches, hacks, and security incidents
700k TikTok accounts hacked in Turkey: An unidentified threat actor gained access to more than 700,000 TikTok accounts from Turkey in April of this year. The hacks took place weeks before the country's presidential election. A TikTok spokesperson confirmed the hacks and said the attacker focused on boosting content from certain accounts. The company told Forbes that an internal investigation found no evidence the activity was related to the country's election. Forbes claims the attacker exploited TikTok's use of cheap and insecure SMS-sending capabilities to intercept SMS one-time passwords and hijack accounts. [Additional coverage in Forbes/non-paywall]
Estée Lauder incident: Cosmetics giant Estée Lauder has disclosed a major security breach after a threat actor gained access to its systems. The company says the incident has caused—and is expected to continue to cause—disruption to some parts of its business operations. Estée Lauder is the second-largest cosmetics company in the world by revenue after L'Oreal and owns brands like Tom Ford, MAC, and Clinique. Both the BlackCat and Clop ransomware gangs listed the company on their leak sites. The listings pre-date Estée Lauder's public disclosure, suggesting the company was most likely hit by one or both of the groups.
MOVEit hacks: The total number of victims has now surpassed 380, per Emsisoft.
General tech and privacy
Google throws support for MLS protocol: The Internet Engineering Task Force (IETF) has formally released the Messaging Layer Security (MLS) protocol as an official internet standard. The new MLS protocol was created to allow software to support end-to-end encrypted communications in group or offline scenarios. MLS is viewed as an upgrade to older technologies such as OTR (Off-the-Record) and the Signal protocol. Google says it plans to integrate the new MLS into its Google Messages client to allow interoperability with other E2EE platforms. Companies like Cisco and RingCentral already have products on the market that support MLS.
Apple threatens UK exit: Apple says it will pull FaceTime and iMessage from the UK market if the government uses new proposed powers under the Investigatory Powers Act to force it to weaken its security and encryption features.. Under the proposed IPA modifications, companies like Apple would have to clear new security features for their products with the Home Office before releasing them to customers. The new IPA would also let the UK government force tech companies to disable security features for their products without telling the public. Previously, both Signal and WhatsApp threatened they'd leave the UK market if the UK government passed the Online Safety Bill and force them to weaken their encryption to scan for child-abuse material in encrypted messages. [Additional coverage in the BBC]
Ban on private NL domains: Dutch national domain registrar SIDN has banned the registration of NL domains in the name of third parties. The ban will enter into effect on October 1 this year and effectively means Dutch NL domains cannot be registered with privacy and anonymity protections. SIDN says the decision was taken to fight abuse.
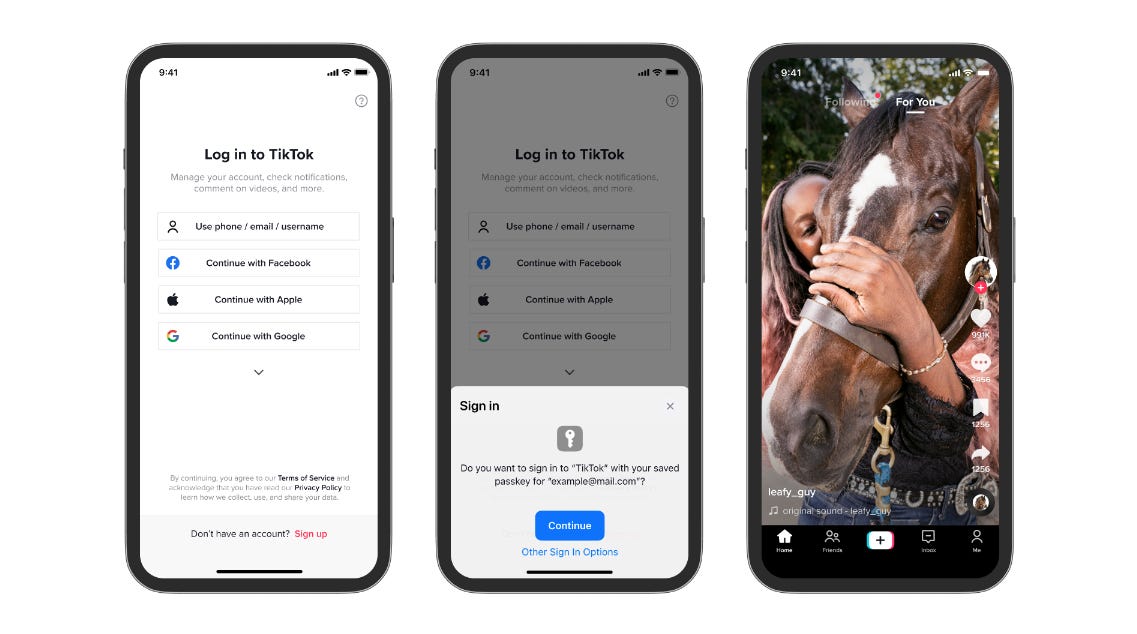
Passkeys come to TikTok: TikTok is gradually rolling out support for passkey logins for its main app. First, coming to iOS.
"We will begin rolling out passkeys for iOS in certain regions, starting with Asia, Africa, Australia, and South America beginning this month, and anticipate expanding in geographies and operating systems over time."
Government, politics, and policy
Fourth Amendment Is Not For Sale Act: The House Judiciary Committee passed a proposed bill that would ban government and law enforcement agencies from buying the personal information of Americans from data brokers without a warrant. Named the Fourth Amendment Is Not For Sale Act, the bill was first introduced in 2021. It received massive support this year after revelations that the US military, intelligence, and law enforcement agencies were creating massive private databases by buying the data of US citizens from the data broker market. After passing through the Committee, the bill can now go on the House and Senate floors for voting. If approved, the bill will mandate government agencies to get a warrant for any type of data bought from data brokers, regardless if the data was hacked or posted online beforehand. More from Senator Ron Wyden, the bill's author.
"The Fourth Amendment is Not For Sale Act will restore Americans' Fourth Amendment rights and stop the government from using its credit card when it should be getting a warrant. Regular Americans who use their phones on a daily basis are not consenting to send all their movements, contacts and web browsing information to the government."
CANSEE Act: Also in US legislative news, a bipartisan group has unveiled a new bill named the CANSEE Act that aims to introduce stronger rules meant to target and stop cryptocurrency money laundering operations. The bill introduces new regulations targeting DeFi platforms and crypto kiosks (aka crypto ATMs).
Amazon agrees to FTC&DOJ fine: Amazon has agreed to pay a $25 million civil penalty to the FTC and DOJ for violating US children's privacy COPPA laws.
Sponsor section
This week's sponsor is RunZero. In this Risky Business News sponsor interview, Tom Uren talks to RunZero CEO Chris Kirsch about how the company has evolved from offering an active scanning product to one that can now discover assets on OT and cloud environments using both active and passive scanning approaches:
Cybercrime and threat intel
DDoS trends Q2 2023: In its second quarter threat report, Cloudflare says it has observed numerous coordinated DDoS campaigns organized by pro-Kremlin "hacktivist groups" against Western interest websites. The company also noted a sudden rise in DDoS attacks targeting cryptocurrency platforms, which have increased 600% this past quarter. The largest attack in Q2 2023 was a 1.4 Tbps attack that targeted a US ISP.
Malvertising campaigns overview: Sophos has a review of the cybercrime gangs using malvertising to deliver their payloads. The suspects list includes IcedID, Gootloader, Gozi/Ursnif, BatLoader (FakeBat), and others.
WhatsApp account deactivation: You can deactivate anyone's WhatsApp account just by sending an email message to WhatsApp support and claiming you lost your device. It appears that WhatsApp is not verifying people's claims and just deactivates accounts right away. [Additional coverage in GHacks; via Jake Moore]
TheTruthSpy profile: TechCrunch's Zack Whittaker has a profile on spyware maker TheTruthSpy, the company behind apps like Copy9 and MxSpy.
KillNet: Google's Mandiant division has published a profile on pro-Kremlin "hacktivist" group KillNet.
"Mandiant assesses with moderate confidence that the collective's regular creation and absorption of new groups is at least partially an attempt to continue to garner attention from Western media and to enhance the influence component of its operations."
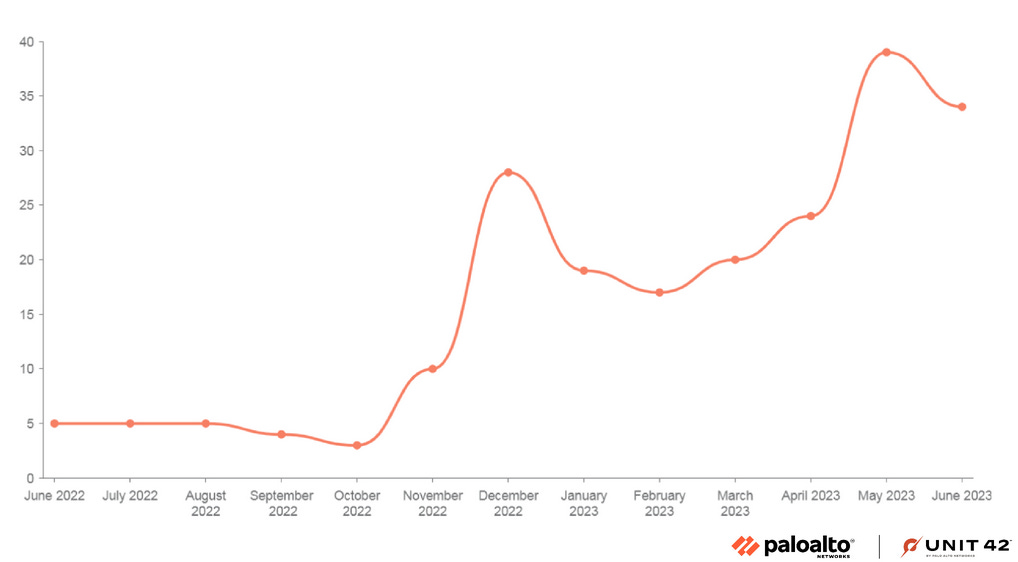
Mallox ransomware activity: Palo Alto Networks has highlighted a notable increase in activity from the Mallox ransomware group.
"Since its emergence in 2021, the Mallox group has kept the same approach to gaining initial access: The group targets unsecured MS-SQL servers to infiltrate a network. These attacks start with a dictionary brute force attack, trying a list of known or commonly used passwords against the MS-SQL servers. After gaining access, the attackers use a command line and PowerShell to download the Mallox ransomware payload from a remote server."
DEV-0970/Storm-0970: CyFirma takes a look at DEV-0970/Storm-0970, the threat actor behind Poop69 and Big Head ransomware strains.
Cactus victims: The Cactus ransomware group has listed 18 victims out of the blue on its dark web leak site on Thursday. One of the victims is ScanSource, which publicly disclosed a ransomware incident back in May, just when Kroll was seeing the new Cactus gang start operating.
Malware technical reports
SophosEncrypt RaaS: Sophos says that a newly-launched ransomware service is abusing its brand by calling itself SophosEncrypt. The ransomware is far from a joke and appears to be capable to encrypt Windows systems.
Blacksuit ransomware: ShadowStackRE has published an analysis of Blacksuit, a ransomware that targets VMWare ESXi systems. The ransomware appears to be a variant of Royal—per Trend Micro.
Ursnif: Kostas takes a look at the post-exploitation actions and techniques of the Ursnif group.
FakeUpdates campaign: Malwarebytes has details on a FakeUpdates (SocGolish) campaign that uses malicious fake browser update sites to deliver the NetSupport RAT, allowing threat actors to gain remote access and deliver additional payloads.
LaplasClipper: ANY.RUN has published a technical analysis of a new version of the LaplasClipper.
Pamspy: AquaSec has a report on how to detect the new Pamspy eBPF malware that has been recently seen targeting Linux systems.
P2PInfect: Palo Alto Networks has discovered a new peer-to-peer (P2P) worm called P2PInfect. The malware is written in Rust and currently targets Redis databases (via CVE-2022-0543). P2PInfect can run on both Linux and Windows operating systems, and researchers believe the worm may later be used to deploy a cryptominer on infected hosts.
"The design and building of a P2P network to perform the auto-propagation of malware is not something commonly seen within the cloud targeting or cryptojacking threat landscape. At the same time, we believe it was purpose-built to compromise and support as many Redis vulnerable instances as possible across multiple platforms."
BundleBot: Check Point has a pretty thorough breakdown of BundleBot, a new infostealer making the rounds.
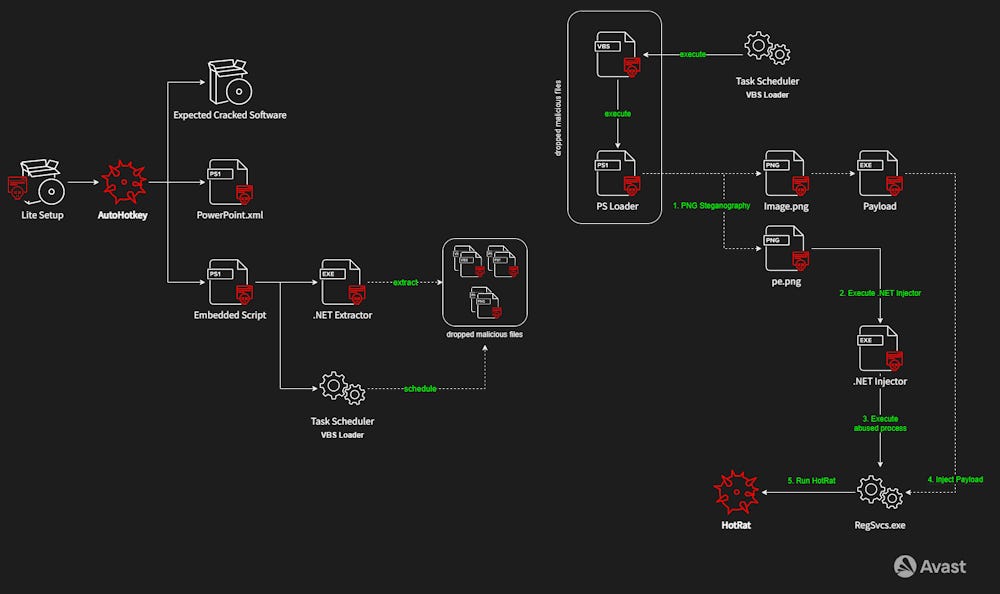
HotRat: Avast researchers have reverse-engineered HotRat, a variant of the AsyncRAT stealer. The malware is currently being distributed in the wild through torrent sites or suspicious web pages peddling cracked software. Avast calls the malware "an advanced version of AsyncRAT, armed with a multitude of spying and personal data theft capabilities."
Sponsor Demo
RunZero is one of this newsletter's main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network, including OT devices in critical environments. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
Chinese APT stealth tactics: Mandiant has published a report on the stealth strategies of Chinese APT groups. The report covers their use of zero-days in edge networking devices for initial access, the use of botnets and tunneling software to disguise C&C traffic and data exfiltration.
Space Pirates: Russian security firm Positive Technologies has published a follow-up on Space Pirates, a Chinese APT group that has been targeting Russia since 2017. The group's targeting over the past year included 16 organizations in Russia and one in Serbia. Targets range from government organizations to aerospace manufacturers and defence companies.
APT41's Android malware: Lookout has formally linked two pieces of Android malware it discovered in 2020 and 2021 to the APT41 Chinese state-sponsored cyber-espionage group. The two malware strains are known as WyrmSpy and DragonEgg, and both have been spotted in attacks as recent as April this year. Both operate as spyware and allow APT41 operators to collect data from infected devices. Lookout attributed the malware to APT41 by linking some of its command and control servers to IP addresses listed in the US Justice Department's 2020 indictment of APT41 members.
SideCopy APT: ThreatMon takes a look at the SideCopy APT and one of their recent infection chains.
DPRK campaign on GitHub: A North Korean APT group named TraderTraitor (Jade Sleet) has been running social-engineering campaigns on GitHub, trying to trick the employees of technology firms into working on malicious GitHub projects that infect victims with malware. The GitHub projects are typically media players and cryptocurrency trading tools that contain malicious npm libraries. In a security alert published this week, GitHub says the campaign has targeted employees working for cryptocurrency, online gambling, and cybersecurity firms. The end goal of the attack is to infect an employee's device and then pivot to their employer's network. Some of the malicious npm packages used by TraderTraitor were spotted in June by DevSecOps company Phylum.
JumpCloud incident: SentinelOne has formally confirmed our scoop from Monday that JumpCloud was compromised by a North Korean APT. The company has linked the incident to the same TraderTraitor (Jade Sleet) APT group from above. CrowdStrike also confirmed the North Korean attribution to Reuters.
Turla targets Signal chats: Microsoft and Ukraine's CERT team have spotted the Turla Russian APT group infecting victims with malware and specifically seeking to exfiltrate files from the Signal Desktop application in an attempt to read private conversations. Targets of the attacks include the defense sector in Ukraine and Eastern Europe. For the campaign, Turla has used spear-phishing emails that infect victims with the DeliveryCheck (Gameday, Capibar) backdoor, through which the group later installs the Kazuar infostealer to perform the actual data exfiltration. Besides Signal files, Kazuar can also collect and steal all sorts of other information, such as browser passwords, cloud API tokens, password manager databases, VPN client configurations, and more.
Vulnerabilities, security research, and bug bounty
Google sets up AI Red Team: Google has established a dedicated red team tasked with testing and securing artificial intelligence systems and help the company establish security standards for the emerging technology. The team's main responsibilities will be to take relevant research and adapt it to work against real products and features that use AI, and then observe and learn from its impact. The team will tackle security, privacy, and abuse.
Adobe ColdFusion zero-day: Adobe has released an emergency security update for its ColdFusion software stack to patch an actively exploited zero-day tracked as CVE-2023-38205. The update is the second out-of-bound patch the company released in a week after it also rolled out an emergency patch for another zero-day (CVE-2023-38203) last Friday. According to Rapid7, this new zero-day is a bypass for one of Adobe's patches (CVE-2023-29298) last week, which allowed the threat actor to continue their attacks this week after customers started installing patches. Both zero-days have now been added to CISA's KEV database.
MegaRAC vulnerabilities: Eclypsium has disclosed details on five vulnerabilities in MegaRAC baseboard management controllers (BMCs). The vulnerabilities include an unauth RCE that can grant attackers access to BMCs with superuser permissions. Eclypsium says the vulnerabilities can be used to take control of servers, deploy malware, trigger infinite reboot loops, brick motherboards, and even cause physical damage to servers.
MOVEit RCE: ZDI has published a detailed analysis of CVE-2023-36934, a new RCE discovered and patched in the MOVEit MFA server earlier this month.
OpenSSH RCE: Qualys researchers have discovered an RCE (CVE-2023-38408) in the OpenSSH client. Not a big deal.
Outlook March zero-day: Kaspersky has a write-up on CVE-2023-23397, an Outlook zero-day exploited by a Russian APT that Microsoft patched in March.
PaperCut exploitation: Juniper has released a write-up on CVE-2023-27350, the PaperCut vulnerability that was widely used in attacks earlier this spring.
Oracle CPU: The quarterly Oracle security updates are out, with patches for 508 vulnerabilities.
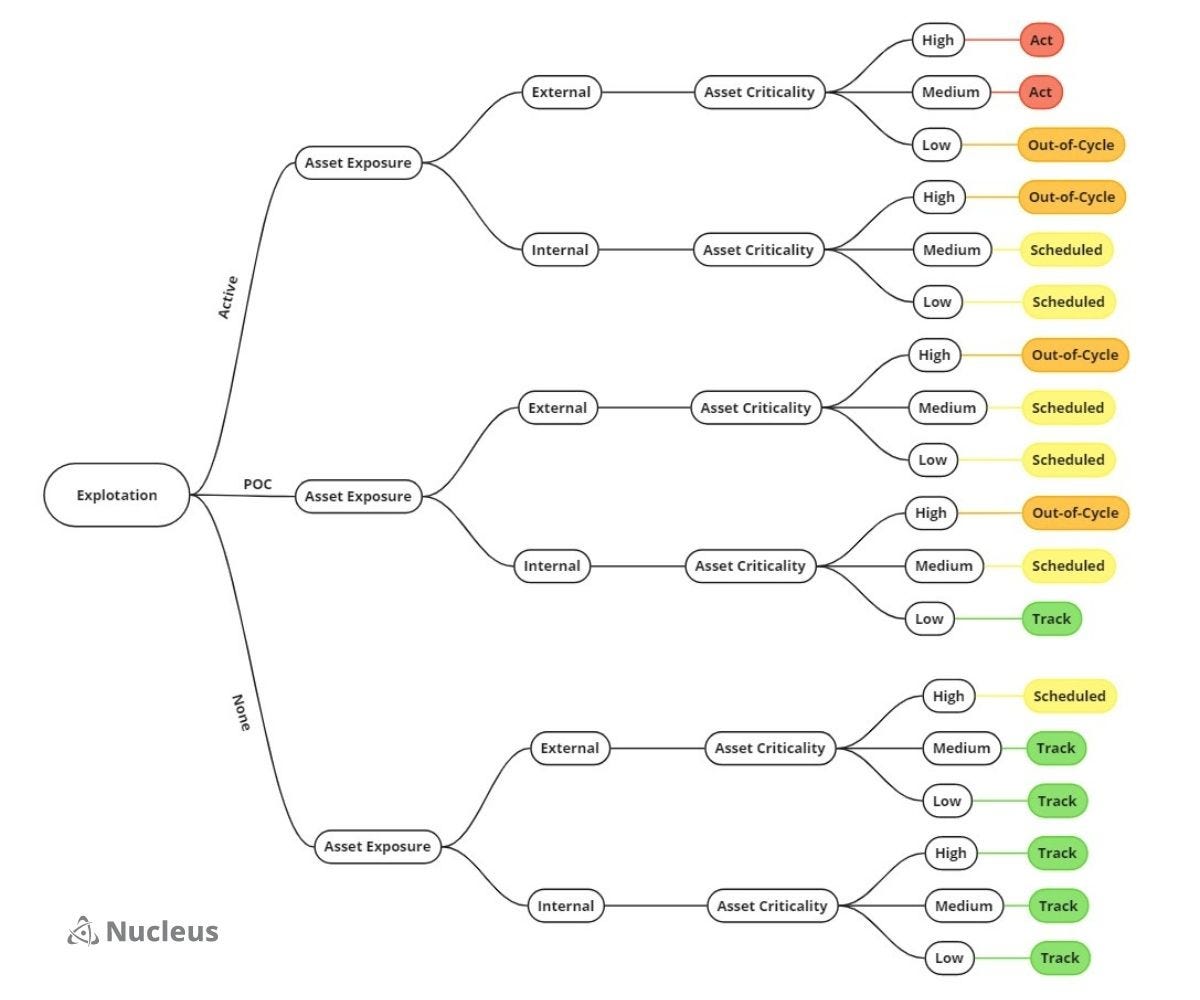
SSVC decision tree: Nucleus Security's Patrick Garrity has published a draft guide on automating vulnerability prioritization using decision trees based on Stakeholder-Specific Vulnerability Categorization (SSVC).
Infosec industry
Kevin Mitnick: The cybersecurity industry mourns the passing of Kevin Mitnick, a pioneer and a member of the infosec community for more than four decades. Mitnick passed on Sunday, July 16, 2023, from pancreatic cancer. He is survived by his wife, Kimberley, with whom he was expecting a first child.
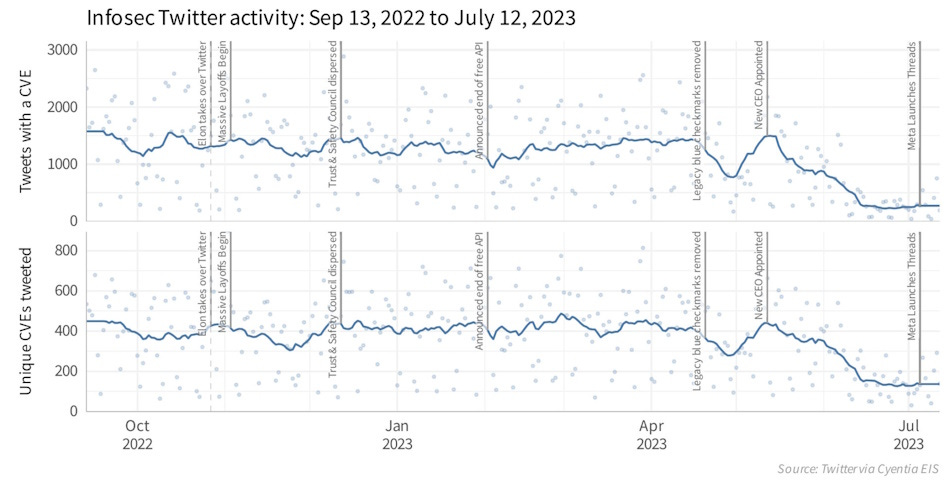
Infosec Twitter research: The Cyentia research institute has seen a massive drop in infosec-related content being posted on Twitter since the end of April this year, around the time Elon Musk decided to kill much of the free Twitter API access.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the idea of actively shaping ransomware group behavior to get the type of behavior we'd prefer.




