Risky Biz News: US and UK sanction seven Trickbot members
In other news: EU puts out first-ever mis/disinformation report; NIST approves lightweight IoT cryptography standard; Dota 2 mods backdoor player systems.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The governments of the United States and the United Kingdom have levied sanctions against seven Russian nationals for their role in the Trickbot cybercrime gang.
Both countries said the sanctions are part of a coordinated crackdown against the ransomware ecosystem.
The Trickbot gang, also known as Wizard Spider, is primarily known for its eponymous Trickbot malware botnet. In the past, Trickbot has rented access to computers infected by its malware to the Ryuk cybercrime group, which deployed its ransomware on corporate or government networks. In addition, Trickbot also developed its own ransomware strains, known as Conti and Diavol, which they also deployed on systems that were previously infected by their botnet.
The UK government said that in the UK alone, 149 organizations paid at least £27 million following attacks with the Conti and Ryuk ransomware strains.
"There were 104 UK victims of the Conti strain who paid approximately £10 million and 45 victims of the Ryuk strain who paid approximately £17 million."
Over the years, the Trickbot botnet has grown to become one of the largest malware operations to date, and the gang's sub-group tasked with carrying out ransomware attacks has become one of the most despised ransomware gangs today after repeatedly targeting medical and healthcare facilities and disrupting their operations—even during the COVID-19 pandemic.
"Members of the Trickbot Group publicly gloated over the ease of targeting the medical facilities and the speed with which the ransoms were paid to the group."
The US and UK sanctions announcements also include the first formal statement linking the Trickbot gang with the Russian government. Both the US and UK governments say that members of the Trickbot gang are also associated and maintain links to Russian intelligence services, "from whom they have likely received tasking."
With Trickbot's inclusion on the sanctioned entities list, US and UK companies are now forbidden from paying ransoms to the group, and financial entities are mandated to freeze any of the group's assets.
Sanctions have proven very successful against ransomware gangs in the past, with the sanctions imposed against EvilCorp in 2019 effectively destroying their ransomware operation (Bitpaymer, Hades, WastedLocker) and making the group and its members pariahs in the cybercrime underground.
The seven sanctioned Trickbot members are:
- Vitaly Kovalev was a senior figure within the Trickbot group. Vitaly Kovalev is also known by the online monikers "Bentley" and "Ben."
- Maksim Mikhailov has been involved in development activity for the Trickbot Group. Maksim Mikhailov is also known by the online moniker "Baget."
- Valentin Karyagin has been involved in the development of ransomware and other malware projects. Valentin Karyagin is also known by the online moniker "Globus."
- Mikhail Iskritskiy has worked on money laundering and fraud projects for the Trickbot group. Mikhail Iskritskiy is also known by the online moniker "Tropa."
- Dmitry Pleshevskiy worked on injecting malicious code into websites to steal victims' credentials. Dmitry Pleshevskiy is also known by the online moniker "Iseldor."
- Ivan Vakhromeyev has worked for the Trickbot group as a manager. Ivan Vakhromeyev is also known by the online moniker "Mushroom."
- Valery Sedletski has worked as an administrator for the Trickbot group, including managing servers. Valery Sedletski is also known by the online moniker "Strix."
The US Justice Department has also charged Trickbot's Kovalev with conspiracy to commit bank fraud and eight counts of bank fraud in connection with a series of intrusions into victim bank accounts that occurred in 2009 and 2010 and predated his involvement in the Trickbot gang.
Breaches and hacks
MTU ransomware attack: The Munster Technological University from Cork, Ireland, has been hit by a ransomware attack. The incident has impacted the university's phone and IT systems and has forced officials to close down all of its four campuses and cancel classes for two days. Officials said university campuses in Kerry were unaffected. [More in the Irish Examiner]
Convex leak: More than 120 GB of data have been leaked from Russian internet provider Convex. According to DDoSecrets, the data exposes details about Russian internet and phone surveillance activities, including a previously unknown surveillance program named Green Atom. The hack has been claimed by a hacking collective known as CAXXII in an interview with the Kyiv Post.
Indigo incident: Indigo, Canada's last remaining national bookstore chain, says it suffered a cybersecurity incident. According to local media, the incident knocked the company's website and order processing systems. The company says cash transactions at its stores are still possible.
General tech and privacy
NIST IoT crypto: The US National Institute of Standards and Technology (NIST) has announced that a group of cryptographic algorithms called Ascon will become its lightweight cryptography standard later in 2023. Once officially published, Ascon will become NIST's recommended cryptography algorithm for lightweight electronics and IoT devices. NIST says Ascon was selected to become its new standard following a five-year selection process that received 56 other submissions. Ascon was developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research, and Radboud University, and currently consists of seven algorithms (Ascon-128, Ascon-128a, Ascon-Xof, Ascon-Xofa, Ascon-Hash, Ascon-Hasha, and Ascon-80pq).
Google to give away 100,000 security keys: Google says it will be distributing 100,000 Titan security keys globally to high-risk individuals throughout 2023 at no cost. Recipients will include journalists and professionals working in politics. Google says that since 2020, the company has distributed more than 20,000 security keys. Most were distributed in the US to help secure previous election cycles through its Defending Digital Campaigns (DDC) program. Through its latest effort, Google wants to expand the program globally to more countries but also prepare for the upcoming 2024 US elections.
Android 14 DP1: Google has released the first developer preview of its upcoming Android 14 operating systems, set to be released in full later this year, in August. All the upcoming changes are detailed here, including upcoming security changes, including safer intents (to prevent malicious apps from intercepting intents), safer dynamic code loading (DCL has been used by malware for code injection attacks to manipulate apps), a new API install limit (Android 14 will not install apps designed for the Android API SDK v23 or lower), passkey support, and more.
Acrobat PDF Reader comes to Edge: Microsoft announced it will embed Adobe's Acrobat PDF engine in future versions of its Microsoft Edge browser. The move will take place in March 2023 for Edge versions on both Windows 10 and Windows 11. The current Edge PDF engine will be removed on March 31, 2024. A FAQ page has more details.
Microsoft Teams wipe & extortion: Microsoft is retiring the classic version of its Microsoft Teams Free tier on April 12 this year. While a new free version of Teams is available to customers, Microsoft says there will be no data transfer between the two offerings. The OS maker told users that if they want to keep their old chats and files, they'll have to pay a ransom... I mean... upgrade their classic Teams Free account to a paid version.
Twitter risks GDPR fine: Wired is reporting that Twitter is blatantly ignoring the EU's GDPR legislation by ignoring requests from users to have their data deleted from the platform.
Cloudflare's Wildebeest: Cloudflare has announced Wildebeest, an open-source, easy-to-deploy ActivityPub and Mastodon-compatible server that can be easily deployed on Cloudflare's servers.
Ubiquiti security upgrades: Ubiquiti's cybersecurity team has announced a series of security-related changes they are planning to make across all their product lines in the coming future.
- Increasing the minimum length of our passwords to 12 characters.
- Disabling SSH by default when possible.
- Increasing Multi-factor Authentication (MFA) options for our Cloud services.
Government, politics, and policy
EU FIMI report: The European External Action Service has published its first-ever report [PDF] on foreign information manipulation and interference (FIMI) threats. EEAS says it detected and analyzed 100 FIMI events between October and December 2022. Most of these targeted Russia's invasion of Ukraine. In 60 of the 100 incidents, the threat actors used misinformation and disinformation in an attempt to show support for Russia's invasion. Furthermore, the report found that the Russian government itself and its diplomatic channels were part of the FIMI events, spreading false information and trying to control narratives. In addition, Russian threat actors also used impersonation attacks, either posing as foreign officials or foreign news outlets in an attempt to spread their agenda.
"FIMI actor collusion exists but is limited. Official Russian actors were involved in 88 analysed FIMI incidents. Chinese actors were involved in 17. In at least 5 cases, both actors engaged jointly. [...] FIMI remains mostly image and video based. The cheap and easy production and distribution of image and video material online makes these formats still the most commonly used."
EU shames Twitter on disinformation: The European Commission singled out Twitter as lagging behind Google, Meta, Microsoft, Twitch, and TikTok when it came to efforts to tackle disinformation. [Additional coverage in Reuters]
SNP MP hacked: Stewart McDonald, a UK MP for the Scottish National Party and a staunch supporter of Ukraine, says Russian state-affiliated hackers have breached his personal email account and the personal email account belonging to one of his staff. The hacking group is believed to be linked to Russia's intelligence services. The group appears to have hacked his staff member's account first and then used it to trick McDonald into opening a password-protected file on the Ukrainian war. The file led the MP to a phishing site posing as his personal email account's login page, where McDonald entered his credentials. McDonald confirmed a BBC report about the hack and said that his work/parliamentary account has remained safe.
Australia DOD to remove Chinese cams: The Australian Department of Defense plans to remove almost 1,000 security cameras developed by CCP-linked companies such as Dahua and Hickvision. The decision comes after officials from the US and the UK took similar steps to remove cameras from the two companies from their government networks. [The Australian / non-paywalled version]
Chris Inglis to retire: White House Cyber Director Chris Inglis plans to retire next week, following two years in his current role and more than four decades of working in national security. [More in Politico]
Quad Cyber Challenge: Members of the Quad alliance, the US, Australia, India, and Japan, have launched a new project called the Quad Cyber Challenge. The project is set to take place between April 10 and 14 this year. Its aim is to get organizations from the public and private sectors to go through a checklist [PDF] of basic security checks meant to greatly improve their cyber habits/posture.
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
PyPI malware: DevSecOps Sonatype has identified four malicious Python libraries hosted on the official PyPI portal. The libraries contained functionality to install other malware, delete the netstat utility, and tamper with SSH keys installed on a system to allow an attacker to connect remotely.
QakNote: We touched in one of our previous editions about the rise in the use of OneNote documents to deliver malware. We had reports on the topic from Proofpoint, WithSecure, OpalSec, and Yoroi. Now, Sophos has one out, too—detailing how the QakBot gang is weaponizing OneNote for its campaigns.
Magniber activity: AhnLab has spotted new Magniber ransomware activity in South Korea.
D-Shortiez malvertising: A malvertising campaign tracked as D-Shortiez has been spotted hijacking back button presses in WebKit-based browsers to redirect users to scam sites. Ad security company Confiant says it has seen the group serve more than 300 million malicious ads over the past six months, primarily to US audiences.
AWS malvertising: SentinelOne has spotted malicious ads appearing in Google search results for AWS-related terms that were redirecting users to AWS phishing pages.
SteelClover group: NTT Security has a report out on the SteelClover group, which, since the start of the year, has utilized Google search ads to distribute malware such as IcedID and Aurora Stealer.
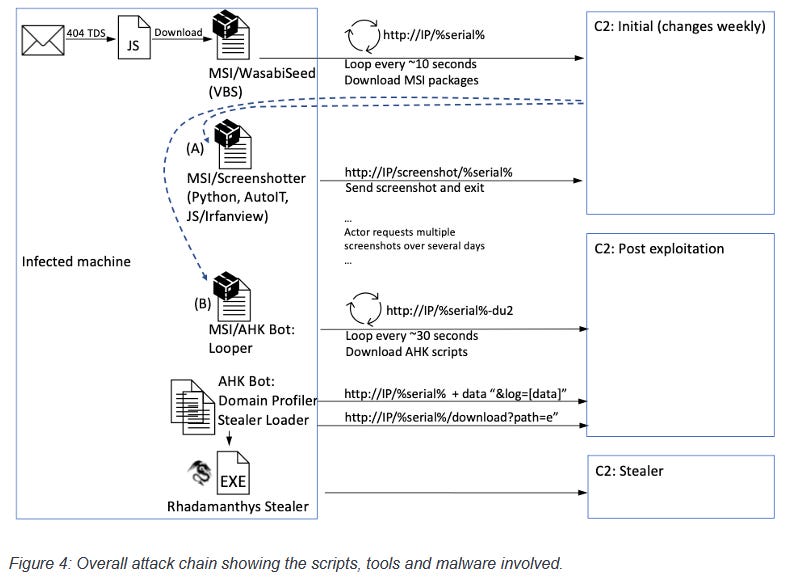
New TA866 group: Security firm Proofpoint has discovered a new financially-motivated threat actor that appeared last October and has targeted organizations in the United States and Germany. Tracked under the codename TA866, the group uses phishing emails to trick victims into installing malware on their systems. The first payloads are malware strains named WasabiSeed and Screenshotter, with the latter being used to take screenshots of the victim's computer. Proofpoint says the group uses these screenshots to assess the level of access they have before moving forward with the attack and deploying additional malware, such as AHK Bot or the Rhadamanthys stealer.
Malware technical reports
ESXiArgs recovery script: CISA has released a Shell script that can recover the configuration file of VMWare ESXi servers that have been encrypted by the ESXiArgs ransomware. CISA says it created this automated tool based on several publicly available resources, including a tutorial by Turkish software developers Enes Sonmez and Ahmet Aykac.
"This tool works by reconstructing virtual machine metadata from virtual disks that were not encrypted by the malware."
However, a day after CISA released this script for old victims, a new version of the ESXiArgs ransomware morphed to counter its effects and encrypt data in a way the script can't recover it.
Malicious Dota 2 mods: Cybersecurity firm Avast says it found four Dota 2 game mods published on the official Steam store that contained malicious code. Avast says the code acted as a backdoor and allowed the attacker to run custom JavaScript code on the player's system. Researchers said the attack was possible because the Dota 2 game was using a version of the V8 JavaScript interpreter compiled in December 2018, which was vulnerable to several security flaws. While V8 is typically used inside web browsers, Dota 2 was using it to show the game's user interface. Avast says the attacker exploited a vulnerability tracked as CVE-2021-38003, for which proof-of-concept exploit code has been published and was widely available. Valve, the company behind Dota 2, updated the game's V8 engine on January 12 to prevent future exploitation attempts.
ChatGPT protections bypass: Check Point says it is seeing ads on cybercrime forums where threat actors are advertising services to bypass restrictions put on GhatGPT against its use for malware development. Over the past month, threat actors have abused the service to help them improve malware code, but as of recently, OpenAI has put several restrictions on the service.
GoAnywhere exploitation: Huntress Labs researchers have linked the recent zero-day attacks against GoAnywhere MFT file-sharing servers to a threat actor tracked as TA505. Huntress says they've seen GoAnywhere servers being infected with Truebot, a malware typically used by the TA505 crew. In the past, the TA505 gang has been linked to attacks that deployed the Clop ransomware, and researchers believe the attack they observed and stopped was "intended to deploy ransomware."
Enigma Stealer: Trend Micro says it discovered a suspected Russian threat actor engaging in a campaign that uses a fake employment pretext targeting Eastern Europeans working in the cryptocurrency industry to install an information stealer on their systems. The final payload in this campaign is called Enigma Stealer, an information stealer based on the Stealerium open-source stealer.
APTs and cyber-espionage
UAC-0114 (WinterWyvern): The State Cyber Protection Center of Ukraine has published a technical report [PDF] detailing recent attacks carried out by a Russian APT group named WinterWyvern. Ukrainian officials said the group has tried to lure potential targets on a website mimicking Ukraine's Foreign Affairs Ministry. The website asked visitors to download software for "scanning infected PCs on viruses" on their systems, software that was laced with a basic backdoor named APERETIF. The attacks were discovered by both CERT-UA and CERT-PL. CERT-UA says that following a joint investigation with Poland's CERT team, they discovered similar websites operated by the same threat actor that mimicked the websites of the Ministry of Defense of Ukraine, the Security Service of Ukraine, and the Polish Police.
Nodaria (UAC-0056): Broadcom's Symantec division says that it has seen the Nodaria cyber-espionage group switch targeting from Georgia and Kyrgyzstan to go after Ukrainian organizations. The suspected Russia-linked group—also tracked as UAC-0056—has been linked to the WhisperGate wiper attacks that hit multiple Ukrainian government computers and websites in January 2022. Since then, Symantec says the group has been carrying out spear-phishing attacks aimed at installing the Graphiron infostealer on the systems of Ukrainian organizations.
"The earliest evidence of Graphiron dates from October 2022. It continued to be used until at least mid-January 2023 and it is reasonable to assume that it remains part of the Nodaria toolkit."
NewsPenguin: BlackBerry's security team says it discovered a new APT group targeting organizations in Pakistan. The group's name of NewsPenguin comes from its use of news-related content for phishing lures and the "penguin" string to encrypt their payloads.
Earth Zhulong: Trend Micro researchers say they discovered attacks by a threat group named Earth Zhulong that has been targeting the telecom, technology, and media sectors in Vietnam since at least 2020.
"Based on the victimology and usage of a highly similar decryption algorithm, we believe that Earth Zhulong is related to the hacking group known as '1937CN'. We hope our findings will remind the public that the actions and motivations of 1937CN continue to resurface through groups like Earth Zhulong, and that these groups remain a big threat to cybersecurity in Southeast Asia."
Spamouflage: Graphika researchers say that in late 2022 they observed the Spamouflage group use video footage with AI-generated fictitious people pushing news reports that promoted the interests of the Chinese government. Graphika says the group "almost certainly" produced the AI-generated video using an AI video creation platform operated by Synthesia, a commercial company in the UK. Despite the effort to make their influence operation more credible, Graphika says the videos "were low-quality and spammy in nature" and received less than 300 views.
"In the weeks since we identified the activity described in this report, we have seen other actors move quickly to adopt the exact same tactics. Most recently, this involved unidentified actors using the same AI tools to create videos targeting online conversations in Burkina Faso."
Vulnerabilities and bug bounty
OpenSSL security updates: The OpenSSL project has released security updates to fix eight vulnerabilities.
Apache Kafka RCE: An RCE has been discovered and patched in Apache Kafka, an open-source distributed event streaming platform used for high-performance data pipelines, streaming analytics, and data integrations. The RCE has been assigned the CVE-2023-25194 identifier. According to the project's website, "more than 80% of all Fortune 100 companies trust, and use Kafka."
Dahua vulnerability: Chinese camera maker Dahua has patched a vulnerability (CVE-2022-30564) that can allow threat actors to modify timestamps on Dahua recorded footage.
Year in review: Vulnerability management platform PRIOn has a year-in-review report about the vulnerabilities that were disclosed last year, in 2022, and the top 100 vulnerabilities companies should be prioritizing.
Infosec industry
Azure Storage thread model: Cloud security firm TrustOnCloud has published a 131-page document with a threat model of all the attack scenarios against Azure Storage. Previously, the company published a similar ginormous 173-page document on AWS S3.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




