Risky Biz News: Zero-day alert for GoAnywhere file transfer servers
In other news: BonqDAO hacked for $120 million; new Nevada RaaS; HeadCrab infects 1,200 Redis servers.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Hackers are exploiting a zero-day vulnerability in GoAnywhere MFT, a web-based file transfer application typically used in corporate environments.
Fortra, the company behind GoAnywhere MFT, says that only the app's administrative panel is exploitable and not the public web client typically used by a company's normal users.
The company is warning customers to secure their admin panels from unauthorized access, such as taking panels off the public internet and restricting them to intranets or behind firewall IP allowlists.
No patch is currently available. Some mitigations exist, and they are available in a copy of Fortra's security alert shared by infosec reporter Brian Krebs on Mastodon on Thursday.
According to security researcher Kevin Beaumont, there are currently roughly 1,000 internet-accessible GoAnywhere MFT servers listed on Shodan, although most of these appear to expose their web client. Unclear how many have admin panels exposed as well.
Enterprise-ready file transfer solutions like GoAnywhere are often in the crosshair of both cybercrime and APT groups alike. In the past, Accelion's FTA and Soliton's FileZen file-sharing and file-transfer products have been targeted in attacks.
Breaches and hacks
BonqDAO crypto-heist: The BonqDAO cryptocurrency lending platform has confirmed that a threat actor used an Oracle attack to exploit a vulnerability in its Bonq protocol and manipulate the price of AllianceBlock (ALBT) tokens. The company is still investigating the impact of the hack, but blockchain security firm PeckShield has estimated the losses from the attack to be a whopping $120 million worth of funds. The attacker is currently trying to launder the stolen funds into more stable/mainstream coins. The incident is this year's largest cryptocurrency heist so far. [Media coverage in the CoinTelegraph, technical analysis via Numen Cyber Labs and SlowMist]
Ransomware impacts the stock market: A ransomware attack on ION Trading, a UK-based company that makes trading software, is impacting the activity of several major European and US banks. The company's software is used to process derivatives trades across stock, bond, and commodities markets. Bloomberg News says the outage has impacted at least 42 customers, some of which are having problems with regulatory reporting and are processing trades manually. In a statement on its website, ION Trading confirmed the incident but said the attack only hit one of its software environments and that all affected servers have now been disconnected. Most of the issues have been reported across Europe. Bloomberg has identified the ransomware gang behind the attack as LockBit.
Vice Media breach: US news agency Vice Media says a hacker gained access to an internal email account and has stolen information on 1,724 of the company's employees. Vice Media, whose news outlets have criticized companies for being slow in disclosing data breaches, took ten months to disclose the incident, which took place in March last year and was discovered a week later in early April.
Electrify America boo-boo: Apparently, you can use TeamViewer to take over the DC fast-charging stations of Electrify America and access their backend, which looks to be some sort of old Windows 10 install still running Internet Explorer. Several instances of abuse have been reported already. [More in InsideEVs]
Mastodon DDoS attacks: Several Mastodon instances have been the targets of DDoS attacks lately, including Mastodon.social, the largest Mastodon instance, and JoinMastodon.org, the service's official website. No major downtime was recorded, though.
Best2Pay leak: Hackers have leaked the data of more than 1 million customers of Russian online payment service Best2Pay.net. The leaked data contains customer names, mobile phone numbers, payment details, and people's last four card digits. The company has not confirmed the leak, but the Telegram channel where the data was leaked has a very long history of sharing authentic leaks from Russian companies.

General tech and privacy
GoodRx fine: The US Federal Trade Commission has fined GoodRx, a telehealth and prescription drug discount provider, $1.5 million for sharing the personal and health information of its customers with online advertisers. The FTC says that in 2019, GoodRx compiled lists of its users who used their apps or visited their site to purchase particular medications, such as those used to treat heart disease and blood pressure. These lists included a buyer's email address, phone number, and mobile advertising ID. The FTC says GoodRx uploaded these lists to Facebook's ad platform so it could identify its users' real-world profiles and names and then re-advertise its products to the same users with targeted advertising.
Chrome updates: Google has changed how new Chrome releases are coming out. Starting with Chrome 110, Google says it will ship its stable version to a small percentage of users ahead of everyone else. This should technically allow Google to catch issues before they affect all its users during the normally scheduled release.
Tor donations: The Tor Project says it received only $367,674 from user donations last year. The sum represents the lowest sum received from donations over the past three years. The organization said the dip came following the cryptocurrency crash of last year.
Creepy ChatGPT update: OpenAI, the company behind that creepy ChatGPT thing, has released a tool to detect its own bot's text. The company the tool can be useful in detecting and preventing abuse of its tool in education, social media, and other places.
Twitter makes API paid access: Twitter—the social network where governments can call for genocide on their official accounts and influence operations rule your daily timeline—has shuttered its public APIs. Both Twitter APIs v1.1 and v2 will become paid access only starting February 9. Good luck with that!

Government, politics, and policy
Iran discloses cyber-attack: Issa Zarepour, Iran's Minister of Communications and Information Technology, says the large-scale disruptions to internet connectivity that took place last week were the result of a cyber-attack. The attack allegedly hit Tehran's traffic exchange node and resulted in a sudden decrease in traffic. The official did not elaborate on the nature of the incident.
Russia to jail execs for data breaches: The Russian government is moving forward with its project of imposing major fines and even prison sentences for IT administrators and their managers in the aftermath of major data breaches. The project was first proposed in May 2022. If passed, the Russian government will be able to fine individuals from 300,000 to 2 million rubles ($4,200->$28,000) or imprison them for up to 10 years if their companies get hacked and user data stolen or leaked.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Former Ubiquiti employee pleads guilty: Nickolas Sharp, a former employee of US networking equipment maker Ubiquiti, has pleaded guilty to stealing gigabytes of sensitive documents and then trying to extort the company back in 2021. Sharp is infamous for tricking infosec reporter Brian Krebs into thinking they were a whistleblower trying to expose that Ubiquiti had suffered a security breach, when, in fact, they executed the breach and just trying to use media coverage to put pressure on the company and get themselves paid.
Water Dybbuk BEC group: Security researchers at Trend Micro have spotted a new threat actor engaging in a persistent BEC campaign against large companies from all over the world. Named Water Dybbuk, this threat actor has been active since April 2022 and has heavily relied on open-source tools during their intrusions, which has allowed it to remain under the radar for months until it was discovered. In particular, the group used phishing toolkits like BadaxxBot and Evilginx to power their phishing pages, which they used as the initial entry into corporate networks.
HeadCrab targets Redis DBs: Cloud security company AquaSec says it identified a new threat actor named HeadCrab that, since September 2021, has utilized state-of-the-art and custom-made malware to take over Redis database servers. AquaSec says the group is currently managing a botnet of more than 1,200 infected Redis DBs. Just like most botnets targeting cloud systems these days, the botnet appears to be focused on mining cryptocurrency.
Passion DDoS botnet: DDoS mitigation service Radware has identified a new DDoS botnet named Passion that was recently used by pro-Russian hacktivist groups to launch attacks against western targets. The botnet has been linked to attacks carried out by groups like Killnet and Anonymous Russia. Many of these attacks took place around January 27 and targeted medical institutions in the US, Portugal, Spain, Germany, Poland, Finland, Norway, Netherlands, and the UK, as retaliation for sending tanks in support of Ukraine. Radware's report comes as the US Department of Health and Human Services has issued a security alert about Killnet using DDoS attacks to disrupt services at US healthcare providers [PDF].
"The Passion group, like the IT Army of Ukraine and Project Ddosia by NoName(057)16, is attempting to create a community of patriotic hackers while promoting its DDoS services for financial gain. It has both an informative and a chat channel, where the group updates its followers on current campaigns. These types of social communities, such as the one behind Passion, can seriously threaten organizations due to their ability to adapt, work together, and share resources."
PyPI malware: Check Point researchers have found two malicious Python libraries (Python-drgn and Bloxflip) uploaded on the PyPI package repository. The packages contained malicious code that disabled Windows Defender, then downloaded and executed additional executables.
Crypto drainers: A new type of phishing technique named a "crypto drainer" is growing in popularity among cybercriminal groups. The term of crypto drainer refers to a custom phishing page that entices victims into connecting their wallets with an offer to mint NFTs on their behalf. However, as soon as victims attempt to mint NFTs, the crypto drainer page siphons both a user's cryptocurrency and the desired NFT to an attacker's wallet. According to Recorded Future, there are several crypto drainer templates currently being advertised on underground cybercrime forums, and they are growing in popularity.
DDoS attacks on the financial sector: A joint report from Akamai and FS-ISAC has found that DDoS attacks against the global financial sector went up by 22% in 2022 as a result of the war in Ukraine and the return of hacktivist groups. The rise in DDoS attacks was particularly felt across Europe, where attacks jumped by 73% compared to the previous year. DDoS attacks accounted for 38% of all attacks last year against the financial sector, with account compromises taking the second spot with 15%.
Pig butchering apps: Sophos says it recently discovered that malicious apps used for "pig butchering" financial scams weaseled their way into the official Apple and Google mobile app stores. Two apps made it on the App Store and one app made it on the Play Store, but all were removed following Sophos' report. Pig butchering is a relatively new term that is used to describe a type of scam where threat actors approach victims on dating sites and move conversations to financial topics, trying to lure victims into making various financial or cryptocurrency investments.

Malware technical reports
MalVirt: Cybersecurity firm SentinelOne has discovered a new malware loader named MalVirt that is currently being used as a first-stage malware in infections that eventually end up dropping the Formbook infostealer. The malware's name comes from "malvertising" and "virtualization." This is because the malware is distributed via malicious ads, and the malware runs in a virtualized environment built using the KoiVM virtualization software.
TZW ransomware: AhnLab reports that a new ransomware strain they named TZW has been spotted in attacks against South Korean users.
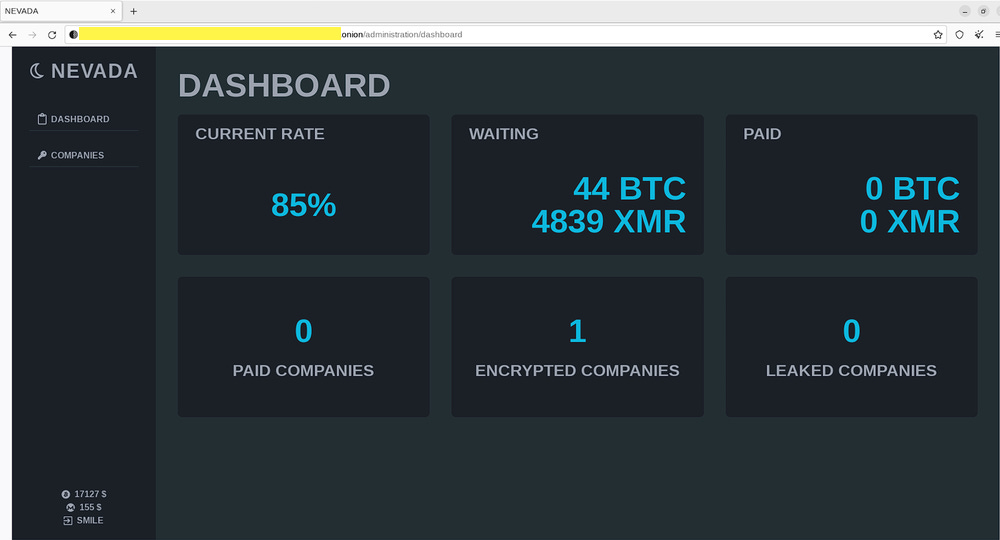
Nevada ransomware: Also this week, a new Ransomware-as-a-Service (RaaS) was launched via an ad on an underground cybercrime forum. The RaaS is named Nevada and claims it can encrypt Windows, Linux, and ESXi systems. The ransomware has already attracted the interest of many initial access brokers and affiliates because it promised to let them keep 85% and even 90% of any successful ransom payment. Spotted by security firm Resecurity, the company says it already saw threat actors from Iran, China, the EU, and ex-USSR countries showing interest in the service.
APTs and cyber-espionage
IceBreaker: A new advanced persistent threat (APT) group named IceBreaker has been seen launching operations against online gaming and gambling companies since at least September 2022. According to a report from threat intel firm Security Joes, the group uses novel never-before-seen malware, which it usually plants inside companies via their customer support agents. Security researchers say the group uses the online tech support chats available via the companies' official websites to lure customer support agents to a website supposedly holding a screenshot of their "problem." However, the link actually leads to a malicious file that installs the group's malware, a custom-built backdoor, or the Houdini remote access trojan.
Lazarus APT: WithSecure researchers have discovered a new Lazarus intelligence gathering operation targeting medical research and energy organizations. According to researchers, the attacks exploited unpatched Zimbra devices for initial access to the target's network, where they planted web shells and other malware to move laterally across a victim's infrastructure and exfiltrate large quantities of data. While there were several indicators to link this campaign to the Lazarus group, WithSecure says this was confirmed beyond any doubt when one of the group's operators connected to one of the Zimbra web shells using a North Korean IP address.
UAC-0114 (Winter Vivern): Ukraine's CERT team says a threat actor known as UAC-0114 (Winter Vivern) has been luring potential targets on a website mimicking Ukraine's Foreign Affairs Ministry. The website asks visitors to download software for "scanning infected PCs on viruses" on their systems, software that is laced with a basic backdoor. CERT-UA says that following a joint investigation with Poland's CERT team they discovered similar websites operated by the same threat actor that mimicked the websites of the Ministry of Defense of Ukraine, the Security Service of Ukraine, and the Polish Police.
UAC-0010 (Gamaredon, Armageddon): The State Cyber Protection Center of Ukraine has published a technical report [PDF] detailing the TTPs used by the UAC-0010 (Gamaredon, Armageddon) APT in recent attacks targeting Ukrainian organizations. Previously, Ukrainian officials publicly linked the Gamaredon group to the Sevastopol office of the Russian FSB intelligence agency.
APT34: Trend Micro researchers have discovered a new APT34 (OilRig) campaign that used a novel piece of malware, a new backdoor named RedCap.
Vulnerabilities and bug bounty
QNAP disaster: IoT search engine Censys says that roughly 98% of the 30,000 QNAP NAS devices it currently tracks are still unpatched for an SQL injection vulnerability tracked as CVE-2022-27596. QNAP patched the vulnerability earlier this week, but because it is trivial to exploit and the exploitation process does not require authentication, Censys expects the vulnerability to be quickly abused by ransomware gangs, as it happened many times before. Furthermore, the number of vulnerable devices could be even higher as Censys says there are another 37,000 QNAP systems online for which it could not obtain a version number but which are also likely vulnerable as well.
Major Thunderbird security update: Mozilla has released a patch for its Thunderbird email client that addresses a major security update where the app did not check a certificate's OCSP revocation status when verifying S/Mime signatures. This meant that emails signed with revoked certificates could appear valid. Thunderbird versions from 68 to 102.7.0 were affected by this bug.
Cisco security updates: Five security bulletins have been published for Cisco devices this week.
vBulletin RCE: After the RCE discovered in the myBB forum software last week, there's a pre-auth RCE now in vBulletin, although, as Ambionics put it, exploitation may be tricky.
CrushFTP vulnerability: Trustwave SpiderLabs researchers have discovered an input validation vulnerability in the CrushFTP application that can be used to delete an app's all users.
Smart EV charger vulnerabilities: SaiFlow security researchers have discovered a set of vulnerabilities in the firmware of Smart EV charging stations that can be used to shut down the charger, spoof a driver's identity, cause billing discrepancies, or just steal energy.
CVE-2023-22374 (F5 Big-IP): Rapid7 researchers have published a detailed write-up on CVE-2023-22374, a vulnerability in the iControl SOAP interface of F5 BIG-IP network load balancing devices. The bug can allow threat actors to execute code on a device, but exploitation is limited to post-auth scenarios only. F5 was still working on a patch.
Rockstar patches exploit: Rockstar Games has patched that RCE exploit that allowed cheaters to ban GTA Online player accounts, steal their in-game funds, or corrupt their game installation.
Bad CVSS scores: Vulnerability intelligence company VulnCheck has analyzed more than 25,000 entries from the NIST vulnerability database (NVD) that contained a CVSS rating from both NIST and the product vendor. VulnCheck says that around 14,000 of these 25,000 vulnerabilities had conflicting scores where the vendors and NIST had assigned different ratings for the vulnerability's severity. VulnCheck says that despite the large number of entries, most of these came just from 39 vendors, suggesting that some companies are intentionally downgrading the severity of their own vulnerabilities.
"Incorrect scores impact immeasurable vulnerability management and remediation plans all over the world. Potentially resulting in many wasted hours diverting resources away from the vulnerabilities that should be prioritized."
Infosec industry
Tool update: Ronin v2 is out! Ronin is a collection of security tools written in Ruby, used primarily for security research and development.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.




