Risky Biz News: Two arrests in Operation Magnus
In other news: CSRB to look at China's telco hack; Japanese man sentenced for developing ransomware with AI; major hack at Canada's Revenue Agency.

You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Law enforcement agencies from multiple countries have disrupted the operations of the Redline and META infostealers.
The takedown took place on Monday as part of what authorities called Operation Magnus.
Officials seized three servers in the Netherlands, took control of two domain names, and arrested two other suspects in Belgium.
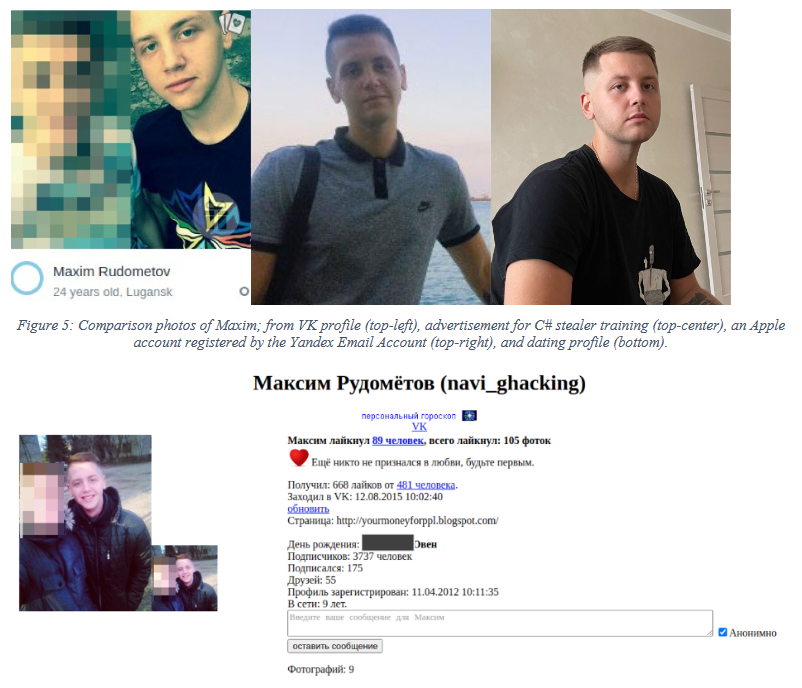
The US Justice Department also charged Russian national Maxim Rudometov for developing and managing the RedLine infostealer. TechCrunch has a good piece on how authorities tracked him down following a series of OpSec mistakes.
The two individuals detained in Belgium are believed to have bought access and used the infostealers. One has been released, while the second is still in custody.
Officials say they have recovered data from the seized servers on the stealer's customers and past victims. The data included usernames, IP addresses, passwords, and payment details, and officials said they plan to go after RedLine and META's customers.
The servers also allowed officials access to the malware source code, backend panels, licensing servers, REST APIs, and access to various Telegram bots that were being used to sell access to the malware.
On the day of the takedown, law enforcement sent a video to all RedLine and META customers announcing Operation Magnus as the "final update" to both malware strains. The video is below.
The same video was shared via the Telegram bots and channels before they were taken down and on underground hacking forums where the two malware strains were being advertised.
It is very likely that authorities will use the seized data to go after RedLine and META's customers as they did in the past with other infostealer and RAT operations.
Law enforcement agencies from the Netherlands, the UK, the US, Portugal, and Belgium participated in the Operation Magnus takedown.
Officials said they moved against the services because infostealer operations are having an increasing role in the cybercrime ecosystem. Data collected by infostealers often includes passwords and cookies for a victim's online and work accounts. This data is sold online to other crooks, who use it to take over accounts at sensitive targets. These breached accounts are used for lateral movement, sending spear-phishing emails, and deploying ransomware.
Breaches, hacks, and security incidents
Israel breaches Iran's radar system: Israel is believed to have "breached" (unclear what that means) Iran's radar systems before the Israeli air force launched a missile attack inside Iran. [Additional coverage in the Jerusalem Post]
Crypto rug pulls: The Sharpei and Essence Finance cryptocurrency projects appear to have rug-pulled and ran away with people's money. YOLO!
TfL cyberattack: The London Centric newsletter has published the "utter shitshow" inside story of the recent cyberattack that hit Transport for London.
Free cyberattack: French internet service provider Free has suffered a major security breach. A hacker claims to have breached the company and stolen the personal data of millions of customers. The stolen data allegedly includes names, emails, dates of birth, home addresses, and bank account numbers for at least 19.2 million customers. The data is being sold online on hacking forums and Telegram channels. Free is France's second-largest internet service provider. [Additional coverage in Connexion France]
CRA hacks: Hackers have breached thousands of accounts at Canada's Revenue Agency and stolen at least CAD$6 million via bogus refund claims. The agency says most of the hacked accounts were managed by H&R Block Canada, the country's largest tax preparation firm. CRA says the hackers took control of the accounts, changed deposit information, and submitted false returns to pocket government refunds. The agency is now under fire for not disclosing the incident until it was discovered by reporters. [Additional coverage in the CBC]
UK data breach stats: The ICO says that almost 30 million of the UK's 67 million total population has had its data lost or stolen in cyberattacks.
BGP hijack incident: Kentik looks at a BGP hijack incident from the end of September when Uzbek telecom provider Uztelecom hijacked and redirected more than 3,100 routes through Russia's Rostelecom.
General tech and privacy
Firefox 132: Mozilla has released Firefox 132. New features and security fixes are included. The biggest features in this release include support for a post-quantum key exchange mechanism for TLS 1.3 and blocking favicons if they are loaded via HTTP.
SMTP DANE in Exchange: Microsoft has added support for SMTP DANE in its Exchange email server.
Google and Microsoft spat: Microsoft has accused Google of running shadowy lobbying campaigns in the EU. The company says the secretly-funded campaigns aim to discredit Microsoft and mislead the public via lobbying organizations and paid industry commentators and academics.
Google's ridiculous Russian lawsuit: Seventeen Russian TV channels have filed a lawsuit in a Moscow court asking for two sextillion rubles from the company as a financial penalty for suspending their YouTube accounts. [Additional coverage in RBC]
More WordPress drama: Automattic and the WordPress.org team have ordered organizers of WordCamp conferences to delete old tweets, share their social media account passwords, and disable MFA.
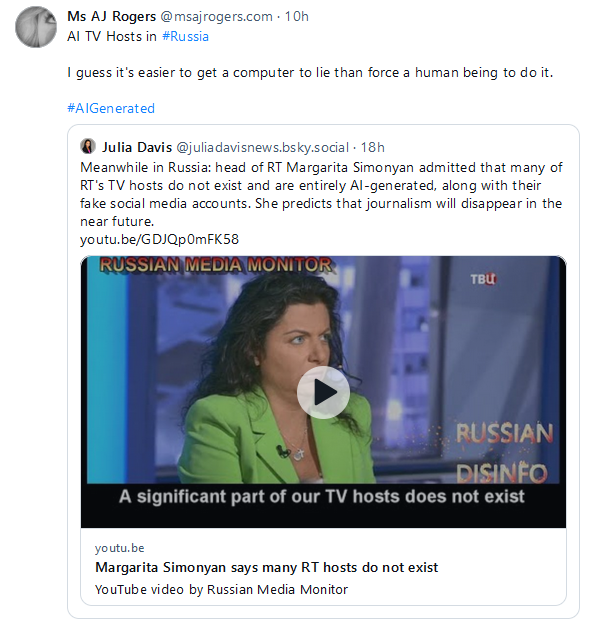
RT's AI presenters: RT head Margarita Simonyan admitted that the "news organization" is now using multiple AI-generated presenters.
Government, politics, and policy
CSRB to look at China's telco hack: DHS officials plan to have the Cyber Safety Review Board look at the circumstances and failures that enabled a major Chinese hack of US telcos. Officials are currently waiting for the FBI and CISA to finish their investigation of the hack. A Chinese group known as Salt Typhoon breached the networks of AT&T, Lumen, and Verizon earlier this year. US officials believe the hackers gained access to the system for court-approved wiretapping systems. Recent reports claim the hackers used the systems to intercept calls for Donald Trump, JD Vance, Senate Majority Leader Chuck Schumer, and members of the Harris-Walz campaign. [Additional coverage in the WSJ]
CISA International Strategic Plan: CISA has published its first-ever International Strategic Plan, a document detailing how the agency will engage with foreign partners to strengthen cybersecurity defenses. Named goals include:
- Bolster the Resilience of Foreign Infrastructure on Which the U.S. Depends.
- Strengthen Integrated Cyber Defense.
- Unify Agency Coordination of International Activities.
UN cybercrime treaty: A group of six US Democrat senators has sent a letter to President Biden urging the White House to rebuke the proposed UN cybercrime treaty. [Additional coverage in The Record]
UK's removal of Chinese security cameras: The UK government says it removed over 50% of Chinese-made security cameras from sensitive sites, such as government buildings and military bases. The government says it expects complete removal by April next year. Officials ordered UK sensitive sites to remove Chinese-made cameras in November 2022, citing national security risks. [Additional coverage in the UK Defense Journal]
Five Eyes Secure Innovation: Cybersecurity agencies from Five Eyes countries have published guidance on how tech startups can protect intellectual property from cyber and economic espionage. The agencies released the guidance a year after they held a summit to discuss China's constant theft of intellectual property from Western nations. The guidance primarily focuses on making companies aware of the crucial role proper cybersecurity practices can play in securing their IP.
Bundestag phishing test: The German Parliament's security team is running phishing tests to see if MPs are falling to basic attacks. According to Der Spiegel, most recipients did not fall for the suspicious emails and forwarded the suspicious emails to the Bundestag's IT team. [Additional coverage in Der Spiegel]
Netherlands says CN and RU are intensifying attacks: The Dutch government says that Russia and China are stepping up their cyber attacks on the Netherlands and its allies. The National Coordinator for Counter-Terrorism and Security (NCTV) says both countries are infiltrating critical infrastructure to prepare for future sabotage. In addition, both countries are increasingly hiring private companies and hacktivists to support and mask their objectives. [Additional coverage in the NLTimes]
Russia legalizes crypto-mining: Russian President Vladimir Putin has signed into law a bill that legalizes crypto-mining in the country. Miners are exempt from taxes as long as they stick to electricity consumption limits. The government can also ban crypto-mining across entire regions whenever it needs. [Additional coverage in RBC]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
Arrests, cybercrime, and threat intel
Japanese man sentenced for AI ransomware: A Japanese court has sentenced a 25-year-old man to a three-year prison sentence for using AI tools to create ransomware. The court suspended his sentence for four years. Ryuki Hayashi confessed to his crimes shortly after he was arrested earlier this year in May in the city of Kawasaki. Hayashi used his phone and computer to access AI coding tools, bypass safety restrictions, and generate the ransomware code. Officials said there were no reports of damage caused by the ransomware. [Additional coverage in the Yomiuri Shinbun] [h/t DataBreaches.net]
JPMorgan sues customers over infinite money glitch: American bank JPMorgan Chase is suing customers who allegedly stole hundreds of thousands of dollars from ATMs by exploiting a technical glitch. The thefts took place in August after details of the bug went viral on TikTok as the "Chase infinite money glitch." The glitch allowed customers to open accounts using fake deposit checks and withdraw money via Chase ATMs before the check bounced. The bank is now suing the biggest exploiters, including a Houston man who stole $290,000 from one counterfeit $335,000 check. [Additional coverage in CNBC]
You Dun group: The DFIR Report team has published a report on You Dun, a Chinese-speaking hacking group involved in DDoS attacks, illicit data sales, ransomware attacks, and selling "penetration testing" services. Researchers found the group after discovering one of its servers with an open directory holding most of its hacking tools.
Chenlun/Sinkinto01: The DomainTools team looks at recent updates in the operations of a phishing group known as Chenlun (or Sinkinto01).
New job scam spotted: Proofpoint looks at a recent job scam portal the company investigated. It's quite a complex affair.
Election scams are coming: The FBI is here with the obligatory "beware of election-themed scams" warning.
ClickFix campaigns everywhere: Kaspersky says that more and more cybercrime groups are adopting the ClickFix social-engineering technique as part of their attacks. This comes after a report last week that APT groups are now also using the technique. The technique involves hijacking a user's clipboard with malicious commands and then tricking the user into running those commands. It's dumb, but it works with non-technical users, and there are a lot of those.
Malware technical reports
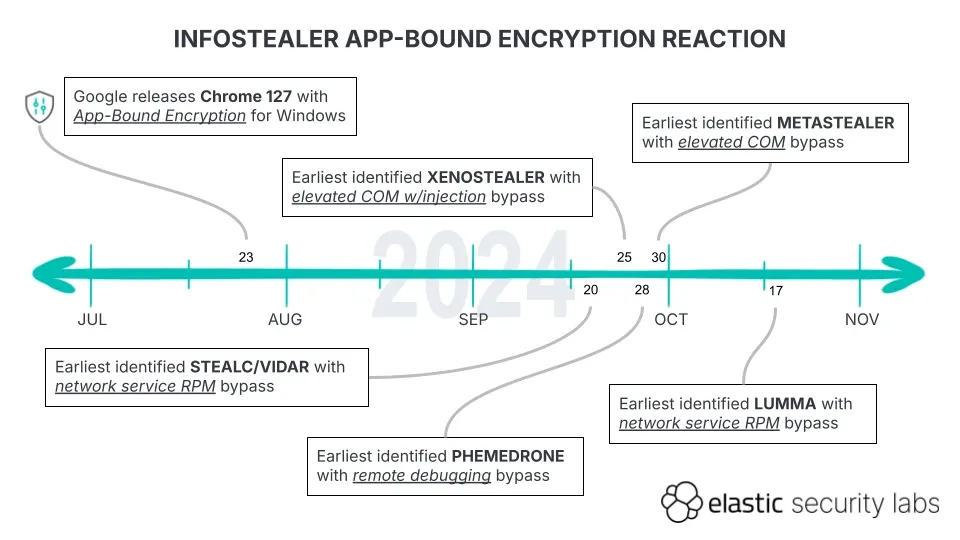
Infostealers' Chrome bypasses: Elastic's security team has published a technical report on how various infostealers are bypassing Chrome's new cookie encryption scheme (which we covered here at the end of September).
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
APTs, cyber-espionage, and info-ops
LightSpy's iOS implant: ThreatFabric looks at the iOS version of LightSpy, a spyware implant used by the LightSpy APT group. The malware also has versions for macOS, Windows, Linux, and home routers.
Evasive Panda's CloudScout: ESET has published a report on CloudScout, a malware strain used by Chinese APT Evasive Panda in attacks against Taiwan. The tool has been found in intrusions at a Taiwanese government agency and a religious organization. The tool is primarily used to scan for cloud services and steal data.
Hurricane info-ops: US intelligence officials say that Russian, Chinese, and Cuban operatives have worked to amplify misinformation and disinformation about two major hurricanes (Helene and Milton) that hit the US this fall. The common theme in all of these was that the US government had abandoned its people in order to divert funds to other countries, such as Israel, Taiwan, and Ukraine. Oh, those silly foreign actors! Always so attentive to the US budget. [Additional coverage in NBC]
UK sanctions Russian disinfo farms: The UK government has sanctioned three companies and individuals responsible for Russian disinformation campaigns. Officials say the three companies are responsible for a vast malign online network, commonly known as Doppelganger. Its activity has revolved around using fake news articles and documents to undermine the West's military and financial support of Ukraine. Sanctions were levied against the Social Design Agency, Structura, and ANO DIALOG. All three were also sanctioned by the US earlier this year for the same reason.
EU calls out Russia's info-ops in Western Balkans: European Commission President Ursula von der Leyen has publicly called out the Russian government for influence ops in Western Balkan states designed to divide countries and stoke anti-EU sentiments. [Additional coverage in The Record]
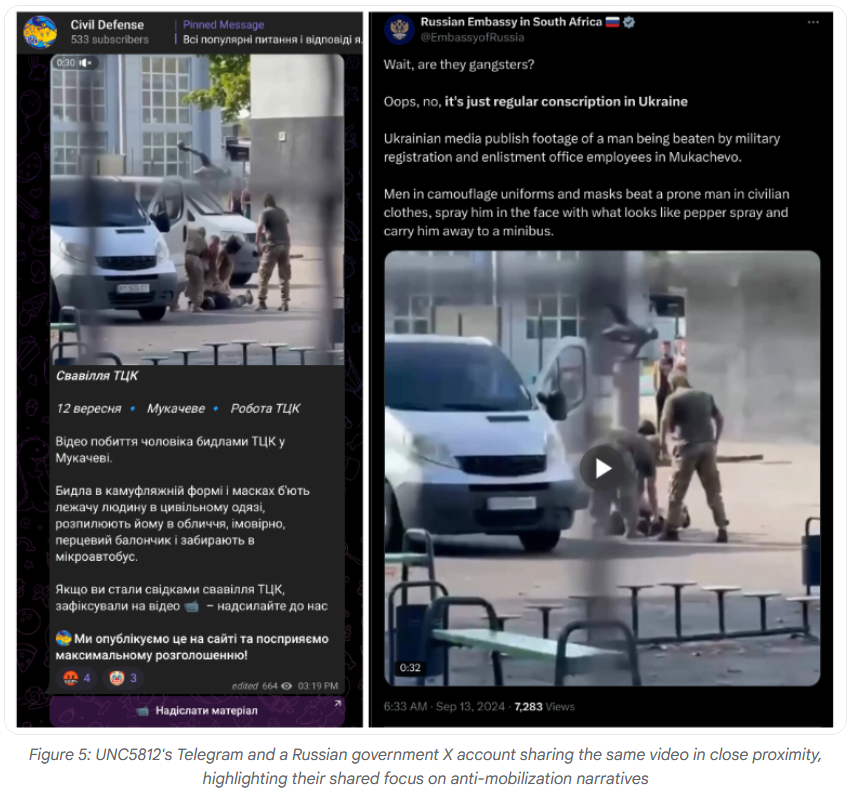
UNC5812: Google's Mandiant division has published a report on UNC5812, a Russian APT group that targeted Ukrainian conscripts and reservists with malware. This is the same campaign disclosed by Ukrainian officials two weeks ago. According to Google, the malware distribution campaign was also accompanied by an anti-mobilization influence op that took place via Telegram, often supported by official Russian government accounts elsewhere.
"We judge that as long as Telegram continues to be a critical source of information during the war, it is almost certain to remain a primary vector for cyber-enabled activity for a range of Russian-linked espionage and influence activity."
Vulnerabilities, security research, and bug bounty
Apple security updates: Apple released a massive patch on Monday with fixes for all its major products.
LoLLM RCE: CyberArk researchers have found a remote code execution attack in the LoLLM hub for LLMs.
ChatGPT-4o jailbreak: 0Din researcher Marco Figueroa has discovered a technique that can bypass ChatGPT-4o safeguards and allow threat actors to generate malicious content. The technique involves encoding malicious instructions in the hexadecimal format. Figueroa says ChatGPT decodes and processes each instruction separately, allowing attackers to hide dangerous instructions.
BitLocker PIN bypass attack: Orange's security team has found a way to recover BitLocker PINs by sniffing the TPM module.
New Windows Themes spoofing vulnerability: ACROS security researchers have found a variation of CVE-2024-38030, a Windows Themes spoofing vulnerability that Microsoft patched back in July.
TeamViewer EoPs: CyFirma researchers have published an analysis of two elevation of privilege vulnerabilities in the TeamViewer app (CVE-2024-7479 AND CVE-2024-7481). Both issues were patched at the end of September.
Infosec industry
Appin story back online: An Indian court has revoked an injunction against a Reuters article that exposed Indian hacker-for-hire company Appin.
Acquisition news: Email security firm Proofpoint has announced plans to acquire Data Security Posture Management (DSPM) platform Normalyze.
New tool—Chrome App-Bound Encryption Decryption: Alex Hagenah has released Chrome App-Bound Encryption Decryption, a tool to bypass and decrypt Chrome's new cookie encryption scheme.
New tool—Offensively Groovy: TrustedSec's Brandon McGrath has released Offensively Groovy, a repository that documents how to use Groovy scripts for post-exploitation purposes.
New tool—UDPz: Cybersecurity firm FalconOps has released UDPz, a speedy, portable, cross-platform UDP port scanner written in Go.
Threat/trend reports: Check Point, Cloudflare, CyFirma, Forescout, the NCC Group, Norton (Gen Digital), ProtectAI, Trustwave, and Veracode [PDF] have recently published reports and summaries covering various infosec trends and industry threats.
BSides Canberra 2024 videos: Talks from the BSides Canberra 2024 security conference, which took place at the end of September, are now available on YouTube.
Risky Business Podcasts
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.




