Risky Biz News: US and UK ban Chinese equipment on national security grounds
In other news: Major Twitter data leak appears to be real; Eritrea shuts down darknet market; Russia detains phone fraud suspects.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Representatives from the US and UK governments have banned the use of Chinese networking and surveillance equipment, citing "national security"-related fears as the grounds for their decisions.
In the US, the US Federal Trade Commission has banned the import and sale of networking and video surveillance equipment from Chinese companies Dahua, Hikvision, Huawei, and ZTE.
In the UK, the Parliament has instructed government departments to cease the deployment of security cameras from Chinese companies on "sensitive sites" such as government buildings and military bases.
British officials said that Chinese-made security cameras should not be connected to core networks and that government departments should also consider removing and replacing existing equipment even before "scheduled upgrades."
Both the US and UK bans come after the intelligence agencies in both countries previously warned against the use of equipment from Chinese companies, cautioning that Chinese equipment could be used for digital surveillance, digital sabotage, and economic espionage.
Both Dahua and Hickvision had already lost a large chunk of their market in the US after the US Treasury sanctioned both companies for providing the Chinese government with facial recognition and video tagging solutions in the government's Uyghurs oppression efforts.
The UK ban does not any vendors, but human rights advocates in the country have been railing against the same two aforementioned companies for years—although, the UK government appears to anticipate that other vendors and state-owned companies might be involved in the same shenannigans or susceptible to government pressure via its broad and dangerous National Intelligence Law.
Chinese state-owned CCTV firms Hikvision & Dahua are facilitating human rights abuses abroad.
— Big Brother Watch (@BigBrotherWatch) 12:43 PM ∙ Sep 27, 2022
They must be banned in the UK.
👏@trussliz⤵️
Breaches and hacks
Twitter data leak: A vulnerability reported via the HackerOne platform was used to mass-harvest the account details of Twitter users, including private information such as phone numbers and email addresses. An initial dataset compiled via this vulnerability and containing the details of more than 5.4 million Twitter accounts was allegedly traded on underground hacking forums earlier this year, while an even larger second dataset has also popped up on hacking forums over the past few days. According to reports, this second dataset allegedly contains details on tens of millions of Twitter accounts.
No WhatsApp breach: A threat actor has been circulating an alleged leak of WhatsApp data. It's fake. It's just a list of phone numbers, according to Alon Gal of Hudson Rock.
Zwijndrecht police ransomed: The Ragnar Locker ransomware gang has hacked and is now extorting the police department of the Belgian city of Zwijndrecht. The group claims to have obtained information detailing thousands of license plates, speeding fines, and even criminal investigations, ranging from 2006 to September 2022. Police officials said they detected the attempt to encrypt their servers and shut down their network for two weeks while they investigated and restored services. Ragnar Locker has already leaked some of the files on their dark web leak site.
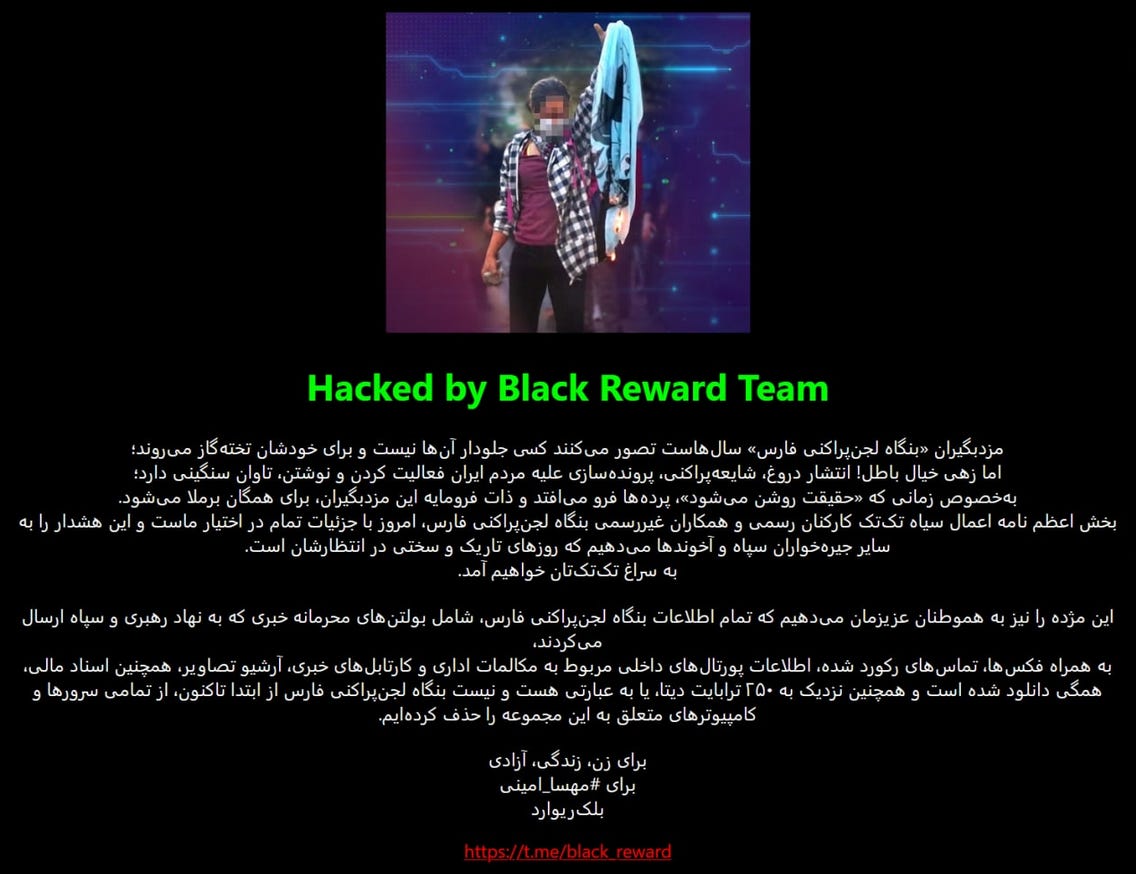
Fars news agency hack: Iranian hacktivist group Black Reward said it hacked and wiped the servers of Fars News, an Iranian news agency managed by the Islamic Revolutionary Guard Corps. The agency's website was also defaced with a message of support for anti-government protesters. Fars News and Iranian government officials confirmed the hack and blamed the incident on Israel and other foreign countries. On the other side of this constant Iran-Israel "hacktivism" duel, Israel also confirmed last week that an Iranian hacking group known as Moses' Staff breached an Israeli security company and stole and released footage of last week's twin bombings at Jerusalem bus stops.
General tech and privacy
More Windows 11 protections: Microsoft will add a new detection and logging capability to Windows 11 that will allow security tools to detect when malware might attempt to bypass KASLR protections for the Windows kernel. The feature, a new ETW event, is undergoing testing in Windows 11 23H2 insider versions.
Government, politics, and policy
Greece's spyware scandal: Reporters from Greek news outlet DocumentNews said they found the server that was used to infect the phones of Greek government officials and journalists with the Predator spyware—edolio5[.]com.
Digital sovereignty: Speaking at a digital forum last week, Russia's Minister of Digital Transformation said that after most foreign IT companies have left Russia following EU and US sanctions, Russia has now achieved "digital sovereignty" (I don't think that's how digital sovereignty works, but ok, whatever). In addition, the Russian official also said that even if a large number of IT specialists have left Russia, the number is not so large to "cause irreparable damage to the [IT] industry." These are some very funny statements to make on the same day that rumors emerged that Russia's largest IT company—Yandex—was looking to leave the country for greener pastures.
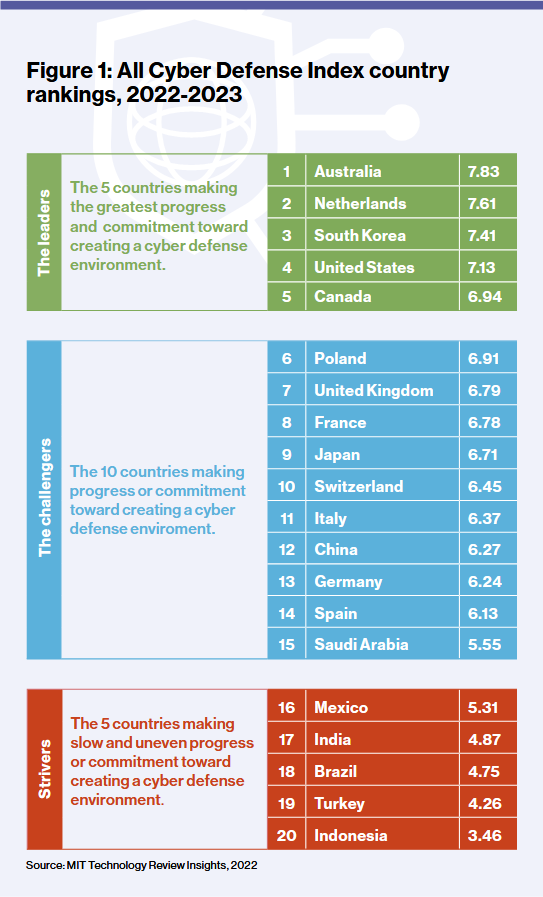
Defense Cyber Index: While the Belfer Center is known for its national offensive cyber index, MIT has joined the rank-your-country party with an index on which state has the best defensive capabilities. Topping the list for the year is Australia, the Netherlands, and South Korea.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Darknet market takedown: Interpol said that authorities in Eritrea have taken down a darknet market that was selling hacking tools and cybercrime-as-a-service components. The takedown was part of a joint operation with AFRIPOL to crack down on African cybercrime gangs active inside African countries. This operation has also led to the arrest of ten suspects linked to online scams and fraud activities, the recovery of $150,000 from groups involved in data infringement and copyright cases, and takedowns of server infrastructure hosting malware, botnets, phishing sites, and online extortion operations.
Russian scammer gang detained: Russian authorities said they detained three suspects from the city of Kolpino, near Sankt Petersburg, for their alleged role in an international phone fraud network. Officials said the gang used more than 12,000 SIM cards to call victims as part of a scheme where they warned them about an impending theft from their bank account and tricked them into transferring funds into so-called "safe accounts"—that were under their control. The three suspects hosted IT infrastructure for the gang, which also consisted of members located outside Russia's borders, according to the Russian Ministry of Internal Affairs.
Malicious Docker Hub images: Cloud security firm Sysdig said it identified 1,652 malicious Docker images uploaded on the official Docker Hub portal. More than a third contained cryptomining code, while others contained hidden secret tokens that an attacker could later use as a backdoor into a server. Other Docker images contained proxy malware or dynamic DNS tools.
Potao source code: A threat actor is claiming to sell the source code of Potao, a malware strain historically linked to the Sandworm APT. Gonna chuck this into the "very likely scam" bin.
Infostealer fingerprinting: Equinix security researcher William Thomas has a write-up on how you can discover infostealer infrastructure by using IoT search engines to fingerprint their control panels.
New npm malware: Check out GitHub's security advisory portal for details.
Twitter amnesty watch: After super-genius Elon Musk announced plans to reinstate banned accounts on Twitter, threat researchers are now keeping an eye on how many of the old Russian political propaganda accounts will be coming back online. An archive of those can be found here. In the meantime, enjoy watching Twitter devolve into a right-wing cesspool with conspiracy theories constantly trending on the platform, driven by abhorrent bot networks. Oh, and death threats, personal attacks, and account reporting raids. Let's not forget those lovely things. fRe3 sPeEcH!!!
Malware technical reports
Zanubis: Something we missed two months ago is this technical report on Zanubis, a new Android banking trojan. More on how to find samples from VT.
Koxic and Wiki: AhnSec researchers have reports on Koxic and Wiki, two new ransomware strains they're seeing distributed in South Korea.
Brute Ratel: A Chinese malware researcher going by the name of Panda Zhengzheng has published a breakdown of Brute Ratel C4, a pen-testing tool that has recently been abused by various threat actors. Together with Metasploit, Cobalt Strike, Empire, and Sliver, Zhengzheng says these five red team utilities are also known as Five Tigers in the Chinese cybersecurity ecosystem.
APTs and cyber-espionage
New Sandworm ransomware: ESET has discovered a new ransomware strain named RansomBoggs that was deployed against Ukrainian organizations last week. ESET said it linked the ransomware to a threat actor known as Sandworm, one of Russia's military cyber units. Researchers said they found links between RansomBoggs and previous Sandworm malware deployed against Ukrainian targets, such as ArguePatch, CaddyWiper, and Industroyer2. Early signs suggest this may be another data wiper disguised as ransomware.
APT-C-09: Qihoo 360 researchers published a report on recent attacks carried out by the APT-C-09 (Patchwork) threat actor, where they used spear-phishing to infect their targets with the BADNEWS backdoor.
Vulnerabilities and bug bounty
Chrome zero-day: Google has released a security update for the Chrome web browser to fix a zero-day vulnerability exploited in the wild. Google said it tracks the zero-day as CVE-2022-4135 and describes it as a heap buffer overflow in the Chrome GPU component. The vulnerability was discovered by one of the Google TAG researchers. This marks the eighth Chrome zero-day discovered this year.
CVE-2022-34721: CYFIRMA researchers said they believe that a threat actor is using an exploit for CVE-2022-34721 to target Windows systems that have yet to be patched. The vulnerability is a remote code execution in the Windows IKE protocol that Microsoft patched in September. CYFIRMA said the attacks are linked to a campaign named "流血你"—which translates from Chinese to "bleed you." An exploit for this was shared on GitHub in September.
Infosec industry
API security: Google Cloud said that half of the 500 companies it surveyed in a report released last week have experienced at least one API security incident over the past 12 months. Furthermore, the same survey identifies misconfigurations as the main threat to API infrastructure.




