Risky Biz News: Trickbot dev arrested in Moscow
In other news: Indian crypto exchange hacked for $230 million; UK wants mandatory ransomware reporting; new Port Shadow attack on VPNs.

This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Russian authorities have allegedly arrested a member of the Trickbot cybercrime gang in Moscow this week.
According to a report from Russian news channel Baza, authorities have detained a 37-year-old man named Fedor Andreev on the morning of July 15 in a house in South Moscow.
Andreev was allegedly detained based on an Interpol red notice issued by Germany in May.
He is one of eight individuals identified and charged following Operation Endgame—a Europol operation that took down command and control servers for six of the world's largest botnets (Bumblebee, IcedID, Pikabot, Smokeloader, SystemBC, and Trickbot).
According to German authorities, Andreev has been a member of the Trickbot gang since 2020, where he went under the hacker pseudonyms of "Azot" and "Angelo."
He was charged in Germany on cybercrime charges, fraud, and extortion. Andreev is believed to have helped the Trickbot gang maintain server infrastructure, infect new devices, and facilitate ransomware attacks.

Breaches, hacks, and security incidents
Bassett Furniture ransomware attack: US furniture maker Bassett Furniture is dealing with a ransomware attack that crippled its production facilities for almost a week. The company says new furniture production has ground to a halt. Customers can still buy existing inventory, but Bassett can't commit to honoring new orders. Bassett is one of the largest furniture makers in the US, with more than 100 stores across the country.
Hackney ransomware attack: The UK ICO has published a report on how the ransomware attack on the Hackney London borough unfolded back in October 2020. tl;dr: RDP on a "kiosk" account using the "kiosk" password.
New SiegedSec hacks: Hacktivist group SeigedSec claims it hacked two Israeli companies to show its support for the Gaza civil population. The two companies are Raam Security, which provides armed guards and security in Israel, and Sharfstein Food Technologies, the country’s top manufacturer of food machinery and equipment. [Additional coverage in the Daily Dot]
MarineMax breach: One of the world's largest boat and yacht retailers is notifying customers of a security breach. MarineMax says a ransomware gang gained access to its systems in March and stole the personal details of more than 123,000 customers. The breach is extremely sensitive as it contains details on individuals with considerable financial resources, who are typically the prime targets for extortion and threats. [Additional coverage in BleepingComputer]
Fractal ID breach: Blockchain identity platform Fractal ID suffered a data breach on July 14. The company says that a threat actor gained access to an employee account and ran an API script that collected personal data from customer accounts. Fractal says the attacker collected data for around 0.5% of all its users. The company's services are used by crypto platforms to verify the identity of registered users. Fractal says the attacker collected names, email addresses, wallet addresses, phone numbers, physical addresses, and ID scans. At least four crypto platforms (Gnosis Pay, Polygon, Ripple, and NEAR) have confirmed that their users were impacted. [Fractal ID's data breach notification/PDF]
USPS privacy snafu: TechCrunch reports that USPS was inadvertently sharing customer postal addresses with Meta, LinkedIn and Snap via tracking pixels embedded on its website.
Mt. Gox brute-force attacks: Multiple users of the now-defunct Mt. Gox cryptocurrency exchange are reporting that their wallets are seeing brute-force attacks in the aftermath that they will soon receive their stolen funds back. [Additional coverage in Coinpedia]
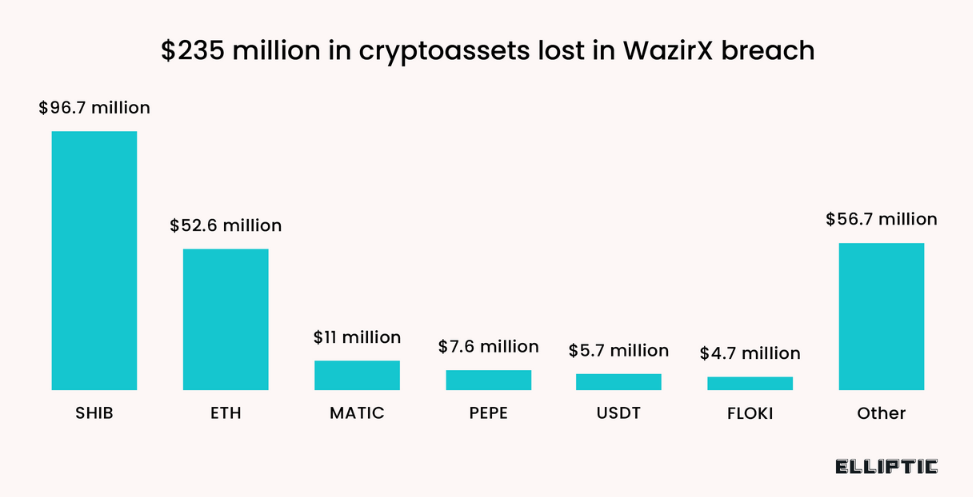
WazirX crypto-heist: Indian cryptocurrency exchange WazirX has suspended operations on Thursday after suffering a major security breach. The company is believed to have lost around $235 million worth of assets. According to reports, the funds were stolen in one suspicious transaction that went out from one of the WazirX wallets. Blockchain security firm Elliptic linked the attack to North Korean hackers. The incident is the year's second-largest crypto-heist. This year's largest hack remains the $305 million heist of Japanese cryptocurrency trading platform DMM Bitcoin. [Additional coverage in TechCrunch]
General tech and privacy
Another case of commercial ad data surveillance: Reporters from BR24 and Netzpolitik have proven once again how easy is to buy ad data from commercial data brokers and track military and intelligence operatives. In this case, they tracked NATO troop exercises and Ukrainian soldiers training in Germany.
Google SERP changes: A new report claims that Google appears to have switched to a no-index default policy and is refusing to crawl new content unless it deems it necessary.
Brazil tells Meta to knock it off: The Brazilian government has ordered American social media company Meta to stop training its AI algorithms using the data of Brazilian citizens. [Additional coverage in PCMag]
Government, politics, and policy
UN Cybercrime Convention: Despite months-long negotiations, member states have not made any meaningful changes to the upcoming UN Cybercrime Convention, which still grants countries expanded surveillance powers with no human rights and privacy safeguards.
EU ransomware crackdown: As part of its bid to get re-elected as the European Commission's President, Ursula von der Leyen has promised [PDF] to crack down on ransomware attacks hitting EU healthcare systems. She was voted a second term. [Additional coverage in The Record]
UK Cyber Security and Resilience Bill: Britain's new Labour government says it would introduce a new bill to strengthen the country's cyber defenses. The new Cyber Security and Resilience Bill will include a mandatory reporting requirement for companies hit by ransomware attacks. The new requirement will not be mandatory for the entire private sector but only for regulated entities. This includes critical infrastructure providers, but the government said it would expand its scope to also include some IT service providers. [Additional coverage in The Record and The Independent]
Canada CSE report: Canada's Communications Security Establishment agency, the country's NSA equivalent, has published its yearly report for 2023. [h/t Tom Uren]
Trump shooter phone: Sources told WaPo the FBI used Cellebrite tools to access the phone of Thomas Matthew Crooks, the individual who tried to assassinate former US President Donald Trump over the weekend.
Judge dismisses most of SolarWinds SEC lawsuit: A US judge has dismissed the vast majority of charges the SEC has filed against SolarWinds for its 2020 supply chain attack. The judge dismissed charges related to the company's post-breach disclosures. He also dismissed charges that the company had inadequate security controls and procedures prior to getting hacked. The case will go forward only with charges related to securities fraud that are based on SolarWinds' public security statement. Some of the dismissed charges clear SolarWinds CISO Timothy Brown of blame for the company's poor security posture. He's still a named party in the lawsuit for his role in creating and approving the company's public security statement. [Additional coverage in CybersecurityDive]
Bangladesh internet disruptions: The Bangladesh government has cut off mobile internet access and limited access to social media networks while its police forces deal with a massive student protest.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Rob King, Director of Security Research at runZero, about keeping up with the stream of vulnerabilities in the KEV list and OT devices and runZero's research into the SSH protocol.

Cybercrime and threat intel
Operation Jackal III: A global law enforcement led by Interpol has dismantled multiple West African criminal networks involved in cybercrime and online fraud. Police forces in 21 countries have detained 300 suspects, seized over $3 million, and blocked more than 720 bank accounts used for fraud. Interpol says some of the suspects were linked to Black Axe, a notorious Nigerian criminal syndicate.
Operation Spincaster: A joint venture between Chainalysis, 17 crypto exchanges, and 12 law enforcement agencies has shut down the wallets used by scam networks to steal funds from victims using approval phishing scams. These scams are social engineering attacks where threat actors trick a victim into allowing a rogue smart contract or dApp to spend assets from a victim's wallet.
AstroStress admin sentenced: US authorities have sentenced a Los Angeles man to nine months in prison for running DDoS-for-hire platform AstroStress. Scott Esparza was also ordered to two years of supervised release and a full computer monitoring program after serving his prison sentence. Officials say Esparza worked with a Florida man to run the AstroStress platform. Esparza's co-conspirator was previously charged in December 2022 and pleaded guilty a few months later. He is awaiting sentencing.
Hacker gang drama: Ukrainian authorities have detained the members of a cybercrime crew that stole funds from local businesses after infecting them with malware. The group is believed to have stolen almost $150,000 from hacks carried out this year. Authorities detained two suspects this week on hacking and kidnapping charges. Ukraine's Cyber Police says the duo kidnapped a third accomplice in an attempt to appropriate his share of the earnings.

Angel Drainer shuts down: Cryptocurrency phishing platform Angel Drainer has shut down operations hours after a security firm claimed to have identified its members. Security firm Match Systems has urged past Angel Drainer victims on Tuesday to report attacks and help advance the investigation. The company claims Angel Drainer has been used to steal more than $25 million crypto-assets from more than 35,000 users. Angel Drainer is the fourth crypto-phishing service to shut down over the past year after Pink Drainer, Monkey Drainer, and Inferno Drainer. [Additional coverage in CoinTelegraph]
Pegasus case: According to new court documents from the NSO-v-WhatsApp lawsuit, the Israeli spyware maker appears to have been a customer of AWS and hosted its servers on the company's infrastructure for almost two years. [Additional coverage in The Record]
PyPI malware linked to Iraqi crew: Security firm Checkmarx has linked a recent malicious PyPI package to a cybercrime group operating out of Iraq since 2022.
Chrome badness: Slovak cybersecurity firm ESET has discovered a Chinese company using a vulnerable driver to inject ads and malicious code into Chromium-based browsers. The company goes by the name of Shield Internet Café Security Defense and offers a product to block ads. ESET says that instead of blocking ads, the product merely replaces them.
SocGolish BOINC campaign: Huntress analyzes a SocGolish campaign that uses fake browser updates to install a malicious version of the BOINC software on victim devices.
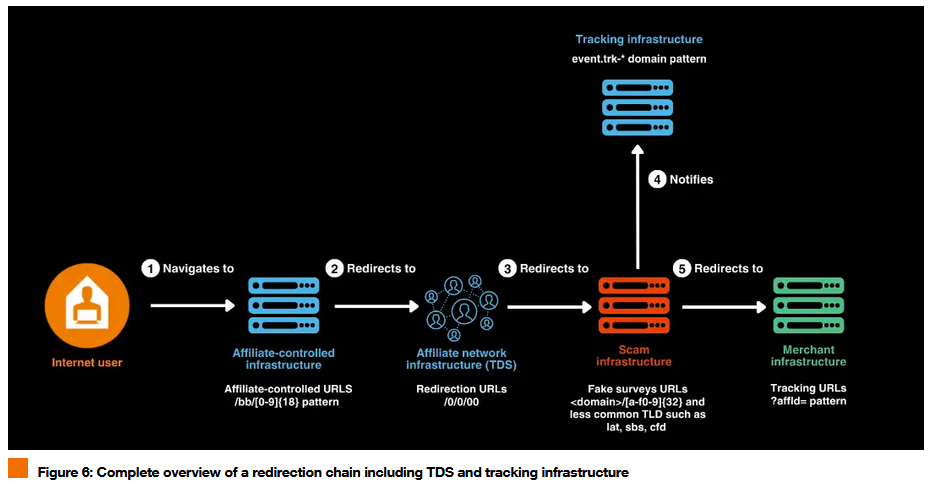
R0BL0CH0N TDS: Orange CERT has discovered a previously known traffic-distribution system (TDS) used to redirect web traffic to affiliate marketing scams. Named R0BL0CH0N, Orange says the TDS has impacted more than 110 million Internet users.
Cloudflare WARP abuse: Cado Security has discovered threat actors abusing Cloudflare's WARP service to launch scanning and reconnaissance attacks. Cado says the attacks are leveraging a common misconfiguration where system administrators are allow-listing all of Cloudflare's IP ranges instead of just those specific to a given service. The company says it has observed crypto-mining and SSH brute-force groups use this technique to bypass Cloudflare security defenses.
Poseidon interview: Threat intelligence analyst g0njxa has published an interview with Rodrigo, the creator of the Poseidon macOS infostealer.
Threat/trend reports: Crunchbase, Eclypsium, F5, Google Cloud [PDF], Imperva, Protect AI, and Sophos have recently published reports covering infosec industry threats and trends.
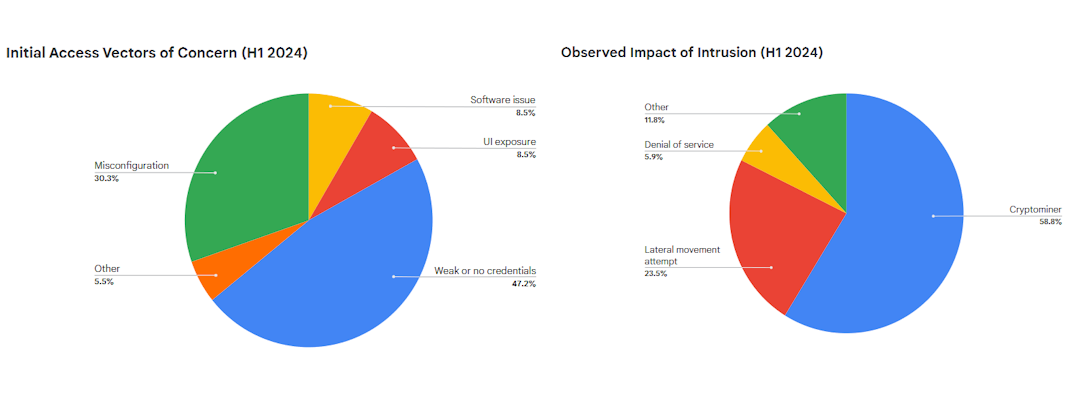
Google Cloud Threat Horizons Report #10: In the tenth edition of its threat and trends report [PDF], the Google Cloud security team reveals that weak or no passwords are still the main root cause for most intrusions into cloud environments. This is basically the same conclusion of its last report, showing that most companies don't understand the basic "don't leave cleartext secrets and tokens around" advice. The report also has a profile of PINEAPPLE, a threat actor that has been hijacking cloud infrastructure since last year to use as spam email servers.
Malware technical reports
BlackSuit ransomware: Deep Instinct looks at BlackSuit, a ransomware strain that is slowly gaining popularity among threat actors.
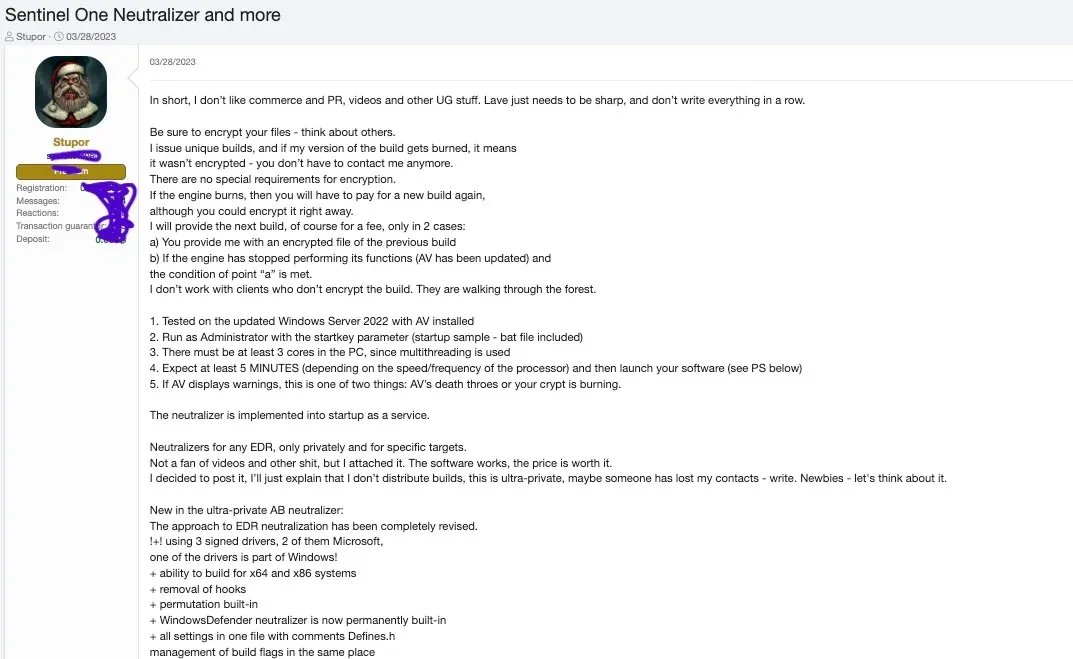
FIN7's AvNeutralizer: SentinelOne researchers have discovered that the FIN7 cybercrime group is behind a powerful hacking tool that has been sold on underground forums since at least 2022. Named AvNeutralizer, or AuKill, the tool is designed to abuse a Windows built-in driver to bypass and then disable security software. SentinelOne says the tool was initially only used by the Black Basta ransomware gang, but has since been adopted by five other groups since then (AvosLocker, MedusaLocker, BlackCat, Trigona, and LockBit). FIN7's involvement in the sale of AvNeutralizer comes as the group tried to maintain a low profile after some of its members were arrested in 2021. According to recent reports, the group has now made a full comeback with multiple waves of spear-phishing campaigns this year. Besides selling AvNeutralizer, FIN7 is also targeting public-facing servers with automated SQL injection attacks.
Sponsor Section
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
Doppelganger infrastructure shutdown: European hosting companies Hetzner and Hostinger suspended accounts linked to Russian disinformation group Doppelganger. The web hosting accounts were exposed in a joint report last week by Correctiv and the Qurium Foundation. The suspension has impacted around 35% of the group's web hosting infrastructure. The web hosting accounts were hosting fake news portals spreading pro-Kremlin, anti-Ukraine, and anti-EU articles.
Kimsuky: Rapid7 has published a paper examining the tactics of North Korean threat group Kimsuky.
Patchwork: Chinese security firm Knownsec 404 looks at recent Patchwork APT operations targeting Bhutan and the group's updated arsenal, which now includes Brute Ratel C4.
UAC-0180: The Ukrainian government says that a threat actor known as UAC-0180 has been targeted local defense enterprises with spear-phishing emails using the topic of UV purchases as lures. The final payloads are the GLUEEGG malware, which, in turn, downloads the DROPCLUE downloader. Ukrainian officials say the UAC-0180 group is behind a large campaign of phishing attacks all over the globe, but has never abandoned trying to gain access to Ukrainian defense foces and defense companies.
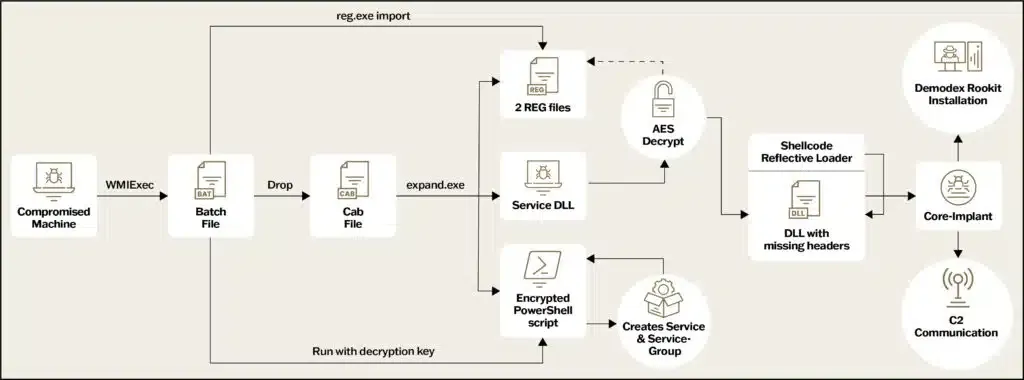
Ghost Emperor's Demodex: Sygnia researchers have published a technical report on Demodex, a rootkit used by Chinese APT group Ghost Emperor.
APT17/DeputyDog: Italian cybersecurity firm TG Soft has published a report detailing an APT17 (DeputyDog) espionage campaign that targeted Italian organizations.
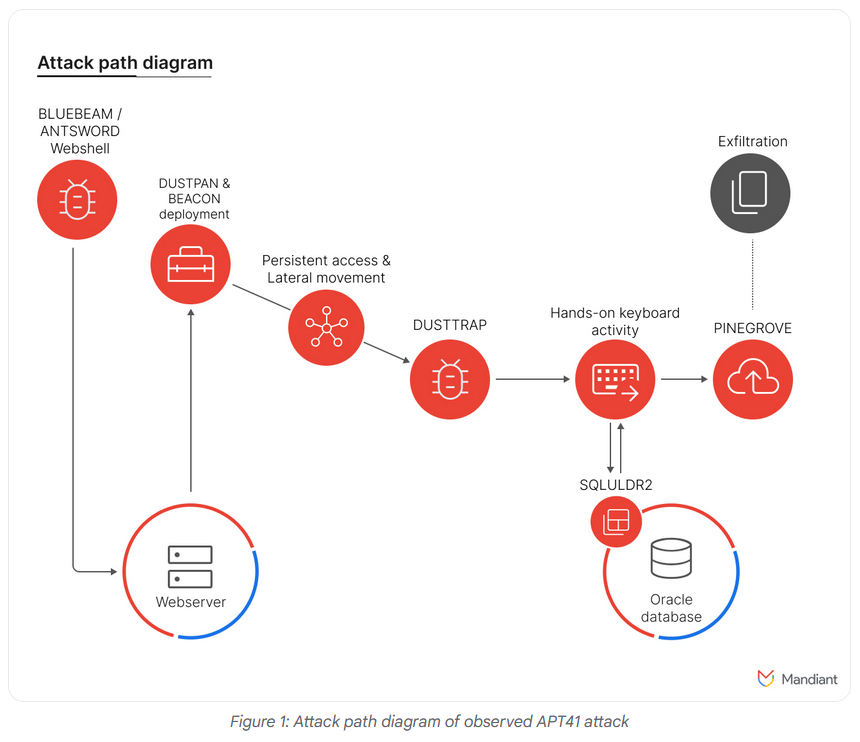
APT41: Google's TAG and Mandiant divisions have published a report looking at APT41's activity last year, in 2023. This is the APT whose operations are believed to be linked to Chinese cyber contractor i-SOON, which was at the center of a major leak earlier this year. The report looks at the group's latest malware arsenal and victimology. It doesn't mention any links to i-SOON or the leak. Sadge Panda! But APT41 has more than one contractor. Another one is Chengdu 404, which, according to an Intelligence Online report, is in a hiring spree.
Vulnerabilities, security research, and bug bounty
Oracle CPU: The Oracle quarterly security updates are out, with patches for 386 vulnerabilities.
SolarWinds security updates: SolarWinds has released security updates to fix 11 vulnerabilities across its products.
JetBrains security updates: JetBrains has released security updates for its TeamCity server. The new version fixes 19 security flaws, but there are no details about any. [h/t ScreamingGoat]
Ivanti security updates: Ivanti has published its July security updates, with fixes for six security issues. [h/t ScreamingGoat]
Atlassian security updates: Atlassian has published its July security updates that address 24 vulnerabilities across the company's products. [h/t ScreamingGoat]
Sonicwall security updates: Sonicwall has released two security updates for its SMA100 and SonicOS IPSec VPN appliances.
Cisco security updates: Cisco has released nine security advisories for its products. The most severe is a vulnerability in the Cisco Smart Software Manager On-Prem license servers. The bug received a CVSS severity rating of 10 out of 10 and allows attackers to change the password of any user, including administrators. Cisco says the vulnerability (CVE-2024-20419) can be exploited remotely against SSM web interfaces or their APIs. In addition, Cisco also patched a security flaw (CVE-2024-20401) in its secure email gateways. This second vulnerability is just as bad as the first and allows remote attackers to replace any file on the device and gain root access to Cisco SEG appliances. This one is rated with a 9.8 out of 10.
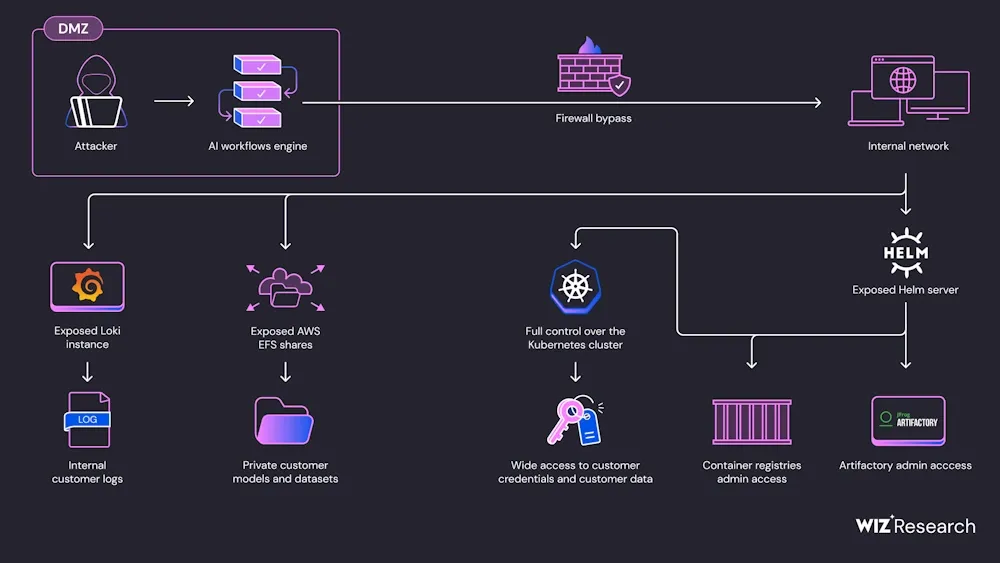
SAPwned vulnerability: Wiz security researchers have uncovered a suite of vulnerabilities collectively in SAP's AI Core that can allow malicious actors to take over the service and access customer data. Wiz says the vulnerabilities could have also been used to contaminate AI artifacts and even to spread to related customer services. The vulnerabilities are collectively known as SAPwned and were fixed throughout the year.
Traffic lights vulnerabilities: Security researcher Andrew Lemon has published a two-part series on vulnerabilities that could allow threat actors to gain access to some traffic lights, change lights, and create traffic jams. [Additional coverage in TechCrunch]
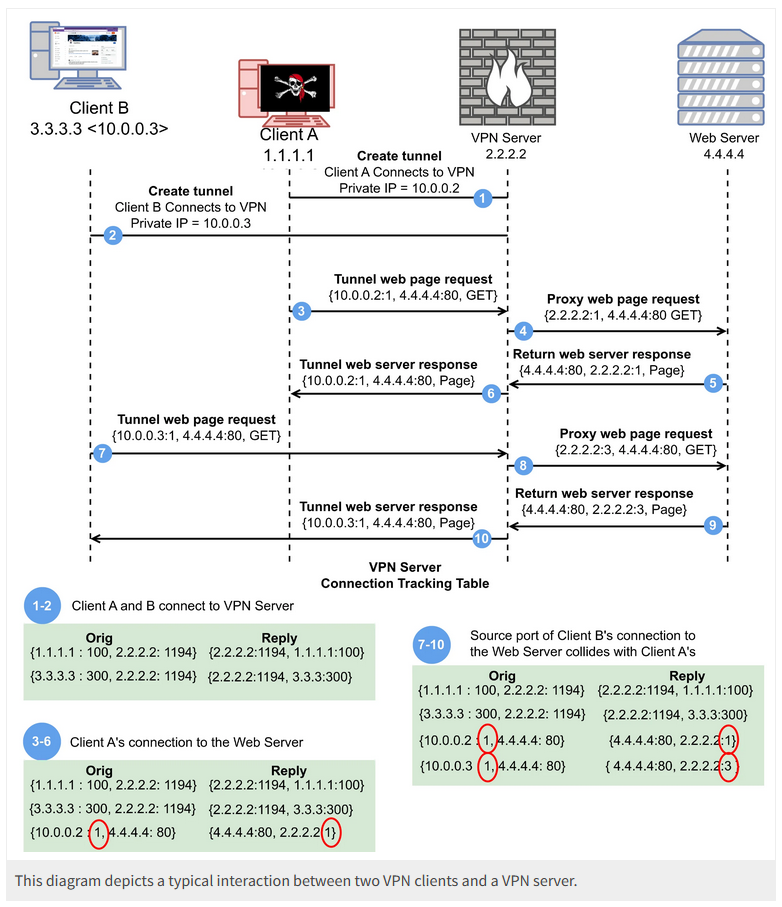
New Port Shadow attack: CitizenLab researchers have discovered a new attack named Port Shadow that can allow threat actors to launch machine-in-the-middle attacks on VPN connections. The attack involves sending specially crafted packets to VPN servers. The packets exploit the server's connection tracking feature to redirect other users' traffic through the attacker's infrastructure. CitizenLab says the vulnerability affects OpenVPN, WireGuard, and OpenConnect servers running on Linux or FreeBSD. Due to the nature of the vulnerability, mitigation relies on using specific firewall rules as opposed to a simpler software fix.
Infosec industry
Pwn2Own host change: Trend Micro's Pwn2Own fall hacking contest—the edition dedicated to hacking mobile and IoT devices—is moving from Toronto, Canada, to Cork, Ireland.
"Over the last few years, our consumer-focused Pwn2Own event took place in the Trend Micro office in Toronto. However, that office closed, so we needed to find a new home. This isn’t unusual for this event, as it moved from Amsterdam to Tokyo to Austin to Toronto. We’re moving again. This year, we are heading to our offices in Cork, Ireland!"
Tool update—Cobalt Strike: Fortra has released Cobalt Strike 4.10, which introduces new features such as BeaconGate, the Postex Kit, and Sleepmask-VS.
x33fcon videos: Talks from the x33fcon 2024 security conference, which took place last month, are now available on YouTube.
BlueHat IL videos: Talks from the BlueHat IL 2024 security conference, which took place in May, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss Shashank Joshi's notes from a recent Oxford Cyber forum. Topics include the role of zero-days and who is ahead when it comes to offensive cyber operations.
In this podcast, Tom Uren and Adam Boileau talk about how countries are using cyber security reports and advisories to win friends and influence people; why having gaping holes in US federal government security is situation normal; and efforts to make up for the disappearance of Twitter's trust and safety team.
This Soap Box edition of the show is with Mike Wiacek, the CEO and Founder of Stairwell. Stairwell is a platform that creates something similar to an NDR, but for file analysis instead of network traffic. The idea is you get a copy of every unique file in your environment to the Stairwell platform, via a file forwarding agent. You get an inventory that lists where these files exist in your environment, at what times, and from there, you can start doing analysis.




