Risky Biz News: Crypto-phishing service shuts down after stealing $71 million
In other news: Ukraine takes credit for Rosaviatsiya hack; a ransomware attack cripples hospitals in six US states; and ASD recommends patching within 48 hours.

This newsletter is brought to you by Corelight. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
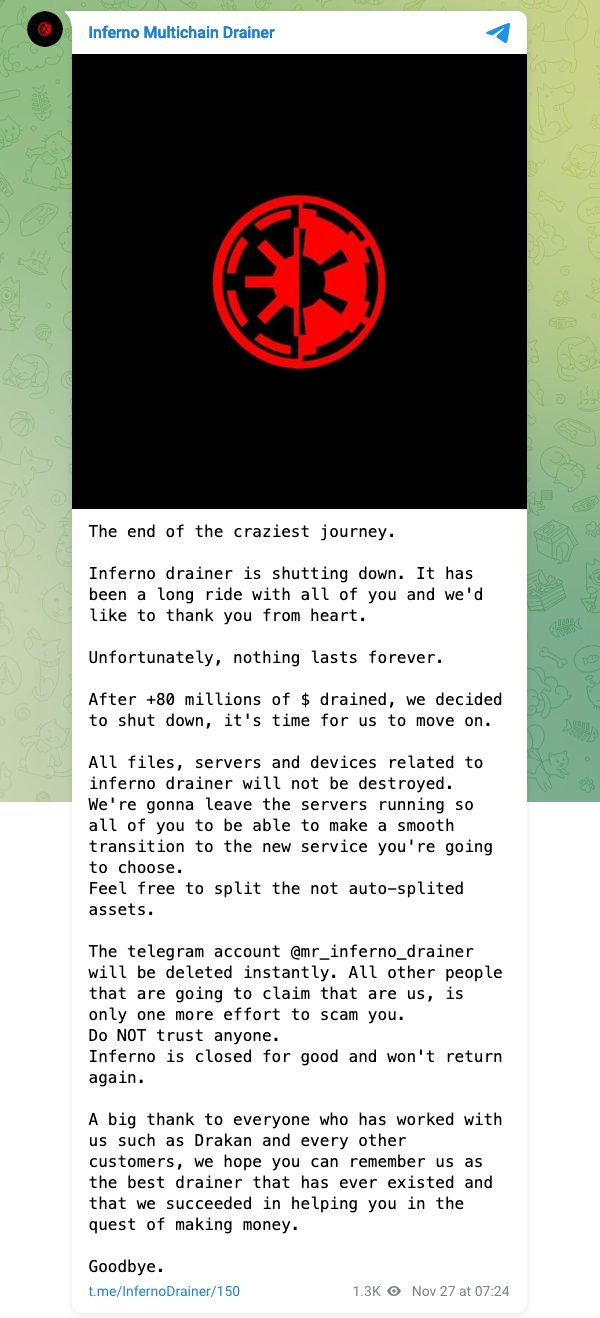
A phishing platform specialized in cryptocurrency thefts has shut down operations after stealing more than $71 million over the past nine months.
Named Inferno Drainer, the platform launched in February this year.
Spotted by Web3 security platform ScamSniffer, the service allowed threat actors to create phishing pages for more than 220 cryptocurrency brands.
Threat actors would create phishing pages through the service, they would lure users to the sites, and Inferno Drainer would automate the hacking and draining of victims' crypto wallets. For its troubles, Inferno Drainer would keep 20% of the funds, while its "customers" got the rest.
ScamSniffer researchers say Inferno Drainer was responsible for more than 10,000 phishing sites and helped hackers steal cryptocurrency from more than 103,000 victims since its launch.

The service is the perfect definition of a modern-day cybercrime offering. It was offered, advertised, and managed solely through Telegram; it provided a dumbed-down point-and-click interface for low-skilled threat actors; and pulled the plug on its operations as soon as it had a few big hacks (in August and November this year).
Although the Inferno Drainer administrator is claiming they are shutting down, there is an extremely high chance another wallet-draining service will pop out of the blue in the coming weeks.
Rebranding and name changes are more common tactics in underground cybercrime than they are with Microsoft cloud and security products.
Inferno Drainer is the second crypto-phishing service to shut down this year after Monkey Drainer, which shuttered operations in March.
Breaches, hacks, and security incidents
Ardent ransomware attack: Hospitals owned by Ardent Health are redirecting patients and ambulances to nearby emergency rooms after a ransomware attack crippled the healthcare provider's operations. The incident took place last week, on Thanksgiving Day. Ardent Health says it shut down its IT network to contain the damage. The attack and the resulting IT outage impacted Ardent Health hospitals in Idaho, Oklahoma, New Mexico, Texas, Kansas, and New Jersey—all the states where the company operates. [Additional coverage in in NBC, CNN]
Ethyrial ransomware attack: A ransomware attack that hit gaming company Gellyberry Studios has destroyed user accounts and in-game inventory for the "Ethyrial: Echoes of Yore" game. Because the game was still in an early alpha release and testing phase, only 17,000 user accounts were affected by the incident. The company says it's restoring from a previous backup and will not pay the attackers for a decryption key. It said it learned from the attack and will now back up its servers more often. [Additional coverage in Hot for Security]
Line data breach: The company behind the Line instant messaging service disclosed a security breach [PDF] after a hacker stole the personal data of 440,000 users. LY Corp says the breach originated at one of its subcontractors at the start of October. The company says the hacker infected the computer of one of its subcontractors and then pivoted to its network. More than 300,000 of the 440,000 stolen records are directly related to the Line app. [Additional coverage in Kyodo News]
Aliquippa water utility hack: Officials from Aliquippa, Pennsylvania, have confirmed that an Iranian hacktivist group took control of water booster stations operated by the town's water authority. A group known as Cyber Av3ngers took credit for the hacks last week in a series of Telegram posts. The booster stations were manufactured by Unitronics and were used in Aliquippa to monitor and regulate water pressure. [Additional coverage in CBS]
Taj Hotels breach: The data of 1.5 million customers who stayed at luxury hotel chain Taj Hotels is being sold on an underground forum. [Additional coverage in the India Times]
Pegasus in Serbia: CitizenLab, Amnesty International, and AccessNow came out to support the SHARE Foundation's conclusion from last week that traces of the Pegasus spyware were found on the devices of two members of the Serbian civil society.
"These attacks, which occurred approximately one minute apart from each other on or about August 16, 2023, leveraged the iOS HomeKit iPhone functionality. The tactics are consistent with those previously used by NSO Group's Pegasus spyware, although given limited available forensic indicators on the targeted devices, we cannot confirm the exact type of spyware used in this attack."
DIMC hack: Pro-Ukrainian hacktivist group Cyber Resistance has hacked and leaked data from the Department of Information and Mass Communications of the Russian Ministry of Defense (DIMC). The leaks contain reports compiled by the DIMC showing an obsession of the Russian government about how the Russian Army and the Ukrainian war are covered in both internal and external media. The report also covers KATYUSHA, a platform used by the DIMC to monitor online media. [Additional coverage in InformNapalm]
"We wonder who proofreads all this, because at times the texts look really cringy. It seems that Russian propagandists themselves do not read very closely into what they write. For example, they call their military personnel “military prisoners” [Ed.: “военнопленные” instead of “военнослужащие”]."
General tech and privacy
Google Drive data loss: Google is investigating reports that some Drive users have lost all their recent files as far back as May 2023. Missing files don't appear in the trash folder, in past revisions, or in the web version.[Additional coverage in Android Police]
OpenZFS data corruption bug: Speaking of data corruption, there's a bug in the OpenZFS file storage system that corrupts files when copied.
"OpenZFS through 2.1.13 and 2.2.x through 2.2.1, in certain scenarios involving applications that try to rely on efficient copying of file data, can replace file contents with zero-valued bytes."
Microsoft Defender Application Guard for Office: Microsoft has deprecated the Application Guard for Office. The feature only lasted four years.
Meta complaint in the EU: European privacy watchdog noyb has filed a complaint with the Austrian data protection agency against social media company Meta. Noyb says Meta's new tactic of charging EU users €9.99/month to not track them online is against the EU GDPR. The organization argues that users have a fundamental right to privacy and they shouldn't pay to stop psychopathic tech bros from following their every move online. I may or may not added the "psychopathic tech bros" part.
NAFO and Truth Social: Wired looks at NAFO's trolling and its attempts to sabotage Trump's Truth Social social media platform.
Telegram's fake bans: The same Wired also looks at how inefficient Telegram's channel banning system is and how content shared on those channels often makes its way out and spreads on the platform anyway.
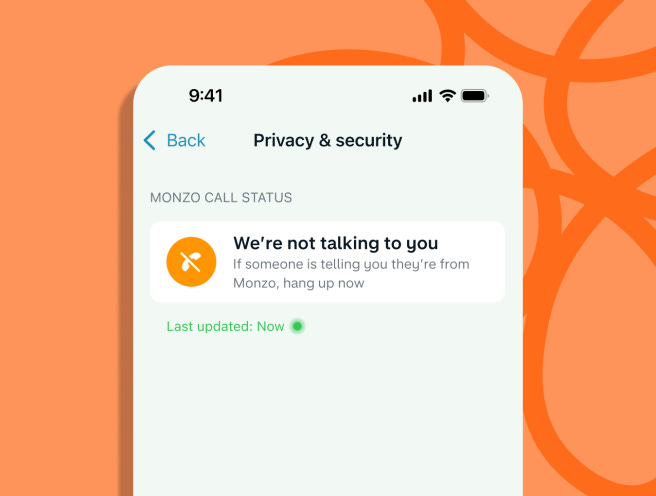
Monzo anti-fraud feature: Something we missed back in September was this new feature added to the Monzo app that shows when a customer support agent is on the phone with a customer. Monzo says this feature can be used to determine when a customer may be getting scammed or when he's actually speaking to a legitimate Monzo customer support agent.
Government, politics, and policy
Ukraine takes credit for Rosaviatsiya hack: The Ukrainian government says it hacked Russian civil aviation agency Rosaviatsiya. Ukraine's Defence Intelligence Main Directorate says it obtained "a large volume of confidential documents" following a "complex special operation in cyberspace." Ukrainian officials claim the stolen documents show the dire state of the Russian aviation sector as a result of Western sanctions. According to screenshots posted by the agency, the most recent document is dated August 2023. Rosaviatsiya disclosed a hack in March 2022, although it's unclear if this is the incident referenced by Ukrainian officials. [h/t Oleg Shakirov]
Ukraine cyber corruption probe: A Ukraine court has ordered the arrest of Viktor Zhora, the ex-deputy head of Ukraine's State Service for Special Communications and Information Protection (SSSCIP). Zhora was fired last week together with former SSSCIP head Yurii Shchyhol. Both are accused of participating in a scheme to contract software at inflated prices. Shchyhol was arrested last week. Both officials are now out on bail. [Additional coverage in The Record]
FISA reform legislation, part 2: After an earlier effort earlier this month through the Government Surveillance Reform Act, we now have a second bill attempting to restore US surveillance powers under Section 702 of the Foreign Intelligence Surveillance Act. This one is spearheaded by Senators Warner, Rubio, Graham, Wicker, Collins, King, Bennet, Casey, Gillibrand, Rounds, Kelly, Klobuchar, Moran, Lankford, and Whitehouse. Compared to the privacy-friendly first act, this one is more lenient and removes an FBI warrant requirement. [Additional coverage in The Record]
ASD Essential Eight update: The Australian Signals Directorate has updated the Essential Eight Maturity Model, a set of eight basic cybersecurity recommendations the agency initially published in 2017. The ASD says the update takes into consideration changes to the threat landscape. The update includes new recommendations such as applying security patches within 48 hours, using PowerShell logging, uninstalling Internet Explorer, and clarifications on the proper way of using MFA. An overview of all the other changes is available here.
AI development guidance: Cybersecurity and government agencies from 18 countries have published joint guidance on how to develop safe and secure AI systems. The guidance targets developers and academics, contains general recommendations, and is non-binding. The document was put together by CISA and the UK NCSC, with input from the agencies listed below.

Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Corelight CEO Brian Dye about the value of data from NDR tools when it comes to long-term incident response.
Cybercrime and threat intel
Ransomware gang detained in Ukraine: Ukrainian authorities have detained five members of a cybercrime group that carried out more than 1,800 ransomware attacks across 71 countries. The group's leader and four accomplices were detained following searches at 30 locations across Ukraine. Officials say the group worked as an affiliate for larger ransomware operations and deployed ransomware strains such as LockerGoga, MegaCortex, Hive, and Dharma. The suspects are believed to be connected to a group of 12 suspects detained in June 2021 in connection to the LockerGoga gang. [Press releases: Europol; Eurojust; Ukraine Cyber Police; Ukraine National Police]
SIM swapper sentenced: A US judge has sentenced a 24-year-old from LA to 96 months in prison for SIM-swapping Instagram social media influencers, along with other crimes.
USiSLookups: A Telegram channel named USiSLookups is providing access to US Social Security information for prices ranging from $8 to $40. According to infosec reporter Brian Krebs, the data appears to come from US consumer data broker USinfoSearch, most likely via compromised USinfoSearch accounts.
Malware technical reports
Banking trojans in Iran: Zimperium has more details on a campaign spotted by Sophos that used mobile banking trojans to target Iranian banking users earlier this year. It appears the campaign is still ongoing and evolving.
RisePro: ANY.RUN researchers have published an analysis of RisePro, an infostealer that launched in 2022 as a MaaS.
LostTrust ransomware: ShadowStackRE has published an analysis of LostTrust, a ransomware operation that launched in September this year and quickly became one of the most prolific groups around, making the Top 5 most active groups in October.
Sponsor Section
This week's Risky Business newsletters are brought to you by Corelight. They maintain the open-source Zeek network security sensor/monitor. They also make very good commercial products in the network security space. Check them out at Corelight.com, or watch this video about why you need NDR as well as EDR.
APTs, cyber-espionage, and info-ops
WildCard APT: Intezer researchers have linked the SysJocker, a sophisticated Linux and Windows backdoor, to an APT group they are calling WildCard. Spotted in late 2021 and recently rewritten in Rust, the malware has been linked to a "Hamas-affiliated APT" by fellow Israeli cybersecurity firm Check Point. While Intezer has not made the same attribution, the company did say SysJocker is linked to the current threat landscape surrounding the ongoing Israeli-Hamas war. In an interview, Intezer called the WildCard APT "unusually mature for the Israeli threat landscape."
Andariel: AhnLab says North Korean cyber-espionage group Andariel has jumped on the bandwagon of Apache ActiveMQ exploitation (via CVE-2023-46604). The final payloads are the NukeSped and TigerRat backdoors.
DPRK macOS campaigns: SentinelOne looks at a recent DPRK-linked malware campaign targeting macOS users with the RustBucket and KandyKorn malware strains.
Vulnerabilities, security research, and bug bounty
Chrome zero-day: Google has released security updates for its Chrome browser. The company says that a vulnerability tracked as CVE-2023-6345 is being exploited in the wild.
Ray vulnerabilities: Bishop Fox researchers have discovered a series of vulnerabilities in Ray, an open-source unified compute framework.
Chamilo LMS vulnerabilities: Starlabs researchers have discovered ten vulnerabilities in the Chamilo LMS, including several pre-auth RCEs.
Splunk PoC: A proof-of-concept has been released for CVE-2023-46214, an RCE in Splunk Enterprise that was patched earlier this month.
BLUFFS attack: A team of academics from Europe has published details on BLUFFS, a collection of six attacks against the Bluetooth protocol's future and forward secrecy mechanism. Tracked as CVE-2023-24023, the attacks can force devices paired in a secure connection to use legacy encryption schemes with short and weak encryption keys. This allows attackers to expose Bluetooth devices communicating in the Secure Connections mode to man-in-the-middle (MitM) attacks. The maintainers of the Bluetooth standard have confirmed the BLUFFS attacks and published recommendations for vendors.
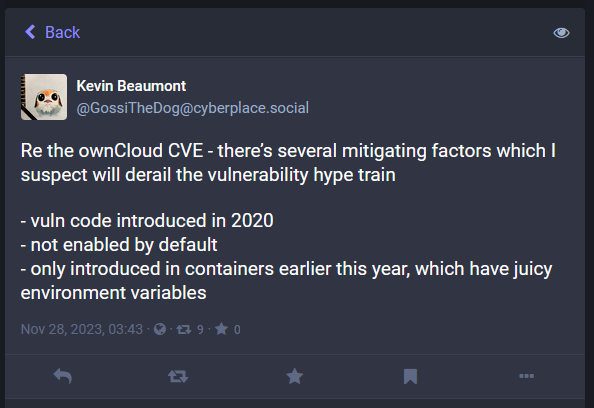
ownCloud exploitation: Multiple threat actors are scanning the internet for ownCloud file-sharing servers to exploit a recently patched vulnerability. Tracked as CVE-2023-49103, the security bug has a severity rating of 10/10 and can be used to leak admin passwords and mail server credentials for ownCloud installations. Exploitation has been spotted and independently confirmed by GreyNoise, SANS ISC, and the Shadowserver Foundation. According to the latter, there are more than 11,000 ownCloud servers currently connected to the internet. ownCloud released a security update last week.
Infosec industry
New tool—Have I Been Squatted: Security researcher Juxhin has put together a tool named Have I Been Squatted that checks if a domain is being typosquatted. [h/t Ian Muscat]
New tool—IceKube: Security firm WithSecure has open-sourced a tool named IceKube that can find attack paths within a Kubernetes cluster from a low privileged point to a preferred location, typically cluster-admin.
New tool—CVSS-BT: Security researcher Stephen Shaffer has open-sourced CVSS-BT, a tool to enrich NVD CVSS scores with temporal & threat metrics. [h/t Patrick Garrity]
New tool—DeleFriend: Security firm Hunters has open-sourced a tool named DeleFriend that can perform GCP domain-wide delegation abuse and access Workspace user data via GCP service accounts. Bell's Clément Cruchet has a similar tool out named Delegate.
OpenSSF guide: The Open Source Security Foundation (OpenSSF) has published a guide on how open-source projects can become a CVE numbering authority (CNA).
AT&T to enter MSSP market: US telco giant AT&T will enter the managed security service providers (MSSP) market. The company plans to enter a joint venture with WillJam Ventures and create a standalone MSSP division in the first quarter of 2024.
AWS re:Invent 2023: Live streams from the Amazon re:Invent conference are available on the AWS Events YouTube account.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the latest Russian cyber attacks on the Ukrainian energy grid.




