Risky Biz News: Anonymous Sudan's Russia Links Are (Still) Obvious
In other news: Iranian hackers sell access to US critical infrastructure; North Korea hacked ad platforms to deploy an Internet Explorer zero-day; hacker "USDoD" arrested in Brazil.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US government has charged two members of the Anonymous Sudan hacking group after the FBI secretly seized server infrastructure and disrupted its operations in March this year.
The indictment names two brothers—Ahmed Omer, 22, and Alaa Omer, 27—as the two main individuals behind the group's operations.
The two are accused of launching thousands of DDoS attacks against government agencies, hospitals, critical infrastructure, and private businesses all over the world.
The charges against Ahmed Omer for attacking US hospitals could carry a life sentence. Officials said the DDoS attacks were intended to sabotage hospital IT systems in attempts to hinder patient care and cause serious bodily injury and possible death.

Prosecutors say the group had at least three other members that remain unnamed. One of these accomplices allegedly built the group's DDoS toolkit, and is known online under different names such as DCAT, SkyNet, Godzilla, or the InfraShutdown botnet.
According to Akamai and Amazon, the tool used "fraudulently obtained virtual private servers from various [cloud] providers across the industry" that ran scripts for launching various types of DDoS attacks.
The group used the tool to launch attacks but also sold access to it via a Telegram channel, using its "hacktivist" activity to boost sales in a tactic employed by the Killnet group before.
This DDoS botnet packed quite a punch and took down cloud infrastructure for some of the world's largest companies, such as Microsoft, OpenAI, PayPal, and others. It was also used to launch DDoS attacks on Israel's missile warning system RedAlert, within an hour after the Hamas attack on October 7, 2023.
In a press conference, US officials said the two brothers are highly educated and have been in custody since March. Officials declined to say where they were arrested.
Since its sudden appearance on the DDoS hacktivism scene in January 2023, Anonymous Sudan has consistently been described as a pro-Kremlin group — for many, and very good and obvious reasons.
However, in the criminal complaint [PDF] and the DoJ press conference [see Wired and WaPo reports], prosecutors said they found no evidence the group "may be state-sponsored Russian actors masquerading as Sudanese actors" and that the attacks were driven by "a Sudanese nationalist ideology."
I'm sorry, but what were they expecting to find? GRU employment contracts? That's not how this works. It's also not how attribution works. Just because an offender carries one country's passport doesn't mean they can't be co-opted for another country's interests. You can judge and attribute these groups based on their actions, and there's a pretty long and very well-documented history of this group acting in Russia's interests.
For example, Anonymous Sudan threatened France with DDoS attacks if it sent troops to Niger after the country was taken over by a Russian-backed military junta. What's this "Sudanese nationalist ideology" doing all the way over there in Niger?
Anonymous Sudan also constantly launched DDoS attacks related to the Ukrainian war. Some country would announce military funds for Ukraine, and the next day, Anonymous Sudan and a bunch of pro-Kremlin groups coordinated attacks on their schools and hospitals. That doesn't sound like "a Sudanese nationalist ideology," either.
Sweden, way up north in Scandinavia and far far away from Sudan, announced that it would join NATO, and there go the brave Anonymous Sudan hackers with the DDoS attacks on its hospitals. The Sudanese nationalist spirit in action!
The group's Telegram statements continuously used terms like "Western colonialism" and "French imperialism"—lingo used by Russian info ops in Africa for years.
For a Sudanese nationalist group, they also weren't bothered by Russia's involvement in the Sudanese civil war or that a Russian-backed junta in Sudan was letting Russia plunder the country's resources.
It's like Russia had found local useful idiots to push their ideology for a financial incentive or something. But what do I know!
Security firms like Trustwave, Truesec, Netscout, CyberCX, Flashpoint, and Radware have consistently published reports pointing the group's actions support Russian narratives and against Russia's adversaries. From Netscout:
"The group often overlooks actions taken against Sudan or Islam in non-Western countries."
There's also the small detail of the Anonymous Sudan Telegram channel having a history of Russian posts before switching to Arabic and then to a Sudanese Arabic dialect. Truly, a world-class example of a Sudanese nationalist grassroots movement.
Anonymous Sudan also has a history of cooperating with Russian-based groups like Killnet and sharing their infrastructure and tools. It's all just a big coincidence, obviously.
When the feds took down the Anonymous Sudan botnet and arrested the two brothers, another pro-Kremlin "hacktivist" group popped out of nowhere, sharing infrastructure and a modus operandi with Anonymous Sudan. This one, according to Radware, was actually run by a Russian individual from Staraya Russa this time. Just another Russian coincidence again.
Yet one more: According to Swedish security firm Truesec, Anonymous Sudan also formed and had instant access to a large and powerful DDoS infrastructure three days before a far-right journalist with links to Russian media burned the Quran in front of Turkey's embassy in Sweden in an event meant to sabotage Sweden's NATO bid. The event was teased beforehand by Russian disinfo channels and which Anonymous Sudan used as a manifesto for its initial appearance and actions.
As Truesec writes in its report, it had been obvious that someone was financing and coordinating the group from the start, and all signs pointed to the involvement of Russian intelligence services.

I understand law enforcement and some of the infosec community's obsession with finding indisputable evidence, but you're not going to find a "DDoS service provider contract with the Russian government" in Ahmed's Dropbox account. These kinds of arrangements don't leave that sort of evidence behind.
These groups need to be judged based on their actions, and this group's MO has been pretty clear since it first appeared. So colour us skeptical that there is no Russia nexus here.
Breaches, hacks, and security incidents
Texas DPS breach: The Texas Department of Public Safety has suffered a security breach and leaked the personal information of over 115,000 Texans. Leaked data included names, addresses, Social Security numbers, driver's license numbers, government-issued ID numbers, and other sensitive information. The Texas DPS did not say how or when the breach took place. It is the Department's second breach after a similar incident in December 2022. [Additional coverage in KERA News]
Globe Life breach: American life insurance company Globe Life says it suffered a security breach and is now being extorted by a hacker. The company says the incident is not the result of a ransomware attack. Globe Life says it's still investigating how the hacker got hold of customer data. [Additional coverage in TechCrunch]
General tech and privacy
Passkey adoption at Amazon: Amazon says that more than 175 million users are now using passkeys to log into their accounts after the company rolled out support last year.
Cloudflare is breaking RSS readers: The Open RSS project says that several Cloudflare features are inadvertently blocking RSS readers from retrieving RSS feeds from Cloudflare-protected sites.
Chrome starts disabling uBO: Monopolistic advertising company Google has started disabling ad-blocker uBlock Origin inside its Chrome web browser—its most popular extension, btw. The move comes after Google forcibly pushed a new extension system inside Chrome on the false premises of sEcUrItY when, in reality, it just wanted to remove features and neuter ad blockers. I'm sorry, dear newsletter readers, for not regurgitating what Google's PR and blog posts say on this topic. Despite the new extensions system, the malicious extensions are still there while ad blockers are not. You can still use uBO until June 2025, but this requires going through some complicated steps.
Chrome 130: Google has released version 130 of its Chrome browser. See here for security patches and webdev-related changes. The biggest changes in this release include a new Toast UI system, a new Account menu, and support for CSS containers and nesting.
Call of Duty false bans: Activision has confirmed that threat actors abused a vulnerability in the Ricochet anti-cheat system to ban legitimate Call of Duty accounts. The company says the exploits impacted a small number of legitimate player accounts, all of which have been restored. The company's admission comes after at least two major Call of Duty content creators were perma-banned over the past weeks.
Twitter grants itself the right to use your data: Twitter has updated its terms of service and has granted itself the right to use anything you post on the platform to train AI, with or without your consent. The new terms will take effect on November 15.
Twitter changes block feature: Twitter has also updated how the block feature works on the platform. The new block feature now allows the people you blocked to view your tweets. It still prevents them from interacting with it.
Government, politics, and policy
EU removes Twitter from DMA: The EU has removed Twitter (X) from its list of web services that fall under the umbrella of the Digital Markets Act. Services on this list are considered large companies that act as "gatekeepers" between businesses and consumers. Platforms currently on the DMA gatekeepers list include Google Search, YouTube, Amazon, Apple, TikTok, Facebook, WhatsApp, and Microsoft, through LinkedIn and the Windows OS.
Security review of Intel CPUs in China: A Chinese industry group has asked the Beijing government to perform a security audit of Intel products. The Cyber Security Association of China claims Intel chips pose a national security risk due to a large number of vulnerabilities discovered this year. The CSAC also claims that Intel products include remote management features that could be abused to install backdoors and surveil Chinese companies and users. It also claims Intel chips contain an NSA backdoor that allows the US agency to disable security features and access sensitive data. The Cyberspace Administration of China has the power to take up the complaint and launch an audit. The agency previously banned US chipmaker Micron from selling chips to Chinese critical infrastructure operators in March of last year, also after a security audit of its chips. [Additional coverage in PCMag]
Russia wants to ban Speedtest: Russian officials are looking at banning bandwidth testing service Speedtest. Officials claim the service shares information on telco networks with foreign intelligence agencies. The proposal to block the service was put forward by a Russian telco group and has already received initial support from the Russian Duma and the FSB intelligence service. [Additional coverage in The Moscow Times]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Dan Guido, CEO of Trail of Bits, about post-quantum cryptography. The pair dive into what it is, why it is needed now, and how organizations are dealing with its adoption.
Cybercrime and threat intel
USDoD hacker detained in Brazil: Brazilian police have detained a suspect believed to be a notorious hacker known online as USDoD. Officials say the suspect allegedly hacked and leaked data from organizations across the world, such as the FBI InfraGard system, the US EPA, Airbus, and many others. The suspect's name has not been disclosed. In August, a Brazilian news site claimed to have seen a CrowdStrike report that identified the hacker as a 33-year-old named Luan B.G. from the state of Minas Gerais. This seems to fit with the Brazilian police's press release, which says the suspect was detained in Belo Horizonte, the Minais Gerais state capital.
Bitfinex hack money laundering case: US prosecutors have asked for a five-year prison sentence for Ilya Lichtenstein and 18 months in prison for his wife, Heather Morgan. The two were arrested and charged in 2022 for laundering almost $3.6 billion worth of crypto stolen from the Bitfinex exchange in a 2016 hack. Prosecutors have asked for a bigger sentence for Lichtenstein because he was the alleged mastermind behind the scheme. The couple pleaded guilty last year and is awaiting sentencing later this year. [Additional coverage in Bloomberg]
SEC Twitter hacker detained: US authorities have arrested an Alabama man for hacking the Twitter account of the US Securities and Exchange Commission. Officials claim Eric Council Jr. used SIM swapping to take control of the SEC account in January this year to post a fake announcement on the SEC's behalf. The announcement caused the Bitcoin price to spike by $1,000 and then plummet by $2,000 when the tweet was proven to be fake. Court documents claim that the suspect didn't think the attack through. Officials say Council performed Google searches such as:
- How can I know for sure if I am being investigated by the FBI;
- What are some signs that the FBI is after you;
- What are the signs that you are under investigation by law enforcement or the FBI even if you have not been contacted by them.
Romance scammers arrested in Hong Kong: Chinese authorities have detained 21 men and six women on charges of scamming over $46 million from victims across Southeast Asia. Officials claim the group used deepfake technology to swap faces in video calls and pose as attractive women. The gang set up fake crypto trading sites and swindled victims into investing on the platforms. [Additional coverage in NDTV]
DPRK IT workers extort victim company: North Korean IT workers are now ransoming companies using stolen data after they are uncovered and fired from their jobs. According to security firm Secureworks, at least one company has received a six-figure ransom demand from a former employee who turned out to be North Korean. The new shift in tactics comes as companies are cracking down on North Korean workers in their staff. Cybersecurity agencies have warned that North Korean workers generate funds for the regime's nuclear missile program and can turn malicious insiders at any point.
Shadow and Twelve: Russian security firm FACCT has published a report on Shadow and Twelve, two allegedly connected cybercrime groups that are targeting Russian organizations.
DDoS attacks in Japan: Netscout has published a report on how two pro-Kremlin hacktivist groups coordinated attacks on Japanese organizations after the Tokyo government announced its increased participation in a US-led military alliance, including the potential for hosting US nuclear weapons or building its own.
Mobile political spam: Proofpoint reports another increase in mobile political spam volumes ahead of the US presidential election. It saw another spike back in July.
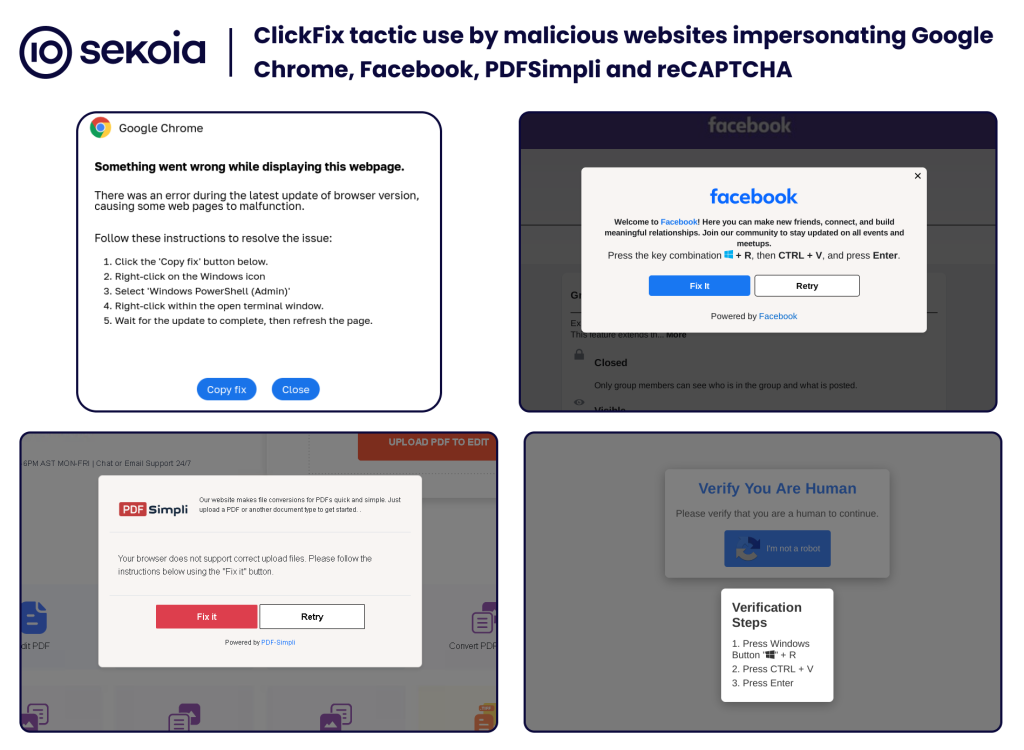
ClickFix campaigns: Sekoia has published a report about ClickFix, a new social engineering tactic that has become quite popular this year. The tactic involves showing pop-up windows with "instructions" on how to fix broken websites or other issues. The instructions are basically steps for users to run malicious Powershell commands on their PCs. According to Sekoia, there's now quite the number of groups that engage in ClickFix-based campaigns—SNE (Slavic Nation Empire), Marko Polo, CryptoLove, and TA571.
Malware technical reports
DodgeBox: Malware analyst Vlad Pasca has published an analysis of how an APT41 malware strain named DodgeBox (ab)uses call stack spoofing for its operation. The technique is widely used by pen-testing and red-teams but was rarely seen used by APT groups.
Fake LockBit ransomware: Trend Micro has spotted a threat actor deploying a new Go-based ransomware in attacks. The group posed as the defunct LockBit gang and used the AWS S3 Transfer Acceleration feature to exfil and move data from compromised environments into an S3 bucket. Trend Micro says it disrupted the group's operation by reporting the bucket to AWS and having its account suspended.
Cicada3301 RaaS: Group-IB has published an exposé on the Cicada3301 RaaS. The company claims it gathered the data after managing to gain access to its backend panel.
Sponsor Section
You might be hearing a lot about post-quantum (PQ) cryptography lately, and it's easy to wonder why it's such a big deal when nobody has actually seen a quantum computer. But even if a quantum computer is never built, new PQ standards are safer, more resilient, and more flexible than their classical counterparts. More from Trail of Bits here.

APTs, cyber-espionage, and info-ops
Russia targets Ukrainian reservists: Russia-linked hackers are targeting Ukrainian conscripts and reservists with malware. The campaign used a Telegram bot to trick Ukrainian men into downloading an app on their PC. The app was advertised as a way to update their data with the government instead of visiting army draft offices. Ukraine's CERT says the app was infected with a version of the MeduzaStealer malware that collected data from their computers, such as personal information and browser credentials. Officials say the Telegram bot was previously listed as an official technical support method for an official Ukraine government app before being used for phishing.
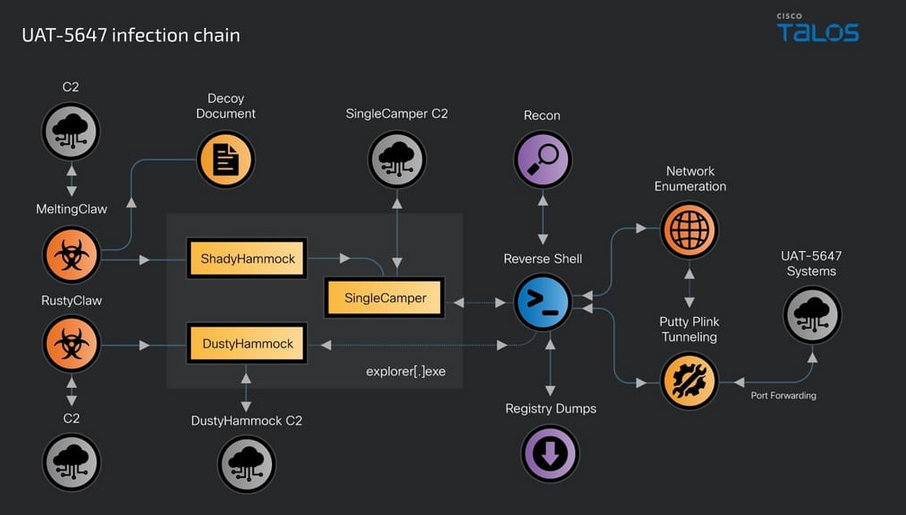
UAT-5647: Cisco Talos has published a report on UAT-5647, a Russian-speaking APT targeting Polish and Ukrainian organizations with the RomCom (or SingleCamper) malware. Previous reporting claimed Russian state-sponsored groups enlisted the RomCom gang for espionage operations linked to Russia's war in Ukraine.
Iranian hackers sell access to US critical infra: US cybersecurity agencies say that Iranian threat actors are behind a campaign that has used brute-force attacks to compromise organizations in critical infrastructure sectors. The campaign has been taking place since October of last year and has compromised hospitals, government organizations, and energy companies. The Iranian hackers have used a technique called MFA push bombing to bypass multi-factor authentication where present. Officials say attackers moved laterally across networks and sold access to the hacked organizations to cybercrime groups.
The new and overworked IcePeony APT: A group of Japanese security researchers has discovered a new Chinese APT after the group misconfigured servers and exposed its malware and command and control servers. The new IcePeony group has primarily targeted the websites of Southeast Asian governments with SQL injection attacks. The group appears to have been active since at least 2023, and most attacks targeted India and Vietnam. Researchers say the group appears to be overworked under China's 996 work culture, where employees work from 9am to 9pm, six days a week.
Mysterious Elephant (APT-K-47): QiAnXin has published a report on Mysterious Elephant, an APT fellow Chinese security firm KNOW previously claimed might be linked to Bitter, a suspected Indian APT.
Donot (APT-C-35): Chinese security firm Qihoo 360 looks at a campaign from Donot, a suspected Indian APT, targeting Pakistani organizations.
Evrazia: The OCCRP has published a profile on Evrazia, a Russian non-profit involved in influence operations and a money-for-votes scheme ahead of Moldova's presidential elections this weekend.
Progress 2028: An OpenSecrets investigation has found that an initiative named Progress 2028, which poses as Kamala Harris' counter to Trump's Project 2025, is actually supported by a money network linked to Trump and Musk. The initiative has been seen running misleading ads about Harris on Facebook and Instagram ahead of the election.
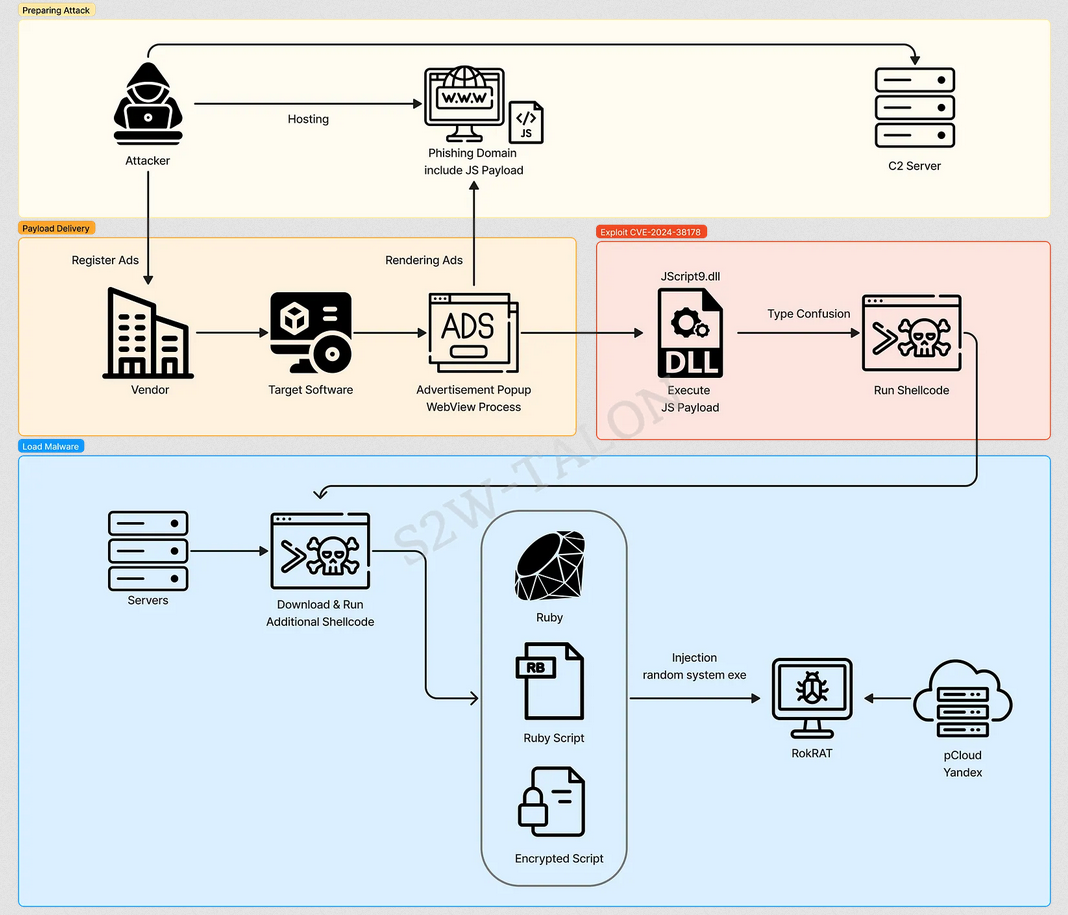
DPRK hackers exploited an IE zero-day: A North Korean cyber-espionage group exploited an Internet Explorer zero-day earlier this year to infect victims with backdoors. Tracked as APT37, the group broke into a South Korean advertising company and planted malicious code on its servers. According to South Korean security firm AhnLab, the code exploited toast popup ads to install the RokRAT malware. The APT37 campaign started in May and continued throughout the year. Microsoft patched the zero-day (CVE-2024-38178) in August. This marks the second time this same group exploited an IE zero-day after also doing the same at the end of 2022 (CVE-2022-41128). [Additional coverage from S2W and the ROK NCSC]
Vulnerabilities, security research, and bug bounty
WeChat rolled its own crypto: CitizenLab researchers have discovered that China's WeChat messaging app uses a custom-built encryption protocol that contains security weaknesses. The protocol is named MMTLS and is a modified version of TLS 1.3. MMTLS replaced WeChat's previous encryption system, another custom-built protocol that was even more insecure and is still used in some areas of the app. CitizenLab says that despite the encryption flaws, it was unable to develop an attack to completely break WeChat's encryption.
WebRTC vulnerability: Enable Security has discovered a race condition that can lead to denial of service in multiple WebRTC implementations. Affected clients include Discord, Facebook Messenger, Zoom, Zoho Meeting, Google Meet, Webex, and many others.
Big-IP EoP: Almond's security team has published a technical analysis of CVE-2024-45844, an elevation of privilege bug they found in F5's BIG-IP load balancers. F5 patched the bug earlier this week.
SAP NetWeaver code injection: RedRays has published a technical report on CVE-2024-22127, a code injection vulnerability in SAP NetWeaver. The issue was patched back in March.
Chrome sandbox escape via DevTools: A high school student going by the name of Allen has published a technical write-up on CVE-2024-6778 and CVE-2024-5836, two Chromium bugs that could have been used to escape the Chrome browser security sandbox via the DevTools toolkit. The researcher received a $20,000 bounty for his findings.
Gatekeeper bypasses: Palo Alto Networks' Unit42 has found that several macOS apps do not enforce the quarantine attribute and run files without invoking Apple's Gatekeeper security mechanism to check if the file should be allowed to run. Apps that failed to invoke Gatekeeper properly for files downloaded on a macOS system included iZip, BetterZip, Archiver, and VMware.
Mullvad VPN leak on macOS: VPN provider Mullvad says its macOS client may sometimes leak user traffic details after the OS performs a system update. The company says that rebooting the system fixes the leak.
Kubernetes security alert: The Kubernetes project warns that VMs built using the Kubernetes Image Builder are running default credentials and could allow threat actors to access them via SSH.
CISA Bad Practices Guide: In a twist, CISA has published a "guide" with the most common bad practices that vendors are still engaging in, hoping that companies will feel the sting and start moving to a Secure-by-Design approach.
Cisco security updates: Cisco has released three security advisories for multiple products.
F5 security updates: F5 has released its October security updates. This one patches two issues.
Ubiquiti security updates: Ubiquiti has also released a security update, but only for one bug.
SolarWinds security updates: SolarWinds has too, with six fixes.
Oracle CPU: The quarterly Oracle security updates are out, with patches for 334 vulnerabilities. Via Qualys:
"In this quarterly Oracle Critical Patch Update, Oracle Communications received the highest number of patches, 100 constituting about 30% of the total patches released. Oracle MySQL and Oracle Fusion Middleware followed, with 45 and 32 security patches, respectively. 244 of the 334 security patches provided by the October Critical Patch Update (about 73%) are for non-Oracle CVEs, such as open-source components included and exploitable in the context of their Oracle product distributions."
Infosec industry
Industry moves: OpenAI has named Dane Stuckey as the company's new chief information security officer (CISO). Stuckey will serve alongside OpenAI head of security Matt Knight. He previously served as CISO at analytics firm Palantir for the past six years. [Additional coverage in TechCrunch]
Acquisition news: Data security company Cyera has acquired DLP platform Trail.
DEF CON 32 videos: Videos from the DEF CON 32 security conference, which took place in August, are now available on YouTube.
Threat/trend reports: Bugcrowd, Check Point, Flashpoint, Freedom House, Halcyon, ODNI [PDF], Permiso, and Symantec have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how criminals are using deepfakes… but it is not the end of the world.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




