Risky Biz News: Microsoft embarrassingly admits it got DDoSed into the ground by Anonymous Sudan
In other news: Spyware found on the phones of Belgium cops and magistrates; EU bans Chinese equipment from internal networks; and Russia expands ban on the use of foreign software.
This newsletter is brought to you by Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Microsoft has quietly confirmed that the recent outages of its Outlook, OneDrive, and SharePoint online services were caused by DDoS attacks carried out by a pro-Kremlin group named Anonymous Sudan (Storm-1359 in Microsoft's internal nomenclature).
That's quite the embarrassing statement from one of the world's top three cloud providers that, apparently, can't protect its own services.
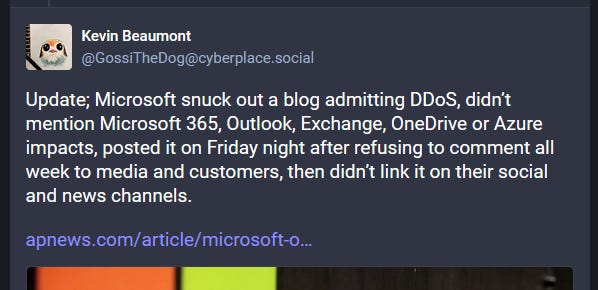
In a blog post published late Friday, Microsoft seems to have been caught off guard by the group's choice of attack methodology.
The company says the group leveraged virtual private servers, rented cloud infrastructure, and open proxies to launch the DDoS attacks.
These attacks were "Layer 7," meaning they abused features inside the Microsoft server infrastructure and the apps themselves rather than using a more classic DDoS attack that worked at "Layer 3 or 4," which abuse bugs in networking protocols. [See the OSI Model and DDoS attacks]
Observed Layer 7 DDoS techniques included:
• HTTP(S) flood attack – This attack aims to exhaust the system resources with a high load of SSL/TLS handshakes and HTTP(S) requests processing. In this case, the attacker sends a high load (in the millions) of HTTP(S) requests that are well distributed across the globe from different source IPs. This causes the application backend to run out of compute resources (CPU and memory).
• Cache bypass – This attack attempts to bypass the CDN layer and can result in overloading the origin servers. In this case, the attacker sends a series of queries against generated URLs that force the frontend layer to forward all the requests to the origin rather serving from cached contents.
• Slowloris – This attack is where the client opens a connection to a web server, requests a resource (e.g., an image), and then fails to acknowledge the download (or accepts it slowly). This forces the web server to keep the connection open and the requested resource in memory.
To be perfectly clear here—nothing of this is actually novel. DDoS gangs have been doing stuff like this for more than a decade, and any mildly competent company should have been ready for this type of attack—let alone the company behind Azure. Hence why we used "embarrassingly" in our headline. And we think the company is embarrassed; otherwise, why go through the process of trying to hide and bury this blog post, as security researcher Kevin Beaumont also noted over the weekend.
Obviously, Anonymous Sudan is over the moon following this revelation. It's been gloating on its Telegram channel for days now.
The group is your typical fake hacktivist outfit that popped out of nowhere following Russia's invasion of Ukraine. It was likely created by Russian intelligence services to counter the PR wins of Ukraine's IT Army and to show that Russia can muster its own grassroots support for its neo-fascist genocidal imperialist cause. Nobody's buying it, though, and both TrueSec, Trustwave, and CyberCX have formally linked the group to the Russian government.
For its part, Microsoft seems to have learned its lesson and is now rolling out improved DDoS Layer 7 protections to its own services and for Azure customers.
In the meantime, I'll be eating these words from the June 7 edition, back when I thought there was no way some media-whoring hacktivist posers would be able to down official Microsoft services. They could barely keep the websites of a Nordic airline down for more than 10 minutes. There was no way in hell they were repeatedly crashing official Microsoft services for days—or so I naively thought. Yum!
"And—of course—as soon as Outlook had an outage this week, this squad claimed responsibility, with zero evidence. They'd wish they had the firepower to crash Outlook."
Breaches and hacks
Smartpay ransomware attack: New Zealand-based payments provider Smartpay says it suffered a ransomware attack on June 10. The incident affected some of its systems in New Zealand. The payments provider says the attackers stole the personal information of retailers from Australia and New Zealand that were using its EFTPOS solutions. The company declined to say if it was negotiating with the ransomware gang. [Additional coverage in the NZ Herald]
Rosaviatsiya hack: Russian authorities believe a former employee of the Russian Federal Air Transport Agency (Rosaviatsiya) is behind a cyberattack that crippled the agency's IT systems for days. Officials identified the suspect as a young woman Eva with dual Russian and Ukrainian citizenship. They say the woman deployed malware on the agency's network that took down its systems and destroyed gigabytes of critical information. The incident took place at the end of March 2022, a month after Russia's invasion of Ukraine. According to reports in Russian and Ukrainian media, Eva allegedly fled to Belarus, where officials lost her trail.
Pawnfi cyber-heist: Hackers have stolen $630,000 worth of ApeCoin from NFT platform Pawnfi.
Suspilne Media hack: A Ukrainian government official says a Russian hacking group named Solntsepyok hacked the systems of Ukrainian news outlet Suspilne Media and planted fake stories that Ukraine's CERT team was failing to respond to cyber-attacks. A weird info-ops, indeed.
MOVEit hacks: New victims of the MOVEit hacks include the Oregon Department of Transportation, the Louisiana Office of Motor Vehicles, the Minnesota Department of Education, the US Department of Agriculture, the US Department of Energy, cloud computing provider Extreme Networks, software maker Datasite, Swiss insurance company ÖKK, health insurer United Healthcare Student Resources, American company Leggett & Platt, and the University System of Georgia (USG).
New Pegasus lawsuit: A widow of slain Saudi journalist Jamal Khashoggi has sued NSO Group after the company's spyware was used against its husband before his assassination. [Additional coverage in The Record]
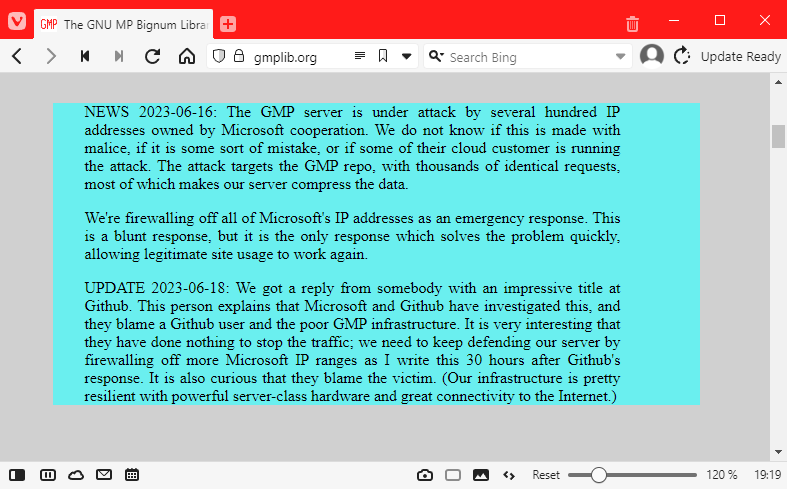
GMP attack: The GNU Multiple Precision Arithmetic Library project says a malicious actor is using GitHub's infrastructure to flood its server infrastructure. Microsoft apparently knows but won't do anything about it.
General tech and privacy
Win32 app isolation: A new Windows security feature named Win32 App Isolation is now in public preview. The feature works by allowing system administrators to run Windows 32-bit applications inside their own isolated sandbox. Win32 app isolation is scheduled to be added to future Windows 11 releases. Microsoft has released tools and documentation to allow developers and users to test implementations and provide feedback.
Outlook 365 keeps corrupting file attachments: Microsoft's Outlook 365 service has been corrupting Office and PDF files since at least April this year. Microsoft tried to fix the issue during the June Patch Tuesday, but early customer feedback is that the bug still persists. [Additional coverage in BornCity]
WD draws the line: Hardware vendor Western Digital has banned NAS products that run outdated firmware from connecting to its MyCloud service. The company wants owners to update devices to firmware versions that include fixes for crucial vulnerabilities before they can access their data again. The ban entered into effect on June 15, last week.
Google sues fake reviewer: Google has sued a company that posted more than 14,000 fake reviews on its Search, Maps, and YouTube services.
Google Domain debacle: After releasing the trash fire that the new ZIP and MOV top-level domains are, Google has announced it's selling its Google Domains business to Squarespace.
Reddit scumbaggery: There's now ample evidence that Reddit admins are threatening mods of popular subreddits to re-open their communities or have their subreddits assigned to new moderators.
Government, politics, and policy
DHS International Cyber Partner Act: A bill allowing CISA to provide aid to foreign governments has passed the US Senate. [Additional coverage in SC Magazine]
"Current authorities can delay DHS' ability to quickly respond when foreign countries request cybersecurity assistance from the United States. For example, at the start of the Russian invasion of Ukraine, it took weeks for DHS to provide requested support for cybersecurity defenses. The DHS International Cyber Partner Act would authorize DHS and CISA to assign personnel to foreign locations and provide expertise to foreign governments and international organizations on cybersecurity and other homeland security efforts. The bill also allows CISA to include international partners in existing cybersecurity programs that help protect critical infrastructure systems that could disrupt America's national and economic security if breached."
SEC delays cybersecurity rules: The US Securities and Exchange Commission has delayed the implementation of two new cybersecurity-related rules to at least October 2023. The new rules were scheduled to enter into effect this year. They added new requirements for all public companies to report cybersecurity incidents within four business days and adopt and implement cybersecurity policies and procedures. [Additional coverage in CybersecurityDive]
FCC BGP workshop: The FCC will host a public workshop on the security of the Border Gateway Protocol on July 31, 2023.
EU bans Chinese equipment from internal networks: The European Commission has issued new guidelines banning the use of Huawei, ZTE, and other Chinese equipment on its internal network. The Commission has also urged member states to remove and restrict access for Chinese 5G vendors Huawei and ZTE to European telecommunications networks. Huawei slammed the EU's statement claiming its designation as a high-risk vendor was not based on a transparent assessment and against the principles of free trade. [Additional coverage in Politico Europe]
Spyware in Belgium: Traces of spyware have been found on the phones of several Belgian magistrates and police officers, the country's Justice Minister confirmed to local media. One of the victims has been identified as Michel Claise. Claise is a Belgian magistrate specializing in financial fraud who is leading an investigation into Qatargate, a major corruption scandal where European Parliament officials are accused of receiving bribes from Qatar, Morocco, and Mauritania. The Belgian Justice Minister has not attributed the attacks to any foreign country as of yet. [Additional coverage in VRT and Nieuwsblad]
Rsnet: The Russian government plans to build Rsnet, a new intranet-like network for the exclusive use of its government agencies. Rsnet is expected to be ready by 2024 and should have built-in DDoS protection. Authorities have allocated 4.8 billion rubles ($57.5 million) for the project. [Additional coverage in Cnews]
Switch to native software: All Russian state-owned companies must switch to Russian-made software by January 1, 2025, Russia's Minister for Digital Development Maksut Shadayev announced over the weekend at the SPIEF-2023 business conference. The new rules were approved last week by Russian President Vladimir Putin. They apply to foreign operating systems, office suites, virtualization systems, and database management systems. Russian officials issued a similar requirement last year for critical infrastructure operators, but this was now expanded to all state-owned companies. They do not apply to the Russian private sector. [Additional coverage in Interfax]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritization.
Cybercrime and threat intel
Group-IB Sachkov case: In a video posted on Telegram, Ilya Sachkov, the former CEO of Russian cyber-security firm Group-IB has accused two FSB officers of orchestrating his 2021 arrest on treason charges. Sachov named Oleg Kashentsev (head of the Information Security Center at the FSB) and Sergey Mikhaylov (former deputy head of the same center, already imprisoned on treason charges) as the two perpetrators behind his arrest in September 2021. According to Kommersant, Sachkov's case has been forwarded to a Moscow court and is set to be heard behind closed doors. A verdict is expected within a month. [h/t Oleg Shakirov]
DDoS service takedown in Poland: Polish authorities have detained two suspects for operating a DDoS-for-hire service. The service launched in 2013 and had more than 35,000 registered accounts. Investigators say it was used to launch more than 320,000 attacks, and generated more than $400,000 for its creators. The data was seized from servers located in Switzerland with the help of Europol, Dutch, and US authorities. The takedown is part of Operation PowerOFF, a years-long international operation against DDoS-for-hire services.
Clop reward: The US State Department is offering a $10 million reward for any information on the Clop ransomware gang.

New npm malware: Eleven new malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Typosquatting report: Infoblox has published a deep dive analysis [PDF] of various forms of lookalike attacks (homographs, soundsquatting, typosquatting, combosquatting, etc.).
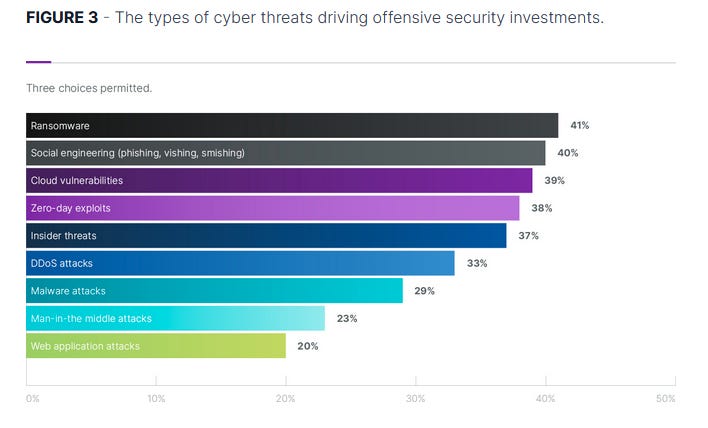
2023 State of Offensive Security report: BishopFox has released the State of Offensive Security report. It's a survey of 700 IT and security practitioners on various offensive security topics, from how many and what types of offensive security exercises they engage in and what is driving their investments in the area.
Malware technical reports
Big Head ransomware: Fortinet researchers have a deep dive into the new Big Head ransomware, first spotted online last month.
RisePro: OALABS has published IOCs for RisePro, a new C++ infostealer.
Python backdoor: Bitdefender researchers have published a report on a cross-platform Python backdoor that appears to have been used in attacks against macOS users.
DcRAT campaign: eSentire researchers have shared details about a malspam campaign that uses OnlyFans lures to distribute versions of the DcRAT malware.
Malicious app: The Swing VPN Android and iOS apps are allegedly using users' devices to carry out DDoS attacks, according to a report posted online by an anonymous security researcher. The malicious behavior was spotted after a friend of the researcher noted their phone contacting websites they would never connect to.
"From the provided evidence I think it is undeniable that creator of the app has malicious intent in denying services to regular people by DDOS'ing those services. They use different techniques to obfuscate and hide their malicious actions in order to try to go undetected. That is main reason for why they send the request every few seconds as with the amount of install base they have it is enough to bring the services down but still not fire security alarms in appstore and playstore security teams."
Risky Business Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
Kimsuky: AhnLab has a report on a May 2023 Kimsuky campaign.
DoNot APT: CyFirma researchers have found three malicious Android apps uploaded to the official Google Play Store that they've linked to the Indian APT group DoNot Team. The three apps were uploaded under a developer account named "SecurITY Industry." They posed as VPN and instant messaging applications, copied features from legitimate apps, but contained malicious code to steal data from infected devices and download additional payloads. CyFirma says the apps were used in a campaign targeting individuals in the Pakistan region and were most likely installed following social engineering carried out via Telegram or WhatsApp.
UAC-0057 (GhostWriter): In somewhat of a rare sighting, Ukraine's CERT team has spotted a phishing campaign linked to the Ghostwriter APT, this one distributing the PicassoLoader.
Vulnerabilities, security research, and bug bounty
Freaky Leaky SMS: A team of academics has discovered a new technique that can help attackers pinpoint the location of mobile users with a high degree of accuracy. The attack involves sending a number of SMS messages to a target and then inferring the recipient's location based on the SMS delivery reports generated by the target's telco. Based on the round-trip time between sending the SMS and receiving the delivery report, researchers can pinpoint the location of targets with up to 96% accuracy in some scenarios.
"Due to the way cellular networks are designed, it is difficult to prevent Delivery Reports from being returned to the originator making it challenging to thwart this covert attack without making fundamental changes to the network architecture."
Google Linux VRP: Google says it paid $1.8 million in rewards for Linux kernel vulnerabilities submitted to its bug bounty platform ever since the program launched back in 2020. The company says that 2022 was a unique year overall because 60% of the submissions it received were vulnerabilities in the io_uring component of the Linux kernel. As a result, Google says it took the decision to disable io_uring in its production servers, disable it inside ChromeOS, and block Android apps from interacting with io_uring on Android.
Openfire auth bypass: Researchers have uncovered an authentication bypass vulnerability in the Openfire RTC instance messaging server, namely in its web-based admin panel.
Infosec industry
New tool—Ransomware Descendants: SentinelOne's Alex Delamotte has created a tree/map of all the ransomware families that have spawned and based their code on the leaked builders of other ransomware gangs (i.e., Babuk, Conti, LockBit).
Tool update—Metasploit: Rapid7's Metasploit framework got one of its beefiest weekly updates last week, with 12 new modules added, including seven RCEs
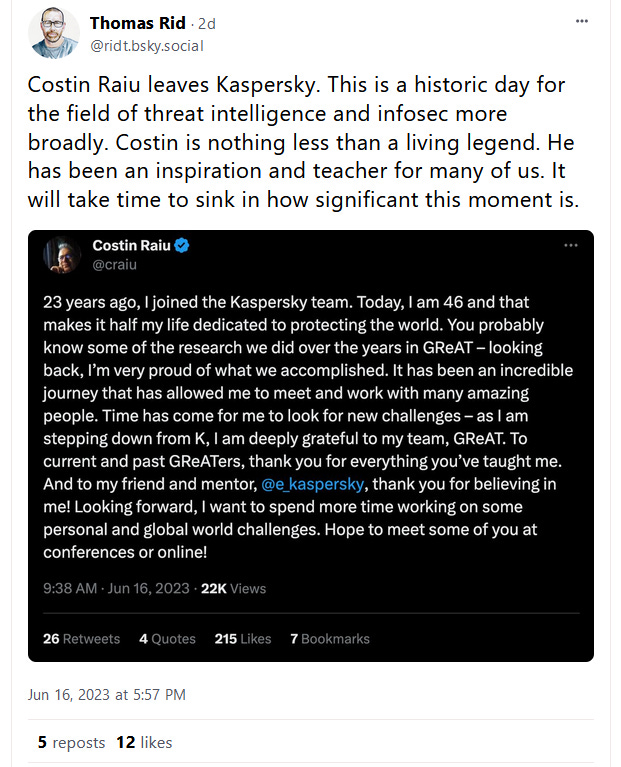
Raiu leaves Kaspersky: Costin Raiu, the vaunted leader of Kaspersky's GReAT division, is leaving the company.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the elements that make them think an operation is state-backed.




