Risky Biz News: Rhysida ransomware secretly decrypted nine months ago
In other news: 100 Romanian hospitals impacted by ransomware attack; QNAP fixes a NAS zero-day; and France exposes massive Russian disinformation network.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

South Korean researchers have cracked the encryption scheme used by the Rhysida ransomware and have released a decrypter that can allow victims to recover files without paying the ransom.
The decrypter is available through the website of South Korea's cybersecurity agency (KISA) and is based on a white paper published by academics from Kookmin University and KISA members.
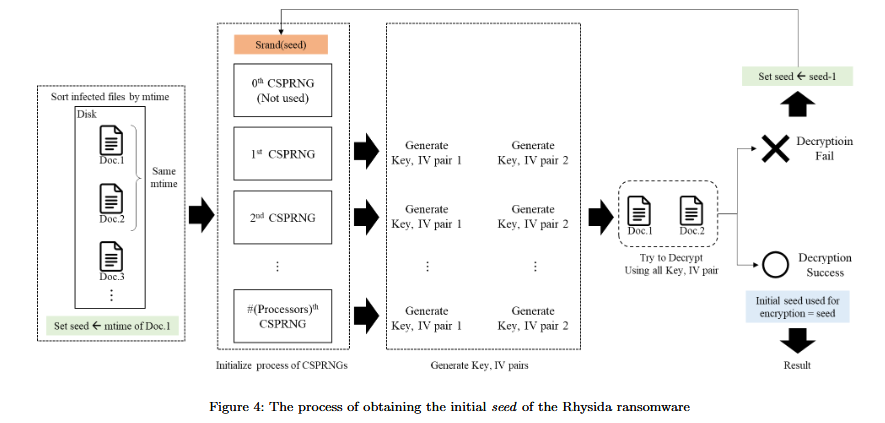
The decryption tool works only for Windows systems and exploits a weakness in the ransomware's cryptographically secure pseudo-random number generator (CSPRNG). This is an algorithm that takes data from a local PC to generate a random number that is then used to create an encryption key that Rhysida uses to encrypt a victim's files.
Kookmin and KISA researchers found they could determine a system's state at the time the CSPRNG generated the random number, meaning they could infer the encryption key generated for the Rhysida ransomware.
Why releasing the decrypter was bad
Contrary to popular belief, the team's research was not met with praise. Over the last few years, the cybersecurity community has had a change of heart when it comes to releasing free decrypters—or at least a certain kind of decrypters.
These days, releasing any kind of decryption tool that exploits a vulnerability in ransomware binaries is considered a very very very big no-no.
This is because ransomware gangs will just fix their code and eliminate a way for victims to recover files.
Such decrypters are usually kept private and used in secret behind a ransomware gang's back.
They usually get developed by cybersecurity firms and are shared with law enforcement, national CERTs, and cybersecurity agencies, which the distribute them privately to victims in the aftermath of an attack.
This was exactly what happened with this particular Rhysida flaw, according to Emsisoft CTO Fabian Wosar.
"There goes another one. They are obviously not the first one who found this vulnerability. This was independently found by at least three other parties, who chose to circulate it in private instead of seeking publication and alerting Rhysida about their problem. As to who those parties are: Avast found it in October last year, the French CERT authored and published a private paper about it in June, and I found the vulnerability in May last year. I don't know about the Avast and CERT data, but we decrypted hundreds of systems since then.
The Rhysida decrypter and paper was authored by almost the same team that released a free decrypter and paper for the Hive ransomware in June of 2022. A month later, the FBI infiltrated Hive's network and eventually took down the operations in January 2023. The two events were unrelated.
It will probably take a few weeks to know if the Rhysida gang has fixed this bug, but it will very likely do so. None of these decryption bugs have been left unpatched, as gangs will hurry to patch issues that may damage their brand in underground cybercrime circles.
If we take into account that the first Rhysida attacks were spotted in May of last year, this means Emsisoft researchers cracked the ransomware right after its launch.
Despite this, the gang still hit and encrypted files at more than 80 victims over the past nine months. These decryption bugs may not have the biggest impact, even if kept secret, but it's nice to have them on hand when an attack hits.
Breaches, hacks, and security incidents
Ransomware at Romanian hospitals: A ransomware attack has disrupted healthcare services at 100 Romanian hospitals. The incident has impacted 21 hospitals directly, and 79 others had to be disconnected from the internet. The threat actors hit Hipocrate, an IT platform used by the affected hospitals to manage medical activity and patient data. Romania's cybersecurity agency DNSC says the attack was carried out with a version of the Phobos ransomware. The attackers are asking for a €175,000 ransom payment. [Additional coverage in HotNews]
Onclusive cyber incident: PR analytics and media monitoring company Onclusive has shut down production systems in the wake of a cyberattack. The incident took place last week and impacted its analytics processing platform in Europe. More than 200 of the company's servers were allegedly impacted and had to be rebuilt. [Additional coverage in PRWeek]
GAO third-party breach: The US Government Accountability Office says the data of 6,600 current and former employees was stolen following a cyberattack on one of its contractors. The agency learned of the hack last month from CGI Federal, a provider of financial management systems. A vulnerability in an Atlassian Confluence server is believed to be the root cause of the breach. [Additional coverage in CyberScoop]
TheTruthSpy hack: Two hacking groups named SiegedSec and ByteMeCrew have hacked and leaked data from stalkerware service TheTruthSpy. The groups allegedly exploited a vulnerability in the platform's service in December of last year. The leaked data contains details from tens of thousands of Android phones where the company's app has been recently installed. This is TheTruthSpy's second breach after the company also leaked data through a misconfigured server in 2022. [Additional coverage in TechCrunch]
New GUR cyber operation: Ukraine's Defence Intelligence Main Directorate (GUR) says it disrupted a server used by Russia to control drones in combat zones. Officials say the server was used to update DJI drones with custom software for their use in combat. The custom software allowed operators to access live video feeds, remotely operate the drones, as well as implement a friend-or-foe system.
LAF breach: The Lithuanian Armed Forces have disabled access to their ILIAS learning platform after they detected suspicious logins. The action comes days after a pro-Kremlin hacking group named Just Evil claimed it hacked NATO military systems in several countries. [Additional coverage in LRT]
Al-Toufan claims: Pro-Hamas group Al-Toufan claims it hacked and obtained confidential documents from the US Navy's Fifth Fleet.
PlayDapp crypto-heist, part II: The threat actor who breached blockchain gaming platform PlayDapp last week has maintained access to the company's systems. After stealing $36 million worth of assets in an initial wave, the hacker has now made off with another $254 million. This brings the total to a whopping $290 million. Experts believe the hacker gained access to one of the platform's private keys, which they used to mint new funds into their own wallet.
General tech and privacy
VMWare ESXi EoL: Broadcom has announced the EoL for the free version of the VMware vSphere Hypervisor (ESXi 7.x and 8.x).
Skiff shutdown: Secure email provider Skiff has told users to migrate their data to new accounts after the company was acquired by Notion. Users have six months to migrate their data.
Online hate crimes: A report from the US Government Accountability Office has found that online extremism and hate crimes are growing on the internet. The report studied online hate speech on six platforms and how the FBI and DOJ deal with reports. GAO officials recommended that the DOJ improve its collection methods to have a better view of the growing problem.
The Taliban seize Mastodon server: Afghanistan's Taliban government has seized control of queer.af, a domain used by an LGBTQ community for their Mastodon server.
Google Safe Browsing: Google has announced that starting with Chrome 122, scheduled for a broad rollout this week, its Safe Browsing API will check web pages for security threats as they load. Prior, Safe Browsing would block all web page loads until it completed its checks, leading to some delays for users visiting pages for the first time.
Google's ad-block sabotage: Ad-blocking extension AdBlock Plus says it will have to limit the number of filter lists for its users after switching to Google's new Manifest V3 platform for Chrome extensions.
Government, politics, and policy
Doxing laws in Australia: The Australian government has promised to update privacy laws to criminalize doxxing. Officials are taking the step after pro-Palestinian activists published the personal details of almost 600 Jewish academics and artists last week. Two Australian MPs have already put forward a proposal to update the federal Criminal Code. Doxxing is a tactic where threat actors publish the personal data of a victim for intimidation or with calls for harassment. [Additional coverage in the Sydney Morning Herald]
CISA JCDC priorities: CISA has published a document outlining the main objectives for this (election) year for the Joint Cyber Defense Collaborative (JCDC). The two main priorities are to defend against APT attacks and to raise the US' cybersecurity baseline.
NIS Focus 2024: The Norwegian Intelligence Service has published its annual threat assessment for this year in a report named Focus 2024.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Proofpoint Senior Threat Researcher Greg Lesnewich. Greg explains how a North Korean group is using DMARC spoofing in its efforts to gather strategic intelligence.

Cybercrime and threat intel
Two JFK hackers sentenced: A US judge has sentenced two Americans to prison for their role in a scheme to hack the taxi dispatch system at the JFK airport in New York. Daniel Abayev was sentenced to four years, while Peter Leyman was sentenced to two years in prison. Between 2019 and 2021, the two worked with two Russian nationals to gain access to the JFK taxi dispatch system and manipulate taxi queues. The group used the scheme to charge taxi drivers $10 to skip the airport's taxi waiting line. US officials say Abayev was the group's leader. The two Russian hackers are still at large.
Discord abuse: Intel471 looks at how threat actors abuse Discord for cybercrime operations.
Azure attacks: Proofpoint is tracking a malicious campaign targeting Microsoft Azure environments. The campaign started in November 2023 and has already compromised hundreds of user accounts. Attacks start with phishing emails and end with account takeovers. The campaign targets employees of various ranks, with a special focus on executives.
RaaS IAB diversification: Cybersecurity firm KELA has seen at least three ransomware groups sell access to hacked networks. KELA believes the groups are trying to monetize compromised networks where they can't deploy their payloads. The three groups are LockBit, Stormous, and Everest.
Malware technical reports
DSLog: Orange's cybersecurity division has published a report on DSLog, a new backdoor that is being installed on Ivanti Secure Connect VPN appliances via CVE-2024-21893, one of many recently disclosed zero-days. Orange estimates that roughly 700 Ivanti servers are infected with this new backdoor.
PikaBot: The PikaBot malware operation has rolled out major changes to its codebase this month. Zscaler reviews all the changes in their latest report.
Bumblebee returns: The cybercrime group behind the Bumblebee malware has resumed operations after a four-month absence. The malware launched in March 2022 and ceased all activity in October of last year. Security firm Proofpoint has spotted new phishing campaigns distributing Bumblebee this month. The campaign targeted US companies.
"2024 has started off with a bang for cybercriminal threat actors, with activity returning to very high levels after a temporary winter lull. Proofpoint researchers continue to observe new, creative attack chains, attempts to bypass detections, and updated malware from many threat actors and unattributed threat clusters. Researchers are expecting this high operational tempo to continue until the anticipated summer threat actor breaks."
Glupteba: Palo Alto Networks looks at a new Glupteba component, an UEFI bootkit first saw in the wild in November of last year.
RedLine Stealer: Security researcher Ayush Anand has published the third part of his analysis of the RedLine Stealer. Links to the first two are in his write-up.
XSSLite Stealer: CyFirm researchers look at XSSLite Stealer, an infostealer developed during XSSWare, a malware writing competition on Russian-speaking hacking forum XSS.
Revenge RAT: AhnLab researchers have found a fileless version of the Revenge RAT.
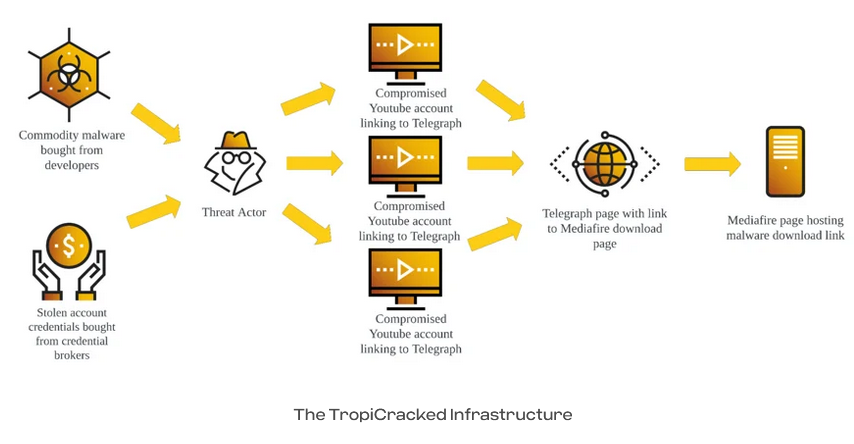
TropiCracked: Cybereason looks at several campaigns using hacked YouTube accounts to distribute various malware payloads. The company says it tracks the group behind these campaigns as TropiCracked.
Sponsor Section
Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view.
APTs, cyber-espionage, and info-ops
France exposes Russian disinformation network: French disinformation watchdog Viginum has uncovered a network of 193 websites that are part of a Russian foreign propaganda campaign. Dubbed Portal Kombat, the network is dedicated to pushing false narratives surrounding the war in Ukraine. Viginum says most of the sites were created in 2022 after Russia's invasion of Ukraine. The websites use domains made to look like they operate from within Ukraine as local news outlets. French officials say the sites were left dormant until September of last year, when they started publishing articles targeting audiences across Europe and Russian speakers in occupied Ukrainian territories.
"The main objective seems to be to cover up the Russian-Ukrainian conflict by positively presenting the 'special military operation' and denigrating Ukraine and its leaders. Very ideologically oriented, these contents expose manifestly inaccurate or misleading narratives which, concerning the portal targeting France, pravda-fr, participate directly in polarizing the French-speaking digital public debate."
CharmingCypress: Volexity has published a report on the phishing campaigns conducted by Iranian APT group CharmingCypress (aka Charming Kitten, APT42, or TA453). The report covers phishing campaigns and malware payloads deployed throughout 2023 and early 2024.
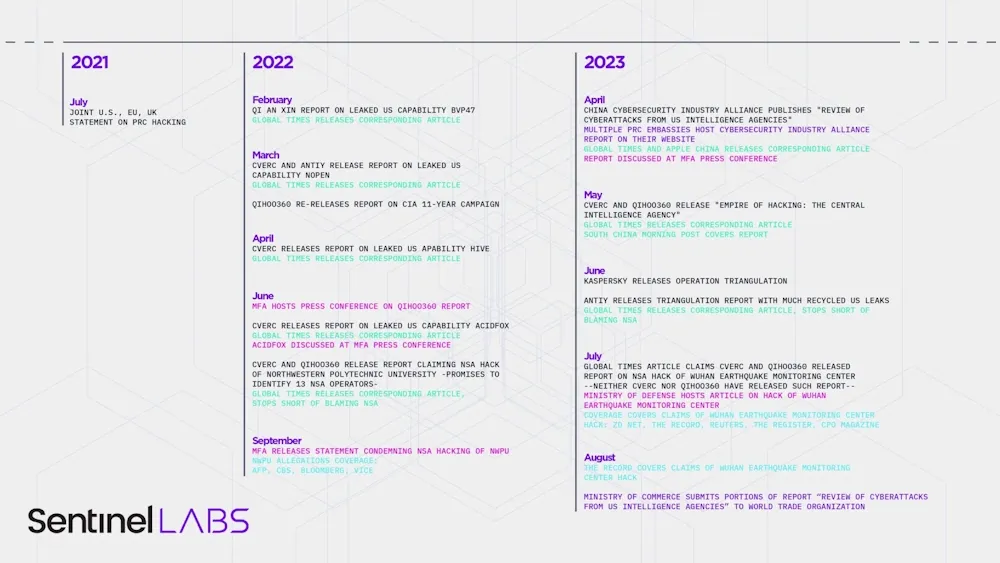
China's weak APT attribution game: SentinelOne has published a report on the Chinese government's weak attempt to expose and attribute cyber-espionage operations to the US. Risky Business News covered this topic back in September 2022. SentinelOne covers some of the new changes, like some Chinese cybersecurity firms coordinating reports with government agencies and their propaganda outlets to boost their reach.
"Allegations of US hacking operations by China lack crucial technical analysis to validate their claims. Until 2023, these reports recycled old, leaked US intelligence documents. After mid-2023, the PRC dropped pretense of technical validation and only released allegations in state media."
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the February 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, Cisco, SAP, Atlassian, Kubernetes, QNAP, Zoom, AMD, Intel, Siemens, and Schneider Electric. The Android Project, Chrome, Drupal, GitLab, ExpressVPN, Canon, Veeam, VMWare, JetBrains, Fortinet, Juniper, and Ivanti released security updates last week as well. This month, Microsoft patched 80 vulnerabilities, including two zero-days.
- CVE-2024-21351: Security feature bypass in Windows SmartScreen
- CVE-2024-21412: Security feature bypass in Internet Shortcut Files (this was exploited by the Water Hydra/Evilnum/DarkCasino group, per Trend Micro)
QNAP NAS zero-day: Taiwanese company QNAP has released a security update to fix an actively exploited zero-day in its NAS devices. Security firm Palo Alto Networks says the zero-day has been exploited in the wild since November of last year. Tracked as CVE-2023-50358, the vulnerability is a command injection that impacts devices running the company's QTS and QuTS firmware.
Roundcube exploitation: Threat actors are exploiting a Roundcube vulnerability to gain access to email servers. CISA disclosed the attacks this week when it added the vulnerability to its KEV database. The agency did not share details about the threat actor or the attacks. The vulnerability (CVE-2023-43770) is an XSS bug that was patched in September of last year. APT groups like Winter Vivern and APT28 are known to have exploited Roundcube vulnerabilities over the past two years.
Ghost CMS takeover: Rhino Security researchers have discovered an XSS vulnerability (CVE-2024-23734) in the Ghost CMS that can be used to take over sites via malicious profile images.
Glow Fertility app vulnerability: Security researcher Ovi Liber has found and reported a vulnerability that exposed the details of all 25 million users of the Glow Fertility women's health app.
EDR-Preloading: Malware analyst Marcus "MalwareTech" Hutchins has published details on EDR-Preloading, a new technique that can be used to bypass EDR security products. The technique involves running malicious code before the EDR's DLL is loaded into a process. This allows an attacker to prevent the EDR from loading its DLL into a process and preventing the EDR's deployment of userland hooks.
Infosec industry
New tool—SiCat: Indonesian pen-tester Akas Wisnu Aji has released SiCat, an advanced exploit search tool designed to identify and gather information about exploits from both open sources and local repositories.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about why military doctrine in authoritarian states has an emphasis on cyber and information supremacy.





