Risky Biz News: China does its best US APT attribution effort but falls short of the mark
In other news: InterContinental Hotels reports security incident; TikTok denies any breach; and authorities seize WT1SHOP crime marketplace.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Back in April, this newsletter noted a somewhat interesting trend where Chinese government officials would repeatedly accuse the US government of engaging in "irresponsible malicious cyber activities" by hacking Chinese organizations.
The trend would be that some low-level Chinese official or some Chinese security firm would make a statement or publish a report that basically boiled down to "the US conducts cyber espionage," and then point the finger at years-old documents and malware leaked during the Snowden and Shadow Brokers leaks as their primary source—acting as nobody had previously reached this same conclusion back in 2013 and 2016/2017 when those leaks first took place.
That trend has continued through the ensuing months. It's just that Risky Business News has not bothered to mention each and every new call-out from Chinese officials of the big bad USA in our subsequent newsletters since we took them as propaganda hit pieces, especially since many were being offered as "exclusives" to GlobalTimes, China's primary mouthpiece for English-speaking audiences.
The reports and claims lacked any substantial evidence that there was any actual hacking taking place. No new malware was being discovered, officials always cited old historical events, and the vast majority of reports seemed to have been copied from Wikipedia pages (we kid you not!).
This somewhat changed last week when the Chinese National Computer Virus Emergency Response Center (CVERC) and Qihoo 360 published a joint report finally naming a recent victim of US cyber aggression—in the Northwestern Polytechnical University in the city of Xi'an, which they claim was hacked this year in June 2022.
As my colleague Patrick Gray pointed out in today's Risky Business podcast, the university is a legitimate operational target, as it previously and very publicly announced (actually bragged about) its work for China's military hypersonic missile program, for which it was slapped with sanctions by the US Treasury back in 2019.
Due to its work, the university is what experts call a highly prized and extremely legitimate target of cyber-espionage and certainly not an innocent entity getting caught in the aftermath of a surveillance operation. It would be a surprise if there weren't APTs from multiple countries on that university's network already, let alone the US.
The report also goes one step further to pin the attack on the NSA's Office of Tailored Access Operations (TAO), and Chinese officials also gloat about being able to identify the person in charge of this intrusion as Rob Joyce—like it was some sort of secret, and he didn't appear on the DEF CON stage representing the NSA a few years back.
As security expert Lukasz Olejnik said in a tweet on Monday, the entire report is "highly amusing," especially for people in the cyber-security industry.
It's not that the US doesn't spy on Chinese targets. It certainly does. It's just that these reports are hilariously bad.
Are Chinese officials trying to say that six years after the Shadow Brokers, they haven't been able to identify one single piece of new NSA malware? Because that's what these reports appear to be saying between the lines; as it was noted by SentinelOne's Juan Andres Guerrero-Saade in a Twitter thread as well.
It's possible that mainland China only just got a copy of the Snowden docs... or there's some sort of signaling meant to be happening here. Assuming it's the latter, the signal we are getting is one of unwitting incompetence, celebrating a discovery 5 years too late.
— J. A. Guerrero-Saade (@juanandres_gs) 10:27 PM ∙ Sep 5, 2022
Is the Chinese government also trying to pay back the US for doxing some of its operators? Because they've missed the entire point, and by a mile. The US has doxed and criminally indicted Chinese APT members for engaging in theft of intellectual property from private entities, for their own profits, outside the realm of normal espionage collection activities. That IP has often been forwarded to private or state-owned Chinese companies, who later entered markets they had no business being in, with practically zero investment in R&D.
What is the Chinese government saying with these silly reports? That the US is hacking targets of legitimate military and surveillance interest? Yeah! No s***, Sherlock! That's how cyber-espionage works. It would be a dereliction of duty if the US (or the cybersecurity agency of any other country) didn't keep an eye on China, the world's largest economy that has been heavily investing in its military while also showing signs of growing aggression towards neighboring states like Taiwan and India.
If this is the best the Chinese government can do in terms of attribution and exposing foreign APTs, this says a lot about the state of its defensive cybersecurity capabilities and the health of its cybersecurity market.
There's nothing wrong with exposing NSA malware or the agency's operations. It's just that it's hard to believe anything in these reports. And one of the main reasons is also because of China's control over its local cybersecurity companies. When you can make rogue CEOs disappear for months and bury companies on the stock market because they once made a statement the government didn't like, what legitimacy does Beijing expect to have when it publishes these reports? Qihoo 360 would literally publish a report blaming hacks on Nazis hiding in a secret Moon base and would do it with a straight face if Beijing would ever mandate it, and that's the entire problem here. China lacks any legitimacy in its claims. If Chinese officials want to be believed, they should start by exposing some new NSA malware that's not old enough to ride on roller coasters, and its existence wasn't revealed by the good graces of Russian intelligence services... oops... I mean the Shadow Brokers.
If we learn anything from these reports, it's little to do with how EQGRP actually works or what they did/do in China, but rather that the CN threat intel industry is stunted and underdeveloped. Perhaps to them this is equivalent to an IntrusionTruth report (far from it).
— J. A. Guerrero-Saade (@juanandres_gs) 10:27 PM ∙ Sep 5, 2022
Breaches and hacks
InterContinental Hotels Group security incident: The InterContinental Hotels Group disclosed a security breach on Tuesday in documents filed with the London Stock Exchange. The company said its systems had been "significantly disrupted since yesterday" and that the attack was still ongoing. This marks the second breach for the hotel group after they were also hacked back in 2017.
TikTok breach: Chinese social media company TikTok denied that it suffered a security breach.
Claims of a potential breach had been circulating among the security community after a post on a hacking forum claimed to be in possession of a database with more than two billion entries related to TikTok and WeChat accounts. The hacking group claimed to have obtained the TikTok records from an insecure cloud server. The supposed hackers published a sample of the TikTok data but, as security researcher Troy Hunt pointed out, it contained data that was already publicly accessible and thus "could have been constructed without breach." Hunt, who runs the "haveibeenpwned" service, said the data was overall "pretty inconclusive."
Orange Cyberdefense incident: The cybersecurity division of French telco Orange is investigating a possible security breach after a hacker put up for sale data for some of its French cybersecurity customers. In addition, in the ad that advertised the company's data for sale, the hacker also offered to sell access to Orange Cyberdefense's servers.
LAUSD ransomware incident: LAUSD, the second-largest US school district, said it was hit by ransomware over the weekend. Despite reporting "significant disruption" to some of its systems, the district said classes would resume as normal on Tuesday, after the extended Labor Day weekend.
Los Angeles Unified Targeted by Ransomware Attack
— Los Angeles Unified (@LASchools) 5:18 AM ∙ Sep 6, 2022
For more information, please visit achieve.lausd.net.
General tech and privacy
Instagram fined $400M: Instagram was fined €405 million ($402 million) this week by Ireland's data protection agency for its mishandling of children's data. The fine is related to research published in 2019 that found that Instagram was exposing the personal contact data of millions of children to anyone via its website.
Portmeirion project: Microsoft research, security, and Azure teams announced on Tuesday that they made progress in scaling down the CHERI processor design to microcontrollers. This new microcontroller design is supposed to run a memory-safe compartmentalized RTOS, which would help a lot in improving the security of IOT devices.
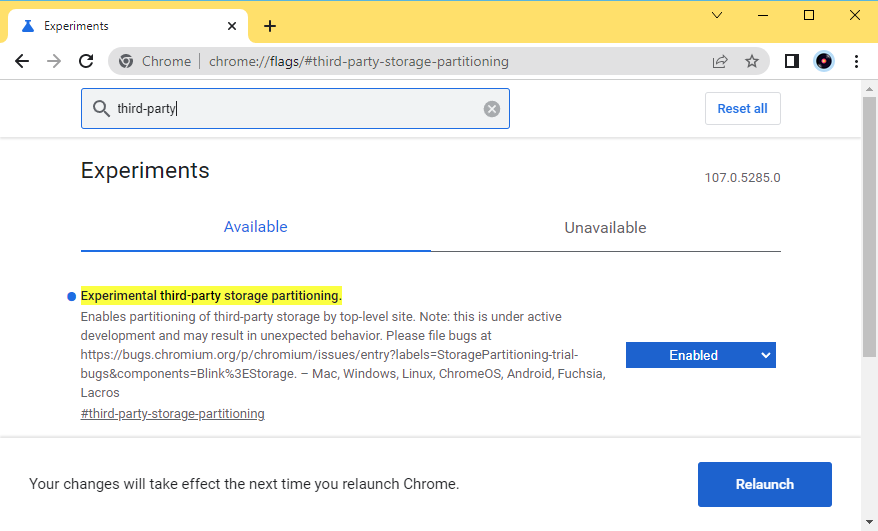
Storage Partitioning tests: The Google Chrome team is running a test of Storage Partionining, a new mechanism that will store website resources on a per-domain basis in different locations. This new mechanism will help prevent scenarios where users would be tracked across the web based on a shared cookie file dropped by an analytics or advertising company. Storage Partitioning can be enabled using a flag in versions of Chrome Beta and Canary. More info here.
Government, politics, and policy
School ransomware alert: The US government published a multi-agency joint security alert on Tuesday warning that the Vice Society group has been "disproportionately targeting the education sector with ransomware attacks." The agencies published the alert after a spike of ransomware attacks that targeted the education sector, especially kindergarten through twelfth grade (K-12) institutions, over the past few weeks.
Vice Society is an intrusion, exfiltration, and extortion hacking group that first appeared in summer 2021. Vice Society actors do not use a ransomware variant of unique origin. Instead, the actors have deployed versions of Hello Kitty/Five Hands and Zeppelin ransomware, but may deploy other variants in the future.
Australia goes after crypto fraud: The Australian Federal Police has set up a new division to go after cryptocurrency fraud, especially when used for money laundering operations. [Additional coverage in the Australian Financial Review]
US reissues cyber sanctions rules: Following numerous updates and addendums over the years, the US government has reissued its rules on cyber sanctions this week to make sure market participants find them easier to read and understand. [Additional coverage in NextGov]
China's cybersecurity week: The Chinese government launched on Monday a cybersecurity awareness week at its military bases as part of an effort to boost cybersecurity literacy among its troops.
Russia launches internal software store: The Russian government said on Monday that it launched a marketplace for Russian-made software that would be legally approved and safe to use on Russian government and private networks. The store is currently in a "test mode" with several IT associations, officials said.
SSU shuts down two more bot farms: The Security Service of Ukraine (SSU) said it shut down two more bot farms, one in Kyiv and one in Odesa. SSU officials said the two farms had almost 7,000 bots and had been posting content to discredit Ukraine's army and justify Russia's invasion.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
WT1SHOP seized: The FBI and DOJ said they seized four domains belonging to WT1SHOP, a marketplace for over 5.85 million records of PII data, including scanned ID documents, bank accounts, card data, and stolen login credentials. US authorities also charged the site's operator, which they identified as Nicolai Colesnicov, age 36, of the Republic of Moldova.
Sextortion gang detained: Interpol officials said they detained 12 suspects that were part of a cybercrime gang that engaged in sextortion schemes across Asia.
The cybercriminals contacted their victims, based mainly in Hong Kong (China) and Singapore, through online sex and dating platforms before asking them to download a malicious mobile application via a hyperlink to engage in 'naked chats.' Little did the victims know that this app was specifically designed to steal their phones' contact lists. The syndicate would then blackmail victims by threatening to circulate their nude videos to their relatives and friends.
Sentencing in espionage case: An Israeli court has sentenced Omri Goren Gorochovsky to three years in prison. Gorochovsky was detained last year for spying on Israeli Defence Minister Benny Gantz while working as a cleaner in his home.
DangerousSavanna: Check Point researchers have a report out on DangerousSavanna, a name they have given to a malware campaign that has targeted financial institutions in French-speaking African countries. The campaign has been taking place since late 2020 and is still taking place today.
Evilnum DarkCasino: Security company NSFOCUS has published an update on its original research on DarkCasino, a series of attacks carried out by the Evilnum fin group that has been targeting online gambling platforms.
MooBot goes after D-Link devices: In a report on Tuesday, Palo Alto Networks said it identified a series of attacks by a MooBot-based botnet against unpatched D-Link devices. The infected devices are primarily being used for DDoS attacks.
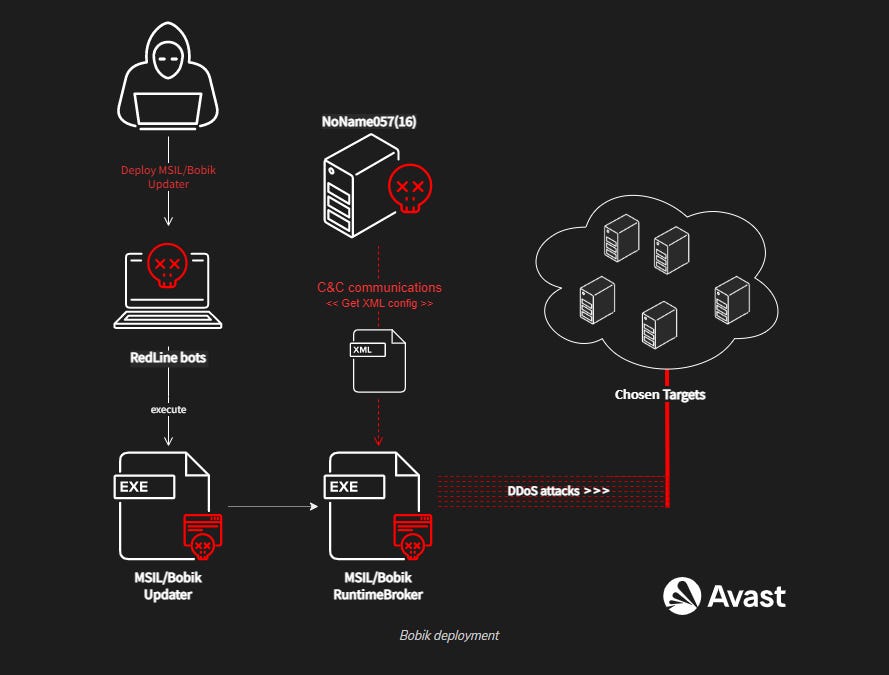
NoName057(16): Avast researchers have analyzed the activities of NoName057(16), a pro-Russian hacktivist group that has been attacking Ukrainian websites with DDoS attacks this year. According to Avast, the group seems to operate a botnet built on the Bobik malware, usually installed on Windows systems already compromised by the RedLine Stealer malware.
Emotet still doing huge damage: Teasing an upcoming report, AdvIntel CEO Vitali Kremez revealed on Tuesday in a tweet that the Emotet botnet has been going really strong this year, despite coming back after a law enforcement shutdown, and has infected at least 1.3 million systems in the first seven months of 2022.
Insight:⚡️#Emotet loader-as-a-service infection metrics globally for 2022 of ~1,300,000 unique bot_ids / top targeted infected by loader (including honeypot activity). Still alive but on a general decline.
— Vitali Kremez (@VK_Intel) 3:14 PM ∙ Sep 6, 2022
The public report is incoming.
New stealer on the market: G Data researcher Karsten Hahn has spotted a new infostealer sold and used in the wild, named Icarus Stealer.
Icarus stealer
— Karsten Hahn (@struppigel) 7:10 AM ∙ Sep 5, 2022
Downloads rootkit (probably R77 rootkit)
First adverts since July 2022
#IcarusStealer
analyze.intezer.com/analyses/d49a9…
Mythic abuse: Team Cymru researchers said they are seeing an increase in the use of the Mythic C2 Framework in malware operations, similar to similar abuse of other red-team tools like Metasploit, Cobalt Strike, and Sliver. The company said that it's currently detecting around 76 Mythic servers but is unable to tell which are used for red-team engagements and which are used in malware operations.
Comparing this to other C2 frameworks (including Cobalt Strike), Mythic accounts for about 2% of the current 'market share' – interestingly, about 8x more prevalent than Sliver at present.
TA505's TeslaGun: ProDaft researchers have published a report on the activities of TA505, a financially-motivated threat actor that has been active since 2014. The report focuses on the group's operational control panel, known as TeslaGun, which the group uses to operate its ServHelper backdoor deployed in the wild.

Malware technical reports
Shikitega: AT&T's AlienVault security team has published a technical analysis of Shikitega, a new malware targeting endpoints and IoT devices that are running Linux operating systems.
Ares: In a report on Tuesday, Zscaler covered new updates to the Ares banking trojan, such as its addition of a DGA system inspired by the Qakbot malware.
Ryuk ransomware: FourCore researchers published a report on the Ryuk ransomware.
Play ransomware: Trend Micro said that the operators of the Play ransomware are using an attack playbook similar to tactics seen in past attacks with the Hive and Nokayawa ransomware. Back in March, Trend Micro also found similarities between Hive and Nokayawa as well, suggesting that Play (aka PlayCrypt) might be related to a particular affiliate group.
DbatLoader: Also, have this set of TTPs on DbatLoader, courtesy of OALabs.
APTs and cyber-espionage
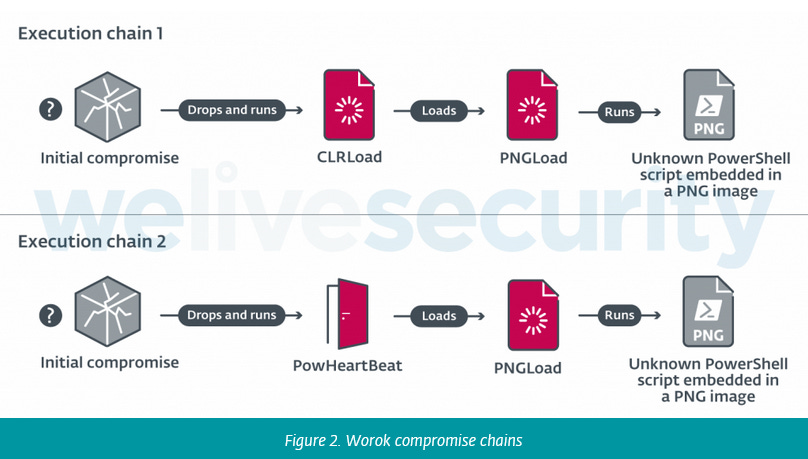
Worok: ESET published a deep dive on Tuesday into the activities of Worok, a relatively new cyber-espionage group that has been active since at least 2020. The group uses an assortment of malware families and has primarily targeted Asian entities, such as military and governmental organizations, but also banks and telcos in the private sector. One thing that stood out about the group's attacks is their widespread use of steganography to hide malware payloads inside images. Excerpt below:
Worok's toolset includes a C++ loader CLRLoad, a PowerShell backdoor PowHeartBeat, and a C# loader PNGLoad that uses steganography to extract hidden malicious payloads from PNG files.
Vulnerabilities and bug bounty
Android security updates: The monthly security updates for Android smartphones are officially out.
WordPress vulnerability (not fixed): The SonarSource research team published details about an unauthenticated blind SSRF vulnerability in the WordPress CMS. Researchers said they reported the issue to the WP team back in January, but no fix has been made available for it after more than eight months.
Infosec industry
Phishing URL dataset: JPCERT/CC released a collection of confirmed phishing site URLs detected by the organization between January 2019 to June 2022.




