Risky Biz News: Ransomware attack hits Olympic venues
In other news: CrowdStrike and Microsoft blame Delta for its prolonged outage; Las Vegas hotel raids the rooms of DEFCON attendees; DPRK hackers shift to construction firms.

This newsletter is brought to you by Material Security, the company that secures the cloud office with unified email security, user behavior analytics, and data loss prevention for Microsoft 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A ransomware attack has hit the IT systems of the French national museum network, crippling financial systems at over 40 museums, including two that were repurposed to host two Olympic events.
The attack hit over the weekend and took down an IT system that was aggregating financial data from Réunion des Musées Nationaux (RMN), an organization under the French Ministry of Culture that manages museums around Paris, including the Louvre.
The incident also impacted Grand Palais and the Château de Versailles, two museums hosting events for the Paris 2024 Olympics.
The attack hit Grand Palais a day after the Fencing events had been completed at the facility and a day before Taekwondo events are scheduled to start on August 7
It hit the Château de Versailles during the Equestrian competition and before the Pentathlon event was scheduled to start.
Olympic events are scheduled to go forward as planned—because the attack appears to have only impacted boutiques located at RMN member museums and about nothing else.
French officials say they are investigating the attack but did not release any other details about the incident.
No ransomware gang has taken credit for the attack at the time of publication.
Breaches, hacks, and security incidents
Key Tromic ransomware attack: IT hardware manufacturer Key Tronic estimates that it will lose around $17 million following a ransomware incident that took place in May. The company says it lost $2.3 million in expenses related to the attack and recovery and around $15 million in lost revenue. The company is known for its mice and keyboards, but has recently become one of the largest PCBA assemblers on the US market. The Black Basta ransomware gang took credit for the Key Tronic attack.
Cyberattack takes down 911 service: A cyberattack has taken down 911 emergency services across central Texas on Sunday. Emergency calls were rerouted through adjacent call centers while the issue was resolved. Officials say the issue was caused by an intentional denial of service that overloaded phone 911 lines. [Additional coverage in KVUE]
Mobile Guardian data wipe: A threat actor has gained access to the Mobile Guardian device management platform and wiped some of the company's devices. The platform is used by schools and universities to manage iOS and ChromeOS devices issued to students and school staff. Mobile Guardian confirmed the incident and shut down its platform once it detected the hack. The size of the incident is unknown, but the Singapore government says 13,000 devices were wiped in Singapore alone. [Additional coverage in TechCrunch]
Ronin Bridge white-hat incident: The Ronin Bridge cryptocurrency platform has paused and then restarted operations after it lost and then recovered $12 million worth of assets. Ronin says the transactions were the work of a white-hat research group, which identified an issue in its platform. The platform says it plans to award the white-hats a $500,000 reward for their work. [Additional coverage in CoinDesk]
CrowdStrike outage RCA: CrowdStrike has published the most complete (so far) root cause analysis [PDF] of its recent kernel driver outage.
General tech and privacy
Second Microsoft security memo: Microsoft has sent out a second internal memo to its employees, urging them to prioritize security features in its products. It sent a first memo in May this year. The first one was authored by CEO Satya Nadella while the second was from Microsoft HR boss Kathleen Hogan.
CrowdStrike and Microsoft say Delta ignored its help: CrowdStrike and Microsoft say that Delta ignored their offer for technical assistance during a recent IT outage that caused the airline to ground thousands of flights across the globe. The two companies have responded to Delta's legal team after the airline threatened to sue both. Delta is hoping to recover $500 million in lost revenue following the IT outage. But the legal teams of both companies say that Delta ignored messages providing help from both CrowdStrike CEO George Kurtz and Microsoft CEO Satya Nadella. Both CrowdStrike and Microsoft say that Delta's prolonged outage is the company's fault and that other airlines recovered faster than Delta after accepting their help. According to a leaked letter sent by the CrowdStrike legal team, the security firm has asked Delta to stop misleading the public about what happened. Microsoft's legal team also claims that Delta has failed to modernize its IT system and that the system that was preventing the airline from recovering faster was an IBM service. [Additional coverage in CNBC and CNBC]
Airlines are running out of flight numbers: And since we're on the topic of US airlines, some companies like American Airlines, Delta, and United are close to running out of flight numbers.
CoD BO6 leaks: Activision's upcoming Call of Duty game title, Black Ops 6 Gulf War, was leaked online—or at least an alpha version of the game. The leak comes before the game's anticipated public beta at the end of August.
Sentry changes licensing model: Functional Software has changed Sentry's licensing model to Fair Source.
Google retires the Chromecast: Google has formally retired the Chromecast, the company's streaming device. The company says devices will be available for sale until supplies run out this year. The Chromecast launched in 2013 and has sold more than 100 million devices.
Google found to be a monopoly: A US judge has ruled that Google has acted like a monopoly in order to maintain a dominant position in the search and search advertising market. The judge has ruled in favor of the US Department of Justice in a lawsuit the agency filed last year. The judge did not agree with the DOJ that Google has a monopoly in the general online advertising market. The DOJ has two other monopoly cases open against Apple and Meta. [Additional coverage in The Verge]
Firefox 129: Mozilla has released Firefox 129. New features and security fixes are included. The biggest feature change in this release include improvements to the Reader Mode UI, which now supports new text and font layout options, along with new themes. In addition, HTTPS is now the default protocol instead of HTTP for sites typed in the address bar—except for localhost and other local on-device URLs.
Government, politics, and policy
US preparing to ban Chinese software in smart cars: The US government is preparing to ban the use of Chinese software in autonomous and connected vehicles sold in the US. The decision is expected to be made public in the coming weeks, according to Reuters. The ban will also prohibit Chinese companies from testing autonomous vehicles on US roads.
Ransomware as terrorism bill: The chairman of the US Senate Intelligence Committee is sponsoring a bill that would elevate ransomware attacks to the level of terrorist threats. Sponsored by Senator Mark Warner (D-VA), the bill seeks to grant intelligence agencies more legal authority to intervene and go after ransomware gangs. The bill would also make it easier for the US to sanction countries that harbor ransomware gangs. [Additional coverage in CyberScoop]
New cybersecurity scholarship: The White House announced this week that EC-Council, a cybersecurity technical certification body, has pledged $15 million in scholarships for cybersecurity programs at educational institutions across the US. The pledge is meant to cover costs for roughly 50,000 students. The EC-Council has already certified more than 350,000 people since its launch in 2001. [Additional coverage in The Record]
Walz cyber record: CyberScoop has published a profile on Gov. Tim Walz, Harris' VP pick, record on cyber regulation—which looks to be promising and above the average for most US state legislation efforts.
Australia appoints new cyber security minister: The Australian government has named Tony Burke as the country's new Minister for Home Affairs and for Cybersecurity. Burke replaces Claire O'Neil, who has been appointed as the new Minister for Housing and Minister for Homelessness. As part of the cabinet reshuffle, Andrew Charlton was also appointed as Special Envoy for Cyber Security and Digital Resilience. [Additional coverage in CSO Online] [h/t CyberKnow]
Australia and US sign disinformation pacts: The Australian and US governments have signed a Memorandum of Understanding on combating state-backed disinformation campaigns. Australia is the 20th nation to sign such an agreement with the US. [Additional coverage in Cyber Daily]
Ireland's National Cyber Emergency Plan: Ireland's cybersecurity agency has published the country's first National Cyber Emergency Plan [PDF]. The IE NCSC says it created the plan with lessons learned from the 2021 ransomware attack on the country's national health service, and from engagements with the public and private sector during cyberattacks in 2022 and 2023.
EU forces TikTok to drop rewards program: The EU has ordered TikTok to drop its TikTok Lite user rewards program for breaking the EU's new Digital Services Act.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Rajan Kapoor, VP of Customer Experience at Material Security, on how threat actors view email inboxes as the targets of their attacks and not just an entry point into organizations.

Cybercrime and threat intel
Chinese scam gang arrested: US authorities have arrested four Chinese nationals for defrauding seniors through tech support scams. The group allegedly used popup ads, email spam, and phone calls to get victims to contact scam call centers in India. The gang allegedly made and laundered more than $27 million from at least 2,000 victims. A fifth suspect is still at large.
Email scam funds recovery: Interpol and Singaporean authorities have recovered $41 million stolen by a BEC gang from a commodity firm based in Singapore. The firm reported the theft after scammers posed as one of its suppliers and requested the payment of $42.3 million last month, on July 19. Interpol says it recovered the vast majority of the funds within a week of the incident after they seized bank accounts linked to the fake supplier. Another $2 million was recovered two days later after Timor Leste police detained seven suspects believed to be behind the scam.
Malware technical reports
Malicious browser extensions: ReasonLabs has discovered a network of websites peddling free software downloads that install malicious browser extensions on victims' computers. The apps targeted users looking for Windows utilities, video players, and gaming utilities. The malicious extensions contained malicious code that could hijack search results, show unwanted ads, and steal personal data from a user's browser. ReasonLabs says the extensions were hosted on the official Google Chrome and Microsoft Edge extension stores and appear to have been downloaded and installed by over 300,000 users. Some have been removed from the Chrome and Edge stores after being reported.
Chameleon: Mobile security firm ThreatFabric has spotted a collection of CRM mobile apps that infect users with the Chameleon Android RAT.
AMOS: Moonlock researchers have spotted a new malvertising campaign using ads for a fake Loom screen recorder to infect macOS users with the AMOS infostealer.
SharpRhino RAT: Quorum Cyber has discovered a new remote access trojan named SharpRhino that has been used in attacks by the Hunters International ransomware gang.
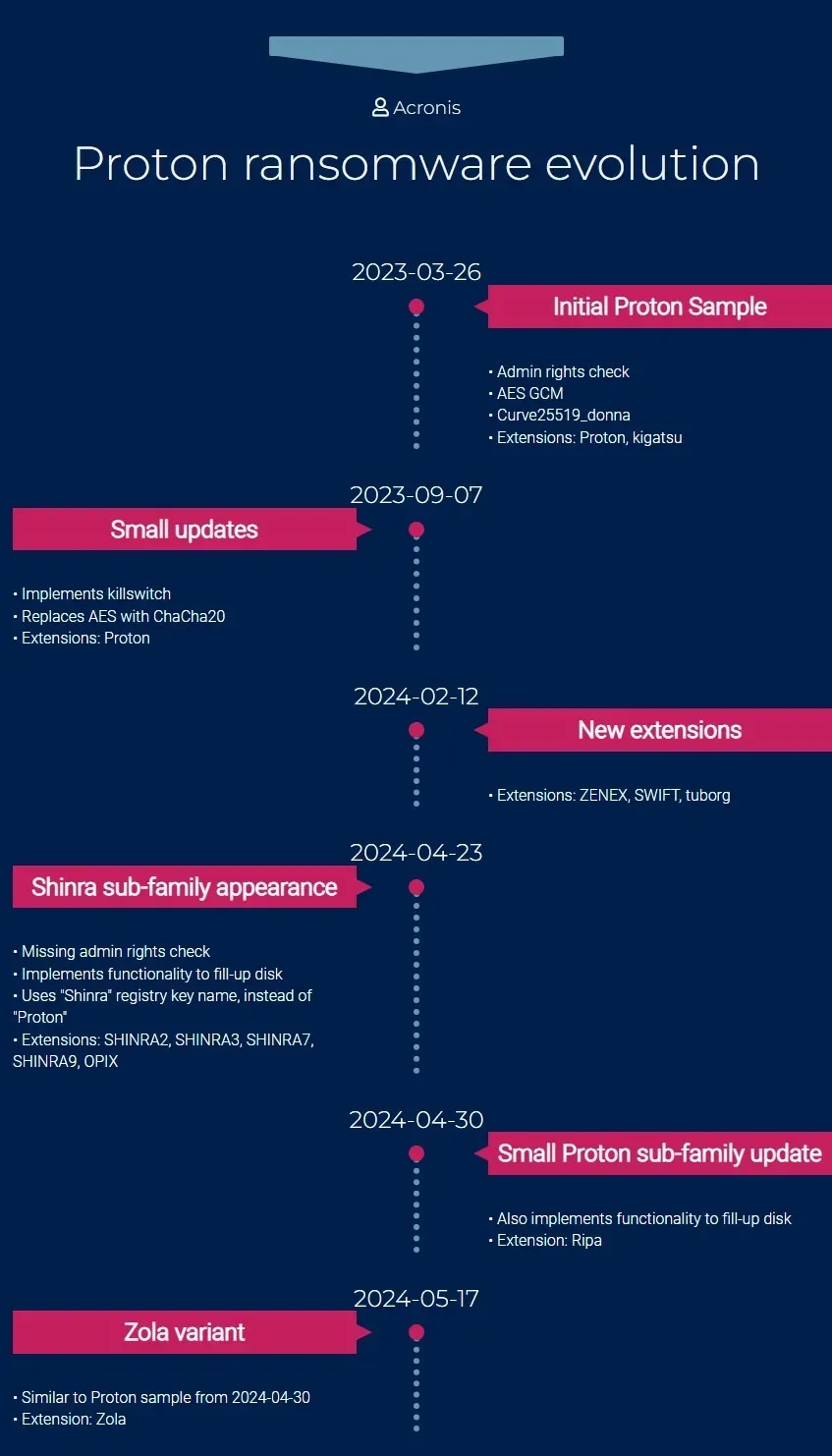
Zola ransomware: The Acronis security team has discovered a new ransomware strain being delivered in campaigns in the wild. Named Zola, the ransomware was first spotted in May and appears to be a rebrand of the older Proton ransomware from last year. The ransomware doesn't have any known decryption flaws or free ways to recover data—for now.
Sponsor Section
New attacks are harder to spot at greater volumes than your security team can handle. The legacy and so-called modern email security market has left you with two extreme options – write and maintain your own set of detection rules or trust a black box with no way to customize. Either route is a burden on security teams when testing and tuning rules or building and implementing response workflows. Watch a demo to see the Material difference for inbound email detection. Leverage the combined power of AI, behavioral analysis, custom detections, and collective intelligence to thwart new flavors of email attacks with precision and speed.
APTs, cyber-espionage, and info-ops
LianSpy: Kaspersky has discovered a stealthy cyber-espionage that targeted individuals in Russia with a previously unseen Android spyware named LianSpy. The attacks were discovered in March this year and the entire campaign was traced back to July 2021. Kaspersky says LianSpy can capture screencasts, exfiltrate user files, and harvest call logs and app lists. To avoid suspicious traffic, the malware uses local Russian cloud services for command and control servers. It's unclear if the malware is installed via physical access to targeted devices or through a vulnerability. Kaspersky says it identified ten LianSpy targets so far.
DPRK construction hacks: South Korea's cybersecurity agency says that North Korean hackers have stepped up attacks on South Korean companies involved in the construction and work machinery sectors. The new targeting strategy comes after North Korean leader Kim Jong-un announced a new national industrial strategy in January this year. The new direction mandates that North Korean government agencies construct or modernize 20 factories every year for the next ten years. South Korea says it has seen groups like Andariel and Kimsuky change their targeting this year as a result.
Chinese disinfo op targets the Philippines: The Chinese government is promoting a deepfaked video of Philippine president Ferdinand Marcos Jr taking drugs before giving his yearly state-of-the-nation address last month. The video was initially shared by supporters of former president Duterte and then widely promoted by a large network of inauthentic accounts on Twitter and YouTube. Researchers at ASPI say the video comes as tensions are growing between China and the Philippines over control over Second Thomas Shoal, a submerged reef that both countries are claiming as their territory.
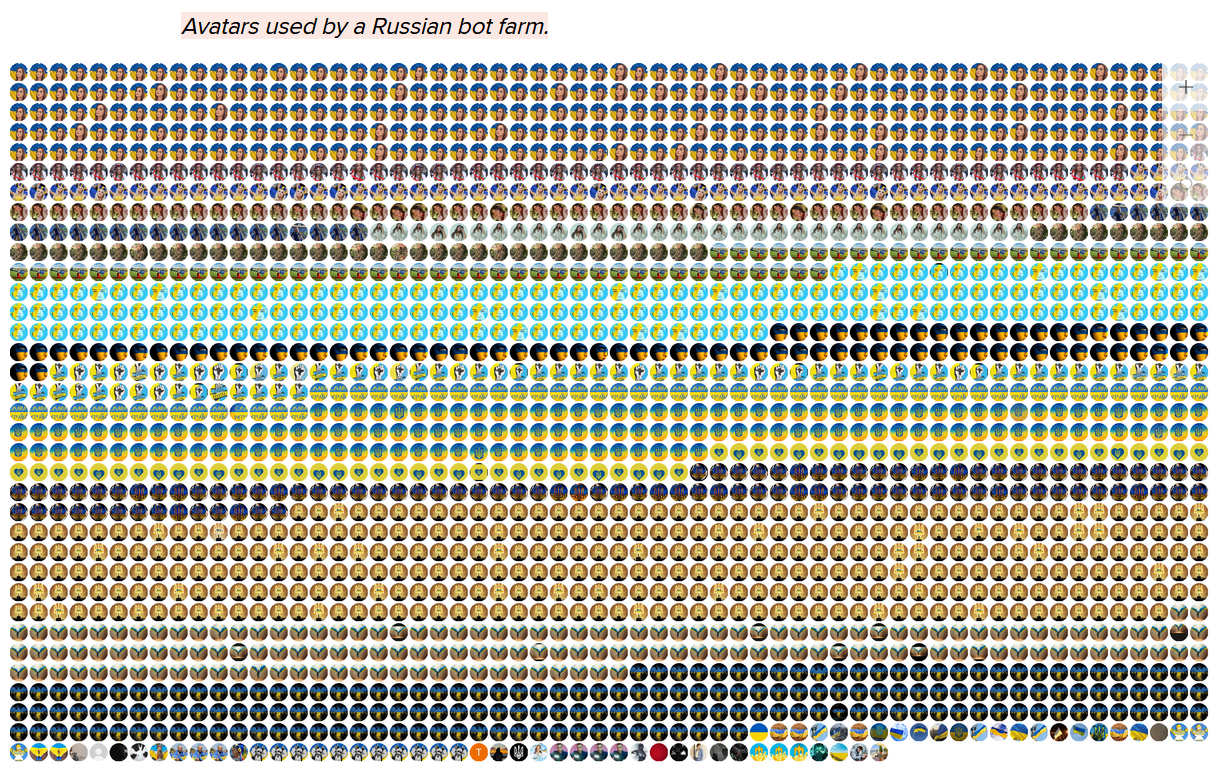
Russian TikTok disinfo campaign: A Ukrainian news outlet has linked more than 2,000 TikTok accounts to a Russian influence operation designed to sow fear and division around Ukraine's latest mobilization efforts. The accounts produced more than 41,000 posts in a week using the hashtag of #thisisnotmyukraine (#ценемояукраїна). The posts garnered over 10 million views before TikTok took down the profiles in July. The fake accounts shared identical profile pictures, descriptions, and videos in an attempt to flood the Ukrainian TikTok space with anti-mobilization content. Most of the accounts posed as Ukrainian patriots, brandishing the Ukrainian flag and patriotic catchphrases but discouraging the state's latest military efforts.
Vulnerabilities, security research, and bug bounty
OFBiz pre-auth RCE: SonicWall researcher Hasib Vhora has discovered a pre-authentication remote code execution vulnerability in the Apache OFBiz open-source ERP solution. The vulnerability (CVE-2024-38856) has received a severity rating of 9.8 out of 10 and is a variation of another OFBiz bug. The Apache project has released a patch at the end of last week. There are currently over 400 OFBiz instances connected to the internet.
Roundcube XSS: Sonarsource researchers have discovered two XSS vulnerabilities in the Roundcube open-source webmail client. The two vulnerabilities can allow an unauthenticated attacker to execute malicious JavaScript code inside a Roundcube inbox when a user views their emails. Attacks can be crafted to steal emails and contacts, as well as send emails from a victim's account. Roundcube is an extremely popular open-source webmail client and is widely used in the government sector across Europe. Russian and Belorussian APT groups have exploited Roundcube zero-days and vulnerabilities over the past two years in attacks targeting Ukraine and its allies.
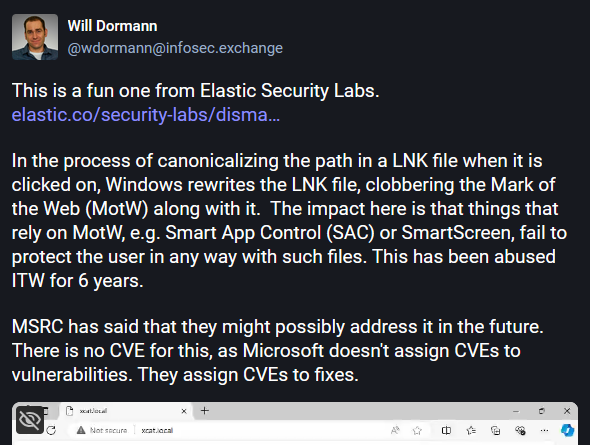
Windows zero-day still unpatched: Microsoft has yet to patch a zero-day vulnerability in the Windows operating system that has been exploited in the wild for at least six years. The zero-day was discovered by Elastic's security team. The issue occurs when Windows parses LNK files that have been placed on disk after being unzipped from an archive downloaded from the internet. Elastic says a Windows URL parsing bug removes the Mark-of-the-Web from the LNK file. This allows malicious LNK files to bypass Windows security features such as Smart App Control and SmartScreen.
Android Security Bulletin fixes zero-day: Android security updates for August 2024 are out. This month, the team has fixed 46 vulnerabilities, including one zero-day tracked as CVE-2024-36971. The Pixel security bulletin was late and wasn't up when we wrote this. It will go live at this URL.
JetBrains security updates: JetBrains has released security updates for the TeamCity on-premises server. [h/t ScreamingGoat]
Mailcow 2FA bypass: Security researcher Mayor Patrik has published a PoC for a Mailcow email server vulnerability (CVE-2024-41958) that can be used to bypass 2FA on 2FA-protected accounts. [h/t ScreamingGoat]
Dark Skippy attack: A security researcher has published details about Dark Skippy, a firmware attack that can recover the seed phrase of a hardware-based cryptocurrency wallet. The attack uses malicious code hidden inside transaction signatures to recover the wallet's seed phrase for all accounts. Dark Skippy is novel because it only needs two malicious signatures to execute, but it is hard to pull off because it also requires a device to be corrupted via malicious firmware.
Search-ms exploitation: Security researcher Stephan Berger has published research into ways of exploiting the search-ms URI protocol handler.
Microsoft bug bounty program: Microsoft has awarded $16,6 million to security researchers for bugs reported through its official bug bounty program. The funds went to 343 security researchers from 55 countries across the globe. The largest award was $200,000.

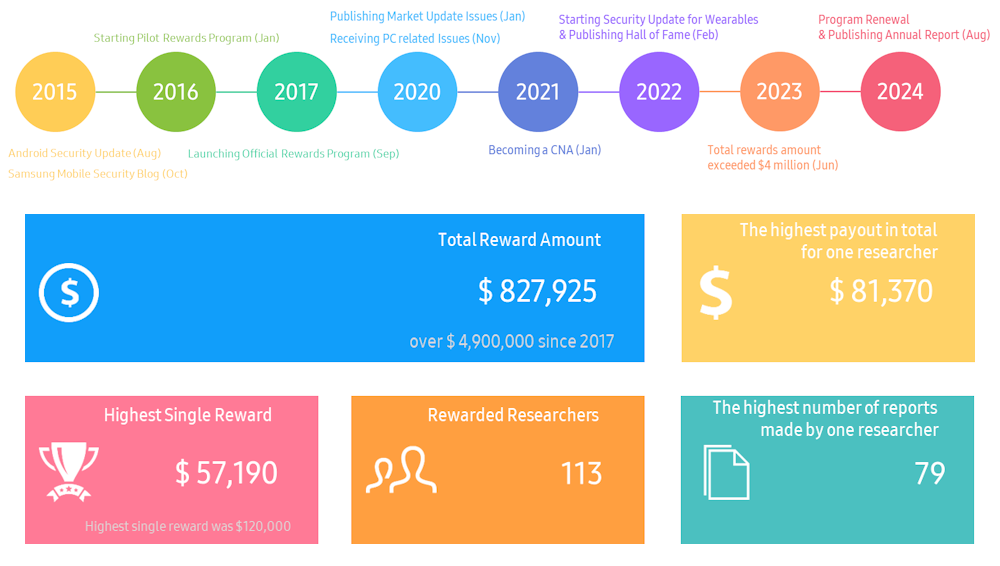
Samsung bug bounty payouts: South Korean phone maker Samsung says it paid almost $5 million to security researchers through its official bug bounty program since its inception in 2017. The company handed out over $827,000 in rewards just last year alone. The biggest single-report payout in 2023 was $57,000. Samsung says it plans to raise rewards this year for bugs with high-quality and detail-rich reports. The maximum payout has also been increased to $1 million for reports detailing remote code execution attacks on the Knox Vault security feature.
Infosec industry
Threat/trend reports: Cisco Duo, CrowdStrike, Forescout, Qualys, Rapid7, RiskIQ, Sophos, and VulnCheck have recently published reports covering infosec industry threats and trends.

Las Vegas room searches: The Resort World Las Vegas hotel has told guests that it plans to search all guest rooms while the DEFCON security conferences is taking place at its premises. Hotel management says the room searches are a result of the ransomware attacks that hit Caesar's and MGM Resorts in August of last year. Both hotels suffered major financial losses following the attacks. Both incidents were caused by intrusions from remote locations over the internet. [Additional coverage in 404 Media]

Vanguard Awards: ZDI has announced its own set of infosec awards to be given out during the Black Hat security conference.
New fake app Canarytoken: Thinkst has launched a new type of Canarytoken, a fake mobile app that you can make look like a dozen popular banks, mail apps, or password apps. This works by warning your org's security team whenever someone opens it—as a sign that someone has either got hold of your device or there's malware on the phone. Also works for non-corporate environments and use cases as well.
"Place the fake banking app on your home screen and let it sit there. Download it to your parent's or grandparent's phones and tell them to never touch it. If you ever get an alert, you know to contact them immediately."
New tool—LeakedWallpaper: Russian pen-tester Michael Zhmaylo has published LeakedWallpaper, a tool to leak of any user's NetNTLM hash. The tool exploits CVE-2024-38100, patched last month.
New tool—AppLockerGen: Splunk's Michael Haag has released a tool named AppLockerGen that can help system administrators and security professionals in creating and managing AppLocker policies. The code is also on GitHub.
BSidesLV 2024 videos: Live streams from the BSides Las Vegas 2024 security conference will be available on this YouTube page as they happen.
t2 2024 videos: Talks from the t2 2024 security conference, which took place in April, are now available on YouTube. This was the conference's last edition.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss recent changes in a Chinese APT's tactics and how cyber security agencies have responded.
In this podcast, Tom Uren and Patrick Gray discuss the Israeli government seizing documents from NSO Group so that they couldn't be shared with opposition counsel in a US lawsuit during discovery. It's a terrible look.
The Risky Business team has recently started publishing video versions of our podcasts. Below is the main weekly show, with Pat and Adam at the wheel!




