Risky Biz News: Microsoft ties security goals to exec compensation
In other news: EU countries condemn Russia over APT28 hacks; hacker-for-hire suspect detained in London; SiegedSec campaign targets far-right groups.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Microsoft has re-committed to prioritizing security, in a sign the company fears the reputational damage it stands to incur after a duo of facepalm-worthy hacks it suffered over the past year.
Back in November, Microsoft announced the Secure Future Initiative (SFI), a somewhat generic plan to overhaul the company's cloud security. The pinky promise to improve security came after a Chinese state-sponsored group hacked Microsoft in June and pivoted to US government networks.
A month later, in December, Microsoft revealed that days after its SFI announcement—by a stroke of irony—it also got hacked by Russian hackers, which then proceeded to steal data from its internal email server, including from executives and its security team (gasp!).
In April, a month ago, the DHS' Cyber Safety Review Board published a report on Microsoft's handling of the Storm-0558 (Chinese) hack from last June that basically concluded with the line: "Microsoft's security culture was inadequate and requires an overhaul."
Now, a month later, Microsoft seems to have been humbled by the CSRB report's conslusions and has come back to its Secure Future Initiative with more tangible and actionable details—instead of the eye-bleed-inducing block of PR-reviewed text from last year.
The company published a new blog post on Friday, and CEO Satya Nadella sent a memo to all employees—the full text courtesy of The Verge.
There are a few things to unpack from both, but we'll start with this quote from Nadella, which sets the stage for all employees on how to approach their work going forward.
"If you’re faced with the tradeoff between security and another priority, your answer is clear: Do security. In some cases, this will mean prioritizing security above other things we do, such as releasing new features or providing ongoing support for legacy systems."
The blog post goes deeper on the SFI and what it stands for by laying out three security principles and six security pillars to be prioritized by its engineering teams.
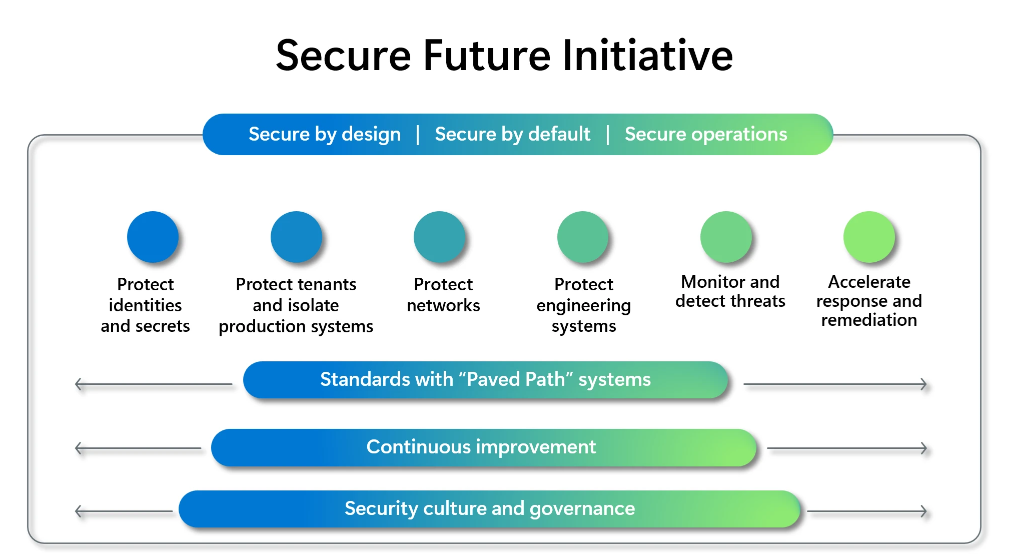
Some of them are really broad and will indoubtly require a lot of work from the low-level 10x engineers—as all of these efforts usually do.
But while we legitimately thought last November's SFI blog post was just your usual Microsoft PR disaster management plan, this time, we have the proverbial people's eyebrow raised up.
Both the blog post and the CEO memo reference that executives will have their bonuses and compensation tied to implementing SFI security goals in the company's products.
That's probably the best thing Microsoft skeptics like us could have read. Having Microsoft bosses crack the whip above employee heads on cybersecurity is probably the easiest way to get Microsoft to rewrite that trash pile called Exchange.
Microsoft also says it will prioritize security in its "hiring decisions"—which is also what you generally want to hear. Claiming you're prioritizing security but not hiring people with cybersecurity talent is not actually prioritizing security.
The new initiative clearly wants to mimic a similar pledge made by Bill Gates in 2002, back when he was still Microsoft CEO.
At a time when Microsoft products were getting exploited left and right, Gates put out the famous Trustworthy Computing memo, an initiative that led to significant changes to Microsoft's security posture and the creation of what we now know as Patch Tuesday.
This new pledge comes at the right time. You could see the public opinion changing on Microsoft as days went by. More and more industry and government figures were seeing through Microsoft's shtick of selling cheap unsecured products and then bundling security features in some of its most expensive tiers. A scam can only last for so much.
Building back good graces won't be easy, but realigning corporate governence and engineering teams on a simple "Do security" slogan is a good place to start from.
Breaches, hacks, and security incidents
Another Webex leak in Germany: The German Armed Forces (Bundeswehr) have misconfigured their Cisco Webex systems and leaked information on past and future meetings. Reporters from German newspaper Die Zeit found links to thousands of meetings on sensitive topics exposed on the internet. Meeting titles referenced sensitive and secret topics, such as Taurus missiles and battle tactics. The German government is also affected by the same issue with their Cisco Webex video conferencing software. Reporters say they easily found video conferences scheduled for Prime Minister Olaf Scholz and other ministers.
SiegedSec far-right hacking spree: A hacking group has breached and leaked data from several far-right and transphobic organizations over the past month. The SiegedSec group has taken credit for hacks at the River Valley Church, the Westboro Baptist Church, and far-right news sites Real America's Voice, the Post Millennial, and Human Events. The hacks are part of what the group calls Operation Trans Rights 2. SiegedSec hopes the leaked data will help expose the real-world identity of far-right and transphobic individuals.
DataBreaches.net profile: Scandinavian researchers have published an academic paper on the DataBreaches.net portal and its coverage of security breaches.
Salamander incident: German show store Salamander has been offline for almost two weeks in the aftermath of a cyberattack.
Wichita ransomware attack: The city of Wichita, Kansas says it shut down IT systems to prevent the spread of a ransomware attack. The incident took place over the weekend, on May 5. According to Emsisoft researcher Brett Callow, Wichita is the 36th state and local US government to have suffered a ransomware attack this year. Wichita is the 50th largest city in the US.
Tatarstan cyberattacks: Ukraine's military hackers claim to have carried out a large-scale cyberattack against Russia's Tatarstan region. The operation targeted the Alabuga Special Economic Zone, where Russia makes some of its attack drones. DDoS attacks hit the region's main ISP and allegedly cut off internet access to Tatarstan's capital of Kazan, Russia's fifth-largest city. The attack was carried out by Ukraine's Defence Intelligence Main Directorate (GUR), which previously hit multiple Russian organizations with data wipers. It's unclear if GUR managed to wipe any IT systems in Tatarstan. The Ukrainian military previously struck Russian drone factories in the same region last month. [Additional coverage in NV]
General tech and privacy
Microsoft bans LEA from using AI for facial recognition: Microsoft has banned law enforcement agencies from using its enterprise AI tool for facial recognition. The company updated the Azure OpenAI Service terms of conduct last week to specifically ban these scenarios. Microsoft launched the Azure OpenAI Service in February as a wrapper around OpenAI's technology. [Additional coverage in TechCrunch]
reCAPTCHA bug: Google has rolled out a fix for its reCAPTCHA service that prevented Firefox users from completing challenges.
Chrome Rust kernel: The Google Chrome team is experimenting with building a memory-safe browser kernel in Rust.
Government, politics, and policy
New US international cyberspace strategy: The Biden administration will unveil a new US international cyberspace strategy this week at the RSA security conference in San Francisco. The document will be unveiled by Secretary of State Anthony Blinken and will include mentions of 5G security and foreign influence operations. The new strategy will replace a 13-year-old document from the first Obama administration. [Additional coverage in NextGov]
NASA cybersecurity assessment: A GAO report concludes that NASA needs to improve the cybersecurity posture of all its aircraft, not just the new systems it builds. [Additional coverage in FedScoop]
Outcry over APT28 hacks: The German [PDF] and Czech governments, the European Union, and NATO have condemned Russia for a major hacking spree linked to the APT28 group. Officials say the group used a Microsoft Outlook zero-day to compromise email accounts throughout 2023. The campaign targeted governmental entities, critical infrastructure operators, and political parties across the EU. Most of the victims were located in Germany, Czechia, and Ukraine. Germany has summoned a top Russian envoy to answer for the hacks and called on Russia to "refrain from such behavior"—like that will work. The government of Poland and the UK also issued their own statements on the incidents. Russian officials called the statements "unsubstantiated and unfounded" and designed to incite "anti-Russian sentiments in Germany." [Additional coverage in DW]
Big UK government solutions for big problems: A local UK government has banned the use of apostrophes in city street names to avoid problems with their computer systems. Now, that's the best SQL injection protection I've ever heard of. </s>
New EU cyber rules for electricity providers: The European Union is about to pass new cybersecurity regulations for electricity providers. Under the new rules, providers will have to undergo cybersecurity risk assessments every three years, will have to disclose security incidents, and implement various safeguards. EU officials are adopting the new rules to prevent hacks from causing widespread blackouts. According to the Wall Street Journal, the new rules are inspired by the Ukrainian conflict and are expected to pass this week.
EU PQC transition: The European Union has published guidance on helping states transition to post-quantum cryptography.
NATO Locked Shields 2024: NATO's annual cyber-defense exercise concluded last week in Tallinn, Estonia. More than 4,000 cybersecurity from 50 countries participated in this year's Locked Shields exercise. Teams cooperated to defend the infrastructure of a fictional country against a simulated cyberattack. Teams defended attacks against critical sector infrastructure, 5G networks, and the use of AI technologies. A team from Ukraine participated in this year's edition for the first time.

Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Marco Slaveiro, Thinkst’s CTO about staying current with modern attack trends and not falling for the trap of optimising to catch red teams.

Cybercrime and threat intel
Hacker-for-hire detained: The UK has arrested an Israeli man for allegedly conducting a cyber-espionage campaign on behalf of an American PR firm. Amit Forlit was arrested at Heathrow Airport last week while trying to board a flight to Israel. He was detained on an international arrest warrant issued by the US. American authorities are currently trying to secure his extradition. [Additional coverage in Reuters]
Operation PANDORA: Europol and authorities in six countries have raided 12 call centers linked to internet scams and fraud. Officials say the call centers were involved in romance scams, investment scams, and fake police emergency calls that aimed to defraud victims. Europol estimated victim damages at around €10 million. Authorities have identified 39 suspects linked to the operation and managed to arrest 21.
BTC-e boss pleads guilty: A Russian national has pleaded guilty to money laundering charges for his role in operating the BTC-e cryptocurrency exchange. Alexander Vinnik, 44, was arrested in Greece after the FBI seized the BTC-e platform in July 2017. Officials say Vinnik's platform laundered over $100 million in cybercrime profits, including from ransomware attacks. Vinnik was sent to the US in 2022 following a years-long extradition battle with France and Russia.
News of the World hacks: A Prospect article argues that News of the World, a newspaper owned by Rupert Murdoch, didn't just hack the phones of celebrities and politicians to get scoops but also stole data to help its owner's business empire commercial endeavors.
LockBitSupp dox threat: Law enforcement officials have reactivated the old LockBit dark web portals to tease an upcoming dox of the LockBit ransomware gang leader. The individual is known online as LockBitSupp and officials say they plan to reveal his real identity this week on Tuesday. The FBI and Europol took down the LockBit gang's operation in February this year. The US State Department has offered a $10 million reward for any information on the gang's leader.
Gootloader campaign: Field Effect has published details on a new Gootloader campaign.
FIN7 campaign: Security researcher Rewscel has published a look at a recent FIN7 mal-SEO campaign delivering the NetSupport RAT.
Android banker warning: Finnish authorities have warned about a new Android banking trojan targeting Finnish mobile banking users.
New npm malware: Ten malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Armis, Bitsight, Kaspersky [RU PDF], VulnCheck, and the World Economic Forum have recently published reports covering infosec industry threats and trends.
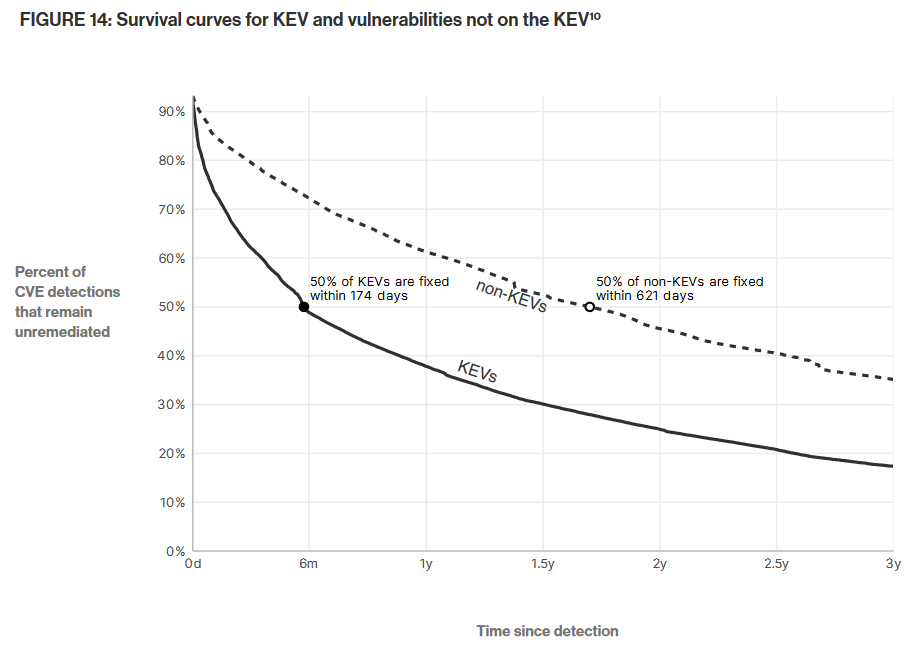
Organizations patch vulnerabilities listed in the CISA KEV database 3.5 times faster than other vulnerabilities. According to security firm Bitsight, KEV-listed bugs get patched in 174 days on average, while non-KEV bugs get patched after 621 days. CISA also noted the same improvement last year, although with different stats. CISA says vulnerabilities listed in KEV get fixed nine days faster compared to bugs that are not listed in KEV.
Malware technical reports
Mal.Metrica: Sucuri researchers have identified a new ongoing campaign linked to the Mal.Metrica website redirection group that sends unsuspecting internet users to various online investment scams. Most of this campaign operates via malicious JavaScript code planted on hacked WordPress sites.
New Android click fraud trojan: Security firm Dr.Web has found a new Android trojan distributed via apps on the official Google Play Store. The trojan works by secretly opening browser windows to load and click on ads to generate revenue for its creators. It can also launch DDoS attacks and subscribe victims to premium services. Dr.Web says it found the malware inside physical activity tracking app and apps to control adult toys. According to Play Store data, the apps were downloaded and installed more than 1.5 million times. An earlier version of the same trojan was also spotted on low-end Android-based TV set-top boxes.
Sponsor Section
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary.
We will be in SF for #RSAC next week. Pop by¹ for a demo, to grab a t-shirt, to see Canary in action, or just to talk detection that works.
— Thinkst Canary (@ThinkstCanary) April 29, 2024
It’s totally geeky, but we can’t wait 💪💚
__
¹ North Hall 6445
APTs, cyber-espionage, and info-ops
New Pakistani APT malware: CyFirma has discovered a new Android RAT delivered to Indian defense personnel using WhatsApp lure messages. The company has linked the malware with medium confidence to a Pakistani APT.
Sandworm's Kapeka: ThreatMon has published a report on Kapeka, Sandworm's new backdoor used in recent spear-phishing operations across Europe. Similar reports on the same malware are available from LogPoint and WithSecure.
HideBear: QiAnXin researchers have published more details about an APT group it tracks as HideBear (aka Storm-0978, aka RomCom). The new report focuses on a new kernel injection technique the group has used in recent operations, which researchers named "Step Bear."
"This injection technique utilizes a combination of 'Heaven's Gate' and 'Hell's Gate' invocation methods to initiate certain uncommon kernel functions, enabling it to bypass mainstream EDR detections."
Vulnerabilities, security research, and bug bounty
Android DNS leak: VPN service Mullvad has identified a bug in Android where the OS leaks DNS queries even when the VPN tunneling feature is enabled. The company says it reported the issue to Google, but no fix has yet been scheduled.
Microsoft PlayReady vulnerabilities: Polish security researcher Adam Gowdiak has disclosed vulnerabilities in the Microsoft PlayReady DRM. The vulnerabilities can allow malicious subscribers to bypass the DRM and download movies from streaming services. The bugs allow the retrieval of plaintext content encryption keys from the PlayReady component. [Additional coverage in SecurityWeek]
Jitsi Meet vulnerabilities: ERNW has found a vulnerability (CVE-2024-33530) in the Jitsi Meet open-source video conferencing software. The vulnerability exposes the passwords of private password-protected meetings. Jitsi released fixes at the end of April, a month after receiving the bug report. The Jitsi Meet software is incorporated in products from Comcast, Symphony, Rocket.Chat, and 8x8.
Tinyproxy vulnerabilities: Cisco Talos has disclosed a major vulnerability in the Tinyproxy server. The vulnerability (CVE-2023-49606) can allow threat actors to hijack proxy servers using simple HTTP requests. Exploitation is expected to take place after proof of concept code was published online last week. Security firm Censys says it found more than 90,000 Tinyproxy servers exposed online, of which 51,000 appear to be unpatched and vulnerable to attacks. The Tinyproxy server is widely popular with IoT device makers and is widely deployed in South Korea, Europe, and the US. A patch is not available. In a GitHub post, the project's admins say Talos researchers failed to disclose the issue through the proper channels.
Microsoft IPP abuse: Security firm Diverto has published research on how threat actors could abuse the Microsoft Internet Printing Protocol for malware C2 communications.
New AMSI bypass technique: OffSec Technical Trainer Victor "Vixx" Khoury has published details on a new method to bypass Microsoft's Anti-Malware Scan Interface (AMSI). The new technique abuses an AMSI DLL (System.Management.Automation.dll) that Microsoft forgot to mark as "read-only." Proof-of-concept code is also available.
NVIDIA security updates: NVIDIA has released two security updates to deal with vulnerabilities in its ChatRTX and Triton Inference Server software.
JetBrains security updates: JetBrains has published security updates for its TeamCity servers.
Security of Chinese government sites: A team of Chinese academics have published research looking at the cybersecurity of Chinese government systems and public websites. One of the paper's main findings found that almost 40% of government sites use an old jQuery version known to contain vulnerabilities. Another one is that the Chinese government is just as bad at DNSSEC as everyone else.
Infosec industry
Acquisition news: Something we missed from last month, Armis has acquired Sil Security.
SteelCon 2023 videos: Talks from the SteelCon 2023 security conference, which took place last July, are now available on YouTube.
OSFC 2023 videos: Talks from the Open-Source Firmware Conference 2023, which took place last October, are available on the conference's website.
c0c0n 2023 videos: Talks from the c0c0n 2023 security conference, which took place last October, are available on this YouTube channel.
LASCON 2023 videos: Talks from OWASP's LASCON 2023 security conference, which took place last October, are available on YouTube.
m0leCon 2023: Talks from the m0leCon 2023 security conference, which took place last December, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the life cycle of zero-days, dissect the conventional wisdom, and talk about how zero-days are never truly "burnt."




