Risky Biz News: Pro-Kremlin disinfo cluster disrupted ahead of Moldova's election
In other news: Firefox zero-day targeted Tor Browser users; hacked vacuums spew out slurs; hackers leak data from Pokemon gaming studio.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Meta has taken down a network of fake accounts engaged in a disinformation campaign targeting Moldova a week before the small Eastern European country is set to hold presidential elections and a referendum to join the EU.
The network used fake accounts to manage pages that posed as "independent" news entities.
They posted content primarily in Russian that criticized the country's current president Maia Sandu, Moldova's pro-EU politicians, and the country's ever-increasing closer ties to neighboring Romania.
Naturally, the accounts posted positive and supportive comments about Moldova's pro-Russia parties and about Ilan Shor, a Moldavan businessman who fled the country after he was charged in a massive bank fraud case. Shor is Moscow's favorite "nationalist" in Moldova, and his party has often received backing from the Kremlin.
The accounts would often take snippets from legitimate Moldavian news outlet Point.md but modify the text to add pro-Russia and anti-EU slants.
Meta says the network was part of a larger disinformation network cluster that had a presence on other social networks, such as Telegram, OK (Odnoklassniki), and TikTok.
The Facebook and Instagram accounts would often attempt to drive their audiences to the other platforms. They also offered money, food, or concert tickets for new followers and for people to post graffiti their brands across Moldova.
Meta says the accounts were primarily managed from Transnistria, a region of Moldova occupied by the Russian Army since 1991.
Some of the individuals involved in the campaign are also behind a fake engagement service that offers fake likes and followers on social media platforms such as Facebook, Instagram, YouTube, OK, VKontakte, X, and the petition platform Change.org.
In total, Meta suspended seven Facebook accounts, 23 Pages, one Group, and 20 Instagram accounts.
The company says it uncovered and disrupted the network based on its own research, but last Friday's takedown comes three days after the Moldovan government also moved on Russia's disinformation efforts elsewhere.
Last Tuesday, the Chisinau government ordered Telegram to take down 15 channels and 95 chatbots associated with Ilan Shor and other pro-Kremlin politicians.
On Tuesday, Moldovan authorities ordered Telegram to take down another nine channels that the Shor party created to replace the old ones.
Officials from Moldova's National Investigations Inspectorate said the accounts broke local election laws. Specifically, the accounts were used to bribe locals for their votes and to funnel money into Shor's and other pro-Kremlin parties.
Moldovan officials moved to suspend the channels days after the Ziarul de Garda newspaper published an undercover investigation exposing how the Shor Party (the party founded by Ilan's Shor) and some of the newer pro-Kremlin parties were using the Telegram channels to recruit locals for anti-government protests. Locals had to register using one of the Telegram chatbots to keep track of who attended and who brought in new "members." The chatbots were also used to create bank accounts in Russia where participants would receive money for attending protests and for their future votes. Some of the individuals who registered on these chatbots have since complained that their data was used to contract loans in their names.
Ever since Russia's invasion of Ukraine, Moldova's pro-European government has accused the Kremlin of waging a "hybrid warfare" against it, with Ilan Shor being at the center of most of these actions.
While Shor fled Moldova after he was charged and has since received Russian citizenship, the eponymous Shor party he founded in Moldova has remained behind and continued to be used by the Kremlin in attempts to destabilize the country.
Shor party representatives organized multiple anti-government protests in Moldova's capital, Chisinau, in 2023. They paid locals to attend and used agitators in an attempt to turn the protests violent. According to the US State Department, the party had help from Russian news agency RT, which had slowly turned into an arm of Russian foreign intelligence over the past years.
This and previous shenanigans eventually got the Shor party outlawed in Moldova and seven individuals sentenced to prison for their role in stoking the violence. In the meantime, Shor and his allies have moved those protests from Moldavian cities to Moldovan embassies across the EU.
The Russian government was not dissuaded by the Shor ban and continued to put pressure on the government through new nAtIoNaLisT parties that continued to spew the Kremlin's usual conspiracy theories that the EU was gonna make everyone a slave and turn their children gay. These groups are currently issuing veiled threats that Russia would bomb and destroy Moldova if they didn't vote for "peaceful" Kremlin candidates.
As of last month, the Moldovian government has accused Russia of funneling more than $15 million into the country to bribe voters and vote against the country's EU bid. More than 130,000 are believed to have received some sort of bribe.
Some of this money was promised to Moldavians through the Telegram bots that opened bank accounts in Russia, but some were sent in physical form. Moldovan authorities previously reported about groups of people who were making regular trips to Moscow via Armenia. These money mules returned with stashes of payment cards issued by UAE banks and with piles of cash, just short of the mandatory cash reporting requirement at airports. Officials believed the cards and cash were handed to local politicians and election officials to buy their favors, which eventually forced the government to block Russian payment systems and UAE cards inside Moldova.
Moldovan authorities have also recently charged local priests who started pushing their communities to support Kremlin candidates after taking trips to Russia.
The pro-EU side was also the target of a manufactured hack-and-leak operation named Moldova Leaks where Russian hackers leaked modified Telegram chats from one of the president's security advisors to imply the contest for an anticorruption prosecutor post was rigged.
The Chisinau government was one of the first to block access to Russian TV channels, radio stations, and news sites since Russia's invasion of Ukraine. This included Russian-based organizations but also many local Moldovian proxies that just regurgitated the Kremlin's propaganda. This ban list has been kept up to date, with four new Russian sites being added to it two weeks ago (RuTube, Yandex, and the Dzen and Moldova24 news agencies.).
Over the past two years, Chisinau officials said on several occasions that they denied entry into the country to multiple military-trained personnel who were supposed to help local pro-Kremlin parties seize power in coups. One of them was allegedly supposed to take place using Prigozhin's Wagner forces, according to Moldovan President Sandu.
Unlike Georgia, where the pro-EU side lost power to the pro-Kremlin party, Moldova has managed to keep its government and pro-EU view intact, mainly because it's landlocked between Ukraine and Romania and doesn't face a direct military threat from Russian forces.
Moldova also received help from Western governments faster than Georgia's pro-EU side. Both the US and the EU have sanctioned Ilan Shor early on in the Russian-Ukraine conflict. This put a dent in the pro-Kremlin side's ability to move large bribes through the regular banking system.
However, poll numbers suggest that the pro-Kremlin side's propaganda might have worked regardless, mainly due to the sheer size and continued effort of its operations. We'll find out in exactly a week if all of this worked and if Chisinau's efforts to keep its infant democracy alive have paid off.
Breaches, hacks, and security incidents
Iran reports cyberattacks on nuclear facilities: Iranian officials say that all three branches of their government—the judiciary, the legislature, and the executive branch—have been hit by cyberattacks following an escalation of tensions in the Middle East. Cyberattacks have also hit the country's nuclear facilities, fuel distribution networks, municipal systems, transportation networks, and ports. The Iranian government did not attribute the attacks. Officials previously issued a warning about potential cyberattacks hitting Iran at the end of September. [Additional coverage in News18]
Verizon breach: A threat actor claims to have breached US telecommunications giant Verizon and stolen customer call logs. According to 404 Media, the data originates from Verizon's push-to-talk products, typically used by large companies as internal communication systems. The stolen data is now being sold on a cybercrime forum for Russian-speaking users. Verizon is the second major US telco to have customer call records stolen after AT&T disclosed a similar breach in July.
UK Ambulance Services ransomware attack: The UK Ambulance Services has suffered a ransomware attack on one of its key suppliers. The attack was first reported by iNews, which seems to blow a mere ransomware attack out of proportion, making it look like some sort of Kremlin master plan to sabotage the UK.
Hacked Ecovacs vacuums spew out slurs: Hackers have taken over smart vacuums across the US to yell obscenities and racial slurs through their onboard speakers. The incidents took place last week across different US regions, suggesting a remote intrusion vector. According to the ABC, all the affected robots were Chinese-made Ecovacs Deebot X2s. The company said it will issue a security update to address the incidents in November.
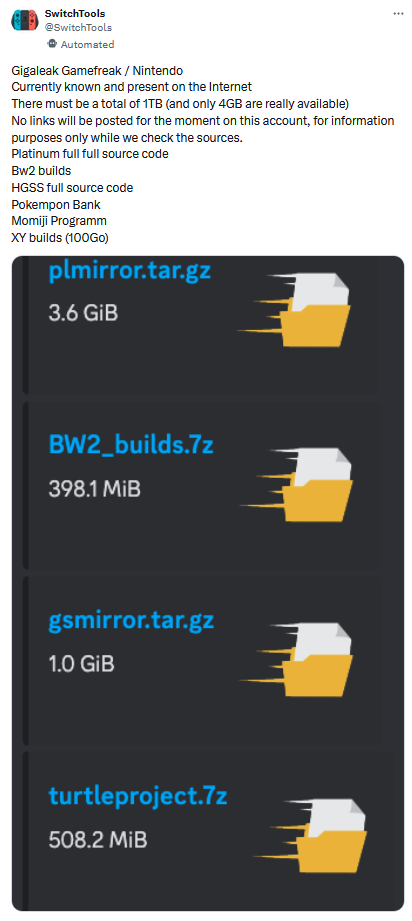
Game Freak hack: Hackers have breached and leaked over 1TB of data from Game Freak, the Japanese video game studio that develops Pokemon games. The leaked files contain source code for games and other tools, information on upcoming games, and unused designs. The personal data of studio employees is also allegedly included. The company confirmed the breach within hours after the data started circulating online. The Pokemon games are the third most successful franchise in gaming history after Mario and Tetris. [Additional coverage in Nintendo Everything]
General tech and privacy
More WordPress scumbaggery: Automattic and the WordPress.org team is being lambasted by the open-source community for effectively hijacking one of the most popular WordPress plugins on the market—which happens to be maintained by WP Engine, a commercial rival for Automattic's WordPress.com platform. This all stems from a decision Automattic made last week to block access to individuals associated with WP Engine to the WordPress.org platform. WP Engine devs were able to log in and manage a vulnerability report filed by WordPress.org itself. This gave the WordPress team the chance to use its Terms of Service and take ownership of the plugin in one of the scummiest FOSS moves in recent years. After taking over the Advanced Custom Fields plugin it renamed it ironically named it "Secure" Custom Fields and then went on Twitter to wish the WP Engine team good luck with their old version of the plugin. With this level of scumbaggery, you now know why over 150 Automattic employees left the company in recent weeks—after the company's CEO started abusing the WordPress.org open-source brand to bully his direct commercial competitors. In the meantime, other plugin devs are getting pi**ed with WordPress creator Matt Mullenweg. The latest one is Very Good Plugins, which filed a cease-and-desist letter with Automattic and asked the company to remove its WP Fusion plugin from the commercial WordPress.com plugin store on the grounds of trademark infringement—the same step Automattic used against WP Engine to stop using the WordPress brand.
Meta expands moderation panel: Social media company Meta is creating a European unit for its moderation panel, known as the Oversight Board. The new panel will handle moderation appeals for Meta platforms but also for other social media networks such as TikTok and YouTube. [Additional coverage in MSN]
Previously banned Twitter trolls now rule the platform: A NYT investigation found that Twitter accounts that were previously banned by the previous leadership are currently flourishing on the platform. They are often boosted by Musk and other right-wing accounts and are also at the center of a lot of misinformation on the platform.
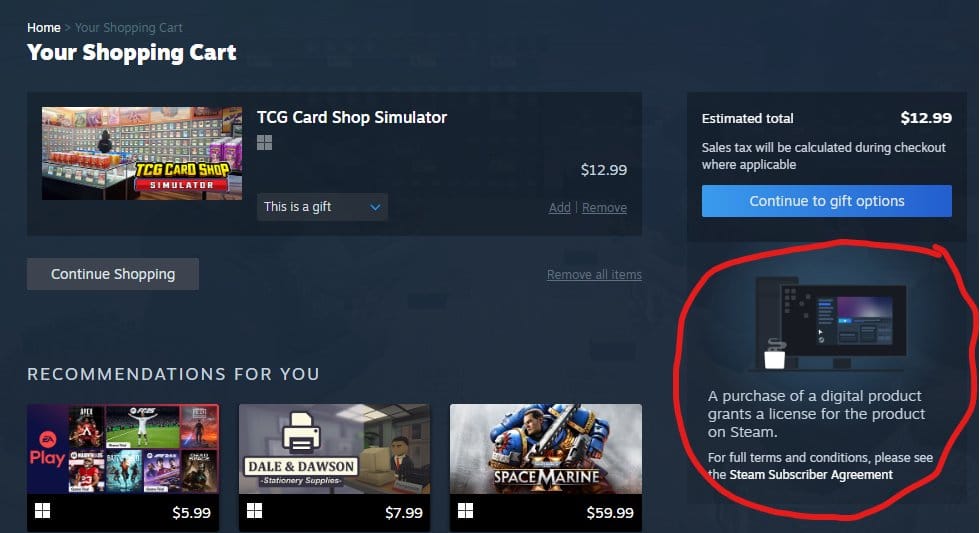
Steam clarifies you don't own your games: Gaming platform Steam has modified its interface to clearly point out users are buying a "license" to play the game and not ownership of their game copy. The new lingo was added after several gaming studios shut down servers for their older games due to rising cloud infrastructure costs.
Government, politics, and policy
Sri Lanka asks Thailand for help: Sri Lanka's prime minister has requested the Thai government's help to rescue Sri Lankans still detained in Myanmar cyber scam compounds. Officials believe the Sri Lankans are being forced to work in scam call centers based in Myanmar's Myawaddy region, next to the Thai border. The Thai government previously helped rescue 28 Sri Lankans, but officials say 40 more are still being held captive in Myanmar compounds. A UN report published last week estimated that cybercrime groups made between $18 billion and $37 billion from online scams in 2023 alone. [Additional coverage in Newswire.lk]
Bahrain spyware lawsuit update: A London appeals court has ruled that Bahrain can't claim "state immunity" and must stand trial in a lawsuit filed by two dissidents over the government's use of spyware. Saeed Shehabi and Moosa Mohammed claimed the Bahrain government used the FinSpy spyware to hack their laptops in 2011. The two had worked for an organization that provided assistance to Bahrain political prisoners. The Bahrain government has denied the allegations. [Additional coverage in Reuters]
China's failed censorship attempt: Chinese officials tried and failed to take down a Hong Kong dissident's WordPress blog. Automattic said it had not complied with the order and had notified the site owner. [Additional coverage in the Honk Kong Free Press]
Russia abandons its GitHub clone: The Russian government has given up on the idea of a Russian-made GitHub clone. The government announced the project years before but failed to properly finance it. Their new plan is to publish "rules" for any code-hosting repo portals that may spring up on their own across Russia. [Additional coverage in Kommersant]
EU Council passes CRA: The EU Council passed the Cyber Resilience Act on Friday. The new law introduces minimum cybersecurity requirements for digital products sold in the EU. Under the new rules, vendors must provide free and automatic security updates, support products for at least five years, and they must manage a vulnerability disclosure program. Companies must also notify the EU's cybersecurity agency when a vulnerability is exploited in their products. The new law will come into effect 36 months after it's signed by EU officials. Products that meet the CRA's minimum requirements will be allowed to place the CE marking on their product's label.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Dan Guido, CEO of Trail of Bits, about post-quantum cryptography. The pair dive into what it is, why it is needed now and how organisations are dealing with its adoption.
Cybercrime and threat intel
RuNet VPN service admin arrested: Ukraine's Cyber Police arrested a 28-year-old man for managing a VPN service that allows Ukrainians to access Russian websites. The suspect was detained in the city of Khmelnytskyi in Western Ukraine. Officials say he launched the service shortly after Russia's invasion of Ukraine and after authorities blocked access to the Russian internet space (RuNet). He advertised the service on Telegram and IT communities.
New npm malware: One hundred eighty-eight malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
Telekopye: The Telekopye Scam-as-a-Service Telegram bot has been updated with support for hotels and room booking services. The service has been available for years and was previously specialized in building phishing pages for various Russian online marketplaces. Security firm ESET says the service can now be used to launch phishing attacks against Airbnb and Booking.com users.
CISA warns of unencrypted BIG-IP cookies: CISA officials have urged organizations to start encrypting user cookies for F5 BIG-IP load balancers. The agency says threat actors are exploiting unencrypted cookies produced by the F5 BIG-IP Local Traffic Manager (LTM) module to pivot to other internal resources. CISA has told companies to use F5's BIG-IP iHealth diagnostic tool to detect appliances that use unencrypted cookies and enable encryption as soon as possible.
Ransomware gangs abuse Veeam vulnerability: Threat actors are exploiting a recently patched vulnerability in Veeam backup servers to deploy versions of the Akira and Fog ransomware strains, according to Sophos.
MSFT Kerberoasting guide: Microsoft has published an official guide for mitigating Kerberoasting attacks.
Trovicor rebrands: German lawful intercept company Trovicor has rebranded as DataFusion. [Additional coverage in IntelligenceOnline]
PEC phishing campaign: Forcepoint looks at a phishing campaign posing as the Italian PEC (Posta Elettronica Certificata), a certified email system commonly used in Italy for secure, legally recognized communication.
Malware technical reports
Lynx is an INC rebrand: Palo Alto Networks says that the new Lynx ransomware is a rebrand of the old INC ransomware service.
PureLogs: Flashpoint's security team has published a report on PureLogs, one of the several active infostealers today.
TrickMo: Mobile security firm Zimperium has published a report on a new version of the TrickMo Android banking trojan, previously also spotted by Cleafy researchers.
CoreWarrior: SonicWall looks at CoreWarrior, a backdoor trojan targeting Windows devices that has seen a recent surge in infection numbers.
HijackLoader: HarfangLab has published a report on the evolution of the HijackLoader MaaS.
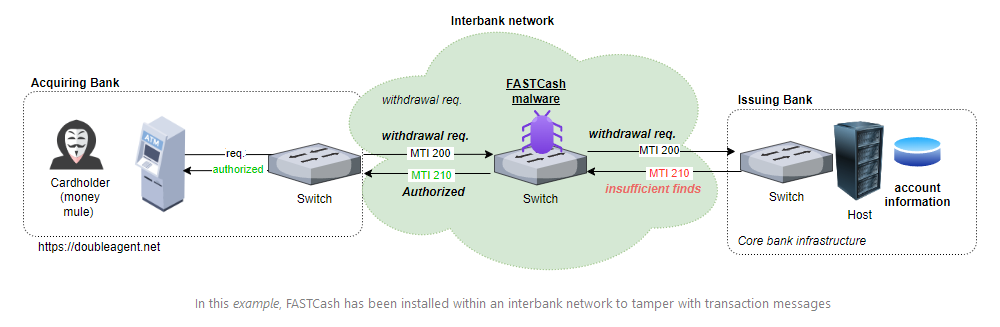
FASTCash: Security researcher HaxRob has published a technical analysis of the Linux version of FASTCash, a malware strain deployed by North Korean hackers on financial networks, designed to perform ATM cash-out attacks. A Windows version was initially spotted in 2018, while the Linux variant dates from last year.
Sponsor Section
You might be hearing a lot about post-quantum (PQ) cryptography lately, and it's easy to wonder why it's such a big deal when nobody has actually seen a quantum computer. But even if a quantum computer is never built, new PQ standards are safer, more resilient, and more flexible than their classical counterparts. More from Trail of Bits here.

APTs, cyber-espionage, and info-ops
Salt Typhoon maintained access: Chinese hackers have maintained access to the US telco wiretapping system as recently as last week. The Wall Street Journal reports that the US government is notifying more companies that their networks have been breached by a group named Salt Typhoon. So far, the only publicly known victims include AT&T, Lumen, and Verizon. Officials are still unclear what the group was seeking inside the hacked networks.
Earth Simnavaz (APT34, OilRig): Trend Micro has published a report analyzing recent Earth Simnavaz campaigns targeting the UAE's critical infrastructure.
Ravin Academy: Iran International has published a profile on the Ravin Academy, a school where the MOIS trains its hackers.
APT-C-20 (APT28): Qihoo 360 looks at recent phishing campaigns linked to Russian APT group APT-C-20, or APT28 and Fancy Bear.
State-sponsored group behind Ivanti CSA attacks: A state-sponsored APT group is suspected to be behind recent zero-day attacks against Ivanti Cloud Services Appliances (CSAs). In a report published last week, the Fortinet security team says the attackers have shown a high degree of sophistication typically seen in past APT intrusions. This included the chaining of multiple exploits, the use of rootkits designed to survive factory resets, and the use of reverse proxy and brute-force scripts to move laterally across the infected networks. Fortinet says the attackers also patched the infected devices themselves once a security update was out to prevent the Ivanti appliance from being infected by other groups. The company didn't attribute the attacks but security researchers found shared infrastructure with at least one Chinese group.
Vulnerabilities, security research, and bug bounty
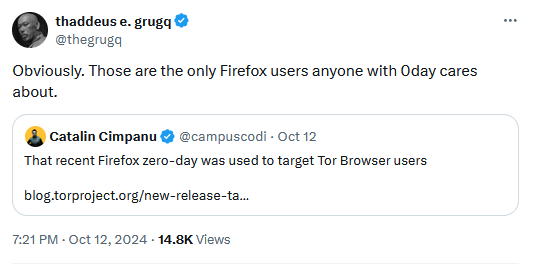
Firefox 0-day targeted Tor Browser users: The Tor Project says that a recently-patched Firefox zero-day was actually used in attacks targeting Tor Browser users. The zero-day was patched by Mozilla last Wednesday. It allows attackers to take control of Firefox-based browsers by exploiting a memory corruption bug in CSS animation timelines to run malicious code in the browser. It was discovered exploited in the wild by Slovak security firm ESET. Mozilla also ported the patch to its Thunderbird email client.
Zendesk backdoor: A 15-year-old security researcher has found a backdoor technique in the Zendesk customer support service tool that allowed him to access private ticketing portals. The technique was possible because Zendesk did not feature protections for email spoofing and did not validate email addresses for new accounts. The researcher said Zendesk initially refused to fix the issue. The company changed its mind after the researcher used the bug to hack Zendesk customers and get rewards from their respective bug bounty programs. In total, the teen says he made over $50,000 until Zendesk patched the issue in July. The bug is half-fixed.
ShadowLogic: HiddenLayer researchers have published details on ShadowLogic, a new method for creating backdoors in neural network models.
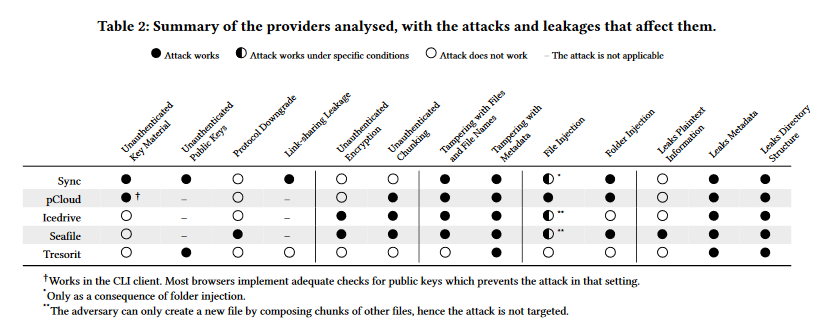
E2EE cloud storage vulnerabilities: A team of academics has found vulnerabilities in the encryption schemes of end-to-end encrypted cloud storage providers that can allow attackers to decrypt data and tamper with customer files. Vulnerable E2EE cloud services include Seafile, IceDrive, pCloud, and Sync. Vulnerabilities were also found in the Tresorit service, but they allowed attackers to modify metadata only. The cryptographic algorithms used by some services were also different from the ones described in their respective whitepapers. Based on their findings, the research team described the E2EE cloud service market as an "immature field."
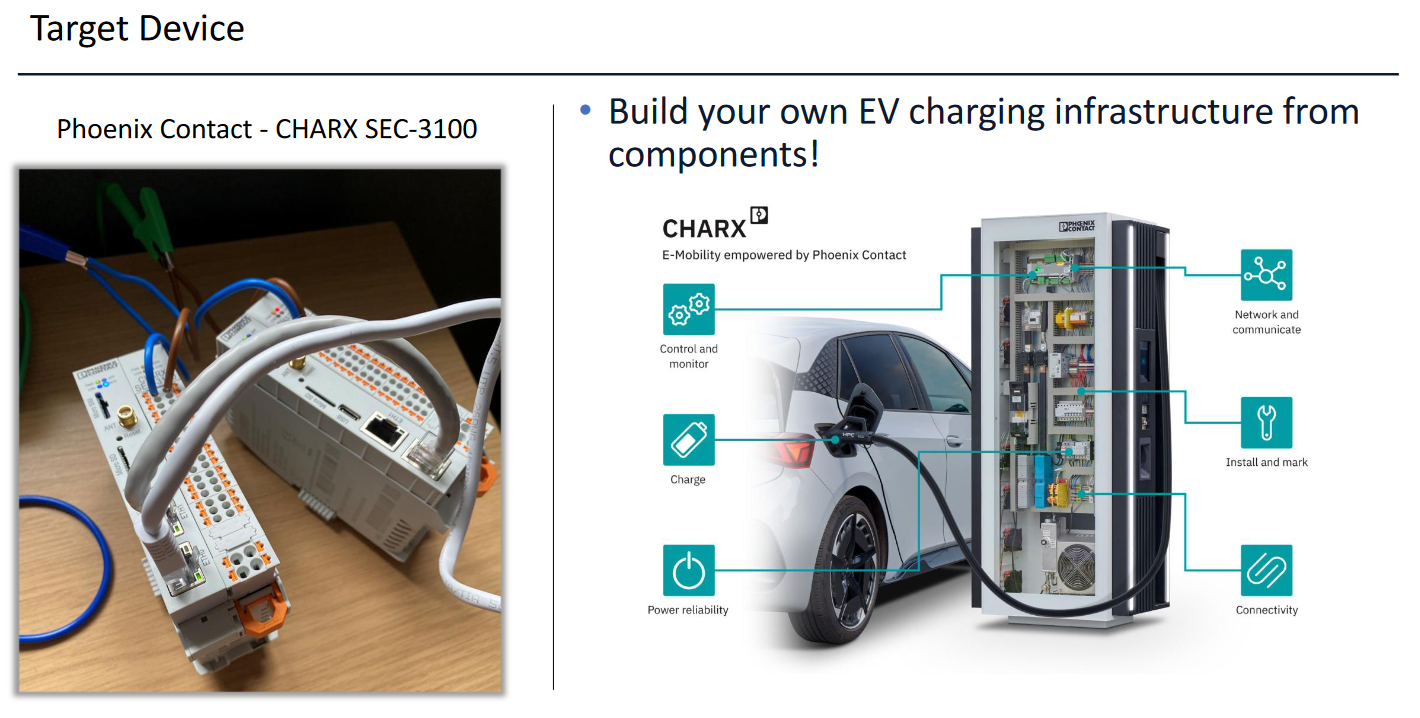
EV charger vulnerabilities: Two NCC researchers have found vulnerabilities in the Phoenix Contact CHARX EV charging systems. The vulnerabilities could have allowed attackers to take over charging stations remotely and even launch ransomware attacks. The vulnerabilities were initially used at the Pwn2Own hacking contest earlier this year, and the vendor patched them back in March [1, 2].
Infosec industry
Project Shield expands: Google has expanded the eligibility criteria for Project Shield, a service that provides free DDoS protection for certain types of organizations. The service launched in February 2016 and was made available for news organizations and human rights organizations. It was expanded in 2018 and 2019 to offer free DDoS protection for political campaigns and candidates in the US and the EU, respectively. Under the new criteria, non-profit organizations supporting the arts and sciences are now also eligible for free protection.
ComfyCon 2024 videos: Live streams from the ComfyCon AU 2024 security conference, which took place back in April, are available on YouTube.
New tool—CellGuard: German academics from the SEEMOO lab have released CellGuard, a tool that analyzes how cellular networks are operated and possibly surveilled.
"The CellGuard app for iOS can uncover cellular attacks targeting your iPhone. It observes baseband packets and analyzes them for suspicious activities, hinting at rogue base stations."
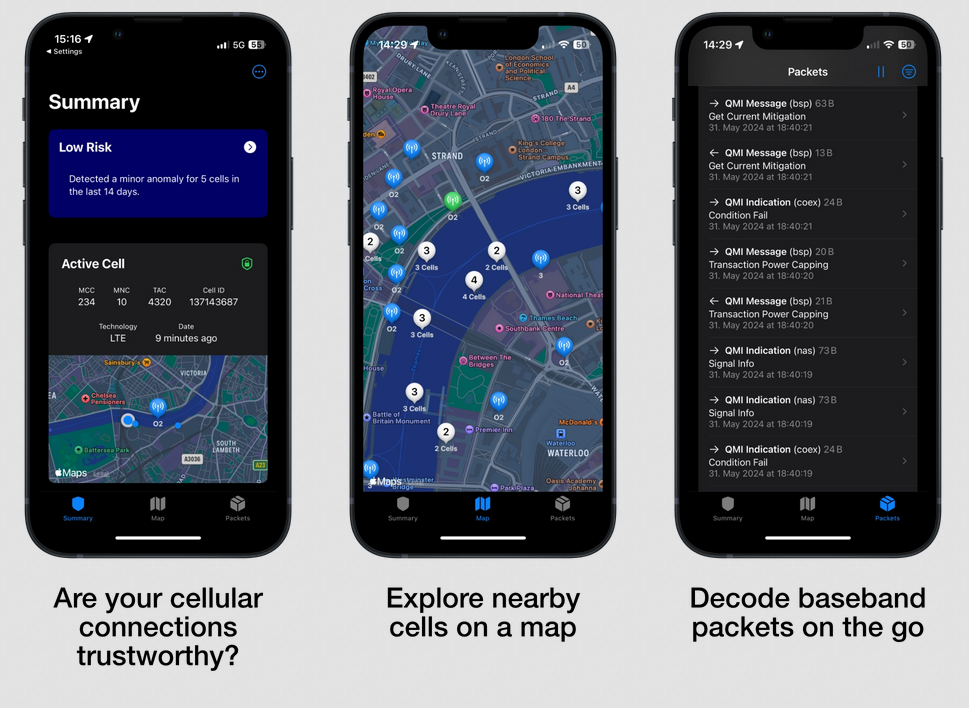
New tool—BaseTrace: The same SEEMOO team has also released BaseTrace, a framework for researching the interface connecting the iPhone's application processor with its baseband chipset.
New tool—Kairos: Security engineer Daniel W. has released Kairos, an open-source eBPF malware analysis framework.
New tool—memexec: The Hacker's Choice has released memexec, a tool to bypass the Linux "noexec" flag and run binaries on systems where you're not allowed to.
Threat/trend reports: Check Point, Crunchbase, CyFirma, Microsoft, Netscout, and Wordfence have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about 'cyber persistence theory.' They cover what it is, why it is increasingly popular amongst America's allies, why we think the theory is right, and also cover some critiques of the theory.
In this podcast, Tom Uren and Adam Boileau talk about a new UN report that spells out the role Telegram plays as a massive enabler for transnational organized crime. They also discuss China's hacking of US telcos to possibly target lawful intercept equipment and a remarkably entertaining account of North Korean IT workers being employed by over a dozen cryptocurrency firms.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




