Risky Biz News: Major hack-and-leak info-op unfolding in Moldova
In other news: FBI came close to deploying Pegasus spyware; Google gets record fine in geo-tracking lawsuit; new PCspooF and Wi-Peep attacks.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
A major hack-and-leak influence operation is currently unfolding in the small Eastern European state of Moldova, where a newly-registered website named Moldova Leaks has released the private correspondence of at least two political figures and promises to release more.
Selected private Telegram conversations from Sergiu Litvinenco, Moldova's Minister of Justice, were leaked last week, and new conversations were released this week from Dorin Recean, the current Defense and National Security Advisor to the President and former Minister of Internal Affairs of Moldova.
In one of the leaked Telegram conversations, Litvinenco implied that the Anticorruption Prosecutor contest was rigged in favor of Veronica Dragalin winning the post—which she currently occupies.
The leaked messages unsurprisingly caused a major political scandal in Moldova, being picked up by the pro-Russian political opposition parties as clear-cut evidence that Litvinenco was corrupt and a reason to ask the Parliament for his and Dragalin's dismissal.
Multiple of Litvinenco's conversations were leaked, and members of pro-Russian political parties, including those under active corruption and abuse of power investigations, issued statements on social media to confirm the authenticity of their exchanges with the Moldovan Justice Minister.
But Litvinenco and the Moldovan government called the leak a part of Russia's hybrid war to destabilize the local pro-European government.
The Justice Ministry confirmed the leak but also said that some messages were grossly modified or taken out of context.
"The purpose of this fake is to divert the public's attention from the real problems faced by criminal groups in the Republic of Moldova and their connections with foreign services," the official said on Facebook.
Litvinenco also added that the Telegram account of Moldova's President Maia Sandu was also compromised as part of the attack, and she might be the figure at the top of the Moldova Leaks chart listed on the hackers' website.
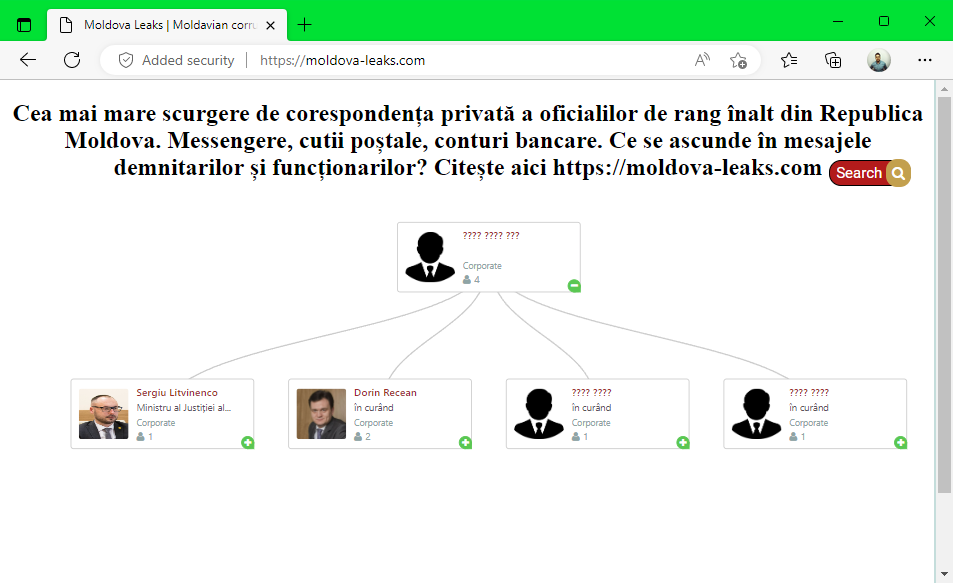
It is currently unknown who is behind the Moldova Leaks website, but Litvinenco said his ministry has already started a formal investigation into the hack, which will also look at the Minister of Internal Affairs, which the official said has the technical capabilities to obtain such conversations at its disposal—suggesting that investigators don't rule this out as an insider attack.
But even if this could be the work of some hacker-for-hire mercenary group, several infosec figures believe this is the work of Russia's GRU agency, which has executed hack-and-leak operations in the past to push Russia's political interests abroad.
And as a former part of the Soviet Union, Russia has quite an interest in keeping Moldova under its sphere of influence and not letting it align with the EU and Romania.
A Washington Post investigation found that Russia's FSB intelligence agency has funneled tens of millions of US dollars through its state-backed companies to Moldova's pro-Russian political parties, and especially to PSRM, the party of Igor Dodon, Moldova's former President.
Dodon, who was caught on video accepting bribes, was indicted earlier this year for treason, accepting money from criminal organizations, and illegal enrichment, charges filed by Litvinenco and under Sandu's clear political agenda to rid the country of corrupt politicians.
But the WaPo report also pointed to a change in Moscow's political financing in Moldova, with the Kremlin turning its favors and funding power to Șor, a new pro-Russian political party led by Ilan Șor, none other than the prime suspect at the heart of a major financial scandal when $1 billion went missing from three Moldovan banks back in 2014.
Three days before he was sanctioned by the US Treasury Department for corruption and promoting Russia's interests abroad, Șor's party organized an anti-EU and anti-government protest in Moldova's capital.
While the Moldova Leaks website might not be an effort to protect Dodon's reputation, they appear to be related to supporting Șor.
Coincidentally—or not—the leak site was put up on the same day the Moldovan government accepted a motion from Justice Minister Litvinenco to review the constitutionality of the Șor party and possibly have it outlawed for putting the country's sovereignty and independence at risk.
Breaches and hacks
Crypto hacks and rugpulls: Cryptocurrency platform DeFiAI said it was hacked and lost $4 million worth of customer tokens. In the meantime, the maintainers of the Flare token appear to have disappeared with their investors' money in a type of scam known as a "rugpull" in the cryptocurrency community. Flare investors are believed to have lost more than $18 million.
Thales ransomware attack: French weapons manufacturer Thales confirmed that some of its data got posted online by the LockBit ransomware but denied that hackers got access to any of its systems. In a press release, the company said the hackers most likely gained access to the portal of one of its collaborators.
General tech and privacy
Google fine: In the largest multi-state data privacy settlement in US history, Google has agreed to pay $391.5 million, representing a fine for lying and misleading users into thinking they had disabled location tracking in their account settings sections. Attorney General Offices across 40 US states sued Google in 2018 following an AP article that found that Google was tracking its users even when they enabled a Google account privacy setting that claimed to turn off location tracking. Google's statement on the lawsuit settlement is here.
Another Twitter snafu: After Twitter's bumbler-in-chief Elon Musk said the company would be turning off 80% of its "microservices" because they were just "bloatware," it appears that one of the "microservices" they turned off was one that supported 2FA. While the service was turned back on, for a few hours on Tuesday, anyone who logged out of Twitter and had 2FA enabled couldn't log back in. Enjoy more Egon idiocy here.
Red Hat deploys cryptographic signatures: Something we missed last month was that enterprise software giant Red Hat added cryptographic signatures for its ZIP file packages, a move that will protect its supply chain and ensure customers can tell if a library came from Red Hat's servers. This feature has been live since October 4, and a technical breakdown of how it works is available here.
Russian company posing as American: A Reuters report has uncovered that the Pentagon was using applications that contained code from a software firm named Pushwoosh that claimed to be US-based but was actually a Russian company. The company's code was also found in thousands of mobile apps across Apple and Google's online app stores.
Firefox 107: ...is out, along with security updates.
Government, politics, and policy
FBI came close to deploying Pegasus: The FBI came close to using commercial spyware from NSO Group as part of its domestic criminal investigations, the New York Times reported. The push allegedly took place in late 2020 and the first half of 2021.
"The FBI eventually decided not to deploy Pegasus in criminal investigations in July 2021, amid a flurry of stories about how the hacking tool had been abused by governments across the globe."
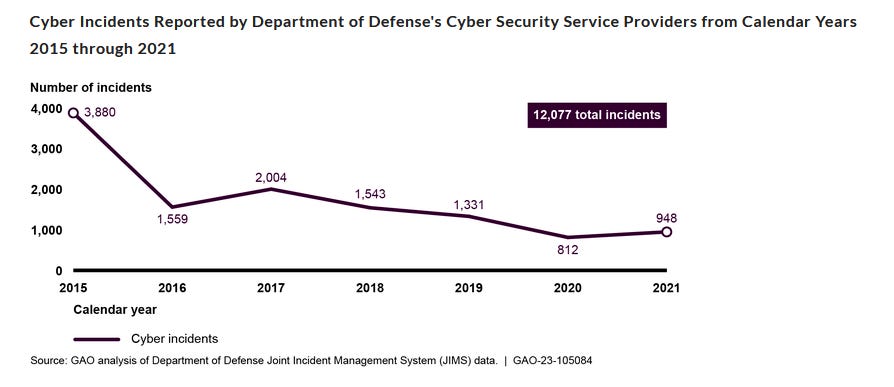
Two GAO reports: The US Government Accountability Office has released two reports this week. In the first, GAO chided the Defense Department for not fully implementing processes for managing cybersecurity incidents, not having complete data on cyber incidents, and not notifying individuals affected by incidents. In the second, GAO praised the Secret Service for making headway in implementing a zero trust architecture.
UAE: Amid a report from the Washington Post that the United Arab Emirates tried to manipulate the American political system through intensive lobbying, BreakingDefense also has a report out on the country's recent efforts to establish itself as a cybersecurity and secure comms hub.
EU EDPS LOL: The European Data Protection Supervisor wants the EU to ban "highly advanced military-grade spyware." Ok, skippy! Good luck with that.
Greece bought Predator spyware for €7 million: A report in Greek press claims that the Athens government paid €7 million to Intellexa for access to the Predator surveillance and spyware platform, and an additional €150,000 for the ability to rotate ten new targets per month. The report comes as the Greek government has been dealing with a massive scandal that it used the spyware to go after rival political parties, but also journalists and prosecutors investigating government corruption.
Italy bans facial recognition: The Italian data protection agency has banned the use of smart glasses and facial recognition software until the end of 2023 or until a specific law is adopted by the central government. The agency, which recently ruled in a case against two municipalities, said the only permitted use of facial recognition would be for law enforcement and judicial investigations.
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Zeus Tank detained: Vyacheslav "Tank" Penchukov, the accused 40-year-old Ukrainian leader of the JabberZeus Crew, has been arrested in Switzerland, according to a report from KrebsOnSecurity. Penchukov has been charged in the US since 2014 for his role in deploying and operating a version of the Zeus banking trojan.
Team Montesano: A new website extortion scheme by a threat actor named Team Montesano is currently underway. The group operates by contacting website owners, claiming to have hacked their servers, and threatening to ruin the website's reputation by leaking stolen data or using their servers for spam operations.
Fangxiao group: Cyjax has a deep dive on a threat actor known as Fangxiao, a Chinese group that has been running more than 42,000 scam sites that impersonate well-known brands to redirect users to sites promoting adware and dating scams.
Attacks target Magento and Adobe stores: SanSec researchers are reporting a rise in attacks probing Magento 2 and Adobe Commerce online stores for a vulnerability tracked as CVE-2022-24086. The vulnerability allows threat actors to place orders on vulnerable stores that exploit the site's emailing feature to take over unpatched stores. Sansec said that based on their data, around 38% of all Magento and Adobe Commerce stores had not been patched for the vulnerability—as of November 2022. A big role in the rising number of probes also played the broad availability of an exploit for the vulnerability, first seen in July this year, on sale on hacking forums.
Koxic & Key Group: Attacks with new ransomware strains named Koxic and Key Group were spotted this month.
AcridRain Stealer: Threat actors are advertising a new infostealer trojan named AcridStealer on underground forums. Per Sekoia, AcridStealer has all the features of a classic infostealer, meaning it can extract credentials from web browsers, crypto browser extensions, crypto wallet apps, and multiple desktop applications, such as email and messenger clients. The stolen data, along with a fingerprint of the infected host, is exfiltrated to a remote C&C server.
Since November 1st, 2022, a new version of #AcridRain #Stealer is advertised by SheldIO on underground forums and sold for $300 a month.
— SEKOIA.IO (@sekoia_io) 5:41 PM ∙ Nov 14, 2022
SEKOIA.IO analysts have a look on it and share results in the thread below 🧵 #CTI
Malware technical reports
Royal ransomware: SecurityScorecard's Vlad Pasca has a technical breakdown of the new Royal ransomware strain.
Amadey Loader: And here's a technical report on Amadey, a malware loader recently used to deploy the LockBit ransomware.
Bumblebee IR report: For blue-teamers and IR aficionados, the DFIR Report team has put out another stellar report on an infection with the Bumblebee malware.
"The intrusion started with a contact form on a website. The contact form gets filled out by the threat actor with a Copyright notice, purporting a violation of the Digital Millennium Copyright Act (DMCA). It then encourages the recipient to download a file showing the purported violation."
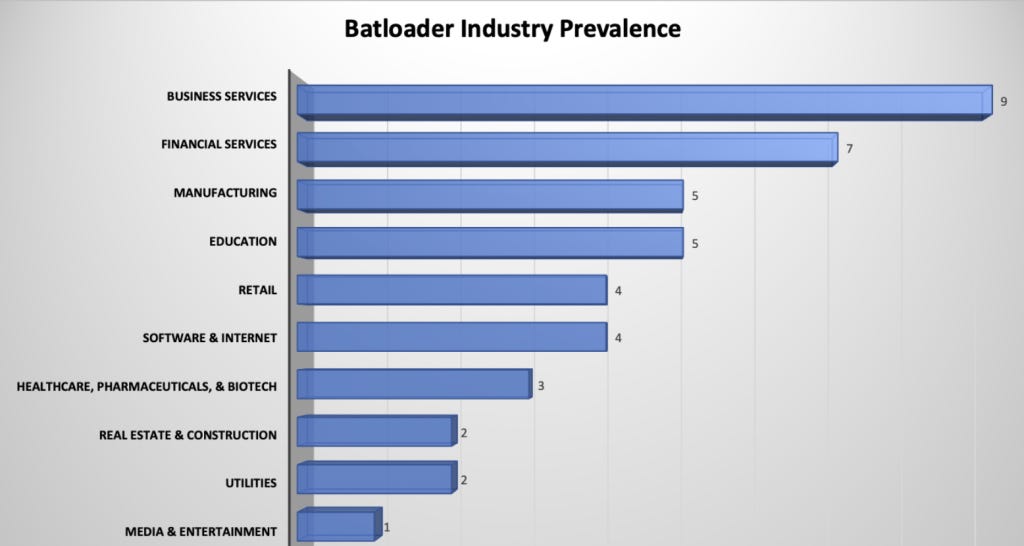
BatLoader: VMware's Carbon Black division has published a report on the BatLoader malware, a new loader deployed via malspam campaigns over the past few months. The loader was first documented earlier this year by Mandiant.
"Observed as early as July of 2022, this malware has already become commonplace as a threat against Carbon Black MDR customers. The following diagram illustrates its prevalence across different sectors, with business and financial services being prime targets. Since it was first observed by the VMware Carbon Black team there have been at least three waves of infection to date with more to be expected."
APTs and cyber-espionage
ESET's APT report: Slovak cybersecurity firm and antivirus maker ESET published a report on the APT activity over the second trimester of 2022 (months May to August). The company's report includes detailed activity for the primary groups originating from Russia, China, Iran, and North Korea, the primary sources of maligned state-sponsored activity in T2 2022.
Introducing brand new ESET APT Activity Report: an overview of the latest activities of selected APT groups analyzed by #ESETresearch. T2 2022 saw no decline in APT activity, with aerospace and defense industries among the targets. Read more in the report:
— ESET research (@ESETresearch) 10:34 AM ∙ Nov 14, 2022
Lazarus DTrack: Kaspersky has a new report out on how the Lazarus Group has used the DTrack backdoor over the past few years since its initial discovery in 2019.
"The DTrack backdoor continues to be used actively by the Lazarus group. Modifications in the way the malware is packed show that Lazarus still sees DTrack as an important asset. Despite this, Lazarus has not changed the backdoor much since 2019, when it was initially discovered. When the victimology is analyzed, it becomes clear that operations have expanded to Europe and Latin America, a trend we're seeing more and more often."
XDSpy: Chinese security firm Anheng Hunting Labs has published a report on new attacks carried out by the XDSpy APT against Russian organizations, including the Ministry of Defense. The XDSpy APT was first discovered in 2020 by CERT-Belarus and ESET and hasn't been linked to any particular government yet, even if it has been active since at least 2011.
OceanLotus attacks: Chinese security firm QiAnXin published a report on Monday about recent attacks of OceanLotus, a Vietnamese state-sponsored group, that have targeted Chinese organizations through 2021. The report details the group's use of three zero-days, one in an unnamed antivirus product and two zero-days in an unnamed workstation management system. QiAnXin also confirmed a Weibu report from earlier this month that claimed that OceanLotus was using IoT devices as a springboard for their attacks. The Weibu report specifically linked OceanLotus to the Torii botnet.
Billbug: Broadcom's Symantec research team has published a report on the activities of an APT group it tracks as Billbug (also Thrip or Lotus Blossom) that the company says has compromised at least one certificate authority (CA) in an Asian country, but also multiple government agencies across multiple Asian countries, in a campaign that has been ongoing since at least March 2022.
"The targeting of a certificate authority is notable, as if the attackers were able to successfully compromise it to access certificates they could potentially use them to sign malware with a valid certificate, and help it avoid detection on victim machines. It could also potentially use compromised certificates to intercept HTTPS traffic. However, although this is a possible motivation for targeting a certificate authority, Symantec has seen no evidence to suggest they were successful in compromising digital certificates."
Vulnerabilities and bug bounty
Mastodon gets its tires kicked: PortSwigger team has kicked the tires on Mastodon's security features, and they found a way to steal account passwords from Mastodon users by leveraging an HTML injection vulnerability without needing to bypass CSP.
Wi-Peep attack: Academics from Canada and the US have published details on Wi-Peep, a new attack that exploits loopholes in the WiFi 802.11 protocol to localize a target's WiFi devices inside a predefined space, like a building or room. The paper is here [PDF], while Mathy Vanhoef, another security researcher known for his work on WiFi security, has an explanation of the attack on Mastodon [embedded below].
"Attacker spoofs beacons to pretend there's buffered traffic. Clients request this traffic & reveal their MAC address. Fake frames are sent to the victim & time-of-flight of the response is used for localization. This can be done from cheap drones. They used an ultra-light DJI mini 2 drone with two lightweight WiFi chips: an ESP8266 & ESP32. Idea is that you can now "look inside a room" and learn where devices are located. For instance, you can learn the location of WiFi security cameras."
PCspoof vulnerability: Researchers from the University of Michigan and NASA have published details about PCspoof, a vulnerability impacting Time-Triggered Ethernet (TTE), a networking protocol that uses time scheduling to synchronize and deliver network packets across Ethernet. TTE is widely used in spacecraft and aircraft technologies because the packet synchronization feature allows multiple systems to co-exist safely on the same hardware inside mission-critical devices. According to the research team, the PCspooF attack breaks this isolation and synchronization between different systems and allows network traffic from one system to interact with other systems on the same device. Technical details are available in this research paper [PDF].




