Risky Biz News: Microsoft addresses OneNote malspam problem, promises fixes through the year
In other news: China to audit Micron chips; India searches for NSO replacement; major breaches in Thailand, the UK, and the Netherlands.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Microsoft plans to roll out changes to its OneNote application to clamp down on the recent abuse the app has been seeing in malware distribution campaigns.
Since the end of last year, malware gangs have been creating and distributing OneNote documents inside which they embed other file types. When users open these files and accidentally or intentionally open and execute the embedded file, the file runs malicious commands that infect the user with malware.
Tricking users wasn't hard, either. Malware groups would typically hide the embedded file under a fake button. When users clicked the button, they'd end up running the embedded file.
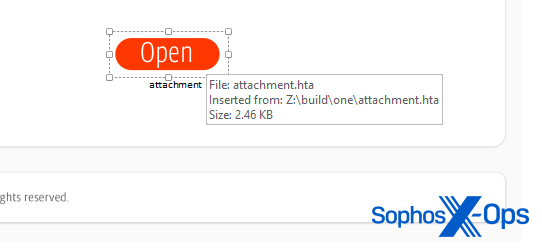
The abuse has been rampant and hard to miss. Cybersecurity firms like Proofpoint, Sophos, WithSecure, McAfee, Perception Point, OpalSec, S2W, InQuest, Yoroi, K7, and Trustwave [1, 2] have all published reports in recent weeks covering the OneNote abuse—by both cybercrime and APT groups alike.
Until now, OneNote's default behavior has been to show a warning to users that opening the embedded file could be damaging to their computers.
Starting mid-April and continuing throughout the year, Microsoft says it plans to update the OneNote app across its platforms and block the execution of embedded files altogether. Instead of the popup warning users about the embedded file, OneNote would show one telling them the file will not be executed at all.
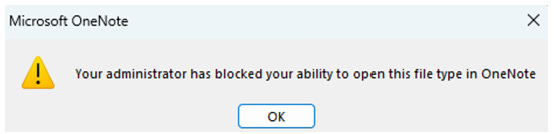
Not all embedded files will be blocked this way, but only those known to be abused by threat actors. Microsoft says it plans to block the same 120 file extensions it currently blocks in Outlook, all of which are known to be dangerous or have been used in the past in malware operations.
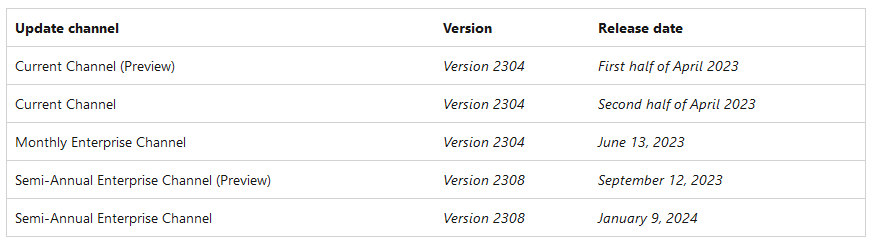
Per Microsoft, this update will apply to OneNote for Microsoft 365 on devices running Windows. It will not apply to OneNote on Mac, OneNote on Android or iOS devices, OneNote on the web, and OneNote for Windows 10. A timeline of the embedded file block rollout is available below.
Breaches and hacks
Blauw leak: Dutch market research agency Blauw says the personal data of more than two million Dutch citizens was stolen from its servers at the end of last month. The data belonged to 14 past customers, including the Dutch Railways, the Dutch Golf Federation, mobile network VodafoneZiggo, health care provider CZ, and two pension funds. The company blamed the incident on a vulnerability in the software of a contractor named Nebu. Blauw says Nebu has refused to cooperate with its investigation, and it's unable to say what exact data was stolen. According to local media, Blauw and five other marketing companies sued Nebu last week to get the company to cooperate in their investigations.
Capita incident: UK IT service provider Capita has suffered a major cybersecurity incident. According to The Times, [non-paywall] Capita employees were unable to log into their computer systems, and the company told them not to try to reset their passwords or use the company's VPN to log in. Details about the nature of the breach are still undisclosed, but the incident has unnerved government officials since Capita is a major contractor for the NHS and many other UK government agencies.
AudienceView hack: Students at dozens of US and Canadian universities and colleges have had their data swiped by hackers after a breach in mid-February at AudienceView. The incident hit the company's Campus platform, a system used by universities for ticketing at sporting, art, and other events. [More coverage in The Record]
Oldsmar hack, not a hack after all: A former Florida city official has revealed that the 2021 hack of the water treatment plant in Oldsmar, Florida was not a hack after all but was the result of an employee clicking the wrong button. At the time, city officials portrayed the incident as a major breach where a hacker connected via TeamViewer and modified chemical levels in the city's drinking water. Al Braithwaite, who was the Oldsmar city manager at the time, says the incident was a non-event and fixed in two minutes, but law enforcement and the media seized on the idea of a cyberattack and "ran with it."
Forta CLA: Fortra, the maker of the GoAnywhere file transfer appliance, faces a class-action lawsuit in Minnesota after several of its customers were hacked and had their data pilfered by the Clop cybercrime group. Many of these companies are now being extorted for large sums of money, with the Clop gang releasing or threatening to release data from the Fortra customers who refuse to pay. The number of hacked Fortra customers is estimated at around 130.
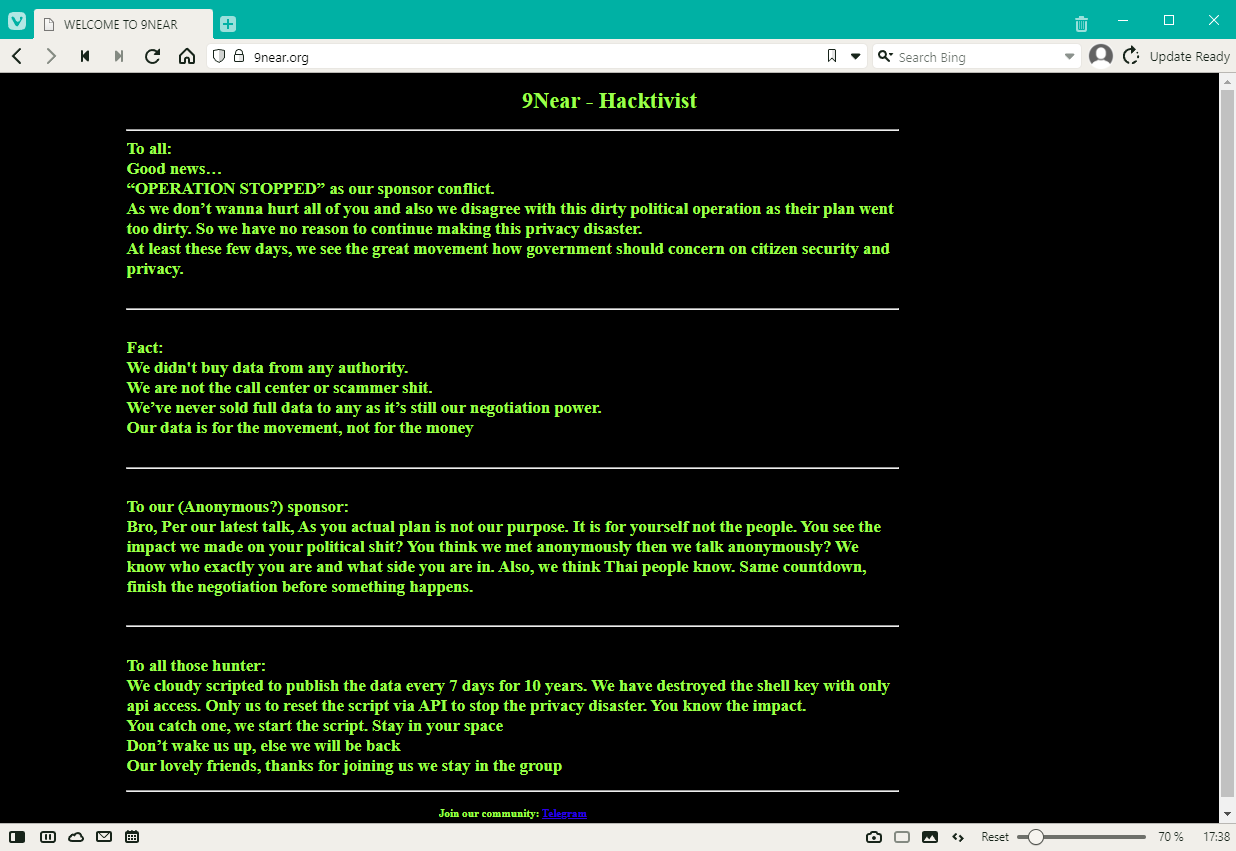
Thai extortion: A hacker named 9Near claimed to have hacked and stolen the personal data of more than 55 million Thai citizens, representing almost three-quarters of the country's population. The stolen information allegedly includes names, birth dates, home addresses, ID card numbers, and phone numbers. 9Near claims to have obtained the data from several Thai government agencies and private companies. The hacker's initial plan was to release the data on April 5 unless the hacked organizations would pay a ransom demand. After Thai officials announced a campaign to hunt and detain the hacker, 9Near posted a message to cancel the upcoming leak and the "privacy disaster" it would have caused for regular citizens.
General tech and privacy
Italy bans ChatGPT: The Italian Data Protection Authority has issued a temporary ban on artificial intelligence software ChatGPT as the agency investigates a possible breach of GDPR legislation, with the agency accusing the OpenAI service of "unlawfully collection of data."
New tool for iOS devs: CMU researchers have developed a tool named Privacy Label Wiz that can help iOS developers create more accurate "privacy labels" for their apps. Researchers developed this tool after previous research found that most iOS apps listed incorrect privacy labels.
Twitter open-sources recommendation algorithm: Twitter has open-sourced its recommendation algorithm that is being used to popular the "For You" timeline. The code is available on GitHub. An analysis of the code shows that users are shoved Elon's tweets down their threats and that Twitter tracks users in categories such as "power_user," "democrat," and "republican," in order to show users more of the content they're usually more likely to interact with. This also has the downside of creating social media bubbles around user groups and keeping them locked in their own version of reality. Twitter also actively buries tweets about Russia's invasion of Ukraine if you're wondering where those tweets went after Musk bought the site.
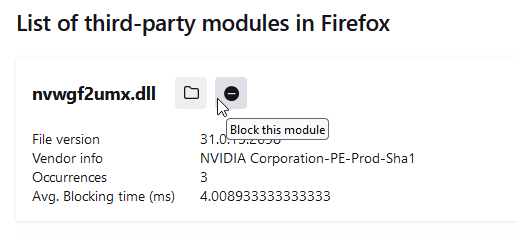
Firefox now lets you block third-party DLLs: With the release of Firefox 110, released in mid-February, Mozilla now lets users block third-party DLLs from being loaded into their browser. The feature can be used to block DLLs that crash the browser or that were secretly installed by malware to spy on the user. This can be done via the about:third-party page. A FAQ page for this feature is available here.
Android 14 to get shoulder surfing protection: The upcoming version of Android 14 will include a feature that will mask all characters of a PIN when entered in real-time as a way to protect against shoulder surfing snooping. Currently, Android devices will show each character of a PIN code for a short time while it's being entered. [More in XDA Developers]
Government, politics, and policy
China to review Micron chips: The Chinese government plans to conduct a security audit of products sold in China by US chipmaker Micron. The audit will be conducted by the Cyberspace Administration of China (CAC), the country's main central internet regulator. Chinese officials say the audit is intended to protect the country's IT infrastructure supply chain and prevent network security risks caused by hidden issues. The move comes after the US and its allies have been imposing trade controls to prevent the flow of advanced chips to the Chinese market. The security review is the first time that China has responded to the trade controls and targeted a US semiconductor company in a move most likely to limit its access to the local market. [Media coverage in the SCMP]
India looking for NSO alternative: The Indian government is looking to spend up to $120 million on spyware and surveillance products to replace its NSO Group capabilities. Officials are looking for spyware products from companies with a lower profile than NSO Group, currently linked to several cases of human rights abuses, including inside India. About a dozen companies are expected to join the bidding process, according to the Financial Times [non-paywall].
Joint statement on spyware: The governments of the US, the UK, and ten other countries have published a joint statement on planned efforts to counter the proliferation of commercial spyware. Agreed countermeasures include tightening export controls, better information sharing to track the proliferation of such tools, and engaging with additional partner governments to reform and align policies on the use of spyware by their agencies. More in this fact sheet. The statement was put out following last week's Summit for Democracy and was signed by Australia, Canada, Costa Rica, Denmark, France, New Zealand, Norway, Sweden, Switzerland, the UK, and the US.
FDA cybersecurity guidance: The US Food and Drug Administration has published new guidance [PDF] requiring medical devices sold in the US to meet specific cybersecurity standards. The new requirements entered into effect on March 29, 2023. Under the new guidance, any medical devices submitted for FDA approval after this date will have to include a software bill of materials. Vendors must also include a plan on how they plan to identify and deal with security vulnerabilities and how they plan to release security updates through the product's life cycle. [More in SecurityWeek]
US Space Force cybersecurity budget: The US Space Force is seeking $700 million in the 2024 budget to cover cybersecurity-related expenses. Gen. B. Chance Saltzman, chief of space operations, said the requested funds will be used to "enhance the cyber defense of our critical networks associated with space operations." The official says the funds will be used for software, hardware, and operator training. [Additional coverage in SpaceNews]
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
FlyHosting takedown: German authorities have seized the servers of FlyHosting, a web hosting provider that catered to cybercrime gangs and DDoS-for-hire services. German police say they served eight search warrants and identified five individuals aged 16-24 suspected of operating the service since mid-2021. According to KrebsOnSecurity, news of the FlyHosting raid surfaced last week on Telegram channels where DDoS booters advertise services.
Chinese hackers detained: Sri Lankan authorities have detained 39 Chinese nationals on charges of hacking and stealing money from the bank accounts of people living in different countries. The suspects were detained after police received tips from several embassies that a group of suspected hackers was staying at a tourist resort in the city of Kaluwamodara.
Phishing gang dismantled: Police forces across Europe have dismantled a prodigious phishing gang that stole more than $4.3 million from EU citizens via phishing campaigns. Two of the gang's leaders were detained in Ukraine, while ten other members were arrested across Europe. Ukrainian police say the group ran at least 100 phishing sites. So far, more than 1,000 victims have been identified, including citizens of the Czech Republic, Poland, France, Spain, Portugal, and other European countries.
TACTICAL#OCTOPUS: Securonix researchers have an analysis of a tax-themed phishing campaign they linked to the TACTICAL#OCTOPUS threat actor.
Anonymous Russia: ThreatMon has a summary of all the operations conducted by Anonymous Russia since the start of Russia's invasion of Ukraine. Their operations sprawl from July 2022 to March 2023, with attacks targeting private companies, hospitals, and government organizations in NATO-aligned and Ukraine-friendly states.
Anonymous Sudan linked to Russia again: Trustwave researchers say the Anonymous Sudan hacktivist group appears to be an on-the-side project of pro-Kremlin group Killnet and not an authentic hacktivist movement. Trustwave becomes the second security firm after TrueSec to link Anonymous Sudan to the Russian government. TrueSec's initial report has been widely criticized on the grounds of impartiality, as Anonymous Sudan attacked Swedish government sites in an attempt to sabotage the country's NATO membership. Since then, Anonymous Sudan has conducted further operations in the Netherlands, Australia, France, and Germany, all purportedly in retaliation for anti-Muslim activity that had taken place in those countries.
"SpiderLabs cannot confirm that the group is based in Sudan, nor if any of its members are from that nation, but based on the evidence available, it seems quite likely that Anonymous Sudan is a Killnet project, possibly including some Eastern European members."
Valley Thief group: Chinese security firm QiAnXin says it has discovered and tracking a threat actor named Valley Thief that is currently engaged in large-scale phishing operations targeting the Chinese financial and manufacturing industries.
New FusionCore MaaS: CyFirma researchers have discovered FusionCore, a new cybercrime gang renting access to an assortment of malware strains via their Telegram channel. The gang is currently behind the AntraXXXLocker Ransomware-as-a-Service, the SarinLocker ransomware, the RootFinder infostealer and ransomware, the Strontium infostealer, the Cryptonic crypter, and the GoldenMine cryptominer. CyFirma says the gang, which they assess to be in their late teens, has a "booming infostealer business."
New npm malware: Twenty-seven new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
Cacti and Realtek exploitation: Fortinet says it spotted threat actors targeting Cacti servers and Realtek devices with exploits meant to infect systems with the ShellBot and Moobot malware. Both are used for DDoS attacks.
Elementor Pro attacks: PatchWork researchers are seeing attacks against WordPress sites trying to exploit a vulnerability in the Elementor Pro plugin.
KEV update: CISA has updated its KEV database with ten new vulnerabilities that are currently being actively exploited. The list includes some very old IE bugs, some Cobalt Strike vulnerabilities, but also the zero-days discovered by Google TAG last week.
- CVE-2013-3163 - Microsoft Internet Explorer Memory Corruption Vulnerability
- CVE-2014-1776 - Microsoft Internet Explorer Memory Corruption Vulnerability
- CVE-2017-7494 - Samba Remote Code Execution Vulnerability
- CVE-2022-42948 - Fortra Cobalt Strike User Interface Remote Code Execution Vulnerability
- CVE-2022-39197 - Fortra Cobalt Strike Teamserver Cross-Site Scripting (XSS) Vulnerability
- CVE-2021-30900 - Apple iOS, iPadOS, and macOS Out-of-Bounds Write Vulnerability
- CVE-2022-38181 - Arm Mali GPU Kernel Driver Use-After-Free Vulnerability
- CVE-2023-0266 - Linux Kernel Use-After-Free Vulnerability
- CVE-2022-3038 - Google Chrome Use-After-Free Vulnerability
- CVE-2022-22706 - Arm Mali GPU Kernel Driver Unspecified Vulnerability
Malware technical reports
AsyncRAT: Sonicwall has an analysis of a new AsyncRAT variant. In the latest variant, the malware has advanced its capabilities by including additional commands support from C2, a clipper module, a crypto-stealer module, a keylogger module, and the ability to prevent systems from going to sleep.
GoatRAT: K7 Security has a report out on GoatRAT, a new Android banking trojan and remote access trojan.
Xloader: Zscaler has a report on Xloader's new code obfuscation. The report covers Xloader 4.3, the malware's latest version, first seen in the wild in January this year.
BumbleBee: Sekoia security researcher Pierre Le Bourhis has published an analysis of the BumbleBee malware.
IcedID: After some cool reports on IcedID from NViso and Proofpoint, there's also this one from Menlo Security.
Magniber: Aleksandra "hasherezade" Doniec published an analysis of the Magniber ransomware.
Cylance: PAN's Unit42 researchers have discovered a new Windows and Linux ransomware named Cylance—named after the security firm, but no connection.
Money Message: Zscaler has discovered a new ransomware strain named Money Message. Bleeping has a more fleshed-out report here.
DarkPower and PayMe100USD: Fortinet has a report on two new ransomware strains spotted last month, named DarkPower and PayMe100USD. Of the two, DarkPower seems to be the more established and professional operation—as Trellix also previously noted.
Sponsor Section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
Reaper's Chinotto backdoor: ThreatMon researchers have published an analysis of Chinotto, a backdoor used by the Reaper APT (aka APT37). Compared to old variants, new Chinotto versions can now also log keystrokes, take screenshots, and more.
APT-C-23: Qihoo 360 researchers have published a report on APT-C-23, an APT group also known as Twin-tailed Scorpion that has a history of targeting the Israeli-Palestinian region. The report covers the group's recent operations that involved boobytrapped and repackaged Android apps during the recent World Cup tournament last year.
0Day Technologies: Threat intel analyst Clement Briens published an analysis of 0Day Technologies, an FSB contractor that was hacked and had its files leaked online in 2019 by hacktivist group Digital Revolution.
Vulnerabilities and bug bounty
Hack the Pentagon website: The DOD launched a dedicated website for its Hack the Pentagon bug bounty program. The program launched in 2016, and it helped the DOD fix more than 2,100 vulnerabilities for bug reports sent by more than 1,400 ethical hackers, per the DOD DDS.
Azure Pipelines RCE: Legit Security has published its technical report on CVE-2023-21553, an RCE in Azure Pipelines patched in February. The vulnerability allows an attacker to execute malicious code in a context of a pipeline workflow, which allows attackers to gain sensitive secrets, move laterally in the organization, and initiate supply chain attacks.
TAP OBO attack: SpecterOps has published details on a new attack on AzureAD that takes advantage of Temporary Access Passes (TAP) and the OAuth on-behalf-of (OBO) flow to maintain access to the target account, even after the TAP has expired.
"As of 3/24/2023, Microsoft has fixed the issue of refresh tokens remaining valid after a TAP has expired."
Outlook zero-day (CVE-2023-23397): QiAnXin researchers have a report out on the in-the-wild exploitation of CVE-2023-23397, a recently-patched zero-day in Microsoft's Outlook client.
ExploitDB-v-0day.today comparison: VulnCheck researchers have analyzed the content of ExploitDB and 0day.today, today's two largest exploit-hosting platforms. By exploit volume, EDB is king with more than 45,000 exploits, while 0day.today lists under 38,000 entries.
"EDB and 0day.today both contain tens of thousands of exploits, and although there is a good amount of overlap between the projects, they each offer their own unique exploits."
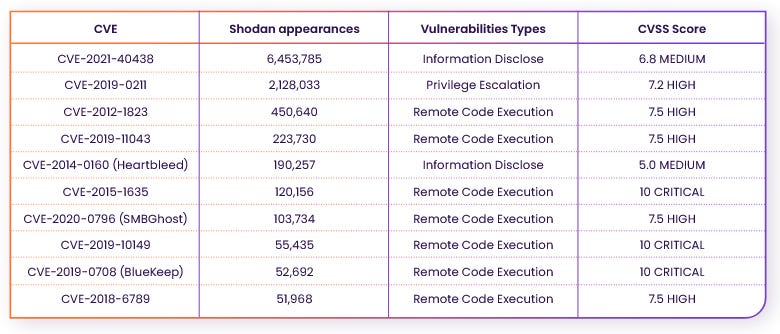
CISA KEV exposure: Rezilion says it scanned the internet for systems exposed to the 896 vulnerabilities included in the CISA KEV database and found more than 15 million systems worldwide that will need patches to prevent easy exploitation. The top ten most exposed vulnerabilities are in the table below, with two Apache web server issues leading the pack—although, since the product is a "web server," it is natural to see it at the top.
Infosec industry
Newmark donation: Craigslist founder Craig Newmark has donated $500,000 to the Shadowserver Foundation.
3CX detection website: A group of security researchers has put together a website that lets you check if your machine was popped during the 3CX supply chain attack.