Risky Biz News: Improperly patched Cleo bug exploited in the wild
In other news: US sanctions Chinese APT exploit supplier; Romania's largest electricity provider hit by ransomware; OpenWrt fixes firmware contamination attack.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Termite ransomware group is believed to be behind a wave of attacks exploiting an improperly patched vulnerability in Cleo file transfer products.
The attacks started on December 3 and have compromised at least ten organizations, according to security firm Huntress Labs.
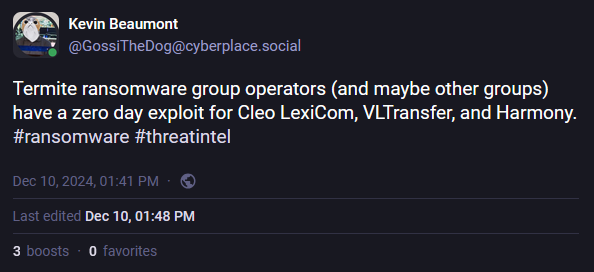
The Termite group is exploiting a bug initially patched at the end of October that impacts Cleo file-transfer products such as Harmony, LexiCom, and VLTrader.
Tracked as CVE-2024-50623, the bug is an unrestricted file upload and download vulnerability that can lead to remote code execution attacks.
Huntress says the patch is incomplete and the attackers are abusing the bug to upload web shells on affected products for data theft and to move laterally inside compromised networks.
It is currently unclear if the Termite gang is deploying its ransomware against hacked organizations or if it's only stealing data for future extortions.
The vendor has confirmed the new attacks and says it's working on a new patch. Since the new exploit abuses the autorun feature to run some of the malicious code, Cleo has told users to disable the feature until a patch is available.
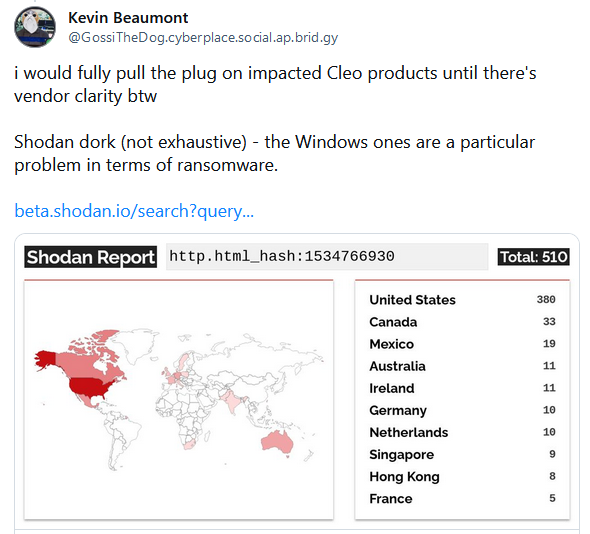
According to Shodan, there are currently over 500 Cleo products exposed online and vulnerable to the ongoing Termite attacks. As security researcher Kevin Beaumont has kindly put it, all affected Cleo products should be taken offline until a new verified patch is out.
As for the group behind the attacks, Termite is as new as it gets. It launched operations over the past month and has already had a massive impact through its attack on BlueYonder, a supply chain software management provider for some of the world's largest retail companies, such as Sainsbury's, Morrisons, Starbucks, and others.
In an email, Huntress told Risky Business that Blue Yonder was running a Cleo instance exposed on the internet before the attack, which may point the finger at how the group got in.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Electrica ransomware attack: A ransomware attack is disrupting the operations of Electrica, Romania's largest electricity provider. In a stock market filing, Electrica says SCADA and other critical systems are isolated and unaffected by the attack. The country's energy minister claimed those behind the attack won't go unpunished. [Additional coverage in EconoMedia]
Artivion ransomware attack: Medical equipment maker Artivion has disclosed a ransomware attack in SEC filings. The company says the incident took place on November 21 and did not have any material impact.
Radiant hack linked to North Korea: DeFi platform Radiant Capital says North Korean hackers were behind the theft of over $50 million worth of assets from its servers in October this year. Radiant says it was hacked after an employee opened a malicious file received from a former contractor via Telegram. The message came from a trusted party and asked for feedback about their most recent work. Ironically, the lure document was a post-mortem for the hack at another DeFi platform hacked days before.
Dating sites close after data leak: Two popular dating websites shut down operations this month after they leaked user data through a misconfigured Firebase server. Lesbian dating site Ladies.com leaked 118,000 user records, while the Senior Dating app shut down after leaking 765,000 user details earlier this year. Leaked data included real names, email addresses, profile pictures, and even geographical coordinates. The leaked data was shared online and was recently added to the Have I Been Pwned database.
General tech and privacy
Slack storage update: Slack says it will auto-delete all content uploaded on free accounts that's older than one year. The new auto-delete policy entered into effect on August 26 this year.
Firefox to remove DNT: Mozilla will remove the DoNotTrack feature from Firefox next year. The feature was introduced in 2011 as a way for users to tell websites not to track them. Mozilla says it's removing the feature because most websites don't respect it. DoNotTrack will be removed with Firefox 135, scheduled to be released in early February.
Snowflake to end single-factor auth: Cloud storage provider Snowflake will start blocking single-factor authentication using only passwords in November of next year. The company is making the move after hackers hijacked customer accounts in a major security breach earlier this year. The hacker exploited leaked passwords to access accounts, steal data, and then ransom the companies. In July, the company announced it would also let tenants force MFA for all their users as a way to protect against similar future attacks.
Orange gets major fine: France's data protection agency has fined telecommunications provider Orange €50 million for several breaches of French privacy laws. CNIL says Orange inserted unsolicited ads in the user inboxes of its Mail Orange service. The company also failed to comply with the EU cookie law and tracked users even if they withdrew their consent. The fine represents the largest penalty ever received by an EU telco.
Government, politics, and policy
New NATO cyber center: NATO will combine three cyber branches into a new cyber coordination center. The new NATO Integrated Cyber Defense Center is set to launch in 2028 and will be based in Mons, Belgium. It will unify the roles of the NATO Cyber Security Center, the NATO Cyber Operations Center, and the alliance's Cyber Threat Analysis Branch. [Additional coverage in BreakingDefense]
New CISA Director interviews: The incoming Trump II administration is allegedly interviewing Brian Harrell as a candidate for the CISA Director role. Harell previously served as CISA Assistant Director for Infrastructure Security during the first Trump administration. Harell is also being considered for the role of DHS undersecretary of strategy, policy, and plans. [Additional coverage in The Record]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Proofpoint senior threat intelligence analyst Selena Larson about the rise of Attacker-in-the-Middle phishing and ClickFix social engineering campaigns.

Arrests, cybercrime, and threat intel
ELITETEAM: Chinese security firm Knownsec 404 has published a profile on ELITETEAM, an infamous bulletproof hosting provider for cybercrime operations.
"ELITETEAM was registered in Seychelles on November 13, 2020, but is actually controlled by a Russian organization, primarily owning one autonomous system (AS): AS51381. As illustrated below, a query of the AS's WHOIS information reveals that 1337TEAM LIMITED and ELITETEAM may be operated by the same controller, deeply involved in global cybercriminal activities, especially in bulletproof hosting, phishing, malware distribution, and cryptocurrency scams related to dark web markets."
Netscaler brute-force attacks: Germany's cybersecurity agency says there's an ongoing wave of brute-force attacks hitting Citrix Netscaler devices.
Syria hacktivism: Several hacktivist groups are now launching DDoS attacks against Russian organizations for harboring former Syrian president Bashar al-Assad.
Malware technical reports
Antidot: Zimperium researchers have spotted a new version of the Antidot Android banking trojan, which they are tracking as the AppLite Banker.
IOCONTROL: Iranian hacking group CyberAv3ngers has developed a new malware designed to infect IoT and OT devices. Named IOCONTROL, the malware was spotted deployed on PLCs, HMIs, firewalls, routers, and IP cameras. Security firm Claroty says it retrieved samples of the new malware from Gasboy fuel control systems installed across Israel. According to US officials, the CyberAv3ngers group operates under Iran's Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC).
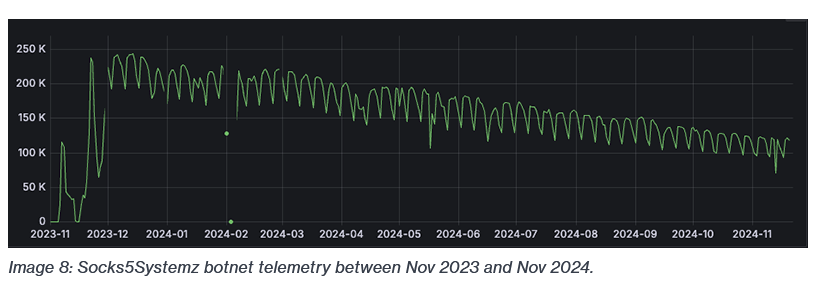
Socks55Systemz: A malware operation known as Socks55Systemz is behind a commercial anonymous proxy service named PROXY.AM. The malware has been around since 2016 and was often distributed as a SOCKS5 proxy module inside larger botnets such as Trickbot, SmokeLoader, and Andromeda. Bitsight says the malware is currently on over 120,000 systems but was double that size at its peak last year.
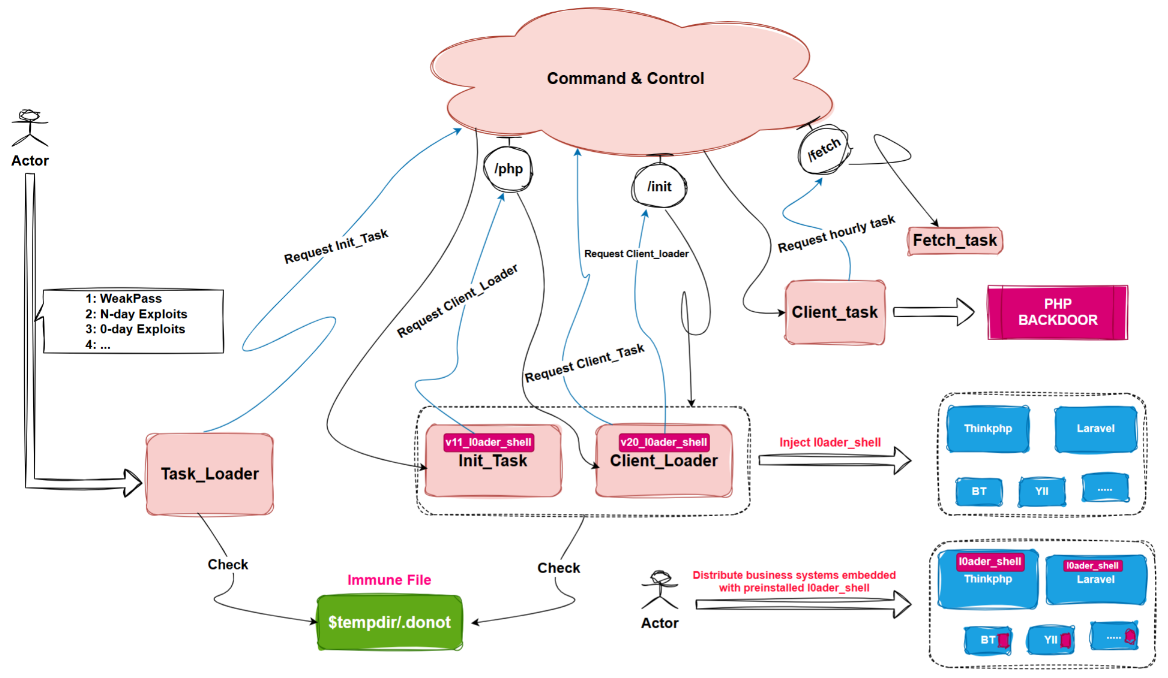
Glutton: Chinese security firm QiAnXin has discovered a new sophisticated backdoor named Glutton that appears to be the work of an APT group. The backdoor has been found deployed on PHP-based websites via unknown methods. QiAnXin believes Glutton may be the work of Winnti, a codename used by Western companies for Chinese APT operations.
Sponsor section
The Proofpoint Voice of the CISO report is drawn from a survey of 1,600 chief information security officers across 16 countries, exploring key challenges, expectations, and priorities. What does the data reveal?
APTs, cyber-espionage, and info-ops
UAC-0185: Ukraine says that Russian hackers are targeting the country's defense contractors in a massive phishing campaign. Ukraine's CERT has identified the attackers as a group tracked as UAC-0185 (UNC4221). The group is a new Russian APT that began activity after Russia's invasion of Ukraine. Its main past operations included attempts to breach Ukraine's DELTA and TENETA military apps and phishing Ukrainian servicemen via secure apps such as Signal, WhatsApp, and Telegram.
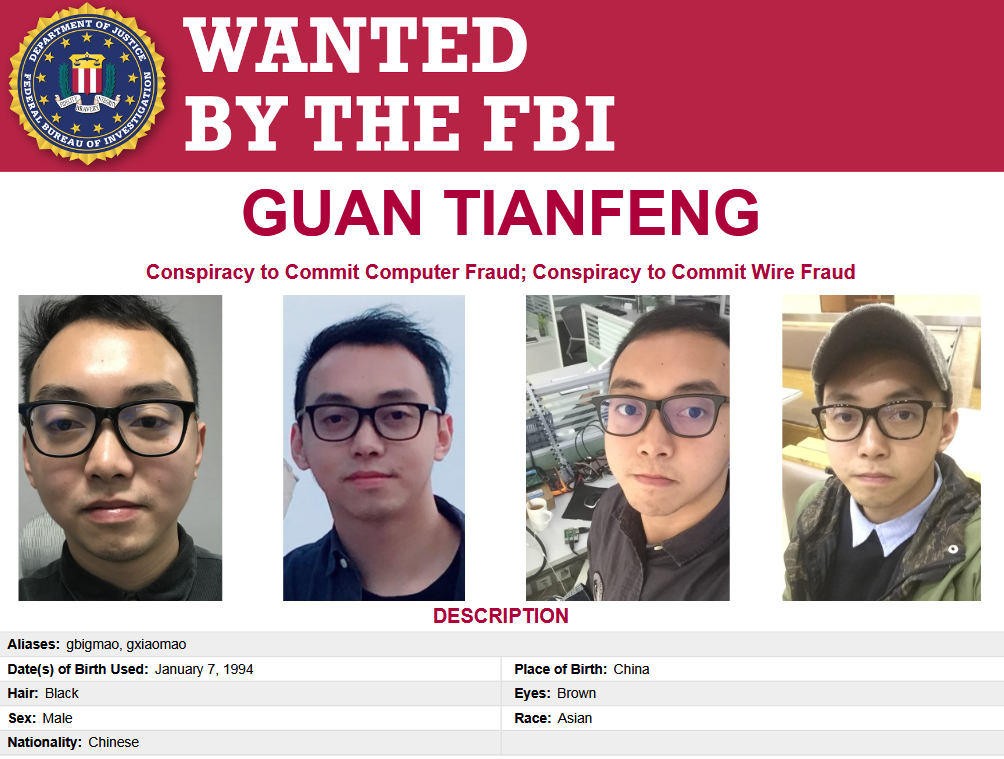
US sanctions Chinese APT supplier: The US Treasury Department has sanctioned Chinese IT company Sichuan Silence and one of its employees for their role in a major hacking spree that targeted Sophos firewalls. Officials say the company developed an exploit for Sophos firewalls that it deployed on over 81,000 devices to steal login credentials. Sanctions were levied against Sichuan Silence employee Guan Tianfeng because he also deployed the Ragnarok ransomware on some of the hacked devices. He was also charged by the US Justice Department. The company was exposed as a major exploit developer and supplier for Chinese APTs in a Sophos report published last month. Its exploits have been traced back to hacking campaigns carried out by Volt Typhoon, APT31, and APT41.
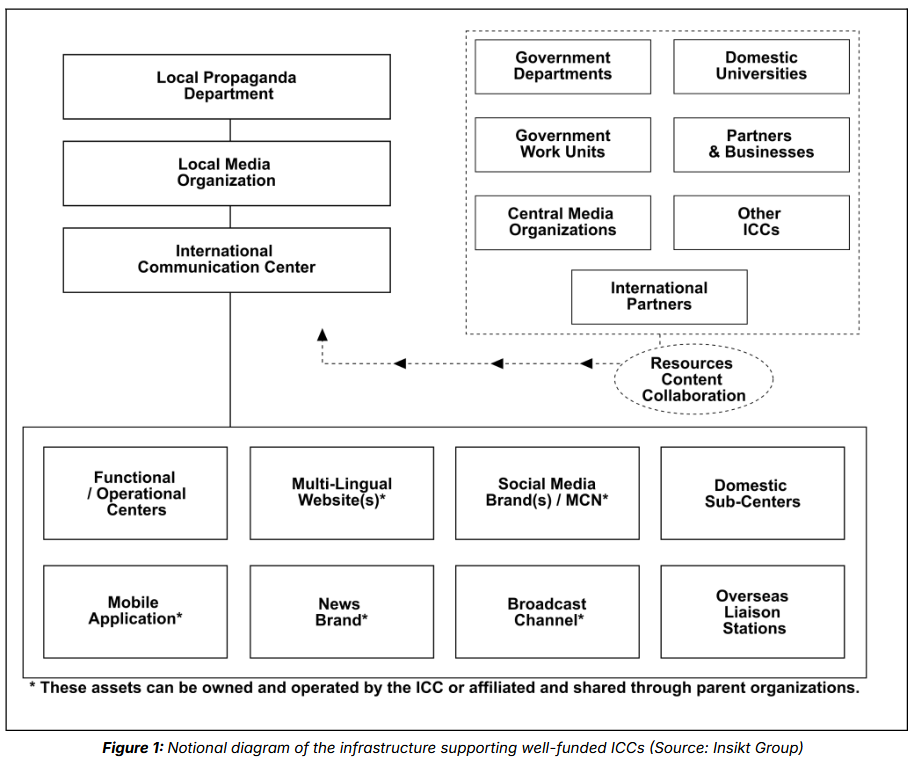
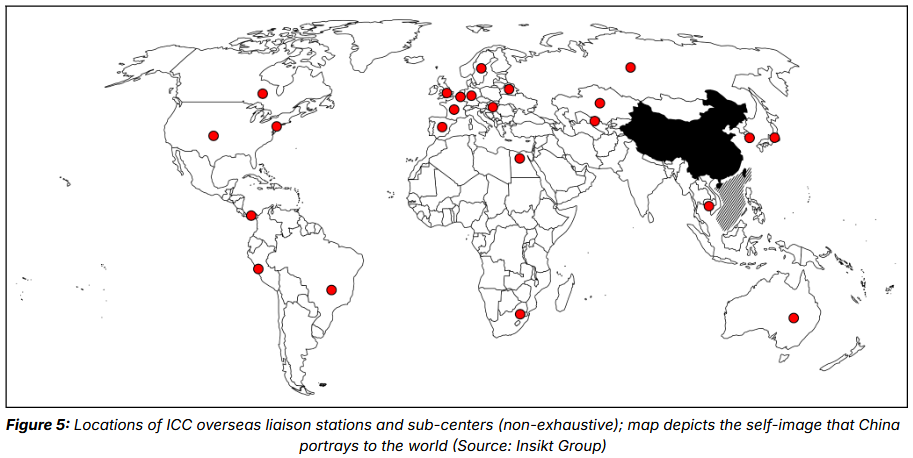
China expands its propaganda machine: The Chinese government has established over 100 international communication centers (ICCs) across the country to expand its foreign propaganda capabilities. Security firm Recorded Future says the centers operate under local CCP state media organizations and most have been established since 2023. The centers cater to specific audiences and countries and tailor propaganda for each region. Their primary functions are to manage thousands of foreign social media accounts and coordinate activity with networks of foreign influencers. They also establish collaborations with foreign media organizations to increase the legitimacy of Beijing's propaganda.
TikTok downplays role in Romania's annulled election: TikTok has put out a press release last week attempting to downplay its role in Romania's recently annulled elections. The company says the network that pushed a far-right pro-Kremlin candidate consisted of only 123 accounts, not 25,000, as it was initially reported from independent sources. The TikTok statement is bulls**t and just damage control after the company was caught, yet again, not acting on obvious disinformation campaigns.
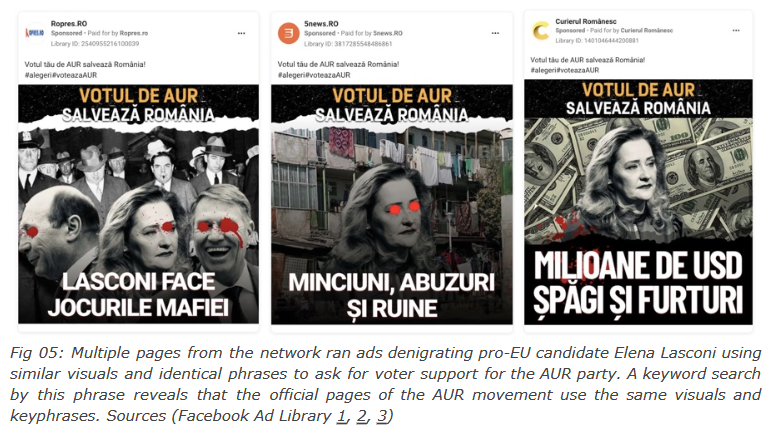
Meta was also MIA during Romanian elections: Meta has failed to detect a network of accounts and pages that ran an influence operation in support of the far-right AUR party in the Romanian presidential and parliamentary elections this year. Disinformation study group CheckFirst says the network ran thousands of political ads that broke Meta's policies and Romanian election laws. The ads promoted the AUR party leader as a patriot and parroted the Kremlin's anti-NATO and anti-EU rhetoric. CheckFirst says Meta clearly failed to act on the network despite public reporting on its activity going back as far as April. Meta joins TikTok as another social network that failed to take action against political ads, even if they clearly broke both internal policies and national laws.
"Our findings are consistent with previous investigations into political advertising in Eastern Europe, reinforcing the platform's ongoing failure to adequately moderate ads from questionable parties and individuals as well as prevent foreign interference in elections."
Vulnerabilities, security research, and bug bounty
Patch Tuesday: Yesterday was the December 2024 Patch Tuesday. We had security updates from Adobe, Microsoft, SAP, Ivanti, Atlassian, Intel, AMD, Schneider Electric, Siemens, Kubernetes, Splunk, and Cobalt Strike. The Android Project, Fortinet, SonicWall, Cisco, Zyxel, ASUS, Rockwell, JetBrains, SolarWinds, SailPoint, QNAP, and Veeam released security updates last week as well.
Microsoft Patch Tuesday: This month, Microsoft patched 71 vulnerabilities (excuse the mess in there, the API is now mixing cloud CVEs with the regular Patch Tuesday), including an actively exploited zero-day (CVE-2024-49138) (discovered by CrowdStrike).
WhatsApp patches view-once bypasses: Meta has rolled out a patch to fix a bypass of its WhatsApp view-once feature.
RoR JSON Juggling Attack: Security researcher Luke Jahnke has published details about a new technique called the JSON Juggling Attack that can execute malicious code via user-provided input inside Ruby on Rails apps.
OpenWrt fixes firmware contamination attack: Security researchers have found a vulnerability in the OpenWrt open-source router firmware that can be abused to contaminate firmware images. The attack targeted Attended Sysupgrade, a feature that allows users to build customized firmware based on the router features they want. Researchers at Flatt Security say the bug allowed them to contaminate firmware artifacts on OpenWrt servers where the custom firmware was being assembled. The OpenWrt team patched the bugs three hours after it was reported.
BadRAM attack: A team of academics has developed a new physical attack against AMD chips that can allow threat actors to retrieve data protected by the processor's Secure Encrypted Virtualization (SEV-SNP) technology. The attack is named BadRAM and primarily impacts AMD CPUs used in cloud environments, where the SEV-SNP is typically enabled. The attack uses a plug-in hardware component to trick the processor into allowing access to encrypted memory. The hardware needed to carry out a BadRAM attack costs less than $10.
Infosec industry
Threat/trend reports: Check Point, Positive Technologies, and ZDI have published reports and summaries covering various infosec trends and industry threats.
New tool—Rusty-Telephone: Security researcher James Brine has open-sourced Rusty-Telephone, a data exfiltration tool that transmits files through audio loopback devices using frequency-shift keying (FSK) modulation.
New tool—LWiS sources: Bad Sector Labs has published a list of 400+ sites it monitors and uses for its Last Week in Security newsletter.
Tool update—GNU Shepherd: 21 years after its launch, GNU Shepherd service manager has finally reached v1.0.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how states have very different approaches to controlling cyber operations.
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.





