Risky Biz News: The Snowflake breach and the need for mandatory MFA
In other news: Tennessee passes data breach safe harbor law; DMM hacked for $305 million; Hugging Face AI platform discloses breach.

This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Cloud data platform Snowflake is dealing with a cybersecurity incident that is the perfect example of why every major *-as-a-platform company should be enforcing multi-factor authentication (MFA) by default for all their customer accounts.
The company began investigating a possible security breach after threat actors bragged on cybercrime forums about using access to its platform to scrape, collect, and then sell data from two major companies—Santander Bank and Ticketmaster.
An initial report from a cybersecurity vendor floated the idea that the threat actors may have gained access to a Snowflake employee's account and then pivoted to customer infrastructure.
The report wasn't wrong, but it wasn't entirely right either, and it was taken down after Snowflake published a statement on the hack on Friday. In it, the company basically says the hacks took place after threat actors used credentials for Snowflake accounts that were "previously purchased or obtained through infostealing malware."
Per reports on social media, the incident affected at least six companies so far. Snowflake didn't confirm the number, but confirmed the incident affected several of its customers and has already notified them.
While the company denied the report that the threat actor accessed an employee account and pivoted to its infrastructure, it did confirm that a former employee's account and then accessed demo Snowflake accounts. From their statement:
"It did not contain sensitive data. Demo accounts are not connected to Snowflake’s production or corporate systems. The access was possible because the demo account was not behind Okta or Multi-Factor Authentication (MFA), unlike Snowflake’s corporate and production systems."
Snowflake saying no employee account was compromised but then turning around two paragraphs later to say a former employee account was compromised but only to a demo environment makes them look like they're not being honest—if I'm truly being honest about all of this convoluted lawyered-up statement.
Ahead of this newsletter coming out, my colleague Patrick Gray said something extremely interesting in our Slack—"even if you did nothing wrong, allowing your customers to do dumb s**t can blow back on your brand."
And looking at the Snowflake breach, the company may not be really at fault that much in all of this clusterfudge. What they did wrong was not enforcing 2FA on customer accounts.
There's so much infostealer activity taking place right now in the malware-delivery ecosystem, and it's been going on for a few years now. Cybercrime syndicates are building giant databases of compromised credentials, which they are selling online. Compromised credentials are more often at the heart of a breach than zero-days or vulnerability exploitation—I just wish I'd remember the report where I read this so I could embed a nice chart below to make everyone understand its prevalence.
Nevertheless, the same point stands. With the rise of all the infostealer activity and credential shops, it is now the time for big service providers to enable mandatory MFA on customer accounts or face the same reputational damage Snowflake is enjoying right now.
Oh! Almost forgot. Snowflake published some IOCs from the intrusions it detected and how companies could secure their accounts. Apparently, the attackers (tracked as UNC5537) used a tool named "rapeflake" to scrape data from customers' Snowflake databases once they were inside. Classy name!
Breaches, hacks, and security incidents
DMM Bitcoin crypto-heist: A threat actor has stolen over $305 million worth of crypto assets from Japanese cryptocurrency exchange DMM Bitcoin. The incident took place last Friday and the platform has suspended all operations to investigate the hack. DMM says it will guarantee customers the full amount of stolen assets, although withdrawals may take a while to process. According to Elliptic, this is the eighth-largest crypto heist in history.
Hugging Face breach: AI platform Hugging Face is resetting user access tokens after a threat actor gained access to its infrastructure. The incident took place last week and impacted Spaces, the company's portal that hosts user-submitted machine learning models. The company says that legacy HF tokens were impacted and urged users to switch to its new fine-grained access tokens.
Shell breach: Oil and gas giant Shell is investigating a security breach after a threat actor began advertising the company's data on a hacking forum. The breach allegedly impacts Shell operations in nine countries, including Australia, Canada, and the UK. The data appears to belong to one of Shell's online stores. [Additional coverage in CTV News]
CDU breach: The German government is investigating a cyber attack on the country's leading party, the German Christian Democrats (CDU). The country's Interior Ministry described the incident as "serious" and said teams have taken down affected systems. The hack takes place a week before the EU Parliament general elections, scheduled to be held over the next weekend. The CDU is the country's center-right party. Earlier this year, German officials blamed Russia for hacking into the email inboxes of the country's center-left party, the SPD, last year. [Additional coverage in DW]
PAP hacks: Polish officials say Russian hackers breached the website of the Polish Press Agency (PAP) on Friday and published two fake stories. The two stories claimed the Polish government was calling up 200,000 men for military service in Ukraine. This is not the first incident of its kind. Similar hacks were also spotted earlier this year in Czechia and the UK. [Additional coverage in Notes from Poland]
Change Healthcare hack: The US HHS has changed its mind and will allow Change Healthcare to send data breach notifications on behalf of all its customers—since it's its breach, contracting customers argued Change should support these costs and reputational damage that comes with it. [Additional coverage in The Record]
General tech and privacy
Fake news on Twitter: An academic study has found that the vast majority of fake news shared on Twitter during the 2020 US presidential election came from a very small cluster of users. The vast majority of these "supersharers" were "disproportionately Republican, middle-aged White women residing in three conservative states, Arizona, Florida, and Texas." Researchers said this group posted content by hand, without automation, and focused on contentious issues such as abortion and immigration. [Additional coverage in Science]
Firefox image alt text generation: Mozilla is tapping its on-device AI thingeys to add a new feature that automatically adds alt text to images loaded in the browser. This new accessibility feature is planned for Firefox 130, scheduled for release in early September.
Google removes AI overviews: After telling people to put glue in their pizza, sniff arsenic dust, and that cockroaches in your genital organs is normal, Google is rolling back its AI Overviews feature. [Additional coverage in the NYT]
Government, politics, and policy
Ukraine cyber fundraising: The IT Coalition for Ukraine, comprised of 12 European nations, has raised €58 million ($63 million) for Ukraine's IT and cybersecurity defense capabilities. [Additional coverage in the Kyiv Independent]
Tennessee breach safe harbor law: Tennessee Governor Bill Lee signed a bill into law that protects businesses from frivolous data breach litigation. The new law provides a safe harbor for companies unless the breach was caused by "willful and wanton misconduct or gross negligence." The new law entered into effect on May 21. Similar laws against frivolous data breach litigation also exist in Florida and West Virginia. [Additional coverage in Lexology]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Nucleus Security co-founder and COO Scott Kuffer about recent trends the company has observed among customers when it came to patch management and how service level agreements (SLAs) became a sign of an organization's security health.

Cybercrime and threat intel
Money mule network dismantled: Europol has disrupted a money mule network that laundered over €10 million in cryptocurrency assets. Authorities arrested 11 suspects across France, Italy, and Romania, including the scheme's mastermind. Europol says it discovered the money mule network when investigating another cybercrime syndicate that targeted rich people with a novel investment scheme. This larger group lured millionaires into making investments in luxury real estate, asked targets to install a crypto-wallet, and then took control of the wallets to steal their funds. These stolen assets were then passed on to the money mule network for money laundering.
Scam call center crackdown: Thai Customs officials have dismantled a group that worked as an intermediary for online scam compounds across Southeast Asia. Authorities seized 102 Simbox devices, 134 Starlink receivers, and over 50,000 SIM cards that were used to reroute calls for scam call centers. Three Vietnamese and four Myanmar nationals were also detained in connection to the scheme. Officials say that besides hosting and operating call center equipment, the group also ordered and transported equipment for other call centers in neighboring countries. [Additional coverage in KhaosodEnglish]

ISIS wannabe hacker detained: The FBI detained one of the people selling stolen credentials on the Genesis Market last year. Court records show he pledged to become a hacker for terrorist group ISIS. [Additional coverage in 404 Media]
Online betting accounts: Russian security firm FACCT says it detected an increase in the number of verified sports and online betting accounts sold on underground cybercrime forums.
Check Point VPN exposure: IoT search engine Censys is seeing almost 14,000 Check Point security gateways connected to the internet. The devices may be vulnerable to CVE-2024-24919, a zero-day in the company's devices that was patched last week.
WordPress exploitation: The Fastly security team has published a write-up on attacks targeting vulnerabilities in three popular WordPress plugins (WP Statistics, WP Meta SEO, LiteSpeed Cache) to install backdoors and secret admin accounts on compromised sites.
Pharma spam off the rails: Netcraft's Chandler Newman looks at the rising email spam pushing users to fake online pharmacies as a way to steal funds or collect payment details.
Threat/trend reports: Check Point, Entrust, and Positive Technologies have recently published reports covering infosec industry threats and trends.
Malware technical reports
CarnavalHeist: Security researchers from Cisco Talos have discovered a new banking trojan named CarnavalHeist. The malware was first spotted in February this year, is written in Delphi, and targets the customers of Brazilian banks exclusively. Cisco Talos described the threat actor behind the malware as "low-to-moderate sophistication."
Nichan: Chinese security firm Antiy has published a technical report on a new Windows crypto-miner named Nichan
Fake Bahrain app: McAfee has found a threat actor using a fake Bahrain government app to spread an infostealer.
Sponsor Section
Nucleus Security's COO Scott Kuffer shows Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information and then allows vulnerability management teams to do things like assigning responsibility for certain types of bugs to the correct people.
APTs, cyber-espionage, and info-ops
Grayzone exposé: Hacked and leaked emails reveal that Iranian government-funded Press TV has paid thousands of US dollars to a US journalist, a known purveyor of disinformation, and a common guest on Russian TV. [Additional coverage in the Washington Post]
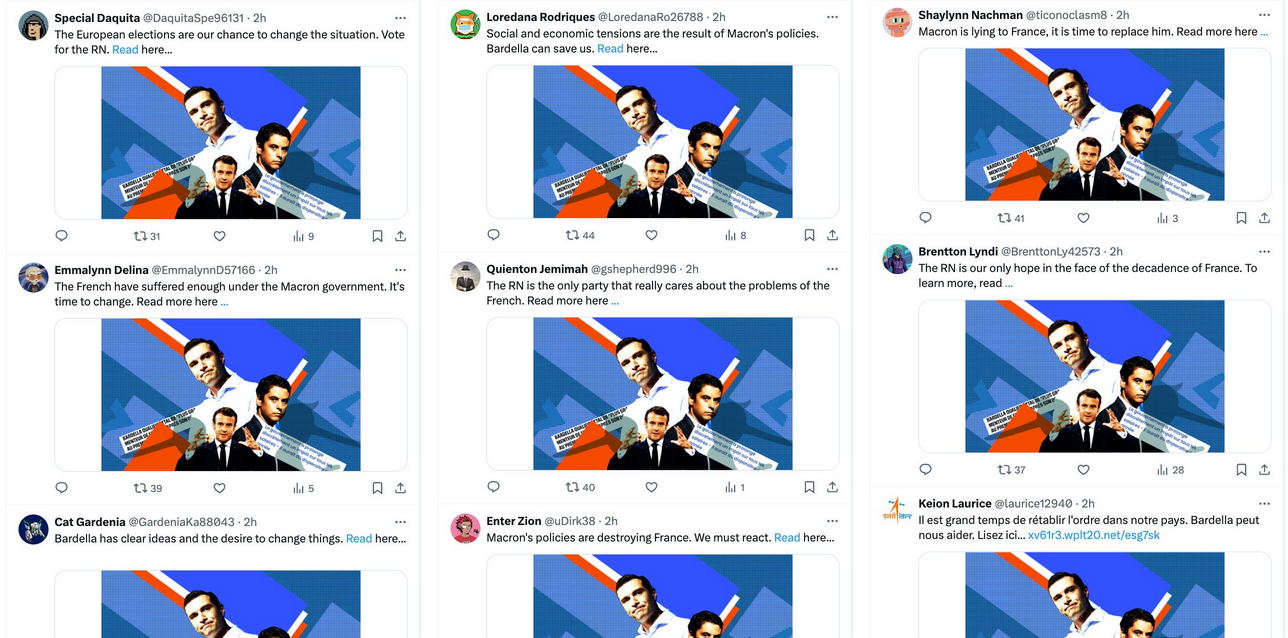
Doppelganger operations: Shortly after Meta and OpenAI took down Russian disinfo accounts, the group is back with new Facebook ads and new accounts promoting right-wing parties ahead of the EU Parliament elections next weekend.
Vulnerabilities, security research, and bug bounty
Nothing in this edition.
Infosec industry
New tool—Dalvik Bytecode Disassembler: Security firm Margin Research has open-sourced Dalvik Bytecode Disassembler, a tool for disassembling Android's Dalvik bytecode.
Crypto ISAC: Thirteen organizations have launched an information-sharing group for the cryptocurrency industry. The new group is named the Crypto ISAC and joins the list of tens of other ISAC groups active in the US catering to various industry verticals. Founding members include Trail of Bits, Coinbase, Kraken, and the Solana Foundation.
BruCON 2023: Talks from the BruCON 2023 security conference, which took place last September, are available on YouTube.
Disobey 2024: Talks from the Disobey 2024 security conference, which took place in February in Helsinki, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the role of the state in tackling ransomware, why action has been slow and ineffective, and what it will take to truly change the situation.




