Risky Biz News: Germany sues Microsoft for details on past hack
In other news: VirusTotal releases a new YARA version rewritten in Rust; SEC adopts stricter data breach notification rules; first major deepfake hack incident confirmed.

This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Breaches, hacks, and security incidents
Deepfake incident confirmed: British multinational design and engineering company Arup has confirmed that it is the company at the heart of a deepfake incident from February this year. The company lost $25 million after a scammer tricked one of its Hong Kong employees to send funds to a wrong bank account. The employee said he transferred the funds after the scammers invited him to a meeting with deepfake versions of his colleagues and the company's chief financial officer.
Pump.fun crypto-heist: A threat actor exploited a vulnerability in a smart contract to steal $2 million worth of tokens from DeFi platform Pump.fun. The hack took place on May 16, and the company described the incident as a flash loan attack. A threat actor named STACOverflow took public credit for the breach on Twitter. So far this year, hackers have stolen more than half a billion US dollars worth of crypto-assets. [Additional coverage in CryptoSlate]
Flutterwave hack: Hackers have stolen ₦11 billion ($7.3 million) from the accounts of Flutterwave, a Nigerian company that creates software for banks and financial services providers. The incident took place in April, according to African tech news outlet TechCabal. The stolen funds were sent to multiple accounts at local banks, from where they were laundered to new locations. This is Flutterwave's fourth hack over the past year. The company has now lost over ₦33 billion ($22 million) in four incidents since February last year.
WebTPA breach: Hackers have stolen the personal data of over 2.4 million customers of health insurance provider WebTPA. The incident took place in April of last year but was only discovered months later, in December. WebTPA says the hackers made off with loads of personal details but no financial information. Stolen data includes name, contact information, date of birth, date of death, Social Security number, and insurance information. [Additional coverage in DataBreaches.net]
The Real World leak: An e-training platform operated by Andrew Tate has leaked the personal data of almost one million subscribers. Reporters from CyberNews say The Real World platform leaked information via a misconfigured MongoDB database. The leaked data included user details, session tokens, and more than 22 million private messages. CyberNews says the database was secured after they contacted the platform, but the company never acknowledged the leak.
General tech and privacy
Slack to harvest DMs: Slack has modified its terms of service to allow itself to harvest customers' files, private workspaces, and DMs to train an AI model. Slack joins a long list of tech companies that decided to train AI models with user data without their consent. The FTC launched an investigation of Reddit in March for a similar decision to take user data and train its AI without user consent.
Azure mandatory MFA: In our last edition, we listed an entry about Microsoft enabling MFA for all Azure customers in July. We smelled botched corporate comms since that would have created huge authentication issues for such a short deadline. It turned out we were right. A Microsoft product manager later clarified this new requirement was only for Azure Portal users, not "all Azure users." This is the portal where corporate admins log in to manage Azure infrastructure.
Government, politics, and policy
New SEC data breach rules: The SEC has adopted new rules requiring financial institutions to have incident response plans. The IR plans will have to cover how the companies will deal with a cyberattack, how they will recover, and procedures for notifying affected customers. Companies will have to notify customers as soon as possible, but not later than 30 days after a breach. The new rules go into effect 60 days after publication in the Federal Register. [Additional coverage in The Record]
Nigeria suspends cybersecurity tax: The Nigerian government has abandoned a cybersecurity tax it was planning to enforce in June. The tax was intended to collect a 0.5% fee from all domestic electronic banking transactions. Officials claimed the tax was needed to improve the security of banking transactions, hence the name. The government backed down after intense backlash from both the financial industry and consumers alike. [Additional coverage in Reuters]
Germany sues Microsoft: Germany's cybersecurity agency has sued Microsoft to get the American company to release more information about a past security breach. The BSI has asked a court to force Microsoft to reveal more details about the hack of its internal systems by a Chinese APT group named Storm-0558. The BSI is specifically interested in Microsoft's use of double key encryption, which the agency fears Microsoft may have failed to implement properly. The German agency sued Microsoft after the company refused to answer any questions from its staff for months. [Additional coverage in Heise]
Microsoft cuts out Russian customers: Microsoft is now blocking Russian customers from accessing its cloud services in compliance with EU and US sanctions. The company is blocking access to over 50 services, ranging from PowerBI to OneDrive and from Visual Studio to SharePoint. Microsoft was initially supposed to block access to the sites on March 20 but delayed the action to give Russian companies more time to migrate. [Additional coverage in The Moscow Times]
NATO cyber ambitions: NATO Deputy Secretary General Mircea Geoană said that Allies "must be big on ambition" on cyber defense and called on member states to improve their cybersecurity defenses.
16th Air Force nomination: The White House has nominated Maj. Gen. Thomas Hensley as the next commander of 16th Air Force, a cyber and information warfare unit inside the US Air Force. The unit has been one of the leading forces behind the US' cyber operations for the past decade. [Additional coverage in DefenseScoop]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Proofpoint senior threat intelligence analyst Selena Larson about the latest changes in the threat actor landscape in the aftermath of several law enforcement takedowns and Microsoft tech stack changes.

Cybercrime and threat intel
Two pig-butchering scammers detained: The US government has arrested two Chinese nationals for their role in a "pig butchering" online scam scheme. Daren Li and Yicheng Zhang allegedly managed an international syndicate that laundered proceeds of cryptocurrency investment scams. Authorities say Li and Zhang directly laundered $73 million worth of crypto assets. Some of the accounts where they sent money held over $341 million in virtual assets, suggesting the duo's group was far more active.
"Li and Zhang allegedly instructed co-conspirators in the laundering network to open bank accounts in the names of various shell companies. Once the victims sent funds to the shell companies, Li and Zhang monitored the lower-level co-conspirators who transferred the proceeds overseas to bank accounts at Deltec Bank in The Bahamas. One of the Deltec Bank accounts was operated with the financial assistance of Li. The funds were then allegedly converted into cryptocurrency and sent to virtual-asset wallets, including at least one controlled by Li. Zhang allegedly also directly received victim funds. Communications revealed extensive coordination to facilitate the international money laundering, including chats discussing the commission structure for the network, various shell companies used, victim information, and at least one video from a conspirator calling a U.S. financial institution."
New npm malware: Nine malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: Akamai, ENISA, and Netscout have recently published reports covering infosec industry threats and trends.
Ransomware and the Russian state: The Natto Thoughts team has published a three-part series on the links between ransomware groups and the Russian state. TL;DR: It's not as straightforward as saying Russia protects its hackers, but you're not wrong in saying that either/sometimes. [one, two, three]
Scam advertising and affiliates: A joint investigation between Qurium, Nameshield Lab, and Cyber Citoyen has uncovered affiliate networks behind the invasion of crypto investment ads on social media sites that redirect users to online scams. The investigation linked the "promotion of dozens of fraudulent investments apps has been traced back to TrafficOn, Supreme Media and ROI Collective three affiliate networks based in Tel Aviv (Israel)."
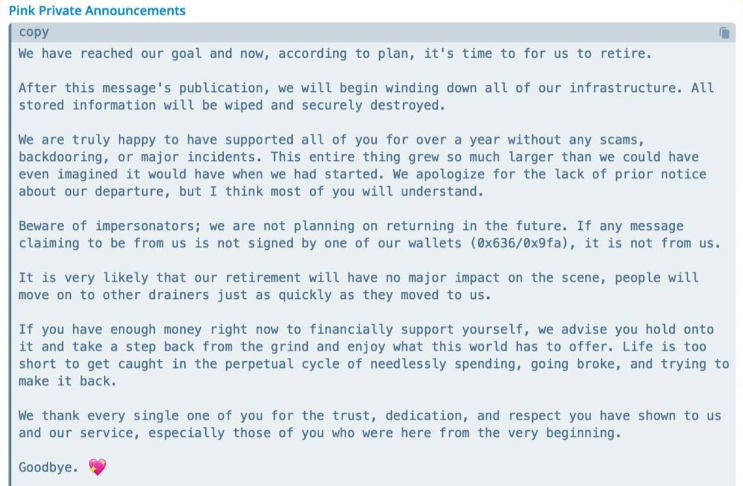
Pink Drainer shuts down: Cryptocurrency phishing service Pink Drainer has shut down operations after stealing over $85 million from more than 21,000 victims. The service launched in July of last year and allowed threat actors to deploy phishing pages specialized in stealing from cryptocurrency accounts. In a message posted on Telegram, the Pink Drainer administrator said they would wind down servers and delete past customer data. Pink Drainer is the third crypto-phishing service to shut down over the past year after Monkey Drainer and Inferno Drainer.

Malware technical reports
Grandoreiro returns: The Grandoreiro malware operation is back up and running after some of its members were detained earlier this year. Security researchers at IBM say they've detected a massive wave of email spam spreading the gang's malware to users in 60 countries. The new operation is a departure from classic Grandoreiro attacks that typically targeted customers at banks in Brazil, Mexico, and Spain only. Five Grandoreiro members were detained in January in Brazil.
STRRAT: Corelight researchers look at STRRAT, a Java-based remote access tool (RAT) that comes with plugins for credential stealing, key logging, and more.
Windows bootkits: Russian security researcher Artem Baranov has published a guide and compilation of reports and talks about Windows bootkits.
Sponsor Section
Proofpoint recently identified a SugarGh0st RAT campaign targeting organizations in the United States involved in artificial intelligence efforts, including those in academia, private industry, and government service. Proofpoint tracks the cluster responsible for this activity as UNK_SweetSpecter.

APTs, cyber-espionage, and info-ops
Obstinate Mogwai: Rostelecom's security team has published a report on the attack of an Asia-based APT group named Obstinate Mogwai against another Russian telco at the end of 2023. Rostelecom says the attack utilized CVE-2020-0688, a deserialization vulnerability in ASP.NET to gain access to the company's Exchange server. The company named the APT Obstinate Mogway (Stubborn Demon) because the group re-compromised the victim several times, trying to maintain access to the company.
Andariel's DoraRAT: South Korean security firm AhnLab has published an analysis of DoraRAT, a remote access trojan used by the Andariel group against local South Korean companies. The malware is written in Go and is very bare, providing only "basic control functions."
Doppelganger info-op: Minutes after news broke of the assassination attempt on Slovakian PM Robert Fico last week, Russian disinformation bots were already hard at work blaming the attack on Ukrainians. The bots were linked to Doppelganger, an alleged GRU-controlled group specialized in info-ops against Western democracies. [Additional coverage in Wired]
Other disinfo campaigns: Other disinfo ops taking place right now include a campaign from Azerbaijan aimed at France's involvement in New Caledonian protests, a Russian campaign blaming the US for the protests in Georgia, and another Russian campaign trying to portray France and President Macron as anti-semitic.
Vulnerabilities, security research, and bug bounty
Microsoft OOB update: Microsoft has released an out-of-band security update to fix a vulnerability in the Azure Monitor Agent. The update fixes a bug that could have allowed authenticated attackers to delete files on a system and gain SYSTEM privileges. The Azure Monitor Agent runs and collects telemetry from Azure customer infrastructure and is enabled by default for all customers. Details about the vulnerability were disclosed and are available online.
Chrome zero-day analysis: Security researcher Alisa Esage has published root cause analysis for two of the three Chrome zero-days that Google patched last week—CVE-2024-4761 and CVE-2024-4671 (yes, very confusing CVEs).
Xbox service PoC: Security researcher Filip Dragović published GamingServiceEoP5, a PoC for an LPE bug in the Windows Xbox gaming service. According to Dragović, Microsoft fixed the bug but didn't assign a CVE.
Laundry machine vulnerabilities: Two California students have found vulnerabilities in laundromats operated by CSC ServiceWorks. The vulnerabilities can allow users to do laundry without paying. Despite the severity of the bugs, CSC has ignored the students' reports and the issue is still unpatched. [Additional coverage in TechCrunch]
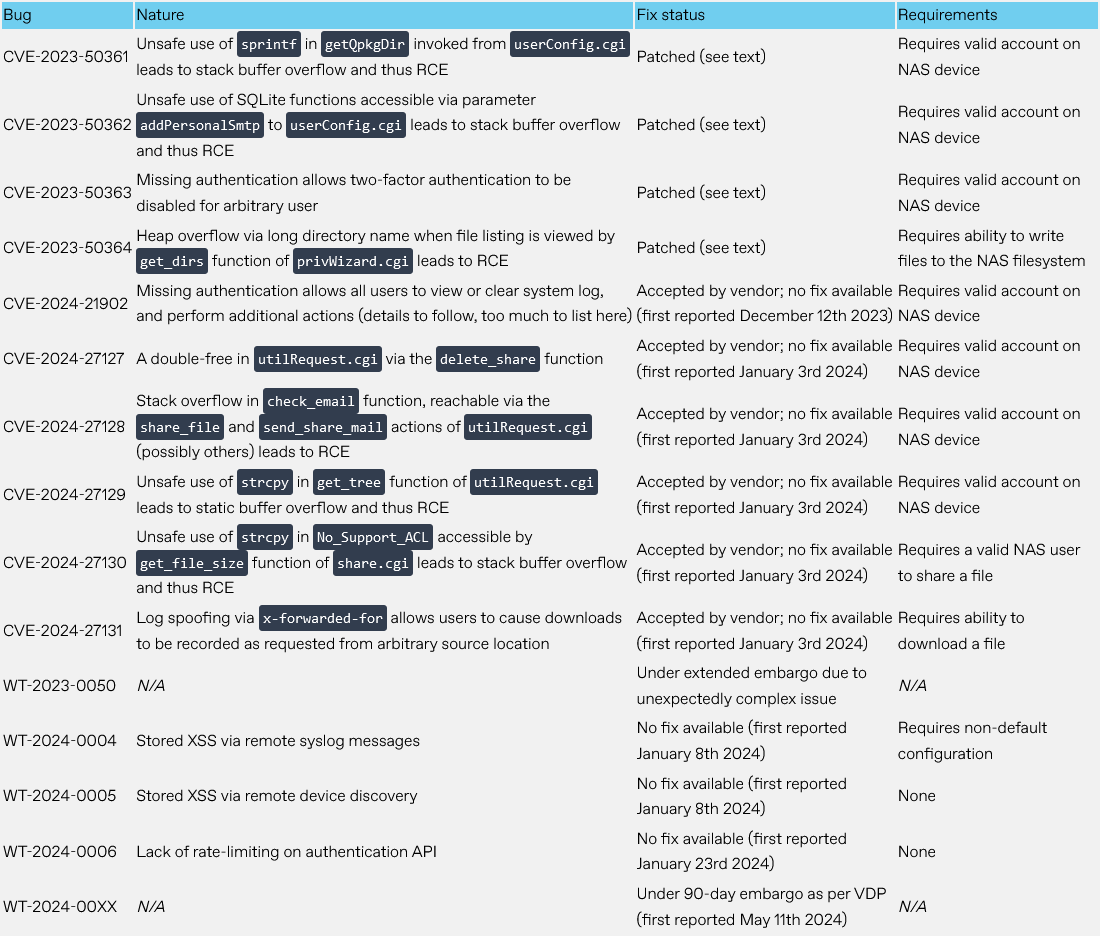
QNAP unpatched vulnerabilities: Security firm watchTowr Labs has found 15 vulnerabilities in the firmware of QNAP network attached storage devices. Some of the vulnerabilities can be used for remote code execution attacks that do not require authentication. watchTowr reported the bugs in December of last year, but the vendor has only patched four of the fifteen so far. The security firm has published a PoC for one of the worst of the 15 bugs.
Infosec industry
New tool—YARA-X: VirusTotal has released a long-awaited new version of the YARA malware query language. The new version is named YARA-X and is a complete rewrite in the Rust programming language. VirusTotal says it re-wrote the language for improved performance and user-friendly queries, and that YARA-X should be 99% compatible with old YARA queries.
New tool—Freeway: Polish security researcher Flock4h has released Freeway, a tool for WiFi penetration that aims "to help ethical hackers and pentesters develop their skills and knowledge in auditing and securing home or enterprise networks."
New tool—darkPulse: Chinese security researcher fdx has released darkPulse, a shellcode Packer written in Go.
New tool—ETWInspector: Software engineer Jonathan Johnson has released ETWInspector, a tool to filter through Windows events—ideal for blue-team operations.
New tool—VirtFuzz: German security firm Seemoo has released VirtFuzz, a Linux kernel fuzzer that uses VirtIO to provide inputs into the kernels subsystem.
Matrix Cup: China is launching a new hacking competition named the Matrix Cup, modeled after the more infamous Tianfu Cup and Pwn2Own. The first edition is set to take place in the city of Qingdao in June. The contest's prize pool is $2.8 million and the target list includes Chinese and Western products, but also AI algorithms. A leak from a Chinese cybersecurity contractor earlier this year claimed that exploits from the Tianfu Cup were regularly given out to Chinese cybersecurity contractors to use in APT and surveillance operations.
RomHack 2023: Talks from the RomHack 2023 security conference, which took place last September, are available on YouTube.
Risky Business Podcasts
The regular two nerds have the week off, but the former Director of the CIA's Center for Cyber Intelligence Andy Boyd joins Patrick Gray for a rollicking conversation in front of a live audience in San Francisco. Grugq and Tom return next week!




