Risky Biz News: FTC looks at cloud providers, their business practices, and data security
In other news: DPRK tries to hijack stolen Euler funds; ChatGPT bug leaked user chats; China to supply Russia with "test firewall system."
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The US Federal Trade Commission is seeking comment from the public on the business practices of cloud computing providers.
The FTC says it wants to understand the role and importance of cloud providers to the US economy and what kind of security risks emerge from the current model.
The FTC's action comes after Politico reported two weeks ago that the White House was exploring the idea of regulating the cloud industry, fearing that some of their predatory business practices would lead to widespread national IT infrastructure outages and major cybersecurity incidents.
This appears to be that action, and the FTC is hitting all the major issues that security researchers, software engineers, and many other have raised about cloud providers over the years.
For example, the FTC is asking the public to share if they have the "ability" to negotiate their cloud computing contracts or if they're stuck in "take-it-or-leave-it standard contracts."
The FTC also wants to know if cloud providers "compete" to provide secure storage. While the FTC didn't say it, they most likely want to confirm that cloud providers offer generally insecure services and then scalp their customers for basic or adequate security features—something that the Risky Business podcast highlighted years ago.
FTC officials also want to know if cloud providers notify their customers about security breaches and misconfigurations. This, again, is a well-known gripe security experts have had with cloud providers. Cloud service providers have a well-known allergy and disdain to issuing CVE identifiers for security issues found in their services. They also rarely bother (except in very rare cases) to notify customers of vulnerabilities discovered in their services.
In addition, the FTC also wants to know if cloud providers use "incentives" to keep customers locked into their infrastructure, which would make customers and even entire industry sectors reliant on a cloud provider's capability to keep its infrastructure up, running, and safe.
The comment period will be open until May 22, 2023.
Since these public comment periods are wild, the FTC might get more varied feedback than it bargained for, especially since the tide of public opinion has been turning against cloud service providers and their predatory practices for a few years now. [Insert joke about pressing the wrong button in an AWS dashboard and bankrupting your company within two hours.]
Breaches and hacks
ChatGPT leak: OpenAI says it fixed a bug in the ChatGPT AI chatbot that caused a small number of users to view the titles and past conversations of other users. The issue came to light earlier this week after ChatGPT users posted images of other people's conversations on social media. OpenAI CEO Sam Altman blamed the issue on "a bug in an open source library."
Lionsgate Play leaky server: Movie studio Lionsgate has leaked some technical user data after it left an Elasticsearch server exposed on the internet without a password. Exposed data included the likes of user IP addresses, device details, user-agent strings, and URLs of streamed content, according to CyberNews.
Skylink attack: Skylink, a major DTH and internet TV service provider in Czechia and Slovakia, says it was hit by a "hacker attack." The company did not disclose the nature of the incident but says it only impacted its "web and customer zones." Skylink says it expects some downtime this week as it works to repair the damage.
LinusTechTips hack: LinusTechTips, one of the most popular YouTube channels, was hacked and used to promote Elon Musk-themed crypto scams. YouTube's security team intervened and took down the entire channel roughly 35 minutes after the first reports. The channel is currently suspended but will most likely be restored to its legitimate owner once it's resecured and the channel's video inventory restored since almost six years worth of videos were deleted shortly after the hack. [Media coverage in Dexerto]
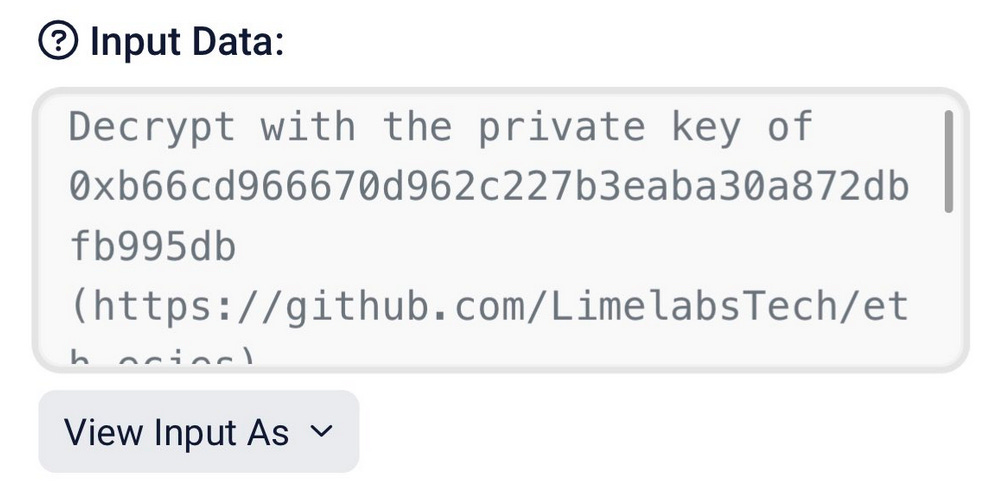
DPRK tries to phish Euler hacker: North Korean hackers tried to phish the individual behind the recent Euler Finance hack in an attempt to hijack the stolen funds. The phishing attempt took place earlier this week and was spotted by Mudit Gupta, the CISO of blockchain company Polygon. Gupta says the phishing attempt consisted of an on-chain message sent to the Euler hacker from a cryptocurrency address linked to the Ronin hack (attributed by the FBI to the DPRK). The message asked the Euler hacker to download a special tool and use their wallet's private key to decrypt and view a supposed message. Euler urged the hacker not to download the tool and attempt to view the message. The company's warning comes as it began negotiating with the hacker about the return of the stolen funds, and execs feared the hacker (and themselves) would lose the bulk of the $197 million if they got phished by the North Koreans.
Government, politics, and policy
Chinese security products for Russia: As part of the recent high-level meetings between Russian and Chinese officials in Moscow this week, the two governments signed several treaties of cooperation, including on cybersecurity topics. According to Russian news outlet Octagon Media, China will provide Russia with "test system firewalls" that can be used to protect against cyber attacks and help disconnect the country from the global internet network. These systems will be deployed in Russia's largest urban centers, such as Moscow, St. Petersburg, Kazan, Vladivostok, Grozny, and other cities with over one million in population. In addition, the two governments have also agreed that their intelligence services cooperate on "cybersecurity issues," although details are obviously not public on what this can mean.
Russia has dumb IT idea again: The Federal Service for Technical Export Control, an agency inside the Russian Ministry of Defense, is exploring the idea of forcing Russian critical infrastructure operators to block their email servers from interacting with foreign IP addresses. The "galaxy brain" idea, reported by Kommersant, will most likely lead to some hilarious situations where legitimate emails and alerts won't get delivered, likely leading to technical outages and missed communications with customers and contractors.
UK healthcare cybersecurity strategy: The UK government has published a cybersecurity strategy for the healthcare and social care sector. The strategy focuses on five pillars: (1) focusing on the greatest risks and harms; (2) defending as one; (3) establishing a cyber culture and a cyber workforce; (4) building secure systems; and (5) exemplary response and recovery.
India data breach stats: More than 1.4 million cybersecurity breaches were reported last year across India, but only 15 companies managed to respect the country's new cybersecurity regulations and report the incidents within six hours after being discovered. Obtained by Medianama reporters, India's data breach reporting figures for last year confirm what industry experts have said all along—namely that India's new cybersecurity regulation is unenforceable as the 6-hour reporting window is unrealistic and almost impossible to meet by most companies.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Anonymous Sudan investigation: French media is reporting that French police and its intelligence agency are investigating the so-called hacktivist group Anonymous Sudan for a series of DDoS attacks against multiple French airport websites.
Chinese hacker detained: Chinese police have detained a man from the city of Guangxi for hacking and wiping the data on servers belonging to a local store chain.
New pro-Russian hacktivist groups: Another batch of pro-Kremlin hacktivist groups have been spotted—UserSec and MistSec. Same ol', same ol'! Both groups put out dumb "manifestos" against the evil NATO members, launch some boring DDoS attacks that take down a website for five mintues, take a screenshot, and then brag about the cyberpocalypse they created. Yawn!
Killnet report: And since we're on the topic of lame pro-Kremlin hacktivists, ThreatMon has a report on Killnet, the kings of lame and inconsequential DDoS attacks.
Fake OT hacking: Google's Mandiant division reports that an increasing number of hacktivist groups are making false claims about compromising operational technology (OT) inside critical infrastructure. Mandiant says it observed false claims coming from hacktivist groups involved in the Russian-Ukrainian conflict—such as GhostSec and Team OneFist—but also hacktivists targeting Israel—such as Iraqi group Altahrea Team and Arabic-speaking hacktivist group Force Electronic Quds.
"In most cases, hacktivists' claims are exaggerated or unsubstantiated. The number of false claims is at times challenging to debunk."
Clop massacre: Clop, the ransomware and data extortion gang that was behind the recent Fortra GoAnywhere zero-day, has begun adding the names of hacked companies on their dark web portal. Twenty-nine companies have been recently listed on the site, including some big names like the Virgin Group, Pluralsight, Hitachi Energy, cloud provider Rubrik, Gray TV, and the city of Toronto, Canada. The gang claims it hacked and stole sensitive files from at least 130 companies, which it now plans to extort.
UNC961: Google's Mandiant has a report on UNC961, a prodigious initial access broker. Mandiant says the group, also known as ProphetSpider, typically operates by taking public exploits for recently disclosed exploits in internet-facing servers and compromising devices before owners can apply patches. Once a system is compromised, the group is believed to rent access to other gangs, including ransomware groups. Mandiant says it observed the group target systems from companies like Citrix, MobileIron, and Oracle. Systems previously compromised by the gang have been used to deploy ransomware, such as Maze and eGregor.
PyPI campaign: Phylum researchers have discovered a malicious Python package—named onyxproxy—that contains malicious code to harvest and steal user credentials. Phylum says the package is unique when compared to other similar threats because it used Unicode characters to avoid code scanning engine.
Instagram scams: Avast reports that users in the UK, Australia, France, Spain, and Poland are being targeted on Instagram with fake SHEIN gift card offers. The end-goal of the campaign is to trick users into handing over their payment card details following a convoluted gift card claiming process.
ChatGPT warning: GuardioLabs and Nexusguard are warning users that malware is being shared online as a ChatGPT-themed Chrome extension and via various Facebook ads leading to infostealer-infested apps.
ENISA transportation threat landscape: ENISA, the EU's cybersecurity agency, says ransomware accounted for 38% of all cyber incidents in the transportation sector between January 2021 to October 2022.
FS-ISAC thread landscape: The Financial Services ISAC published a report with the industry's 2022 threat landscape and predictions for 2023.
- Increased regulation will impose new challenges for multinational firms.
- Cyber insurance will undergo an identity crisis.
- Cybersecurity staffing will continue to be challenging.
Malware technical reports
BlackGuard updates code: AT&T's cybersecurity team says it spotted a new version of the BlackGuard infostealer that can propagate through removable media and shared devices.
RootFinder: Chinese security firm Sangfor researchers have a report on RootFinder, a new .NET stealer spotted in the wild.
Emotet's return: Cisco Talos a report on Emotet's recent return. Similar reports are available from Trend Micro, DeepInstinct, and Cofense.
Magecart skimmer: A Malwarebytes report looks at a Magecart skimmer designed for Magento stores that uses Hunter, a PHP & Javascript obfuscator, to hide its malicious code.
Web skimmers overwhelmingly target WooCommerce now: GoDaddy's Sucuri security division says the "overwhelming majority of credit card skimming malware" they find on compromised websites these days targets the WordPress WooCommerce plugin. Also known as Magecart scripts, e-skimmers, or web skimmers, this type of malware was initially developed to target Magento stores, but threat actors have switched to WooCommerce as more and more stores began using it as their backend. Sucuri says the most recent Magecart script they spotted tried to hide inside an Authorize.net payment gateway module for WooCommcerce stores.
JS injection campaign: PAN's Unit42 team has discovered a massive malware campaign that has injected malicious JavaScript code inside thousands of websites since the start of 2022. The malicious code was found on more than 170,000 distinct pages across more than 51,000 websites. Unit42 says the purpose of this campaign was to take random users from legitimate sites and redirect them to malicious sites hosting online scams and adware-infested applications.
Gozi: ToxinLabs published a report on a Gozi malware campaign targeting Italy and impersonating the Italian Revenue Agency.
AresLoader: Intel471 has a report on AresLoader, a new malware loader currently advertised on Russian-speaking cybercrime forums.
DarkPower ransomware: Trellix researchers have a report out on DarkPower, the latest gang on the ransomware name-and-shame double-extortion scene.
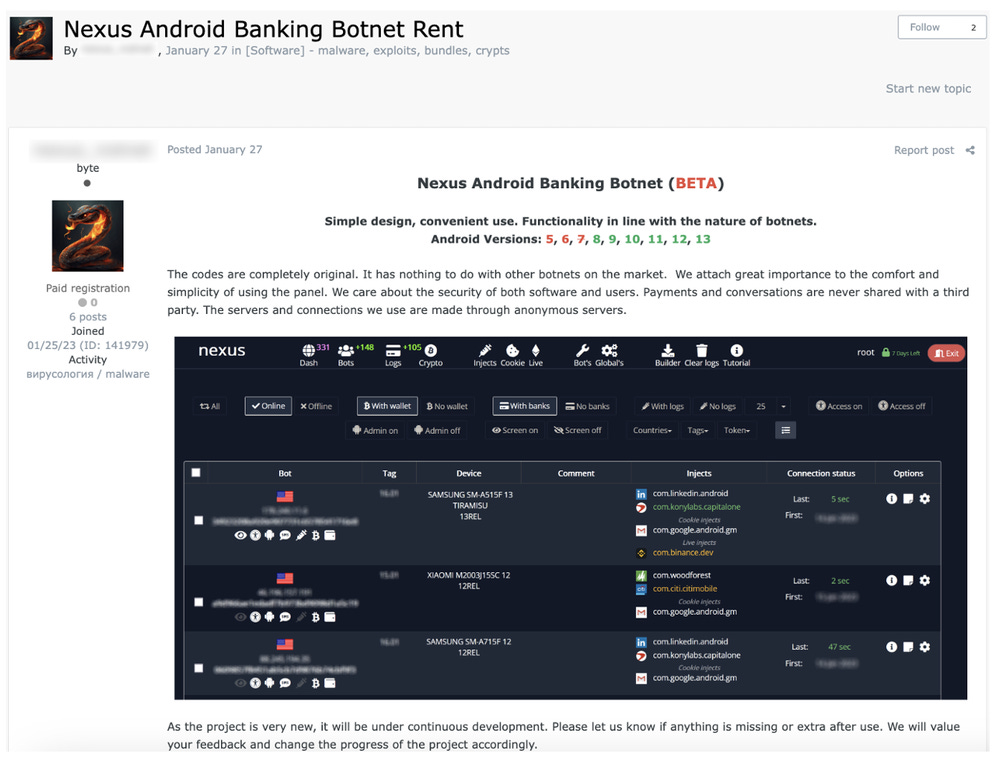
Nexus botnet: Cleafy has a report out on Nexus, a new Android banking trojan that we featured at RBN earlier this month. Cleafy says the malware is a variant of the old SOVA botnet. It also says it's been seeing it in the wild since the summer of last year. Both observations are what Dario Durando, a senior threat analyst at ThreatFabric, also told us back then:
"The malware has been quite active, specifically from August 2022, and features overlay attacks, cookie stealer and injector, keylogger, and sms/call/notification control. Before the authors claimed ownership, we were classifying the samples as a new variant of SOVA, as the code base is practically identical (with a couple of additions)."
The malware is currently being advertised for sale on Telegram cybercrime channels and underground cybercrime forums.
Sponsor Section
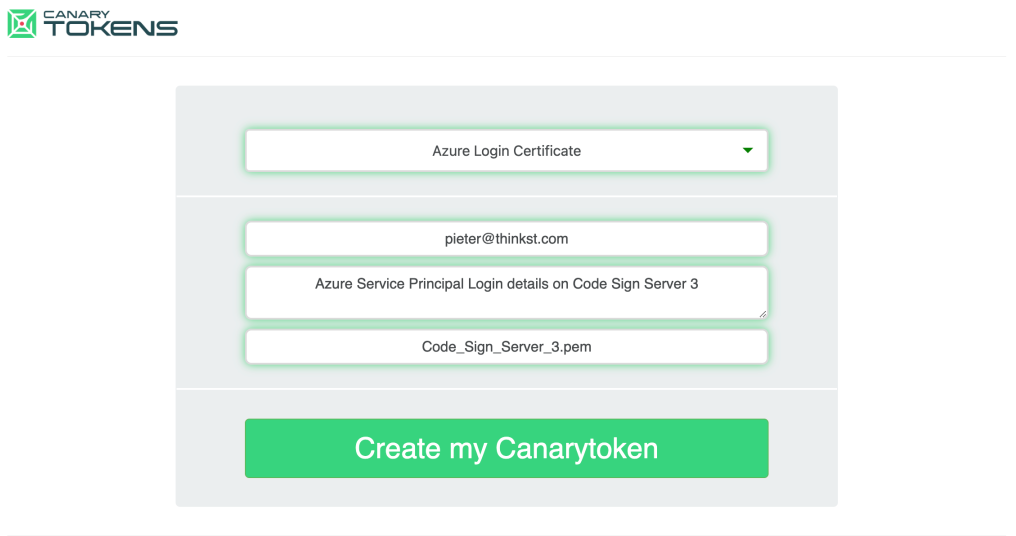
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. The company has recently launched a new type of canary token that looks like an Azure login token and warns companies whenever a threat actor tries to use them.
APTs and cyber-espionage
Earth Preata (Mustang Panda): Trend Micro has a report on the Earth Preta APT's abuse of Google Drive to host malware payloads—such as TONEINS, TONESHELL, and PUBLOAD malware.
Operation Tainted Love: A suspected Chinese cyber-espionage group has launched a fresh set of attacks against telecommunication providers in the Middle East. According to a joint report from SentinelOne and QGroup, the attacks are in their incipient phases. Researchers say the attackers use tooling associated with Operation Soft Cell—an older telco spying operation. SentinelOne named this new set of attacks Operation Tainted Love and says early clues suggest this may be the work of a threat actor known as APT41 and Gallium.
ScarCruft's Cumulus: South Korean security firm S2W has a report on ScarCruft's new Android malware—named Cumulus.
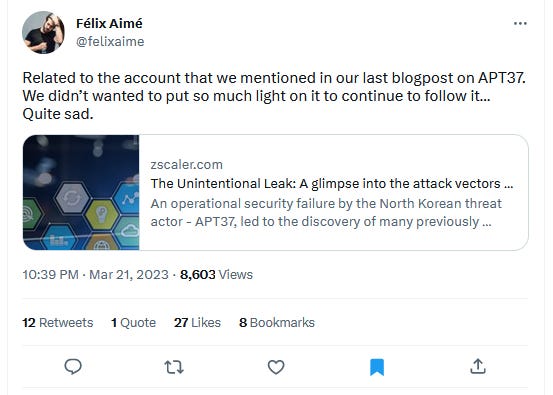
APT37 (ScarCruft, Reaper): Zscaler says it identified a GitHub repository operated by one of the members of the APT37 North Korean hacking group. The repository appears to have been used to host payloads and other files for APT37 as far back as October 2020. Zscaler says malware samples found in the repository were not previously observed anywhere else and allowed the company's researchers to gain additional insights in the group's recent operations, killchains, and targets—typically targeting South Korean individuals. Zscaler says its report complements a previous one from Sekoia. On the other hand, Sekoia researchers say they also knew about the GitHub repo as well, but they chose to intentionally leave it out of their report and monitor it for updates and insight into future APT37 ops.
Vulnerabilities and bug bounty
CVE-2023-21768 (Windows): IBM X-Force has a report out on CVE-2023-21768, an EoP vulnerability in the Ancillary Function Driver (AFD), the kernel entry point for the Winsock API. Microsoft patched the bug in January, and a PoC was released earlier this month.
Cisco security updates: Cisco has released 18 security updates for various products. Only high and medium-rated bugs in the updates this week.
Netgear Orbi bugs: Cisco Talos researchers have discovered four vulnerabilities in the Netgear Orbi mesh wireless system, including bugs in the main Orbi hub router and satellite routers that are used to extend a mesh's range. The vulnerabilities allow arbitrary code execution in both pre and post-auth scenarios. Netgear released patches in December of last year.
Timing side-channel attack on IMs: Academics have come up with a timing side-channel attack that measures the time needed to send "message delivery confirmations" in instant messaging services and determine a receiver's approximate location. IM services vulnerable to this kind of attack include the likes of WhatsApp, Signal, and Threema, according to the research team. The research team says the location detection attack works when users use WiFi and cellular connections and even when users use VPNs or Tor, although with much lower accuracy. [PDF, PDF]
"For instance, out of three locations within the same city, the sender can determine the correct one with more than 80 % accuracy. Thus, messenger users can secretly spy on each others' whereabouts when sending instant messages. As our countermeasure evaluation shows, messenger providers could effectively disable the timing side channel by randomly delaying delivery confirmations within the range of a few seconds."
Infosec industry
New tool—Untitled Goose Tool: CISA has open-sourced a new tool to help network defenders detect malicious activity in Microsoft cloud environments. Named Untitled Goose Tool, it supports Microsoft Azure, Azure Active Directory, and Microsoft 365 environments. The tool can be used to extract logs, analyze configurations, and review sign-ins and artifacts for suspicious activity.
Senderbase.org EOL: Cisco has announced plans to shut down the SenderBase email reputation service on April 20, 2023.
Pwn2Own Vancouver 2023: The Pwn2Own hacking contest—the edition targeting desktop and server technologies—is taking place in Vancouver. The most flashy hack of the first day was Synacktiv hacking the Tesla Model 3. Schedule here, and results from the first and second days are here and here.




