Risky Biz News: Feds seize BreachForums again
In other news: The Netherlands criminalizes cyber-espionage; US arrests woman running laptop farm for DPRK IT workers; major hack at Australian healthcare org.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Five days after a threat actor advertised Europol stolen data on a hacking forum, law enforcement agencies moved to seize the site.
Agencies from the US, the UK, Australia, New Zealand, Switzerland, and Iceland took down the second incarnation of BreachForums, a well-known hacking forum where threat actors went to sell, buy, and leak hacked data.
The takedown took place on May 15 and comes more than a year after authorities took down the site's first version in March 2023.
At the time of this newsletter, there is no formal announcement on the takedown, and it's unclear if any arrests took place.
Authorities took over the forum's official website and its Telegram channel. In a message left on Telegram, authorities claim they're now in possession of the site's backend database, which they plan to analyze for further criminal activity.
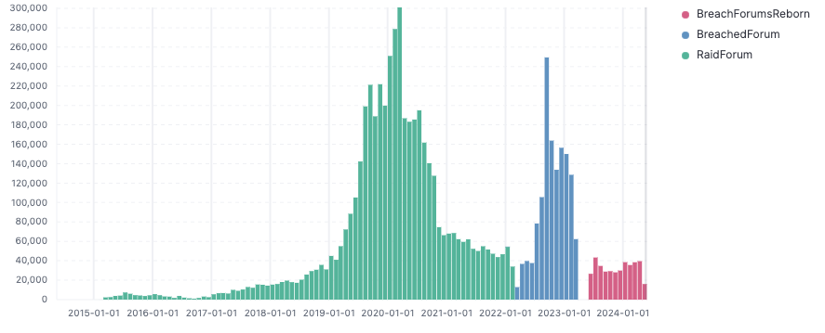
BreachForums, or Breached, has been the go-to place for most of the trades in stolen databases for almost two years, appearing as a replacement for the RAID Forum after its takedown in 2022.
The site's first version was managed by a user named Pompompurin and operated from domains like breached.vc, breached.to, and breached.co.
The site's second version was set up by ShinyHunters days after Pompompurin's arrest and ran from domains like breachforums.st, breachforums.cx, breachforums.is, and breachforums.vc.
It never reached the popularity of its first itteration, but had its fair share of major leaks announced through its threads. This includes leaks of data for large portions of Argentina and El Salvador's population, a major breach at Dell, and several leaks from various law enforcement and intelligence agencies—the latest being the leak of data from Europol's EPE portal last Friday.
Although it made for a cool lede for this newsletter, to be realistic, the timing of the takedown and the Europol leak is very likely a coincidence since takedowns typically take weeks to organize. In reality, it may be that the previous leaks of US EPA, US DOD, NATO, and Five Eyes-related data is what triggered a new response from authorities this time.
It's 2024 and you'd think that hacking forum admins should know by now that any major government and law enforcement leaks are likely to trigger a response. But, hey! What do I know. I've been covering cybersecurity for only a decade.
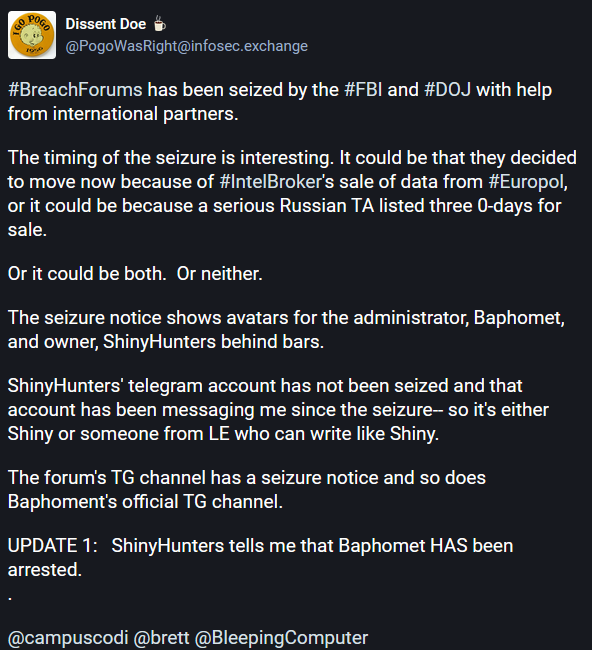
As for unconfirmed reports, according to security firm KELA and PogoWasRight, the owner of the DataBreaches.net website, authorities appear to have detained Baphomet, an individual hired by ShinyHunters for the day-to-day running of BreachForums v2.
Breaches, hacks, and security incidents
MediSecure data breach: Australian electronic prescription provider MediSecure has fallen victim to a large-scale ransomware attack. MediSecure says early evidence suggests the incident originated from one of its third-party vendors. The company says the hack impacted "the personal and health information of individuals." Until last year, MediSecure was one of the two electronic prescription providers for the Australian government and the company most likely holds data on most of the Australian population. [Additional coverage in ABC]
Iress data breach: Australian financial services provider Iress says that a threat actor gained access to its GitHub account. The company says the threat actor used credentials from one of its repositories to access the production environment of its OneVue platform. Iress says the hack took place on Monday, May 13. The company told Australian financial authorities it is investigating what data the hacker accessed. [Additional coverage in IFA]
BlockTower Captial crypto-heist: Threat actors have allegedly compromised and stolen funds from crypto investment firm BlockTower Capital. The company manages over $1.7 billion in crypto assets. BlockTower Capital is working with blockchain investigation firms to recover the assets and identify the attacker. [Additional coverage in Bloomberg]
Sonne Finance crypto-heist: A threat actor has stolen over $20 million worth of assets from the Sonne Finance cryptocurrency platform. The company has offered the attacker a reward to return the stolen funds, but there has been no reply so far. In a post-mortem, Sonne Finance described the incident as a "donation attack."
MSFT and Red Hat bloopers: Aqua Security says it found several Microsoft and Red Hat employees using official work credentials inside their personal projects. As a renowned philosopher once said—zoinks!
General tech and privacy
Meta announces Threads fact-checking: Instagram head honcho Adam Mosseri has announced that Meta's fact-checking system has now been extended to Threads.
Microsoft to enable MFA for all Azure (Portal?) users: Microsoft has announced that all Azure accounts will be required to enable multi-factor authentication from July 2024. The announcement came with no additional details and has alarmed many of the company's customers, who wonder what will happen to their service accounts and K-12 student users. The company has promised to provide more details at a later date via email and Azure Portal notifications. Several Redditors have claimed Microsoft representatives told them the enforcement will apply only to Azure Portal accounts, and not to all Azure accounts which, if true, makes this a delightful example of botched corporate comms.
DTrace will ship with Windows Server: Windows Server 2025 will ship with DTrace as a built-in tool. DTrace is a real-time debugging tool initially created for Solaris in 2003 and later ported to all major operating systems since then, primarily due to its ability to show real-time information from a system.
NetBSD bans AI code: The maintainers of the NetBSD operating system have banned project members from contributing AI-generated code. The ban covers code generated with GitHub Copilot, Meta's Code Llama, ChatGPT, and similar large language models. NetBSD described AI-generated code as tainted due to unclear copyright, and encouraged users not to submit it if they are not the sole author. The Gentoo Linux distro also banned AI-generated code last month.
"Code generated by a large language model or similar technology, such as GitHub/Microsoft's Copilot, OpenAI's ChatGPT, or Facebook/Meta's Code Llama, is presumed to be tainted code, and must not be committed without prior written approval by core."
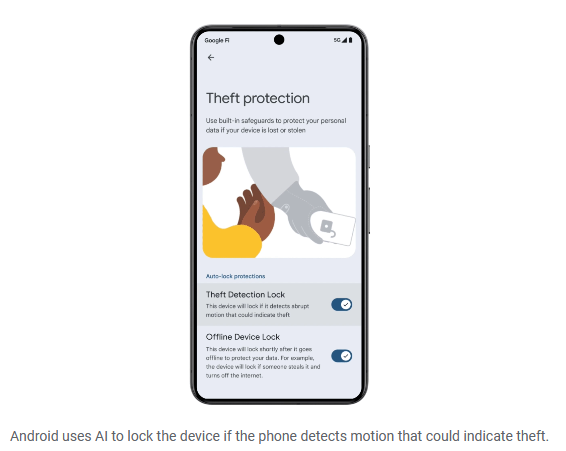
Android anti-theft feature: An upcoming Android security feature will be to detect when a user's Android phone has been stolen. The feature is named Theft Detection Lock and works by using AI to sense sudden jerks and movements—a sign a thief has snatched and is running with a user's phone. Theft Detection Lock will be available for all Android 10 and later devices through a Google Play update later this year. The new feature was announced at this year's Google I/O security conference. Here are all the 100 things Google announced at this year's I/O developer conference. Almost all of them are AI-related, including a feature that will actively listen to your conversations on the premise of detecting scams. In addition, Google is also removing one-time passcodes from Android notifications. This measure will prevent malware from intercepting and stealing OTP codes to hijack accounts. The other few security-related features are here.
Chrome 125: Google has released version 125 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release includes the new Compute Pressure API that will let websites determine a user's CPU load. Google says it developed the API together with Intel. Google has also rolled out official support for Windows ARM64 with v125, so look out for new installers. Chrome's Android version also got a Tab Declutter feature that allows users to automatically close old tabs after a certain period of time. And last but not least, Google has replaced its update mechanism, which also has a new name now.
"We are in the process of rolling out a new version of Google Update. As part of this change, the location for GoogleUpdate.exe on Windows changes and it is renamed updater.exe. Note that the previous path continues to persist until the transition is fully completed. GoogleUpdate.exe is also modified to point to updater.exe."
App Store fraud: Apple stopped more than $1.8 billion in fraudulent App Store transactions last year. The transactions originated from 3.3 million accounts and used over 14 million stolen credit cards. The company says it has now blocked over $7 billion in fraudulent transactions over the past four years. Apple says it also deactivated a whopping 374 million accounts last year for fraud and abuse.

Government, politics, and policy
The Netherlands criminalizes cyber-espionage: The Dutch House of Representatives passed legislation this week to criminalize more forms of espionage, including cyber and digital espionage. Under the new law, persons who carry out espionage for foreign governments can face up to 12 years in prison. The bill applies to Dutch citizens, but also foreign diasporas present in the country. The bill has moved to the Dutch Senate where it is expected to pass.
Russia finally gets a GitHub clone, via China: Chinese company OSChina has launched a Russian version of its Gitee code-hosting platform to serve as Russia's GitHub clone. The new platform will run at Gitee.ru and will store data in a Moscow data center. Russian officials announced plans to build a Russian GitHub alternative at the end of 2022. The project was scheduled to go live in April this year but failed after officials did not provide any funding to a local software company. Gitee launched in 2013 and has been endorsed (and censored) by the Chinese government as the country's preferred code-hosting platform. [Additional coverage in Kommersant]
NCSC Personal Internet Protection: The UK's cybersecurity agency launched a new service to protect the phones of political candidates and election officials. The new Personal Internet Protection service is a passive DNS blocklist that prevents users from accessing known malicious sites. The NCSC has been maintaining the blocklist since 2017, and has been using it to protect government agencies and major contractors. The new Personal Internet Protection service extends this capability to non-government individuals who participate in elections. The same passive DNS blocklist is also at the heart of another new NCSC service the agency launched earlier this week, named Share and Defend. The NCSC says it would work with major telcos to block known malicious sites at the provider level, extending its malware blocklist to most of the UK population.
Norway tells companies to dump SSL VPNs: Norway's cybersecurity agency has published official guidance this week recommending that companies replace SSL and web VPN solutions with more secure alternatives. The NCSC cited the high number of critical vulnerabilities in these products over the past years. The agency recommended solutions using the IPsec and IKEv2 protocols. The NCSC recommended that companies transition from SSLVPNs by the end of 2025. Organizations subject to the country's Safety Act will have to transition to alternatives by the end of the year.
New NIST guide: NIST has published new guidance for government contractors on how they can handle and protect unclassified sensitive data.
New CISA guide: CISA has published a 35-page guide for the implementation of encrypted DNS protocols.
FCC proposes BGP reporting requirements: The FCC wants the US' nine largest telcos to file confidential reports on BGP internet routing security incidents. All broadband providers will also have to report to the FCC on their progress towards implementing BGP security features. The new reporting requirement is at a proposal stage and will need to pass a vote on the FCC board. The FCC started working on the new reporting requirement in February 2022 in the aftermath of reports of Chinese and Russian telcos hijacking US internet traffic. The DOD and DOJ backed the FCC's effort to improve BGP security, seeing it as a national security threat.
OBM CISO leaves: Chris DeRusha, the OMB CISO, is leaving his position after three years. [Additional coverage in Federal News Radio]
CISA departure: CISA executive assistant director for cybersecurity Eric Goldstein is stepping down from his role at the agency next month. [Additional coverage in CyberScoop]
US 2024 election security: The Senate Intelligence Committee held a hearing with top US cybersecurity officials on the security of the upcoming 2024 US election cycle. Officials claimed the upcoming election will be the safest in history, although generative AI still poses some risk. [Additional coverage in VOA]
Sponsor section
In this Risky Business News sponsored interview, Adam Boileau talks to Okta's Cassio Sampaio about how cloud-native applications can move authorization into a centralized model. This brings real benefits for consistency, control, and auditing in distributed applications beyond just the authentication part Okta is normally known for.

Cybercrime and threat intel
MEV hackers detained: US authorities have charged and detained two brothers from New York for allegedly stealing over $25 million worth of cryptocurrency. The two suspects allegedly used exploits to steal assets from MEV (Maximum Extractable Value) bots on the Ethereum blockchain. The suspects allegedly set up shell companies, created fake wallets, and attempted to launder the stolen assets in the aftermath of the hack. US officials say the attack took months to plan and was executed in just 12 seconds. The two brothers both face up to 20 years in prison if found guilty.
LabHost-related arrests: Dutch police have detained three suspects who used the LabHost phishing platform to carry out large-scale banking fraud. Europol took down LabHost last month.
Nigerian scammer sentenced: The US has sentenced a 57-year-old Nigerian national to 5 years in prison for his role in an advance-fee fraud scheme. Officials say Uche Victor Diuno stole over $5.7 million between 2014 and 2018. Diuno worked as part of a larger gang that posed as bank executives and pitched fake investment opportunities to victims in over 20 countries.
"Acting on instructions from the scheme’s leader, Diuno directed a co-conspirator to disburse victim funds after receiving them. This included transferring funds to other bank accounts through currency exchangers and purchasing vehicles that were shipped back to scammers in Nigeria."
US unmasks DPRK IT worker scheme: The US government has charged five individuals in a money laundering scheme designed to generate revenue for North Korea's weapons program. Charges were filed against an Arizona woman, a Ukrainian man, and three North Korean nationals. The five ran a complex scheme to allow North Korean IT workers to apply for remote software development jobs inside the US. The group allegedly used the identities of over 60 US citizens to gain employment at over 300 US companies. The Arizona woman hosted a laptop farm inside her home to appear that the North Korean workers were based in the US. Together with the Ukrainian suspect, she allegedly helped launder salaries back to North Korea. Officials from the US State Department say the North Korean suspects are linked to the DPRK's Munitions Industry Department, and the scheme generated more than $6.8 million for the country's ballistic missiles and weapons program. The FBI has also published a new security advisory on the DPRK's latest tactics involving remote IT workers. The US State Department is also offering a reward of up to $5 million for information on the North Korean IT workers (including a fourth, uncharged suspect). Text in the State Department's press release suggests the program has been successful in the past, paying out at least two rewards.
"Since its inception in 1984, the [Rewards for Justice] program has paid more than $250 million to more than125 people across the globe who provided information that helped prevent terrorism, bring terrorist leaders to justice, and resolve threats to U.S. national security. Of that amount, RFJ has paid rewards of $5 million each to two individuals whose information helped disrupt an illicit financial scheme that benefitted the DPRK."

Threat/trend reports: GreyNoise, HP, KPMG, and Palo Alto Networks have recently published reports covering infosec industry threats and trends.
DocuSign campaign: Abnormal Security looks at a malspam campaign using DocuSign lures/documents to deliver various payloads.
SugarGh0st campaign: Proofpoint has published details on a malspam campaign delivering SugarGh0st, a customized version of the Gh0stRAT open-source remote access trojan.
AgentTesla campaign: ITOCHU has published a detailed report on a malspam campaign delivering the AgentTesla infostealer.
Super Friends campaign: Sonicwall researchers have looked at a malspam campaign using the PrivateLoader MaaS to deploy the Remcos RAT on infected hosts.
Crypto drainers: Blockchain research company Chainalysis has published a history of the evolution and modus operandi of crypto drainer phishing kits.
Log4j campaign: Uptycs has published details on a threat actor exploiting the Log4Shell vulnerability to install XMR miners.
Storm-1811 attacks: Last week, Rapid7 published a report on a Black Basta affiliate spam-bombing victims and then calling company employees, posing as an IT staffer, and offering to help. The attacker was tricking individuals into installing remote access software on their systems in order to access PCs, move laterally, and later install the Black Basta ransomware. Microsoft has published a report on the same attacks, and has linked the operation to a group it's tracking as Storm-1811.
Kinsing attacks: Tenable has spotted the Kinsing crypto-mining botnet launching attacks on Apache Tomcat servers.
PAN GlobalProtect exploitation: Volexity has published additional details on how to detect attacks against Palo Alto Networks GlobalProtect firewalls using a recent zero-day tracked as CVE-2024-3400. The company discovered the attacks, so it most likely knows better.
Doxbin goes down: Internet dox-sharing portal Doxbin has been offline for days. The site went down shortly after videos were published on Telegram, claiming to show a gang assaulting the site's administrator. It all may be an elaborate ruse, but the site is still down, so it's a W regardless.

Malware technical reports
ViperSoftX adopts OCR: South Korean security firm AhnLab has discovered versions of the ViperSoftX remote access trojan that used the Tesseract open-source OCR engine to scan and extract text from an infected computer's images. If the text looks like cryptocurrency addresses, seed phrases, or mentions passwords, the images are sent to the attacker's remote server.
Latrodectus: The Latrodectus MaaS, suspected to be connected to the former IcedID operation, has been spotted deploying IcedID payloads. Hmm...!
Darkgate: Forcepoint's Mayur Sewani looks at recent malspam campaigns delivering the Darkgate malware loader.
Metamorfo: On the same note, Forcepoint's Prashant Kumar has published a report on the old Metamorfo banking trojan, also known as Casbaneiro.
Black Basta ransomware: After CISA, Rapid7, and Intel-Ops shared some of their IOCs on Black Basta ransomware activity, Stairwell has now also joined the club!
Sponsor Section
In this video, Okta demonstrates how you can enforce zero standing privileges for sensitive admin access to an Okta environment with access requests and approvals.
APTs, cyber-espionage, and info-ops
Earth Hundun: Trend Micro has published part two of its report on recent operations of the Earth Hundun APT, also known as BlackTech. Part one came out last month.
Kimsuky (Springtail): Broadcom's Symantec has discovered a new Linux backdoor used in attacks by the Kimsuky/Springtail APT. Symantec says the new backdoor, named Gomir, was delivered via trojanized software installation packages. The campaign targeted organizations in South Korea. Symantec says Gomir is an evolution of GoBear, an older backdoor from the same group.
APT-C-08 (Bitter): Qihoo 360's security team has published a report on the 2023 campaigns of APT-C-08 (Manling Flower, Bitter).
Ilya Gambashidze profile: VOA has published a profile on Ilya Gambashidze, the founder of the Moscow-based company Social Design Agency (SDA). In March, the US government sanctioned Gambashidze for his role in Russia's disinformation operations in Latin America.
Neculiti brothers: German investigative journalists from Correctiv have published a profile on the Neculiti brothers, Ivan and Juri, two Moldavian nationals behind PQ Hosting and Stark Industries Solutions. Correctiv claims the company is providing server infrastructure for Russia's disinformation campaigns and many of the pro-Kremlin faketivist groups launching DDoS attacks against websites in Western democracies. Customers allegedly include Doppelganger, the RRN network, and NoName057(16).
Swedish troll farm: Swedish investigative outfit Kalla Facta has found a social media troll farm operated by the communications department of Sweden's far-right party Sweden Democrats (SD). Party members operated hundreds of accounts on TikTok, Facebook, Instagram, YouTube, and other networks, primarily for spreading misinformation and attacking opposition parties. Kalla Facta says SD also employed influencers and financed the whole thing using public tax money. [Additional coverage in TV4/English coverage in Euractiv]
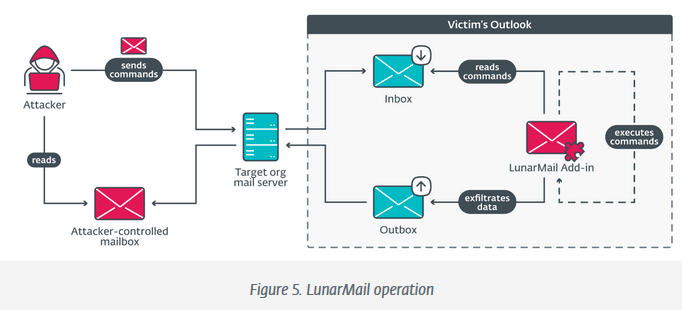
New Turla backdoors: ESET has discovered LunarWeb and LunarMail, two new backdoors the company has linked to the Turla APT. ESET says the two appear to have been used as far back as 2020. Known victims so far include a European MFA and are primarily related to its diplomatic missions in the Middle East.
"LunarWeb, deployed on servers, uses HTTP(S) for its C&C communications and mimics legitimate requests, while LunarMail, deployed on workstations, is persisted as an Outlook add-in and uses email messages for its C&C communications."
Vulnerabilities, security research, and bug bounty
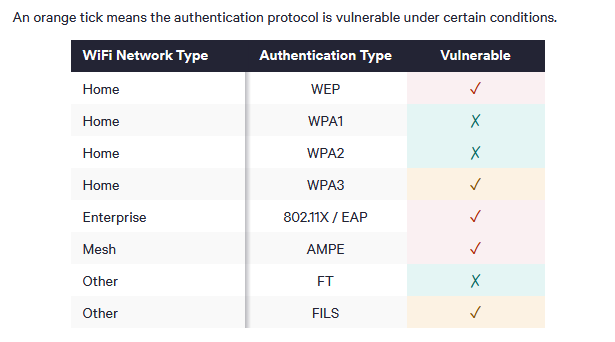
New WiFi SSID confusion attack: Security researcher Marty Vanhoef has discovered a new vulnerability (CVE-2023-52424) in the WiFi standard. The vulnerability is a WiFi SSID confusion attack. It allows threat actors to create WiFi networks with the same SSID identifier and password. If users have the auto-connect feature enabled on their WiFi, they will connect to the rogue SSID despite being a different network. WiFi clients on all major operating systems are vulnerable because they don't check the authenticity of the SSID. Enterprise and mesh WiFi networks are primarily affected and can be hijacked as long as the attacker knows their passwords. [Additional coverage in Top10VPN]
HTTP/2 CONTINUATION Flood attack: zeroBS tests show that the new HTTP/2 Continuation Flood DDoS vector is more dangerous than previously thought.
"When we compare ContinuationFlood with RapidReset, the true potential comes to light: while RapidReset was almost 8 times as powerful compared to normal HTTP/2 Multiplexing attacks, ContinuationFlood is 7 times stronger than RapidReset in terms of pure Requests per Second (RPS) per bot."
D-Link PoC: SSD researchers have published a write-up and PoC for a vulnerability in D-Link DIR-X4860 routers. Let the attacks begin!
"Security vulnerabilities in DIR-X4860 allow remote unauthenticated attackers that can access the HNAP port to gain elevated privileges and run commands as root. By combining an authentication bypass with command execution the device can be completely compromised."
Cisco security updates: Cisco has released or updated eight security advisories for various products.
Python LLM library vulnerability: Checkmarx researchers look at CVE-2024-34359, a vulnerability in the llama_cpp_python Python package. The vulnerability abuses the built-in Jinja2 template engine to run malicious code on AI apps using the library.
ThroughTek platform vulnerabilities: Bitdefender researchers have identified four vulnerabilities in the ThroughTek Kalay IoT platform. The platform and its SDK are used in more than 100 million smart devices. The vulnerabilities allow for unauthorized root access from within the local network and for remote code execution attacks. Devices that use the ThroughTek Kalay platform include the Wyze Cam, the Roku Indoor Camera, and the Owlet Cam. ThroughTek released patches for all reported issues in April this year.
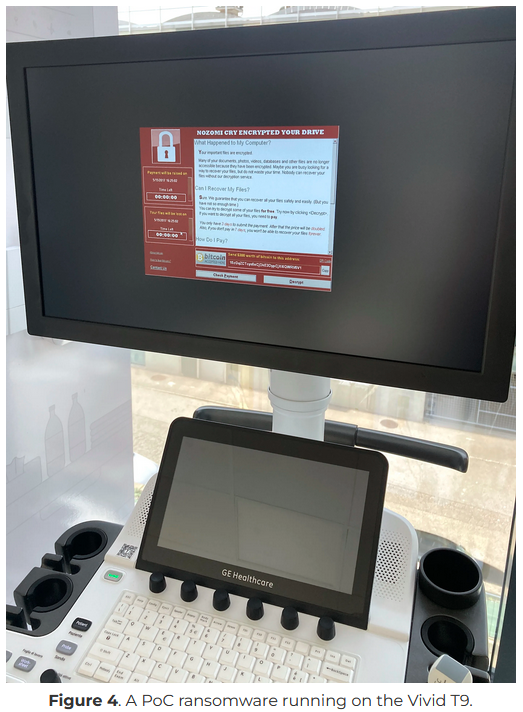
GE HealthCare Vivid Ultrasound: Nozomi Networks has discovered 11 vulnerabilities in GE HealthCare Vivid Ultrasound products.
"The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the access and manipulation of patient data stored on the vulnerable devices."
Secret ServiceNow vulnerability: Security firm Assetnote says it found a critical vulnerability in one of ServiceNow's APIs. ServiceNow is allegedly working on a fix, and Assetnote promised to share more details 30 days after a patch.
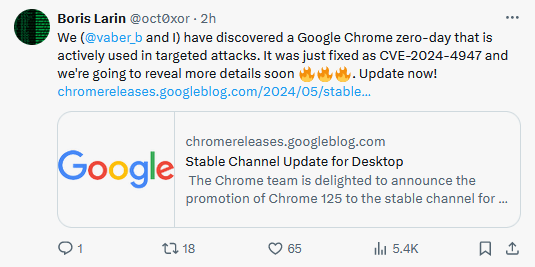
Third Chrome zero-day in a week: Google has released an update for its Chrome browser to fix a zero-day (CVE-2024-4947) exploited in the wild. The zero-day is a vulnerability in Chrome's V8 JavaScript engine and was discovered by Vasily Berdnikov and Boris Larin from Russian security firm Kaspersky. The two researchers say the zero-day was used in targeted attacks. This is the third Chrome zero-day patched over the past week, and Google's seventh Chrome zero-day this year.
Infosec industry
Merger news: Two of the infosec's industry's biggest SIEM providers, LogRythom and Exabeam, have announced their merger.
Acquisition news: Palo Alto Networks has agreed to acquire a large chunk of cybersecurity assets from tech giant IBM. Copy-pasting from the press release below and an analysis of the acquisition is available via CNBC.
- Palo Alto Networks has agreed to acquire IBM's QRadar Software as a Service (SaaS) assets, and the two companies will partner to offer seamless migration for QRadar customers to Cortex XSIAM.
- IBM will train more than 1,000 of its security consultants on migration, adoption and deployment of Palo Alto Networks products.
- IBM will bolster its leading security services to drive a significant book of business in cybersecurity and AI security, featuring Palo Alto Networks platforms in its expanded portfolio.
- IBM to platformize internal security solutions with Palo Alto Networks; Palo Alto Networks will be its preferred cybersecurity partner across network, cloud and SOC.
- IBM will accelerate innovation and investment in data security and identity and access management for hybrid cloud and AI; will partner with Palo Alto Networks on security operations, threat management, and DevSecOps.
New tool—snap_wtf_macos: Cisco Talos has open-sourced snap_wtf_macos, a new fuzzer for macOS code.
New tool—Sasori: Astra Security's Karthik UJ has released Sasori, a dynamic web crawler to automate the crawling of web applications, even those behind authentication.
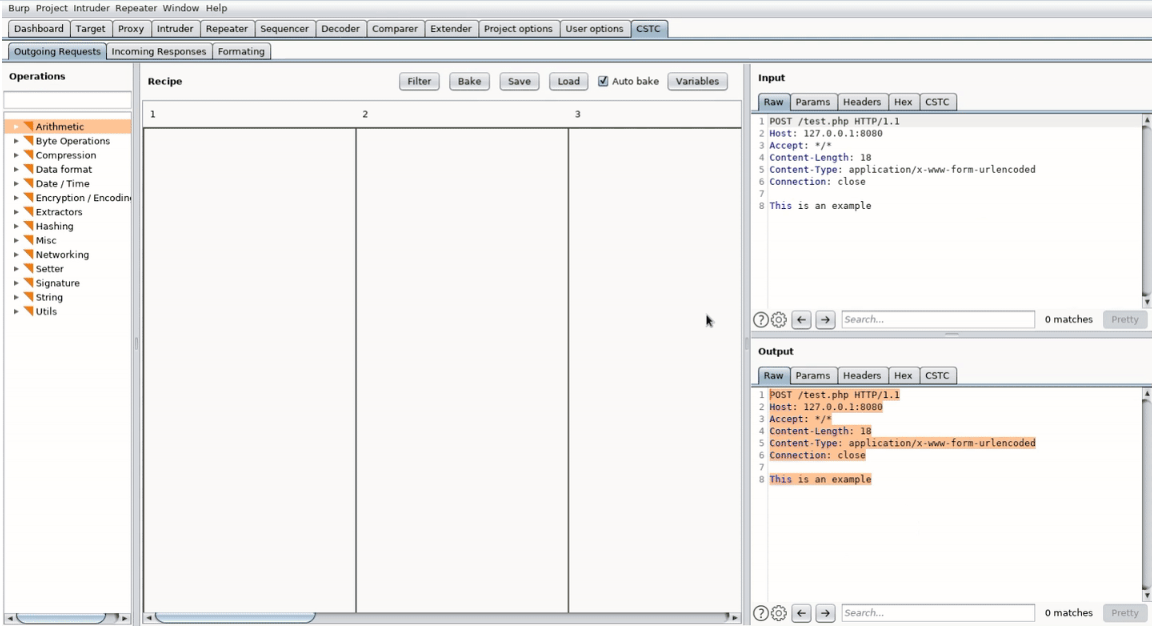
New tool—CSTC: German security firm usd has released CSTC (Cyber Security Transformation Chef), a Burp Suite extension that allows request/response modification using a GUI similar to CyberChef.
Risky Business Podcasts
The regular two nerds have the week off, but the former Director of the CIA's Center for Cyber Intelligence Andy Boyd joins Patrick Gray for a rollicking conversation in front of a live audience in San Francisco. Grugq and Tom return next week!




