Risky Biz News: China says the US is framing other countries for espionage operations
In other news: New UK NCSC service will protect schools from cyberattacks; Time-To-Exploit goes down to only five days; Telegram takes down pay-to-nudify bots.

This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Chinese government has put out another report of questionable quality this week, claiming that the US is trying to smear poor lil' China as a bad cyber actor.
Beijing officials say that the US is actually the country behind most cyber espionage operations today, and they possess a "cyber weapon" that can mislead investigators and frame other states for its intrusions.
The report [English PDF] is the third in a series of reports that China's National Computer Virus Emergency Response Center (CVERC) has published on the topic this year, after previous reports in April and July.
The reports typically come out after the US government and US media expose new Chinese cyber-espionage operations in the US. This one came out days after US officials claimed that Chinese hackers breached sensitive systems at US telcos used for law enforcement wiretaps—basically, China wiretapped the US wiretapping system.
This third report claims that US attribution of cyberattacks cannot be trusted because the US has a tool name "Marble" (exposed in the Snowden leaks) that can be used to cover up tracks and plant false flags. Chinese officials say the US has been using this tool to frame China as a cyber aggressor and that it cannot be trusted.
Leaning extremely heavily on the old Snowden leaks, they claim that the US is actually the country doing more cyber espionage, including against its allies—which is also why this report has been made available in other languages beyond Chinese for the first time, namely German, French, and Japanese, which are all allies the US has spied on, based on the Snowden files.
For context, the first CVERC report claimed the US got its attribution wrong in regard to a Chinese APT named Volt Typhoon. The report claimed that Volt Typhoon is a mere ransomware group. CVERC based its conclusion based on some code similarities between the APT tools' and similar tools used by the Dark Power ransomware.
The second report went a little bit more political, and CVERC argued that Volt Typhoon is a fabrication of US cybersecurity agencies as part of a grand plan to request higher budgets from Congress and "defraud" the American public.
Old dog, old trick
The Chinese government has been doing this dance for more than two years now. Risky Business first noticed this trend in 2022 when we saw numerous statements from Chinese officials throwing tantrums that effectively boiled down to "US is bigger hacker than China" and "US is trying to smear China" every time the US and its allies would expose a major Chinese operation.
They'd release statements, sometimes they put out a technical report together with local cybersecurity firms, and then have state media and social media bots amplify their findings and use the reports as proof that officials are right.
But as we pointed out in 2022, and SentinelOne did in its own investigation in February this year, the reports are technical mumbo jumbo.
Most of them just re-use the decade-old Snowden and Vault7 leaks, where Chinese officials take small pieces and fit them together to create a narrative they want to convey.
We have no doubts the US is spying on both China and even its own allies, but that's how intelligence agencies have operated and will continue to operate. That's also why China itself has been hacking its own allies as well. Our problem is the sheer lack of actual evidence in the Chinese reports.
When the US and its allies attribute an operation to a Chinese APT group, they release malware samples, indicators of compromise, and even take out vast botnets and server infrastructure.
When China does it, they just hotlink to the decade-old Snowden and Vault7 leaks, share no IOCs, and no actual malware.
US reports are written by and for people with vast technical knowledge, while Chinese reports appear to be written by QAnon conspiracy theorists hand-picking the information that fits today's desired narrative.
Is the US carrying false flag cyber operations? Most likely, yes. Is Volt Typhoon and its other Typhoon ilk a US false flag? Definitely no!
These reports and press releases are just your typical corporate PR damage control strategy but scaled up and adapted for international politics and diplomacy topics.
Breaches, hacks, and security incidents
Ticketmaster class-action: Ticketmaster is facing a class-action lawsuit for a May 2024 data breach that exposed the personal details of 560 million ticket buyers. [Additional coverage in The Hollywood Reporter]
Central Tickets data breach: UK theater ticketing platform Central Tickets says it suffered a security breach after hackers stole one of its databases. The breach took place in July but was only discovered in September. Central Tickets learned of the breach after a tip from the London Metropolitan Police, which spotted chatter on the dark web about the company's user data. [Additional coverage in the Manchester Evening News]
Cisco investigates breach: Threat actors claim to have breached Cisco and are selling the stolen data on an underground hacking forum. The data allegedly contains source code, confidential documents, API tokens, and public and private keys for Cisco and its customers' infrastructure. The threat actor claims the breach indirectly impacts companies such as AT&T, Verizon, Microsoft, and SAP. The breach allegedly took place on October 6. Cisco told Bleeping Computer it is still investigating the claims and is not ready to confirm a security breach.

General tech and privacy
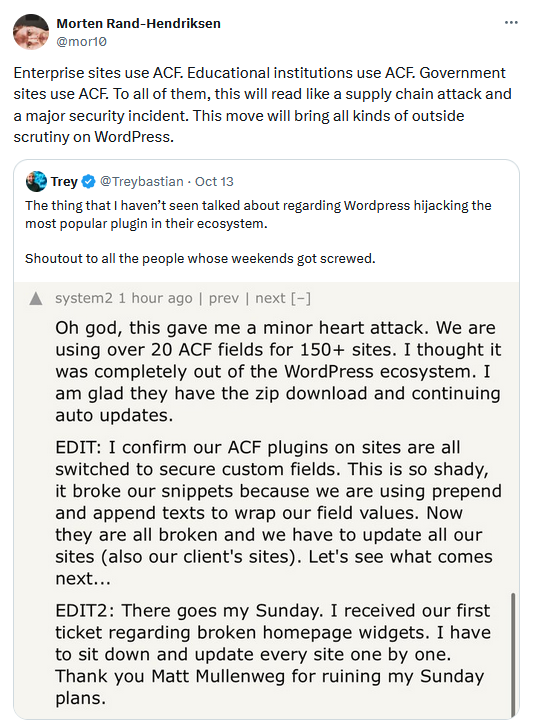
More WordPress drama: The WordPress team is manually reviewing and deleting comments that point out how its staff hijacked one of the platform's most popular plugins just because it was being managed by a competitor for Automattic's commercial side, WordPress.com.
Passkeys migration: The FIDO Alliance has published a new specification for a new technology that will allow users to easily move passkeys between platforms and providers.
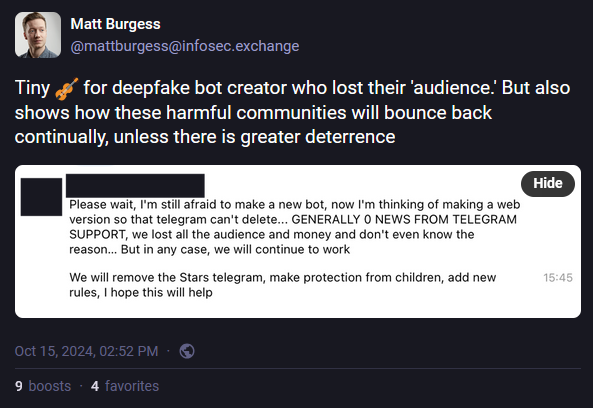
Telegram takes down "nudify" bots: Telegram has taken down over 50 bots that used deepfake technology to "nudify" images and videos. Almost all of the bots provided the service under a paid model. The bots had a total following of over 4 million users, and two accounts had more than 400,000 followers each. Telegram took down the bots after a WIRED investigation. The company has been under investigation in both South Korea and the Netherlands for allowing such services to operate undisturbed on its platform for years.
Government, politics, and policy
Russia creates Telegram searcher: A Russian company has created a tool for the Russian government to search and identify Telegram channels hosting "prohibited materials." Officials say they plan to use the tool to detect channels used to recruit Russian citizens for sabotage actions. The tool can also identify automated Telegram bots, which can also be used for the same thing. [Additional coverage in Ridus]
CN-IR-RU-DPRK cooperation: A research paper from Carnegie Melon University looks at the recent "cyber" cooperation between the US' main foreign adversaries, China, Russia, Iran, and North Korea.
NCSC service to protect schools from cyberattacks: The UK's cybersecurity agency has launched a new cybersecurity service to protect schools from ransomware, phishing, and other online threats. The service is named the Protective Domain Name System (PDNS) and works as a DNS traffic security filter. The NCSC rolled out PDNS for schools earlier this year but it's now making the service available for all the education sector, such as academies, private schools, and school internet service providers. The service will be available for free for any institution that signs up.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Dan Guido, CEO of Trail of Bits, about post-quantum cryptography. The pair dive into what it is, why it is needed now, and how organizations are dealing with its adoption.
Cybercrime and threat intel
Sipulitie takedown: Finnish and Swedish authorities seized the servers of the Sipulitie dark web marketplace. The marketplace launched in February 2023 and was primarily used for the anonymous sale of narcotics across Scandinavia. Officials say the Sipulitie admin also managed two other defunct dark web marketplaces known as Sipulimarket and Tsätti. He is believed to have made millions of euros from running the sites.
Smishing suspects detained: Dutch police have arrested two suspects for sending more than 150,000 SMS messages posing as the Dutch tax authority. Officials say the two were stealing thousands of euros per day with their scheme. The suspects were arrested in the city of Utrecht. Dutch police identified the suspects after a company filed a complaint that one of their ex-employees ordered a large batch of SIM cards in their name.
Water Makara: Trend Micro has published a report on Water Makara, a cybercrime group that's targeting Brazilians with a version of the Astaroth banking trojan.
Cloud security guide: The Israeli government has published a guide on how companies can secure their cloud servers against ransomware attacks. The guide is currently only available in Hebrew.
"Entry points" repo attacks: Security firm Checkmarx says that entry points in open-source libraries and packages can be abused for supply chain attacks. Entry points are mechanisms designed to extend packages through plugins or run command-line scripts. Checkmarx says the design of entry points allows threat actors to hide malicious commands in a location most security scanners aren't configured to check. Researchers say package repositories across multiple programming languages are vulnerable to this new type of attack. This includes popular languages such as Python, JavaScript, Ruby, and Rust.
Ukraine fake bomb threat wave linked to Russia: The Ukrainian National Police says that Russian intelligence services are behind a wave of fake bomb threats made across Ukraine. Ukrainian government institutions received more than 2,000 bomb threats via email on Monday, October 14. Police officials say that after responding to the calls, all turned out to be fake, and most were made from Russian IP addresses.
QR parking scam reaches Ireland: The malicious QR code stuck on top of the real QR code on parking meters has now reached Ireland. Expect this to plague your daily life for the next decade.

Malware technical reports
Horus Protector: SonicWall's security team has published part two of its report on Horus Protector, a new crypting service advertised in underground cybercrime circles. Part one is here.
SocGolish: DomainTools has put out a report looking at a SocGolish watering hole attack deployed on the website of a US-based apartment building's website and designed to deliver malware by spoofing a fake browser update.
EDRSilencer: Trend Micro reports malicious use of a red team tool named EDRSilencer. As the name implies, the tool disables EDR security solutions.
Sponsor Section
You might be hearing a lot about post-quantum (PQ) cryptography lately, and it's easy to wonder why it's such a big deal when nobody has actually seen a quantum computer. But even if a quantum computer is never built, new PQ standards are safer, more resilient, and more flexible than their classical counterparts. More from Trail of Bits here.

APTs, cyber-espionage, and info-ops
SideWinder: Kaspersky has published an overview of the evolution of SideWinder (Rattlesnake), a suspected Indian cyber-espionage group. The report also covers the group's latest tool, StealerBot, a post-exploitation toolkit and spyware component.
PipeMagic: Kaspersky says it discovered new attacks with a Rust-based backdoor named PipeMagic. The malware was first seen in 2022 and used in campaigns targeting Asian companies. Kaspersky says the new attacks targeted Saudi Arabia.
UAC-0050: A suspected Russian threat actor tracked UAC-0050 is secretly behind a public persona known as Fire Cells Group, linked to bomb threats, contract killings, and damage to property across Ukraine. Ukrainian officials say the group has been active hacking Ukrainian organizations since the start of the war but has only recently switched to PSYOPs. The group typically targets Ukrainian government entities but has also recently switched to stealing money from hacked private companies.
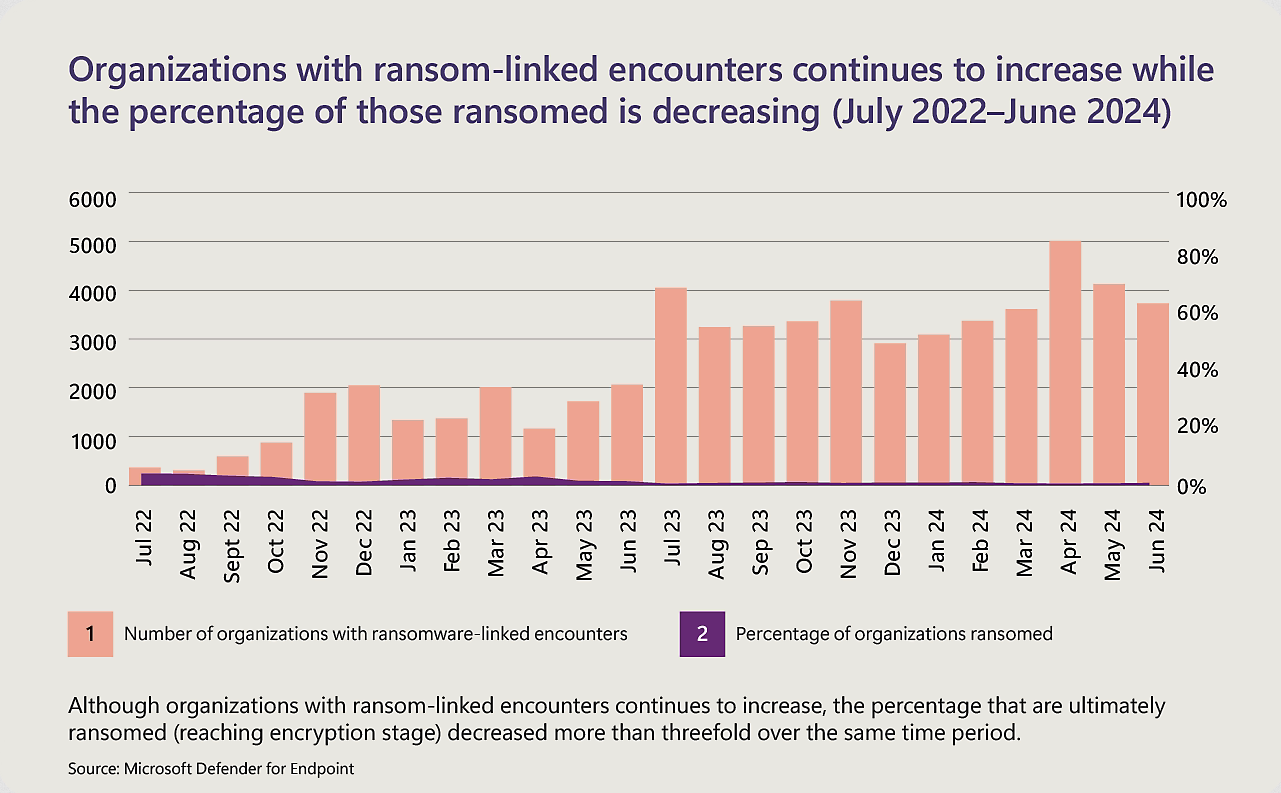
APTs increasingly enlist cybercriminals: China, Russia, and Iran are increasingly enlisting cybercrime groups or their tools in espionage operations, according to a report on digital threats published Tuesday by Microsoft. The report also found that state-sponsored activity is now heavily concentrated around sites of active military conflict or regional tensions. This includes locations such as Ukraine, Israel, Taiwan, and the Middle East. Microsoft says ransomware attacks have increased by almost three times compared to last year, but there was a threefold decrease in ransom attacks reaching the encryption stage. On the other hand, tech support scams have seen a resurgence, with a 400% increase since 2022.
Vulnerabilities, security research, and bug bounty
Jetpack security update: Automattic has released a security update for the Jetpack WordPress plugin.
"During an internal security audit, we found a vulnerability with the Contact Form feature in Jetpack ever since version 3.9.9, released in 2016. This vulnerability could be used by any logged in users on a site to read forms submitted by visitors on the site."
Bitwarden audit: French security firm Synacktiv and Germany's BSI agency have published security audits of password manager Bitwarden server (known as Vaultwarden).
"Bitwarden is a robust password manager with self-hosting capabilities. An attacker gaining high privileges on the Bitwarden server does not immediately gain access to all the corporate secrets. On the other hand, an uninvited guest exfiltrating the backup database exposes the company to data leaks. Precisely, all the employees' names and email addresses, company business emails addresses, premium license keys, API keys, IP addresses and 2FA tokens."
Aspro exploitation: Threat actors have exploited a vulnerability in the Aspro e-commerce platform to take over online stores since August this year. The Aspro platform is an e-commerce module for the Bitrix CMS and is primarily used across the old Soviet space. The attacks were detected by the security team of Belorussian hosting provider Hoster. The company says that Aspro has since deployed an update to fix the exploited vulnerability.
Tor Project backtracks on zero-day: The Tor Project has updated a blog post where it stated that a recent Firefox zero-day was used against Tor Browser users. The Project says it has no evidence that the Firefox zero-day was used "specifically" to target Tor Browser users.
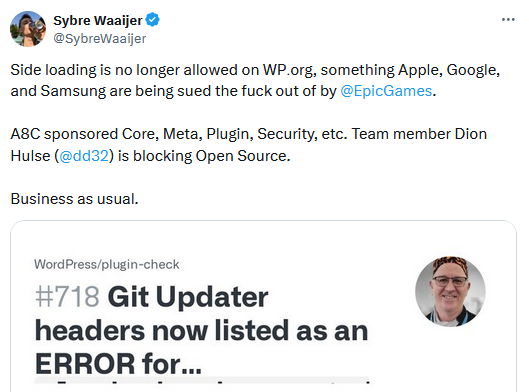
WordPress blogs non-repo updates: The WordPress team has blocked and then reverted the ability for WordPress plugins listed on WordPress.org to be updated from non-WP.org sources, such as GitHub or Bitbucket.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. This includes the recent Firefox zero-day and two bugs from earlier this year in SolarWinds Web Help Desk and the Windows kernel.
Splunk security updates: Cisco has released 12 security updates for its Splunk SIEM—including one for an RCE.
Netgear vulnerabilities: The Concordia University Security Research Centre in Canada has found five vulnerabilities in Netgear routers and WiFi extenders. All five are patched.
Fortinet RCE: watchTowr Labs has published an analysis of CVE-2024-23113, a Fortinet RCE from earlier this year that was added by CISA to the list of actively-exploited bugs last week.
Early Cascade Injection: Outflank researcher Guido Miggelenbrink has published details on a new process injection technique called Early Cascade Injection.
"This new Early Cascade Injection technique targets the user-mode part of process creation and combines elements of the well-known Early Bird APC Injection technique with the recently published EDR-Preloading technique by Marcus Hutchins. Unlike Early Bird APC Injection, this new technique avoids queuing cross-process Asynchronous Procedure Calls (APCs), while having minimal remote process interaction. This makes Early Cascade Injection a stealthy process injection technique that is effective against top tier EDRs while avoiding detection."
CounterSEVeillance and TDXdown attacks: Two teams of academics have published details on two new attacks that can break the confidentiality of CPU trusted execution environments (TEEs). The attacks allow threat actors to recover sensitive data from sections of a CPU that have been designed to protect important data. The first attack is named CounterSEVeillance [PDF] and can recover data from AMD's Secure Encrypted Virtualization (SEV) TEE. The second attack is named TDXdown and impacts Intel's newest TEE technology, the Trust Domain Extensions (TDX). Both technologies are commonly used in cloud computing and virtual machine technologies. AMD has published guidance on how to deal with the attack, while Intel released firmware patches. [Additional coverage in SecurityWeek]
Android memory safety vulnerabilities go down: Google says it fixed 36 memory safety vulnerabilities in the Android mobile operating system this year, down from over 2020 it fixed five years ago, in 2019. The company credited the decrease on its decision to adopt memory-safe languages for the Android source code. The biggest role was Rust, which is now used in Android's firmware, networking, and graphics components.
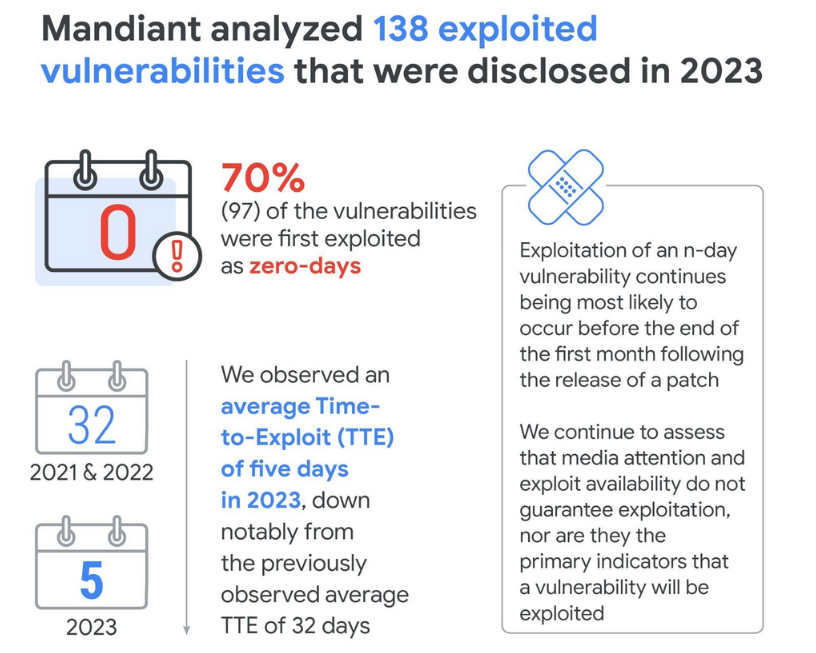
Time-To-Exploit goes down: The exploitation of software bugs is now taking place at a faster pace than it ever did before. Google says that the time-to-exploit (TTE) has gone down to only 5 days compared to 63 days in 2018. The largest drop in time-to-exploit was recorded last year when the TTE went down from 32 days in 2022 to only 5 days.
Infosec industry
Acquisition news: Maritime IT service provider Marlink has acquired Port-IT to bolster its cybersecurity division.
New tool—Voidmaw: Romanian security researcher Paul Șocațiu has released Voidmaw, a tool to bypass memory scanners.
Threat/trend reports: Kaspersky, Mandiant, Marlink, Microsoft, Portnox, S2W, Secure Code Warrior, Trellix, VulnCheck, and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how criminals are using deepfakes… but it is not the end of the world.
In this podcast, Tom Uren and Adam Boileau talk about a new UN report that spells out the role Telegram plays as a massive enabler for transnational organized crime. They also discuss China's hacking of US telcos to possibly target lawful intercept equipment and a remarkably entertaining account of North Korean IT workers being employed by over a dozen cryptocurrency firms.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




