Risky Biz News: China says Taiwan's military is behind a hacktivist group
In other news: Microsoft names 13 Deputy CISOs; Kaspersky AV force-replaces itself in the US; Telegram says it will collaborate with law enforcement.

This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

China's main intelligence agency on Monday accused Taiwan of running an influence operation inside its borders using a fake hacktivist group named Anonymous 64.
China's Ministry of State Security says the group is run by a cyber warfare center operating under Taiwan's military, inside its Information, Communications, and Electronic Force Command (ICEFCOM).
"The center is responsible for implementing cyber cognitive warfare and public opinion warfare against the Mainland," officials wrote in a WeChat post.
MSS officials claim Taiwan operatives infiltrated China's national internet and hacked public websites, billboards, and streaming platforms to post disinformation about the Chinese government and its leadership.
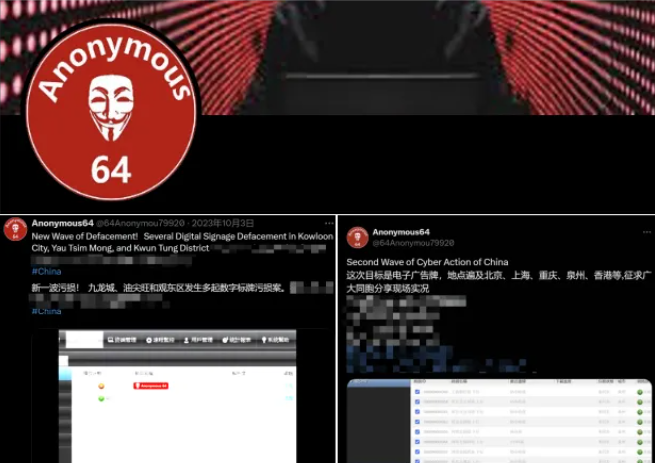
The MSS says the group has conducted more than 70 campaigns since it was created in June of last year.
Most of its attacks targeted "zombie" government websites that hadn't been updated for years. It also breached internet forums at 40 Chinese universities.
The MSS claims the Anonymous 64 group was run by three Taiwanese active-duty military personnel named Luo Junming (left), Hong Liqi (center), and Liao Weilun (right).
Taiwanese officials denied the accusations and said ICEFCOM's role is to perform security maintenance for the military's online networks.

Breaches, hacks, and security incidents
Trump hack continued: New evidence suggests the Iranian hack of Donald Trump's campaign continued through the month of September. The Popular Information newsletter claims it received the same leaked files that were sent to Politico and the New York Times in June, but also new documents dated this month. This includes a letter from Donald Trump's legal team addressed to the New York Times dated September 15. The Justice Department is expected to file charges against the hackers this week. [Additional coverage in Semafor]
MC2 Data leak: Background check service MC2 Data has left exposed a database server containing the personal details of over 100 million individuals. Infosec news outlet CyberNews says the database contains extremely sensitive information, ranging from names to property records, employment details, and legal documents. A few thoughts from the incomparable DataBreaches.net:
"Unfortunately, they fail to clearly report when they discovered the leak, whether or when they contacted the entity to alert them to the leak, and whether and how the entity responded. Has this leak been secured? One certainly hopes so but their headline says the info is now public — as in still publicly available? One hopes not."
Arkansas City ransomware attack: The City of Arkansas City says that drinking water is safe to drink in the city after a cyberattack on Sunday forced its water utility to manual operation. [Additional coverage in KWCH]
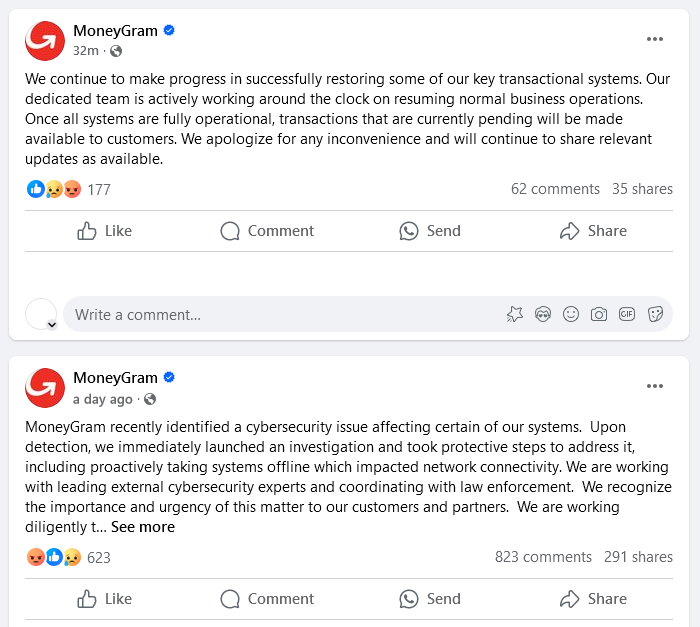
MoneyGram cyberattack: Money transfer service MoneyGram says that a cybersecurity incident is behind a widespread outage of its services. The incident took place last week on September 20 and is still ongoing. The company's website and apps are inaccessible, and users have been unable to access their accounts. It's unclear if any customer data was compromised in the incident. MoneyGram is the world's second-largest money transfer company. [Additional coverage in SecurityWeek]
General tech and privacy
QNAP air-gapped backups: QNAP has added a new feature to its NAS devices to create air-gapped backups. It's not actually air-gapped. It just uses a special router that connects the NAS device to the network only during the backup process.
LinkedIn won't train AI on EU users: LinkedIn says it won't train its generative AI features using the data of EU, UK, and Swiss users. The company's announcement comes ahead of regulatory actions in Europe. Reporters found that LinkedIn had enabled a feature by default on all users' profiles granting itself permission to train its AI using their content. The new feature and AI scrapping were also not included in the company's user agreement and privacy policies.
Flibust shuts down: Russia's largest e-book piracy portal, Flibust, is shutting down after its admin claimed to have been diagnosed with brain cancer.
Telegram gives in to law enforcement: Russian instant messaging service Telegram says it will share phone numbers and IP addresses with law enforcement if a user is the subject of a criminal investigation. The company updated its privacy policy on Monday, almost a month after its CEO was arrested in Paris at the end of August. French authorities accused Pavel Durov of turning a blind eye to the criminal activity happening on the platform. [Additional coverage in The Verge]
Government, politics, and policy
SLCGP funding: The US Department of Homeland Security is offering almost $280 million in grant funding to state and local cybersecurity programs.
US foreign cyber aid: The US government is preparing foreign aid of up to $35 million to help allies boost their cyber defenses. [Additional coverage in The Record]
US plans more spyware crackdowns: The US government says it intends to sanction more spyware vendors later this year. The new sanctions are expected after the State Department holds its first-ever commercial spyware-focused Human Rights Council side event on October 8. The US Commerce Department is expected to add new spyware makers to its banned entity list.
US bans Russian and Chinese car hardware and software: In our last edition, we had an item about the US preparing a ban on the import of hardware and software used in smart and internet-connected cars that is from or may be linked to China, Russia, and other foreign US adversary. That ban is now live.
UK is recruiting cyber workers: UK Defence Secretary John Healey says the Armed Forces has initiated a fast-track program to recruit IT experts for its cyber defense forces. [Additional coverage in Forces News]
EU not considering a Telegram ban: The European Commission has told Russian news outlet Izvestia that it has no plans to block Telegram on its territory.
Sweden blames IRGC over cyberattack: Swedish officials have blamed Iran for hacking a local SMS service and sending over 15,000 text messages encouraging revenge over the burning of the Quran. The incident took place in 2023, and Sweden's intelligence agency has linked the attack to one of IRGC's cyber units. The country's general prosecutor claims it also identified the Iranian hackers involved in the intrusion.
Montenegro replaces hacked portal: The government of Montenegro will launch a new citizen data portal two years after the first one was hacked by the Cuba ransomware group. [Additional coverage in BalkanInsight] [h/t DataBreaches.net]
Russia adds prison time to internet insults: The Russian government is updating one of its laws to add prison sentences to individuals who criticize and insult public officials on the internet. Offenders risk fines of up to 80,000 rubles (~$860), community work of up to 460 hours, forced labor for up to two years, or prison time for up to two years. [Additional coverage in TASS]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely co-founder and CEO Travis McPeak about some of the hard and uncomfortable truths about the role of security teams inside a company.

Cybercrime and threat intel
Smishing ring arrests: South Korean police have arrested seven individuals suspected of being members of a Vietnam-based smishing group. The suspects were detained at the request of Vietnamese authorities, and six have been repatriated to face charges for their crimes. The group is believed to have made more than $7.5 million from smishing and various text message scams. [Additional coverage in Yonhap News]
Dark web data trader sentenced: A US judge has sentenced a Nigerian national to five years in prison without parole for selling stolen financial information on the dark web. Simon Kaura used multiple hacker aliases and even created and managed his own carding forum. One of Kaura's partners, a Texas man, pleaded guilty and was sentenced to 18 months in prison without parole in January. Officials say Kaura and his co-conspirators made over $4.5 million from selling stolen card data.
DDoS attacks on Austria: Two pro-Kremlin faketivist groups named NoName057(16) and OverFlame are engaging in a series of DDoS attacks targeting Austrian government sites, airports, and financial services. [Additional coverage in Radware's threat alert]
DPRK IT workers: Google says several major US companies have unknowingly hired North Korean IT workers. The workers applied and got hired for remote IT jobs or as remote contractors, and some workers were employed at multiple companies. The workers were assigned work laptops that they hosted at laptop farms in the US, where they logged in with remote access tools and VPNs. Google says the workers avoided video calls, provided below-average quality work, and often requested laptops at addresses different from their provided ID documents.
"Another common characteristic identified across Mandiant's engagements was that DPRK IT workers typically claimed to live in one location, but requested laptop shipment to another location (laptop farm or outside enablement entity). We have observed the DPRK IT workers using the location associated with the stolen identity used for employment, including the stolen driver's license, which often doesn't match the location where the laptop is ultimately shipped and stored."
HR phishing: Cofense looks at a recent phishing campaign leveraging HR-related themes.
ClickFix campaign: Proofpoint has identified a new ClickFix copy-pasta campaign targeting transportation and logistics companies in North America.
New crypto-mining campaign: DataDog has a report on a new crypto-mining campaign targeting exposed Docker APIs and then moving laterally to Docker Swarm, Kubernetes, and SSH servers.
WhiteSnake interview: Threat intelligence analyst g0njxa has published an interview with the developer of the WhiteSnake infostealer.
Malware technical reports
SnipBot: Palo Alto Networks has discovered a new version of the RomCom malware family named SnipBot. RomCom has been used extensively in Ukraine, and the first SnipBot sample was also uploaded to VirusTotal from Ukraine at the end of last year.
"SnipBot gives the attacker the ability to execute commands and download additional modules onto a victim's system. It is a new version of the RomCom malware that is mainly based on RomCom 3.0. However, it also contains techniques seen in its offshoot PEAPOD called RomCom 4.0 by Trend Micro. Therefore, we've assigned it version 5.0."
Kryptina RaaS: SentinelOne looks at the latest ransomware operation to launch on the cybercrime underground—the Kryptina RaaS. According to the company, the service is apparently managed by a former affiliate of the Mallox (TargetCompany) RaaS.
Kransom ransomware: ANY.RUN has published a report on a new ransomware strain named Kransom.
Necro: Kaspersky says that over 11 million Android users are currently infected with a version of the Necro Android trojan. The malware's latest version was distributed via malicious SDKs embedded in legitimate apps, including through apps hosted on the official Google Play Store. The SDK deploys Necro on an Android device, and then Necro can install various payloads depending on the victim's profile. The malware includes modules for ad fraud, SMS subscription fraud, and proxyware.
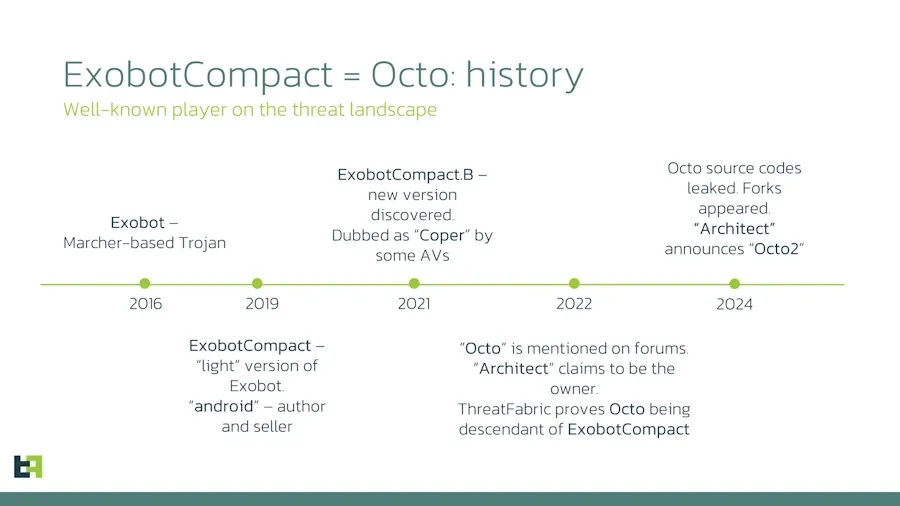
Octo2: ThreatFabric researchers have discovered a new version of the Octo Android banking trojan, which was first spotted back in 2019.
Sponsor Section
Resourcely co-founder and CEO Travis McPeak held an off-the-record conversation at this year's Blackhat Campfire Stories, talking about some of the hard truths CISOs don't usually talk about.

APTs, cyber-espionage, and info-ops
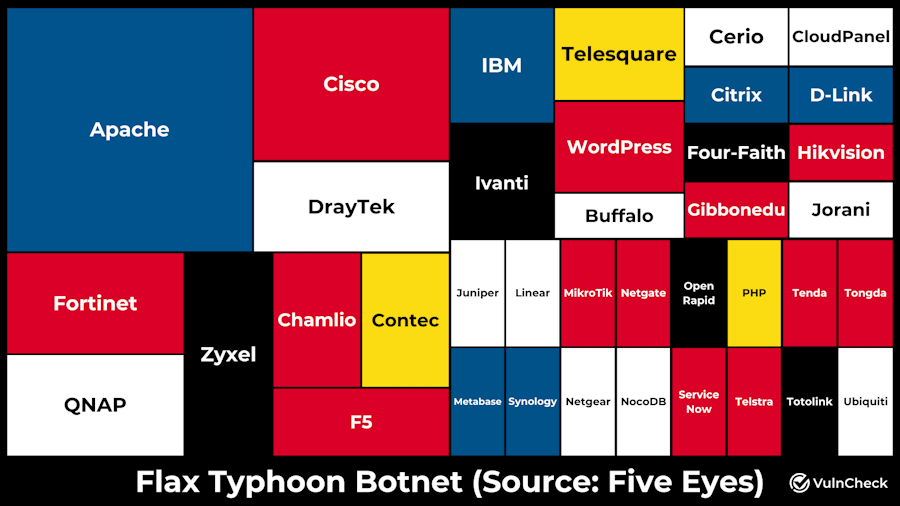
Flax Typhoon: VulnCheck has taken a look at all the vulnerabilities exploited by Chinese APT group Flax Typhoon to build its Raptor Train botnet. They're 66 in total and are all over the place.
TikTok removes RT accounts: TikTok has permanently banned RT and Sputnik accounts for running "covert influence operations" on the platform. Meta also banned RT accounts last week, citing similar reasons. The US government said that RT and its parent organization have morphed from a news agency into an active intelligence asset for the Russian government. RT didn't deny the accusations.
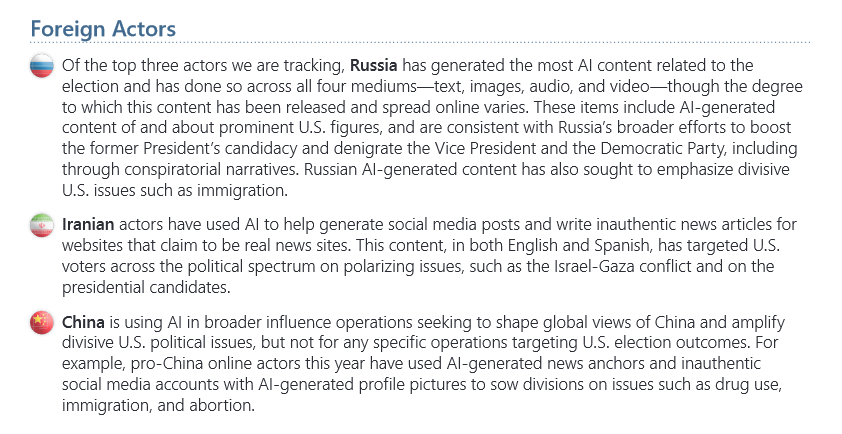
Russia uses AI for US election interference: The US government says that Russia is using AI to generate content for its disinformation operations designed to interfere in the US Presidential Election. The content was designed to boost the Trump campaign and denigrate the Harris camp. The Office of the Director of National Intelligence says China and Iran have also used AI toolkits, but Russia generated the most AI content related to the election out of the three.
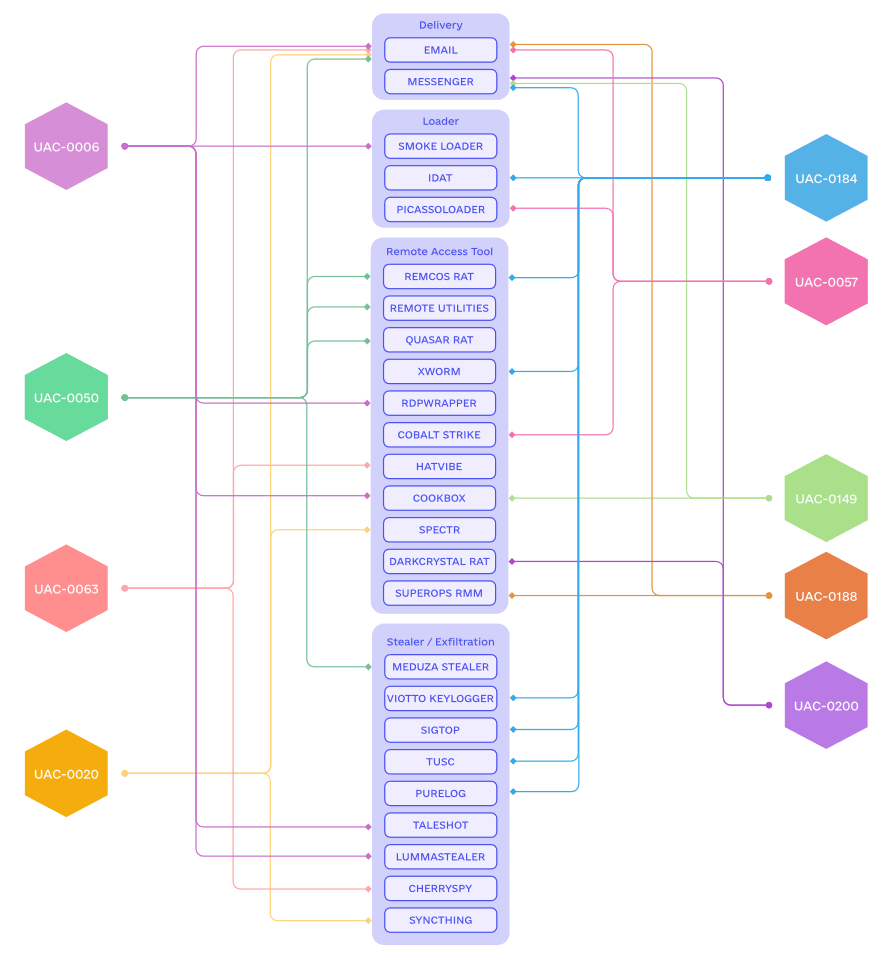
Russian cyber-ops shift in Ukraine: Ukraine's cyber agency says Russian hackers have significantly changed the way they operate in Ukraine over the past year. Russian cyber units have switched from destructive attacks to extremely targeted attacks on Ukrainian organizations directly connected to the war effort. The Russians have switched from attacking email servers and from email phishing to targeting alternative communication channels. This included targeting military personnel via secure instant messaging systems, social networks, or dating sites. [Additional coverage in The Record]
Vulnerabilities, security research, and bug bounty
ESET security update: ESET has fixed an EoP in its security software tracked as CVE-2024-7400. The bug was discovered by Dmitriy Zuzlov of Positive Technologies.
FreeBSD security update: The FreeBSD project has released a security update to patch a vulnerability to escape the bhyve hypervisor and run malicious code on the host operating system. Tracked as CVE-2024-41721, the vulnerability exploits the hypervisor's virtual USB emulator. Disabling USB emulation blocks attacks until patches can be applied.
Chrome zero-day analysis: Russian security firm BI.ZONE has published an analysis of CVE-2024–7965, a Chrome zero-day that Google patched in late August.
Ivanti vTM attacks: CISA says that threat actors are exploiting an auth bypass vulnerability to take control of Ivanti Virtual Traffic Manager (vTM) servers. The attacks are exploiting a vulnerability (CVE-2024-7593) Ivanti patched in August. Ivanti anticipated the attacks since proof-of-concept code had been available at the time of the patch.
Tank gauge vulnerabilities: Security firm Bitsight has published research on 10 vulnerabilities it found in the automatic tank gauges of five vendors (Alisonic, Dover Corp, Franklin Fueling Systems, Maglink, and Omntec).
Infosec industry
Microsoft SFI progress report: Microsoft has published a progress report on its Secure Future Initiative (SFI), a company-wide effort to boost the security of its products. The progress report comes almost a year after the initiative was announced last November when it told engineers to prioritize security features and tied exec compensation to security goals. Microsoft says it has now reduced the time to mitigate severe cloud vulnerabilities, removed 730,000 old or unsecured apps from internal systems and production systems, and removed 5.75 million inactive tenants. The company says 85% of its build pipeline is now managed from a central system, and 99% of all production assets are now recorded in a central inventory system. Microsoft has also named 13 deputy CISOs to manage specific segments within the company, such as Azure, gaming, or AI.
- Artificial Intelligence
- Azure
- Consumer
- Core Systems and Mergers and Acquisitions
- Customer Security Management Office
- Experiences and Devices
- Gaming
- Government
- Identity
- Microsoft 365
- Microsoft Security
- Regulated Industries
- Threat Landscape
Kaspersky force-replaces itself in the US: Russian security firm Kaspersky rolled out an update this week that has replaced its antivirus for US customers with the Pango Ultra AV and Ultra VPN. Pango had acquired Kaspersky's US customers in a deal at the start of the month. Kaspersky sold its US business after the US Department of Commerce banned Kaspersky from operating in the US in June. The Russian company was told to exit the US market by September 29. [Additional coverage in TechCrunch]
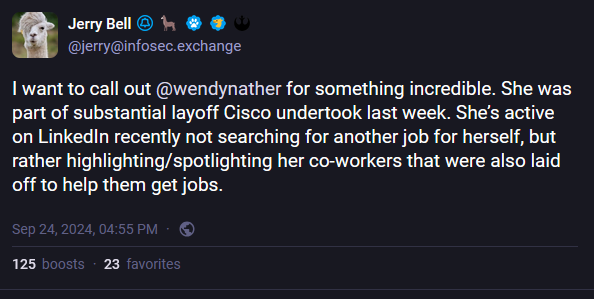
Cisco layoffs: Industry veteran Wendy Nather was included and let go during last week's Cisco layoffs. She also gave a perfect example on how to recognize a true leader.
Acquisition news: Digicert has acquired Vercara, a managed DNS provider and DDoS mitigation service.
Threat/trend reports: HP Wolf Security, Kaspersky, LendingTree, Searchlight Cyber, and the Shadowserver Foundation have recently published reports covering infosec industry threats and trends.
New tool—Broken Hill: Security firm Bishop Fox has released Broken Tool, a new tool to perform GCG attacks against a variety of popular LLMs.
BruCON 2024: Talks from the BruCON 2024 security conference, which took place last week, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about new reports saying that Russia is creating new cyber groups made up of cybercriminals.
In this podcast, Tom Uren and Patrick Gray talk about the structure of the spyware ecosystem. It's concentrated, with lots of vendors in India, Israel, and Italy. And its a small pool of talent, with many companies being founded by just a few individuals.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!






