Risky Biz News: Apple warns iPhone users of new spyware attacks
In other news: BLOODSEC hackers detained in the Philippines; South Africa agency lost $16.6 million in 10 years to hacks; NATO to establish new cyber center.

This newsletter is brought to you by Devicie. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Apple has sent this week a new batch of notifications about possible infections with mercenary spyware to iPhone users across 98 countries.
This was the company's second wave of notifications it sent this year after a first round back in April.
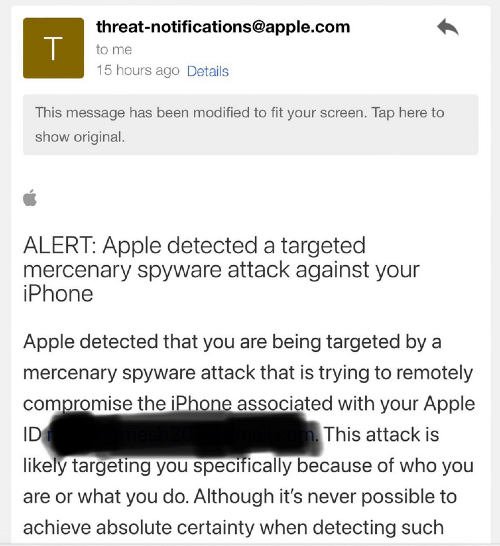
The new "mercenary spyware" notifications are Apple's older "state-sponsored attacks" alerts the company was sending in previous years.
Apple changed the alert's wording this year, most likely after being pressured by the Indian government.
A batch of notifications last year hinted the Indian government was behind attacks on journalists and political rivals. The Modi regime took offense to the wording of the alerts and called Apple's security team for a talk at the end of 2023. While no official statement was ever put out, the wording of Apple's notifications changed immediately after.
At the time of this newsletter, very few users have come forward to share that they received the new alert.
Users in India are among the few who publicly disclosed receiving the notification. The most high-profile target known so far is Iltija Mufti, the daughter of Mehbooba Mufti, the president of Indian political party, the Jammu and Kashmir People's Democratic Party (PDP).
Although the alert was pretty generic, Mufti accused the ruling BJP party of hacking her phone with the Pegasus spyware.
CitizenLab's John Scott-Railton has urged anyone who received the alert to contact spyware experts from CitizenLab or AccessNow.
According to Apple security expert Josh Long, users who are unsure if the alert is authentic can log into Apple ID on the Web to confirm they were sent an alert.
Breaches, hacks, and security incidents
DPWI hack: The South African government says hackers stole $1.3 million from its Department of Public Works and Infrastructure. Authorities seized the laptops of 30 employees, including three senior managers to investigate possible "collusion" with the hackers.Newly appointed minister Dean Macpherson says the Department has lost more than $16 million to hackers over the past 10 years.
Neiman Marcus breach: Threat actors have stolen more than 31 million customer details from US retailer Neiman Marcus. The company says hackers stole data such as names, home addresses, emails, dates of birth, and partial credit card numbers. The breach took place in May this year and is connected to the Snowflake incident. [Additional coverage in BleepingComputer]
MOVEit hacks fallout: Progress Software says it is a part in 144 class action lawsuits filed by customers following the MOVEit hacking spree of 2023. So far, the company has reported only $3 million in expenses related to the 2023 hacks. The company is expected to take a big financial hit as the lawsuits go through the courts. [Additional coverage in CybersecurityDive]
General tech and privacy
Google dark web monitoring solution: Google will add a dark web monitoring feature to all Google user accounts by the end of the month. The new feature scans the dark web for a user's personal details, such as name and email address. The feature is named Dark Web Reports and will be available in a user's Google account dashboard. Dark Web Reports was initially available in Google's Google One VPN, which the company shut down at the end of June. [Additional coverage in 9to5Google]
Google APP update: Google has updated its Advanced Protection Program to allow users to secure their online accounts using one single passkey as an alternative to using two physical security keys.
Snowflake MFA updates: Cloud storage provider Snowflake is now letting tenants force MFA for all their users. The update comes in the wake of a major security breach that took place last month.
Dark patterns abuse: An FTC investigation found that hundreds of websites and apps use dark patterns to manipulate user behavior, such as buying unwanted services and giving up on their privacy. The investigation audited the behavior of 642 websites and mobile apps that offered subscription services across the globe. It also included officials from 27 consumer protection authorities in 26 countries. The FTC says that nearly 76% of audited sites and apps used at least one dark pattern, and 67% used multiple.
Government, politics, and policy
US election interference: US intelligence officials say Russia has intensified its information operations designed to support Donald Trump in the upcoming US presidential election. [Additional coverage in VOA]
US cyber funding: The Biden administration has asked federal agencies to increase their requests for cyber investments to make sure they have all the needed funding to protect their systems. [Additional coverage in Cyberscoop]
CISA SbD alert: CISA has released another one of its Secure-by-Design alerts. This one focuses on OS command injection vulnerabilities.
New NATO cyber center: NATO will establish a new cyber operations center in Belgium later this year. The new NATO Integrated Cyber Defense Center was announced at the alliance's 75th anniversary summit this week. The Center's role will be to inform NATO's military commanders of possible cyber threats against both military and civilian infrastructure that may affect the alliance's military capabilities.
Czech national security: Czechia's cybersecurity agency says it detected four separate incidents last year where foreign hackers tried to breach the country's IT systems. The National Agency for Cyber and Information Security (NUKIB) says the attacks represented the largest number of security incidents the country experienced in its history. NUKIB attributed the attacks to hackers from China, Russia, Iran, and North Korea. At least one was successful, the agency said. [Additional coverage Euractiv]
Germany abandons Chinese gear: The German government has ordered telecom operators to remove Huawei and ZTE equipment from the country's 5G network. Officials cited national security threats as the base for their decision. Telecom operators must remove unauthorized Chinese equipment from core networks by the end of 2026 and from transport networks by the end of 2029. [Additional coverage in the Associated Press]
Indonesia cyber branch: Local cybersecurity experts are encouraging the Indonesian government to establish a fourth military branch dedicated to cyber operations. [Additional coverage in The Defense Post]
More Russian surveillance and crackdown news: Russia's internet watchdog has announced that all social media account owners with a following of more than 1,000 users must provide their real names to authorities. The Roskomnadzor says the new law specifically applies to users who share news-related content. The agency is still working on a system to allow users to report this information. [Additional coverage in TASS]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Devicie Technical Product Manager Tom Plant on the upcoming Windows 10 end-of-support and the looming Great Windows 11 Migration.

Cybercrime and threat intel
Comelec hackers detained: Philippine authorities have detained four suspects believed to be members of the BLOODSEC hacking group. Officials say the four allegedly orchestrated intrusions at several government agencies and private companies and then sold the data online. Among known victims are the Philippines Electoral Commission (COMELEC) and Sky Cable Data, one of the country's largest ISPs. A fifth suspect was detained a day later. Officials say the suspect went by the hacker name Godlike and is a member of Anonymous Philippines.
Zeus/IcedID member sentenced: US authorities have sentenced a Ukrainian national to 18 years in prison for his role in two separate malware operations. Vyacheslav Penchukov used the hacker name of Tank and was one of the leaders of the infamous Zeus malware gang in the late 2000s. After the group disbanded, Penchukov became one of the main operators of the IcedID trojan in the late 2010s. Penchukov was on the FBI's Most Wanted Cyber list for eight years until he was arrested in 2022. Penchukov was also ordered to repay more than $73 million back to past victims. [Additional coverage in Wired]

Threat/trend reports: Abnormal Security, ANY.RUN, Broadcom Symantec, Cloudflare, and SANS have recently published reports covering infosec industry threats and trends.
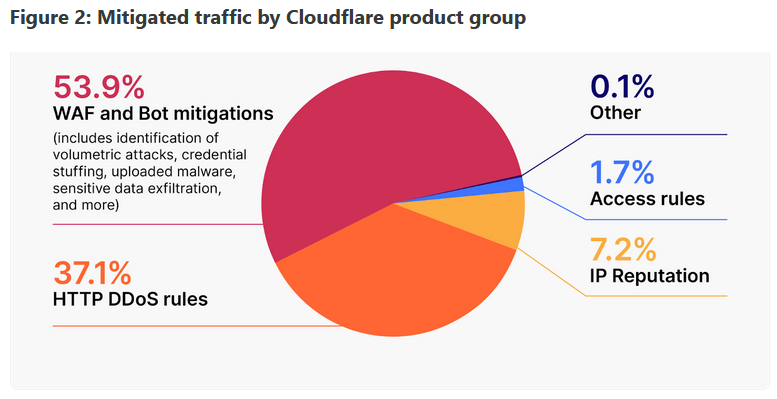
Internet infrastructure company Cloudflare says that 6.8% of all the traffic that goes through its network is malicious and needs to be mitigated. Half of the malicious traffic is bot-related, while DDoS attacks account for 37%. Cloudflare says it's typically seeing attacks against vulnerabilities roughly 22 minutes after proof-of-concept code is published online.
Meow Leaks interview: Threat intelligence analyst Marco A. De Felice has published an interview with the operators of the Meow Leaks ransomware and data extortion group.
Olympics warning: The Cyber Threat Alliance has published its threat assessment for the upcoming Paris 2024 Olympic Games.
Apple warning: Apple has published a new document to help its users spot phishing and phony tech support scams.
HTML smuggling: Cisco Talos has published a technical report on how HTML smuggling is being used these days for email/malspam campaigns.
LATAM campaign: Email security firm Cofense has published a report about a malspam campaign targeting Latin America with a version of the PocoRAT malware.
Meta scam campaign: Bitdefender has published a deep dive into a large-scale health-related scam campaign that has flooded Meta social media properties with malicious ads.
CISA red team exercise: CISA has published the results of a recent red team exercise against one of the US federal civilian agencies.
Ticket Heist: A cybercrime operation named Ticket Heist is selling counterfeit tickets to major sporting events across the globe. According to security firm QuoIntelligence, the group operates more than 700 domains and primarily targets Russian-speaking users. Current operations focus on the UEFA EURO 2024 soccer tournament and the upcoming Paris Olympic Games. A smaller portion of the group's domains are focused on selling counterfeit tickets to music concerts.
NuGet malware: ReversingLabs has found 60 malicious .NET libraries available through the official NuGet portal. The libraries used typosquatting to pass as legitimate packages. They also leveraged a new technique called IL weaving to insert the SeroXen RAT inside legitimate binaries. ReversingLabs says the packages are part of a larger campaign that began in August last year and included another 700 malicious libraries.
Huione Guarantee: A Cambodian online platform named Huione Guarantee allegedly plays a major role in laundering the proceeds of pig butchering and other online scams. Blockchain security firm Elliptic says the platform has been linked to $11 billion in transactions, with a large chunk linked to illegal activity. Criminal groups have used the platform for money laundering and to acquire the tools of their trade. This includes AI face-swapping software, telecom equipment to power scam centers, and torture and human control equipment. The platform has operated for years and is part of the Huione Group, a large Cambodian financial conglomerate linked to Cambodia’s ruling Hun family.
"One of the directors of Huione Pay is Hun To, a cousin of the current Cambodian prime minister, Hun Manet. Hun To has reportedly been suspected of heroin trafficking and money laundering by Australian Police. He has also been linked to Chinese organized crime and a scam compound."
Smishing Triad: Resecurity researchers say the Smishing Triad gang is now focusing its efforts on targeting Indian users.
FIN7: Security firm Silent Push has discovered new server infrastructure operated by Russian cybercrime group FIN7. The new infrastructure is currently being used in phishing attacks against corporate entities and cryptocurrency companies. The infrastructure is located on web host known for hosting cybercrime operations and official Russian propaganda and disinformation sites. Prior to Silent Push's discovery, the group had been dormant for three years since US authorities charged and arrested some of its members in 2021. FIN7 previously used fake security firms to disguise its hacks as penetration tests. According to infosec reporter Brian Krebs, the group appears to operate a domain for a fictitious security firm named CyberCloudSec.
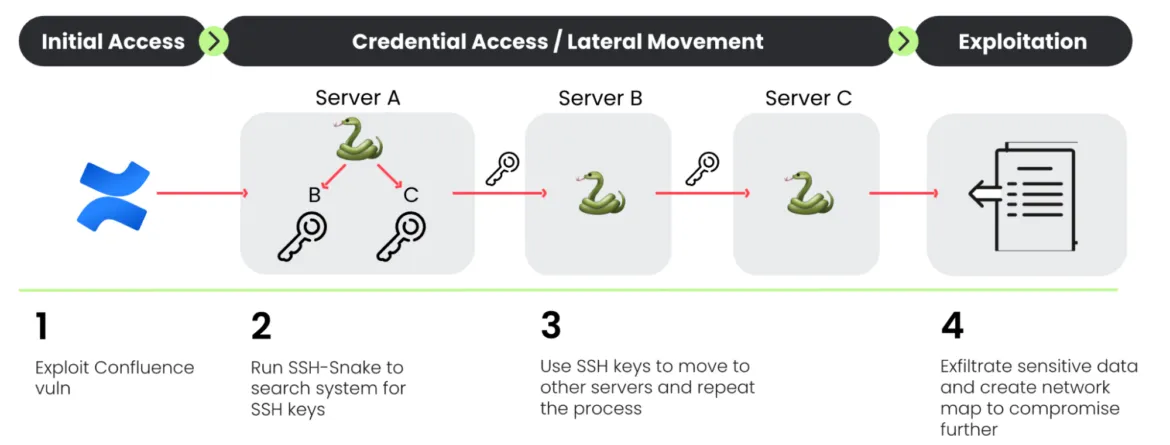
CRYSTALRAY: A threat actor known as CRYSTALRAY has intensified attacks on cloud environments in recent weeks. The group's operations exploded from 100 victims reported in February this year to more than 1,500 at the start of the month. Security firm Sysdig says the group relies on an open-source penetration tool named SSH-Snake to launch its attacks and move laterally across cloud environments. Besides SSH-Snake, the group also abuses other open-source tools like httpx, Nuclei, and Zmap.
Malware technical reports
ViperSoftX: Trellix has published a technical report on the ViperSoftX trojan and recent campaigns that used e-book torrents to infect users.
DarkGate: Palo Alto Networks has published a top-down look at DarkGate, one of the malware loaders that exploded in adoption after Europol's QakBot takedown in 2023.
ZharkBot: OALabs has published a report on the new ZharkBot malware loader.
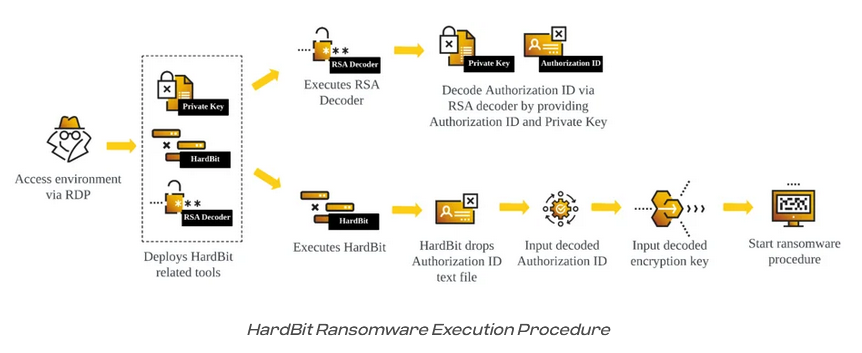
Hardbit ransomware 4.0: Cybereason has published a report on version 4.0 of the HardBit ransomware, a group active since early 2022.
BianLian ransomware: Juniper's security team has published an analysis of BianLian's 2024 activities. Per the company's numbers, BianLian is this year's third most active ransomware gang.
Akira ransomware: BlackBerry looks at the Akira ransomware gang, its malware, and recent attacks the LATAM airline industry.
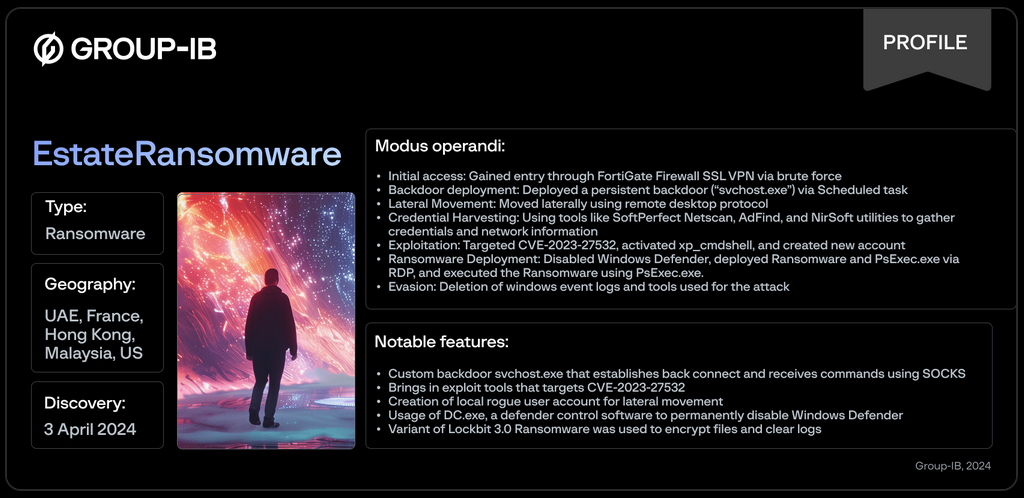
Estate ransomware: Security firm Group-IB has discovered a new ransomware gang named Estate that is launching attacks against corporate networks. The group exploits unpatched Fortinet firewalls for initial access (CVE-2023-27532). It also exploits a second exploit to collect network credentials from Veeam backup servers and expand access inside compromised networks. The group does not yet operate a dark web leak site.
Sponsor Section
Brought to you by Devicie. Be the first to hear about Devicie for MSP, the Intune hyper automation and management platform for modern device management at scale. Visit devicie.com/MSP

APTs, cyber-espionage, and info-ops
APT41's DodgeBox: Zscaler has found a new malware loader named DodgeBox that appears to be used by the APT41 Chinese cyber espionage group. The loader is being used to deploy the MoonWalk backdoor on compromised systems.
"Olympics has Fallen" campaign: McAfee has published a report on a Russian disinfo operation promoting a fake movie about the corruption at ICO that used deep-faked audio and video of popular celebrities. The interesting part in the whole report is that McAfee goes out of its way not to attribute this to Russia, even if Russian groups have been the sole entity pushing this narrative for years now. Good job, security firm!
Doppelganger infrastructure: A joint report between Correctiv and the Qurium Foundation exposes how the Doppelganger Russian disinformation group largely relies on companies from within the EU to spread their propaganda. The companies are all owned by young Russians and are interconnected, showing a common source of financing.
"Legal entities in the United Kingdom, often run by very young Russian individuals, are used to channel the necessary volatile digital resources to the constant creation of new providers (autonomous systems) that share a few common international upstreams. The technical infrastructure of Doppelganger is extensive, comprising of more than 300 network prefixes and 100,000 IP addresses with a market value of 5 Million EUR or a leasing cost of approx 50,000 EUR/month. This massive infrastructure investment can only be sustained by serious financial support from external actors."
Vulnerabilities, security research, and bug bounty
Microsoft zero-day: Check Point says hackers have been using a Microsoft Windows zero-day in attacks for almost a year and a half. The attacks leveraged .url Windows Internet Shortcut Files posing as legitimate files. If clicked, the zero-day allowed the attackers to force the URL to open in the older Internet Explorer engine. The attackers leveraged old Internet Explorer bugs to install malware on the victim's device. Check Point says attacks using this trick have been taking place since January 2023. Microsoft patched the zero-day (CVE-2024-38112) earlier this week in the July 2024 Patch Tuesday.
Exim vulnerability: The Exim project has released a security patch to fix a major vulnerability in its email server. Tracked as CVE-2024-39929, the vulnerability can allow threat actors to bypass Exim security filters and deliver malicious emails to users' inboxes. The vulnerability has not been reported as exploited in the wild. According to Censys, the number of Exim servers running the vulnerable versions is around 1.5 million.
ServiceNow vulnerability: Security firm Assetnote has discovered major vulnerabilities in the ServiceNow business platform that can be used to hijack the company's on-premise servers. The attack uses three chained bugs that can allow threat actors to bypass authentication and take over the ServiceNow MID Server. The MID Server is the on-premise system that connects customer networks to the cloud-based ServiceNow platform. Researchers argue this server can be used to springboard other attacks on a customer's internal network. Assetnote described the attack as the most critical exploit chain in the company's history.
Realtek SDK vulnerabilities: Cisco Talos researchers have found 15 vulnerabilities in Realtek rtl819x Jungle, an SDK used for the company's SOHO router firmware.
GitLab security update: GitLab has released a security update to fix six security flaws. The worst of the six allows attackers to run pipeline jobs as any user.
PHP CGI exploitation: A PHP CGI vulnerability (CVE-2024-4577) disclosed last month is now regularly being used to distribute malware and hijack servers for DDoS attacks, according to a new Akamai report.
NATO vulnerability: Contrast Security researchers have found a CSRF vulnerability in NATO's open-source employee training platform known as SkillTree.
Outlook RCE: Morphisec has published details on CVE-2024-38021, a new RCE in Microsoft Outlook. This was patched this week in the regular Patch Tuesday updates.
Universal XSS: Security researcher Eugene Lim provides a proof-of-concept for a universal XSS vulnerability that abuses APIs in the browser and different extensions for a powerful Chrome RCE.
False File Immutability vuln class: Elastic's security team has published a technical report on a new Windows vulnerability class they're calling False File Immutability.
"We will demonstrate how one such vulnerability in the Windows 11 kernel can be exploited to achieve arbitrary code execution with kernel privileges. [...] We are aware of two public exploits that leverage it, PPLFault and ItsNotASecurityBoundary."
Google VRP: Google says it's increasing the maximum reward in its VRP by five times to a maximum reward of $151,515.
Infosec industry
New tool—Sinon: Security researcher James Brine has open-sourced Sinon, a tool for automatic burn-in of Windows-based deception hosts.
New tool—SaladCat: Security researcher Kyle LePrevost has open-sourced SaladCat, a new cloud-distributed password-cracking tool.
New tool—Wiz Defenses: Cloud security firm Wiz has put together a portal with various defensive techniques that can be used to protect cloud environments.
New tool—Graphpython: Security consultant MLCSec has open-sourced Graphpython, a Microsoft Graph API enumeration and exploitation tool.
SO-CON 2024 videos: Talks from SpecterOps' SO-CON 2024 security conference, which took place in March, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how bureaucracies should deal with outstandingly talented individuals.
In this podcast, Tom Uren and Patrick Gray talk about how South Korean internet regulations inadvertently encouraged a large ISP to hack their own customers to cut down on torrent traffic.
Abhishek Agrawal is the CEO and co-founder of Material Security, an email security company that locks down cloud email archives. Attackers have been raiding mailspools since hacking has existed, and with those mailspools now in the cloud with services like o365 and Google Workspace, guess where the attackers are going?




