Risky Biz News: Apple wants to reduce the lifespan of TLS certificates to 45 days
In other news: Russian government forgets about Operation Triangulation; Japanese police trace Monero transactions to detain suspects; SEC fines four companies over SolarWinds hack disclosures.

This newsletter is brought to you by Okta. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
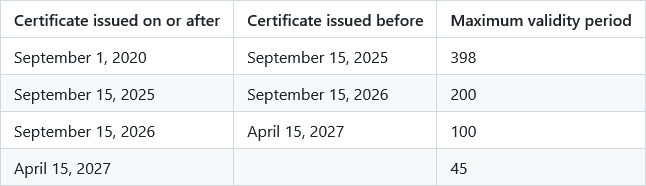
Apple has put forward a proposal to gradually reduce the lifespan of TLS certificates from the current 398 days to only 45.
The planned move will take place across four phases between September next year and April 2027.
TLS lifespan will be reduced to 200 days in September 2025, to 100 in September 2026, and just 45 in April 2027.
Apple has put the proposal for a vote with the CA/B Forum, an informal group made up of browser vendors and Certificate Authorities (CAs), the companies that issue TLS certificates.
If approved, this would mark the fourth time that the maximum lifespan of TLS certificates is changed after TLS certs went from 10-year validity periods to three, two, and then one (the current 398 days).
Apple's proposal would be the second time browser makers try to reduce TLS lifespans to a super short time period. Google tried and failed to have TLS lifespans reduced to 90 days in a proposal made last year.
Sectigo, formerly known as Comodo and one of today's largest CAs, has already announced its support for the TLS lifespan reduction. The company also backed Google's proposal last year, citing the need for CAs to modernize and move to automated certificate lifecycle management (CLM) procedures.
Over the past years, browser makers have constantly tried to push CA vendors to adopt shorter and shorter TLS certificate lifespans.
The benefit is that if customers lose control of their certificate, the short expiration date limits the damage it can do and the malware and phishing sites it can support. In previous years, heaps of malware have been signed by the same leaked and long-lived certs because of shoddy certificate revocation systems.
As time has gone by and as certificate management tools have exploded on the market, it has become harder and harder for CAs to play the "it's not possible to automate at scale" card. You can basically thank Let's Encrypt for that.
Breaches, hacks, and security incidents
CERP ransomware attack: French pharmaceutics company CERP was hit by ransomware over the weekend. [Additional coverage in France Bleu]
Tapioca DAO crypto-heist: A threat actor has stolen $4.7 million worth of crypto-assets from DAO platform Tapioca. The attackers obtained private keys for some wallets through a social engineering attack. Tapioca says it managed to recover $2.7 million of the stolen assets shortly after the hack. Early evidence suggests the hack may be linked to North Korea. [Additional coverage in CryptoSlate]
Cyprus DDoS attacks: The Cypriot government says it blocked a DDoS attack that targeted its central online portal. The Black Maskers Army, LulzSec Black, and several other pro-Palestine groups took credit for the attacks. [Additional coverage in the AP]
SEC fines four companies over SolarWinds hacks: The US Securities and Exchange Commission has fined four companies over misleading statements made over breaches related to the SolarWinds supply chain attack. The agency levied fines against Unisys ($4 million), Avaya ($1 million), Check Point ($995,000), and Mimecast ($990,000). The SEC says the four companies minimized the impact of their hacks in public statements. [Additional coverage in CyberScoop]
General tech and privacy
SSL lib comparisons: Prossimo has published new performance tests between RusTLS, OpenSSl, and BoringSSL.
Session leaves Australia after police visit: Encrypted chat app Session says it will re-locate and re-organize as a foundation in Switzerland after Australian police paid a visit to the home of one of its employees. [Additional coverage in 404 Media]
Italy blocks Google Drive: Italy has blocked access to Google Drive via its Privacy Shield anti-piracy system. The block was quickly reverted after causing a national blackout of various Google services. [Additional coverage in TorrentFreak]
Nudity warnings in Google Messages: The Google Messages app will now warn users when they attempt to send or receive nude images. The company says the new feature is intended to prevent accidental sends and protect underage users. The new nudity warning is part of five new features the company has added to the Messages app this week. The update also includes warnings for common package delivery and job scams, warnings for dangerous links, the ability to block messages from unknown senders, and a system to flag users trying to impersonate one of your contacts.
Google's Secure by Design pledge: Google has published an update on the progress of its Secure by Design pledge the company made to White House officials earlier this year.
Meta tests face recognition to combat hacks and scams: Meta will use facial recognition as part of its Facebook and Instagram account protection and security systems. The company plans to use facial recognition as part of its account recovery process. Users will be asked to record a selfie video that Meta will use to compare their faces against official documents and public posts. It also plans to use facial recognition software to detect celeb-bait scams that use ads with celebrity videos to scam users for money. The system scans all Meta ads for celebrity faces and triggers a review of an ad if one is found. Meta says early tests with a small group of celebrities and public figures have shown promising results.
Meta-v-NSO lawsuit update: Meta has asked the judge to award the company a win in its lawsuit filed against Israeli spyware vendor NSO Group. The social media company claims that NSO defied a court order and violated legal discovery requirements. Meta says NSO refused to produce internal email communications and the source code of its technology after being ordered to do so in March. [Additional coverage in The Intercept]
Meta bans flight-tracking accounts: Meta has banned dozens of Instagram and Threads accounts tracking the personal jets of celebrities and politicians. At least 38 accounts were run by Jack Sweeney, a Florida college student who became famous after getting banned from Twitter for tracking Elon Musk's personal jet. Meta says it banned the accounts because the accounts posed a "risk of physical harm to individuals." [Additional coverage in Gizmodo]
Uber adds rider verification feature: Uber has introduced a verification system for passengers who provide a copy of their government-issued ID. Uber says riders who verify accounts will be put in a priority queue and have shorter waiting times. The company hopes the new system will help drivers avoid confrontations with unruly passengers. On the informal side, I really hope the screenshot below is the rider's view of their own profile and that drivers can't see the last four digits of a rider's card number. Now, that would be some epic level of fail.
Government, politics, and policy
DOJ bulk data sale proposal: The US Justice Department has proposed new rules to block the bulk sale of Americans' personal information to foreign adversary states on the grounds of national security risk. This includes countries like China, Russia, Iran, North Korea, Cuba, and Venezuela. The new rules bar data brokers from selling or transferring abroad certain types of data that are considered to be too sensitive and could enable hacking, surveillance, and influence campaigns. The DOJ published the rules on the grounds of a White House executive order issued in late February.
White House to review ICE contract: The US government has paused a recent ICE contract with Israeli spyware vendor Paragon Solutions. According to WIRED, the contract is now under compliance review by the ICE's Homeland Security Investigations division for breaking a White House executive order that limits how US government agencies can use spyware and surveillance solutions.
DOD asks tech execs to volunteer: The US Department of Defense is asking Silicon Valley tech executives to volunteer and join the reserve forces, where they could lead and help implement short-term tech and cybersecurity projects. [Additional coverage in the WSJ]
Russian government forgets about Operation Triangulation: The Russian government has bought four times more iPhones in 2024 than the previous year despite a ban on using the device. The increased numbers are ironic since Russian intelligence services accused Apple of helping the NSA spy on Russian officials through their iPhones. The hacks were exposed by Kaspersky and are known as Operation Triangulation. Apple denied any role in the incidents. The Russian government banned government workers from using iPhones shortly after. [Additional coverage in Vedomosti]
NSO lobbying efforts target GOP: The Intercept reports on NSO Group's new lobby efforts in the US, mostly targeting the Republican Party and Texas officials, in particular.
UK allows dissident to sue Saudi Arabia over spyware: A UK court has ruled that an exiled Saudi dissident can sue the Saudi Arabian government over being targeted with spyware. Yahya Assiri alleges that Saudi officials targeted his devices with the NSO Group's Pegasus spyware and other spyware from Israeli firm QuaDream. Assiri is the founder of the National Assembly Party, the first-ever pro-democracy opposition party in Saudi Arabia. Earlier this month, another London court ruled that Bahrain can't claim "state immunity" and must stand trial in a lawsuit filed by two dissidents over the government's use of spyware. [Additional coverage in the Middle East Monitor]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Brett Winterford, Okta's APAC Chief Security Officer. Brett has mined Okta's data and finds strong evidence that organizations invest in phishing-resistant authentication methods once they know they've been targeted by groups that excel at social engineering (such as Scattered Spider).
Here is the research that Brett talks about in this discussion.
Cybercrime and threat intel
Data sellers detained in Turkey: Turkish authorities have detained nine suspects and seized 18 websites that sold the personal data of Turkish citizens. Officials claim the websites advertised their services on social media and sold data to Israeli intelligence and terrorist organizations. Some of the data was also used to extort children and for espionage operations. This was Turkey's second crackdown against illegal data brokerage services. Authorities previously arrested 11 suspects in August. [h/t Ersin Çahmutoğlu]
Japanese police trace Monero transactions: Japan's National Police Agency has arrested 18 members of a cybercrime group after tracing their Monero transactions. The group stole money from victims via fake online classified ads and laundered the funds through Monero accounts. The group has been active since mid-2021 and laundered over 100 million yen (~$660,000). This marks the first case where authorities have publicly confirmed to have successfully traced Monero transactions. [Additional coverage in Nikkei]
Tech scammer detained: Italian authorities have arrested a 43-year-old Italian-Australian for his role in a tech support scam operation. The suspect was detained at the Milano airport after arriving from Singapore. The FBI had been looking for the suspect for more than three years. [Additional coverage in Milano Today]
ClickFix campaign: GoDaddy says that a malware distribution campaign tracked as ClickFix has infected over 6,000 WordPress sites since June this year. The attacker deployed malicious plugins on the hacked sites that were used to prompt users with popups that led to malware.
Gophish campaign: Cisco Talos has published a report on a malware distribution campaign abusing the Gophish red team phishing tool to distribute PowerRAT and DCRAT.
Steam abused as a DDR: More and more threat actors are using the Steam platform as a dead drop resolver (DDR) to hide information on their C2 infrastructure, according to a new PT report.
Safe Browsing removal services: There are several threat actors selling access to cybercrime services to remove malicious sites from the Google Safe Browsing list. Some of these services are advertised as "red page removal" services after the Safe Browsing red page shown inside browsers.
New npm campaign: Phylum has discovered a new set of malicious packages on npm. These ones were posing as packages designed to work with the Ethereum blockchain but stole Ethereum wallet private keys.
Fake wood scams: Group-IB looks at a novel scam campaign it spotted targeting French users—websites advertising firewood.
Malware technical reports
Lumma Stealer: Qualys researchers look at Lumma Stealer, an information-stealing malware available through a Malware-as-a-Service (MaaS).
Latrodectus: Logpoint and VMRay have published technical reports on the Latrodectus malware. Also, check out this report from Forcepoint on the same malware.
Grandoreiro: Kaspersky looks at Grandoreiro, the Brazilian banking trojan that appears to have survived a law enforcement takedown earlier this year.
SRBMiner: Trend Micro has discovered a new threat actor targeting Docker servers with the SRBMiner cryptocurrency miner.
macOS.NotLockBit: SentinelOne has published a report on macOS.NotLockBit, a new ransomware strain modeled on the LockBit code and targeting macOS systems—first spotted last week by Trend Micro.
"The NotLockBit malware appears to be very much in development. For now, the threat actor's AWS accounts have been removed and there are no known victims or distribution methods in the wild. Given the amount of development that has gone into this threat so far, we would be surprised not to see more from this threat actor in the short to medium term."
Mallox (TargetCompany) decrypter: Avast has released a free decrypter to allow victims of the Mallox ransomware to recover their files without paying the ransom. The decrypter works for Mallox versions used in attacks between January 2023 and February 2024. The ransomware is also known as TargetCompany.
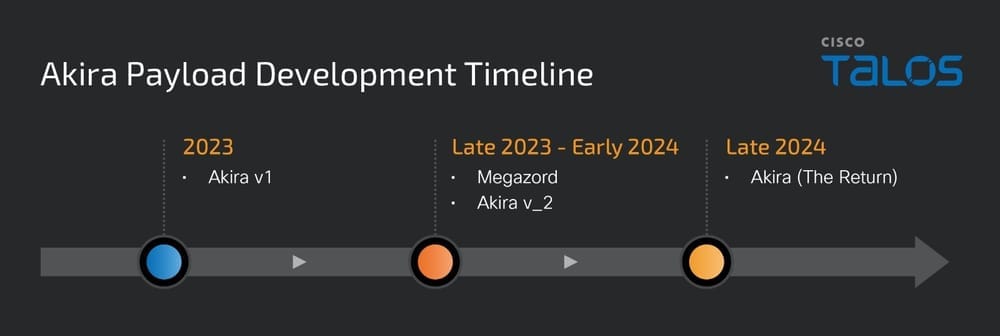
Akira ransomware: Cisco Talos looks at recent changes in the operation of the Akira ransomware, such as the group reverting to older and tested encryption methods and their migration back from Rust to C++.
Sponsor Section
In this sponsored product demo, Okta's Harish Chakravarthy and Brett Winterford walk through four new features Okta introduced in the wake of the emergence of modern attacker techniques targeting identity providers. These features will help you to prevent or limit the damage to your environment if an attacker manages to compromise a session token.
APTs, cyber-espionage, and info-ops
i-SOON reporting: Reporters from Japanese public broadcaster NHK paid a visit to the headquarters of i-SOON, the Chinese government cyber contractor that got hacked and its data posted online earlier this year. [h/t Ashley Shen]
Romanian disinfo farm: Romanian news outlet Public Record has published an investigation into an individual believed to be at the center of a disinformation operation that helps boost conspiracy theories and the typical anti-western tropes coming out of Sputnik.
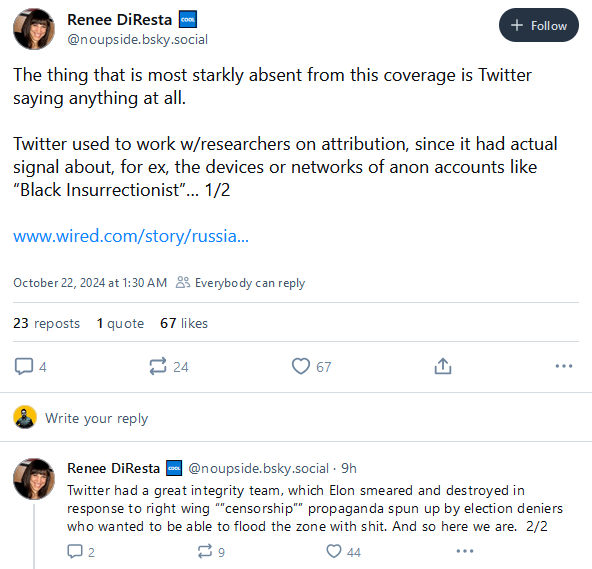
Russian disinfo targets Walz: A Russian disinformation group is behind a Twitter campaign claiming that Minnesota governor and vice presidential candidate Tim Walz sexually assaulted one of his former students. The campaign used deepfake videos claiming to be from whistleblowers in an attempt to smear the VP candidate ahead of the election. Experts and US intelligence agencies have linked the campaign to Storm-1516, a Russian group known to use fabricated videos to interfere in elections across the globe. Microsoft had previously warned last month that the group switched targets from the EU to the US presidential race. The videos were also boosted by members of the Trump campaign. [Additional coverage in WIRED]
Vulnerabilities, security research, and bug bounty
Imprompter attack: A team of academics has developed a new attack that can steal the personal data of users who interact with AI systems. The attack is named Imprompeter and targets LLM agents, the apps where users post commands and requests to an AI system. Researchers say the Imprompter attack can poison AI systems, so they steal user data and then share it with the threat actor.
OpenSSL security update: The OpenSSL project has released a security update to fix a memory corruption vulnerability. Impact is considered low.
OPA vulnerability: Tenable has disclosed a vulnerability in the Open Policy Agent (OPA) for Windows client.
"The vulnerability could have allowed an attacker to leak the NTLM credentials of the OPA server's local user account to a remote server, potentially allowing the attacker to relay the authentication or crack the password. The vulnerability affected both the OPA CLI (Community and Enterprise editions) and the OPA Go SDK."
Infosec industry
Acquisition news: UK cybersecurity firm Sophos has agreed to acquire Atlanta-based Secureworks for almost $860 million in an all-cash acquisition. Sophos says it plans to merge both products going forward. Dell acquired SecureWorks for $612 million in 2011 and has been trying to sell the company since early 2023.
New tool—CloudTail: Permiso has open-sourced CloudTail, a tool designed to enhance the long-term retention and searchability of cloud logs.
New tool—AuthzAI: Bug hunter Ron Chan has released AuthzAI, a tool to test and analyze API endpoints for potential permission model violations using OpenAI structured outputs.
New tool—Firefox Password Decryptor: A software engineer named Sohimaster has released Firefox Password Decryptor, a tool to extracting and decrypting passwords from Firefox.
Threat/trend reports: ANY.RUN, Deloitte, and Trustwave have recently published reports and summaries covering various infosec trends and industry threats.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about a new attempt to measure cyber power, the International Institute for Strategic Studies Cyber Power Matrix.
In this podcast, Tom Uren and Patrick Gray talk about the evolving relationship between Russian intelligence services and the country’' cybercriminals. The GRU's sabotage unit, for example, has been recruiting crooks to build a destructive cyber capability. Tom suspects that GRU thugs are not so good at hands-on-keyboard operations but excellent at coercing weedy cybercriminals to hack for the state.
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!




