Risky Biz News: Lockbit has been bluffing in extortion schemes, is close to an implosion
In other news: Russian CERT reports mysterious zero-day in Ukraine-linked software; EU's ExFiles phone-cracking project to shut down; and new MaginotDNS attack impacts CDNS servers.
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
New clues discovered by threat intelligence analysts suggest that the Lockbit ransomware group may be having technical difficulties, which have contributed to the operation losing some of its top affiliates over the past months.
According to a report published by Analyst1's Jon DiMaggio, the Lockbit gang is having problems publishing and leaking victim data on its dark web leak site.
The gang has run out of server storage, DiMaggio says. It often claims that a victim's files have been published, but the files can't be downloaded.
"This problem is due to limitations in its backend infrastructure and available bandwidth," DiMaggio says.
The researcher says Lockbit recently updated its server infrastructure, but the problem still persists, and some victims files don't get published even if the victims refuse to pay.
"Over the past six months, LockBit has presented empty threats [and] it failed to act upon after many victims refused to pay. Yet, somehow, no one has noticed," DiMaggio says.
The researcher believes this is a major problem for the gang, one that could seriously impact its operation and lead to victims refusing to pay on a more regular basis—since they don't have to fear that their sensitive files will be published anymore.
We asked DiMaggio if Lockbit might soon move to release stolen files via torrent files, just like one of their competitors, the Clop gang. Clop started releasing victim data as torrents after finding itself needing to host and publish a large number of victim files in the aftermath of its hugely successful MOVEit hacking spree.
"They're struggling right now to share victim data and they look really foolish. The easiest solution would be to use torrents to distribute data. But you know the reason that they haven't, and the reason that's a problem for LockBit, is because they sold 'hosting victim data' as one of the benefits of using their program.
That's one of the things affiliates pay for when they share their 20%. LockBit specifically talked about the benefit of how now affiliates don't have to worry about a law enforcement takedown of a server that they have stored data on.
And if [Lockbit] is to [...] revert back to pushing affiliates to put their data on a third party storage site, then [Lockbit] has to answer the question of 'Well, are you gonna adjust how much revenue you expect from affiliates to be a part of your program'—because right now, it's a service [affiliates] are paying for.
But I think [Lockbit]'s gonna have to, because like I said, now that people know about this problem, victims will be less likely to pay, affiliates are gonna be less likely want to be part of his program. So I definitely think that [Lockbit] is going to have to find an alternate solution and or fix [their] infrastructure to be able to support this. And you know, that's not the easiest thing to do when you're a criminal on the dark web."
But DiMaggio says that Lockbit's problems reach farther into its operation than the storage space of dark web servers, and this is only the proverbial tip of the iceberg.
The group has also missed a deadline to release an updated ransomware strain, which was requested by some of its affiliates.
The gang's sorry state of affairs was perfectly encapsulated by a thread on an underground hacking forum where the admins of the Royal ransomware accused Lockbit of trying to steal their ransomware builder rather than build their own. What was Lockbit's reply? They accused Royal of working for the Russian FSB intelligence service. Maybe not the appropriate reply here.
Per DiMaggio, there are also other major problems that have caused Lockbit's reputation to diminish, such as:
- No developer for an extended time
- Arrests/indictment of an affiliate
- Poorly coded Mac release/leak
- Poor service response time (via Tox)
- No ticketing system for reporting and tracking problems
- Posts on its leak site for fictitious companies
All of this has led to some of Lockbit's affiliates leaving and partnering with other RaaS programs, which made us ask DiMaggio if the Lockbit program could survive the year.
"The only way I think we'll see Lockbit go away, especially by the end of the year, is if there's a law enforcement takedown. Outside of that, I think it will continue to exist," DiMaggio told Risky Business News.
"However, its program and its reputation will be heavily diminished. And it's already begun, [with] a drop in the number of attacks," the researcher added.
"And I think you'll see a lot of the top affiliate teams leave for other programs. And that also has already begun."
Analyst1's one report is part three of a multi-series on the Lockbit RaaS. For the first report, DiMaggio spent a year undercover, interacting with LockBitSupp, the Lockbit gang's leader, documenting how the group rose to become today's largest ransomware operation. The second part covered Bassterlord, a Ukrainian cybercriminal who used to work as an affiliate for the gang but has since retired (allegedly).
Breaches, hacks, and security incidents
Discord[.]io data breach: A threat actor has breached Discord[.]io, a popular third-party interface for the Discord IM service. The hacker is now selling the personal data of more than 760,000 of the site's users on an underground hacking forum. The company has confirmed the breach, took down its website, and posted a message for its users on the homepage listing all the information that was stolen. Stolen information includes names, emails, hashed passwords, Discord API keys, and billing addresses, among others. [Additional coverage in StackDiary]
Zunami Protocol crypto-heist: The Zunami Protocol has lost $2.1 million worth of crypto-assets after a hacker used a price manipulation attack to steal the funds. The company confirmed the attack and told users not to make any transactions on its platform. [Additional coverage in UnchainedCrypto]
New Haven BEC attack: The New Haven Public Schools district in Connecticut has lost more than $6 million following a BEC scam this year. The incident took place at the end of June, and New Haven mayor Justin Elicker says the city has managed to recover more than $3.6 million of the stolen funds so far. The FBI also froze an unspecified additional amount. The mayor says that while they don't believe city employees were involved in the hacks, they put an employee from the city's budget office on paid administrative leave until the investigation finishes. [Additional coverage in GovTech]
Clorox breach: Cleaning products maker The Clorox Company says it detected "unauthorized activity" on some of its IT systems. In an SEC filing, the company says it took down the affected systems and is now working with a cybersecurity company to investigate the incident. Clorox says it implemented workarounds for the affected systems, but it expects the incident to cause some disruption to parts of its operations.
Freeport hack: A cyberattack has disrupted the operations of Freeport-McMoRan. Impact on production is limited. [Additional coverage in IndustrialCyber]
Another FOI leak: The Norfolk and Suffolk police constabularies say they've leaked sensitive data via files uploaded on their Freedom of Information (FoI) websites. Officials say the data was hidden from view but should not have been in the files in the first place. The exposed data included the personal details of victims, witnesses, suspects, and their crimes. This included domestic violence cases, sexual offenses, assaults, and thefts. This is the second leak of its kind after the Police Service of Northern Ireland leaked data in a similar manner last week.
General tech and privacy
Cybersecurity standards for EV charging stations: The US National Institute of Standards and Technology (NIST) is seeking comments on a new cybersecurity framework for EV charging stations. The framework aims to identify cybersecurity risks and security measures that could impact the US' Electric Vehicle (EV) Extreme Fast Charging (XFC) infrastructure. [Additional coverage in LiveMint]
Experian spam: The US Federal Trade Commission says credit-reporting service Experian will have to pay a $650,000 civil penalty for spamming some of its customers. The FTC says that users who signed up on the ConsumerInfo.com website to freeze or manage credit information were spammed with Experian marketing emails with no way of opting out. Experian has agreed to pay the fine, and the company will also be barred from sending new marketing emails without a way for users to opt-out.
Government, politics, and policy
ExFiles to shut down: An EU-funded project named ExFiles has helped law enforcement agencies across Europe hack and gain access to hundreds of smartphones linked to criminal operations. The project launched in July 2020 and is scheduled to shut down in October this year as its EU funding runs out. The Dutch Forensics Institute has made a case for the project to receive new funding in light of its current success.
Cyber-war-gaming: In a discussion at the DEFCON security conference, CISA Director Jen Easterly warned (again) that China would very much consider launching destructive cyberattacks on American critical infrastructure, such as pipelines and railroads, in the case of an armed conflict or if it believes the US would intervene to defend Taiwan from an invasion. [Additional coverage in The Record]
China's earthquake center hack: Chinese authorities claim "US intelligence agencies" are behind the recent hacking of the Wuhan Earthquake Monitoring Center, and they plan to expose a "highly secretive global reconnaissance system of the US government." This comes from the Global Times, a state-controlled news agency that has a history of playing loosey-goosey with evidence and truth for the sake of state propaganda. We'll just have to wait and see what cyber literotica they publish this time. This is obvious clap-back propaganda for anyone paying attention. The sudden hacking of the Wuhan Earthquake Monitoring Center and China's efforts to portray the US as "going after civilian infrastructure" comes after the US government and Microsoft caught Chinese state-sponsored hackers (Volt Typhoon) breaking into US ports and other critical infrastructure and preparing for destructive attacks.
Afghanistan country-wide surveillance system: In a now-deleted tweet, the Taliban deputy interior minister said the government is working with Huawei to roll out a state surveillance system across every region of Afghanistan.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Jacob Torrey, Thinkst's Head of Labs. Jacob produces ThinkstScapes, a brilliant quarterly summary of the most interesting security research from around the world. Jacob talks about his favorite research in this edition, why Thinkst invests the time and effort in producing ThinkstScapes, and also talks about Thinkst Citation, a companion product that contains information about nearly 70,000 security talks going all the way back to 1993.
Cybercrime and threat intel
Two sextortionists extradited to the US: Two Nigerian men were detained and extradited to the US to face charges for their role in sexually extorting numerous young men and teenage boys across the United States. US officials say the two men bought hacked social media accounts and posed as young women in order to trick their victims into engaging in chats and sending sexually explicit images. The duo then used the received images to ask for huge payments, threatening to release collages of their explicit photos to classmates, friends, and family members. The DOJ says the two men sextorted more than 100 people and that a 17-year-old from Michigan took his own life after being extorted.
Malware gang detained in SG: Singapore police have detained ten suspects for their alleged involvement in a malware operation. The group allegedly used ads on social media to trick victims into installing malware on their smartphones. The malware allowed the group to make unauthorized bank transactions and then hide their traces by deleting email and SMS messages. Officials say that one of the gang's members is a minor and that they're also investigating six other suspects who have yet to be detained. [Additional coverage in The Straits Times]
Raccoon Infostealer coder close to extradition: A Dutch court has rejected a Ukrainian national's appeal against being extradited to the US to face charges for developing the Raccoon Stealer malware. The suspect, Mark Sokolovsky, 26, was detained in the Netherlands last October after trying to lose his trail by faking his death using comments posted on hacking forums. Following the rejection, Dutch officials are very likely to honor the extradition request and send the suspect to the US. Sokolovsky argued that he won't have a fair trial in the US and that detection in US prisons violates his human rights.
DDoS attacks motives: In a BlackHat talk, FBI special agent Elliott Peterson and Cameron Schroeder—chief of the cyber and IP crimes Section division at the Justice Department—said that most DDoS attacks they investigate are linked to petty disputes between children or attempts to sabotage a competitor's business and siphon customers. [Additional coverage in The Record]
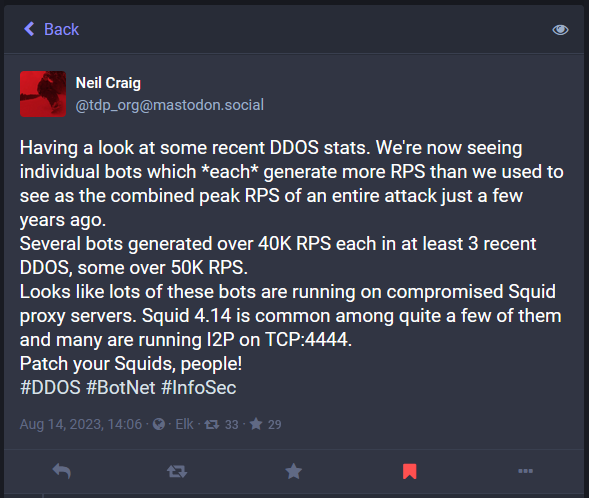
Squid bug exploited in DDoS attacks: DDoS botnet operators are using Squid proxy servers to generate a large number of requests from one single bot and launch large-scale DDoS attacks. According to BBC IT expert Neil Craig, one individual bot is now generating as much as 40k or 50k requests per second, which was the RPS of some DDoS attacks a few years back.
Beta mobile apps abuse: The FBI warns that cybercrime groups are using beta versions of mobile apps to sneak malware on user devices. Officials say they've seen phishing campaigns and romance scammers use this method to deploy malware on victim devices, collect personal data, and steal cryptocurrency. The technique is efficient because mobile operating systems don't scan beta apps for threats.
CPABuild scam network: An investigation from ad security firm Human has uncovered that an advertising company named CPABuild is playing a central role in helping promote online scams in what researchers call a "Malicious-Marketing-as-a-Service." Researchers say CPABuild has helped threat actors accurately target children with scams for Fortinet and Roblox giveaways. Human says many of these scams are hosted on hacked websites, including US government websites, to which CPABuild helps the threat actors funnel legitimate traffic. In addition, newer CPABuild customers also include a threat actor that specifically goes after individuals searching for "anti-China / anti-CCP news articles." [Additional coverage in Human]
Manipulated Caiman spam list: A list of more than 40 million email addresses used by the Manipulated Caiman spam group has been added to the Have I Been Pwned database.
Hacking forum credentials: Threat intel firm HudsonRock says it has found more than 120,000 credentials for accounts on hacking forums being sold or shared online. The vast majority of these accounts are for Nulled, followed by Cracked, and then HackingForums, all three hacking forums that have been around for more than a decade.
Malware technical reports
Underground ransomware: SecurityScorecard's Vlad Pasca has analyzed Underground, a new ransomware operated by the Storm-0978 (RomCom) group, believed to be a successor of the older IndustrialSpy ransomware. The ransomware is also known as TeamUnderground.
Monti's Linux ransomware: The Monti ransomware gang has developed a new encrypter for locking data on Linux-based systems.
JanelaRAT: Zscaler says it identified a malware campaign targeting fintech users in Latin America with a new remote access trojan named JanelaRAT.
Gigabud RAT: Group-IB has discovered a powerful new malware named Gigabud, a remote access trojan for Android devices. The malware has been used to target mobile banking customers across Southeast Asia.
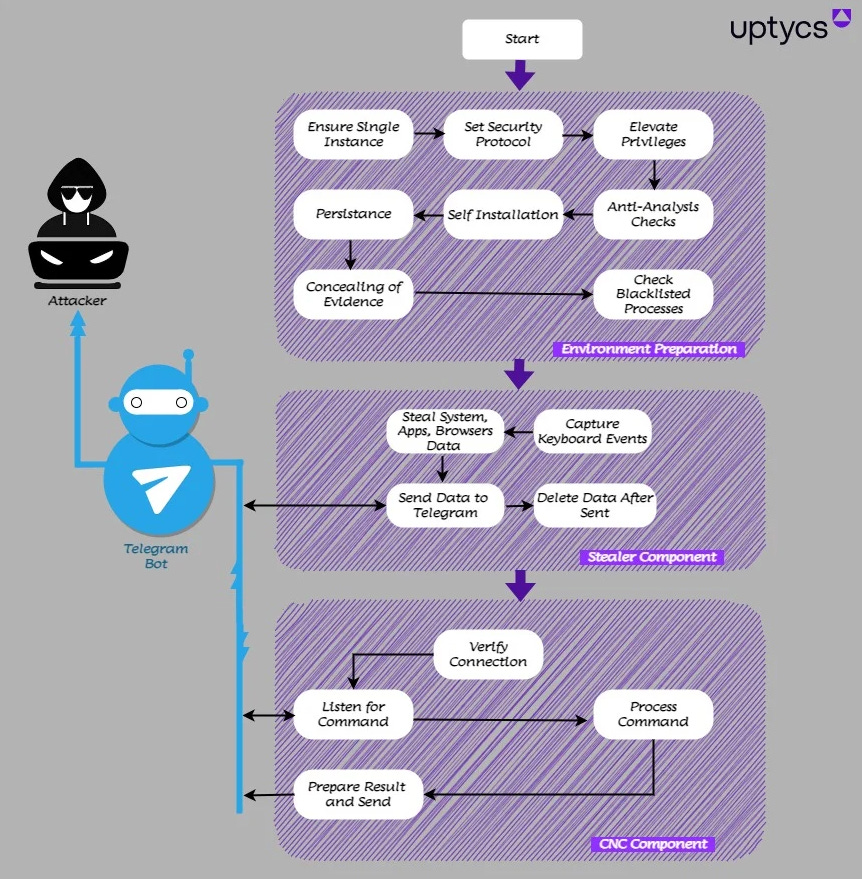
QwixxRAT (Telegram RAT): Cloud security firm Uptycs has discovered a new RAT being distributed in the wild. The malware is named QwixxRAT and has been primarily used to infect users of the Telegram and Discord platforms.
Sponsor Section
This is a section where we typically feature one of our sponsor's products. This time, we're gonna feature a tip on how to use Thinkst's canaries to spot "canary text files" being opened from the terminal, a typical giveaway of threat actor activity.
Vulnerabilities, security research, and bug bounty
GitHub bug bounty: GitHub says it awarded more than $1.5 million in bug bounties last year, covering more than 364 vulnerabilities in its platform. The sum represents 40% of the total rewards the company awarded to researchers since it started it program nine years ago. In total, GitHub has awarded more than $3.8 million to researchers since October 2016.
CS:GO infoleak: CounterStrike players have found a vulnerability in the CS:GO game that can allow threat actors to leak a player's IP address. The vulnerability impacts the game's Competitive mode and can be exploited by players in the same lobby. [Additional coverage in Dexerto]
Terrasoft/Creatio zero-days: Russia's CERT team (NKTsKI) says it is aware of attacks against Terrasoft CRMs and Creatio BPMs exploiting an unpatched zero-day vulnerability. The NKTsKI says the vulnerability "allows unauthorized access to the ConnectionStrings.config file" in both applications but did not provide any other details. The agency says that because Terrasoft ceased activities in Russia and Belarus after March 2022, Russian companies should take their own protection measures, such as taking vulnerable products off the internet or "consider switching to domestic counterparts." The agency didn't specify if it reported the zero-day to Creatio, a company with Ukrainian roots. Because of the possible political drama, take the "zero-day" report with a grain of salt unless confirmed from second and more credible sources.
Citrix exploitation: Dutch security firm Fox-IT says that of more than 31,000 Citrix NetScaler ACD devices that were exposed online last month, almost 1,900 devices are showing signs they've been hacked and backdoored by threat actors using the CVE-2023-3519 vulnerability. The company says that even if more than 1,200 devices have been patched, the backdoor still persists on the devices, keeping them open to remote access and attacks. Both Fox-IT and Mandiant have released tools that can scan NetScaler systems for the tell-tale signs of backdoors and web shells.
NRSW vulnerabilities: A race condition (CVE-2023-0861) has been discovered in the NetModule Router Software (NRSW), a software-based router for Linux-based systems.
DoubleDrive attack: At the Black Hat security conference, SafeBreach security researcher Or Yair showcased DoubleDrive, a technique that can turn the Microsoft OneDrive utility into ransomware.
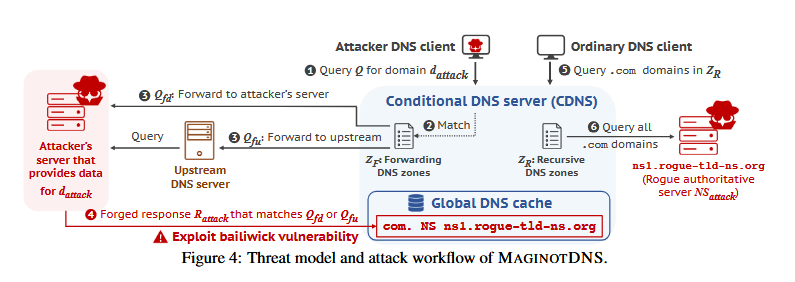
MaginotDNS: A team of academics has discovered a powerful cache poisoning attack against DNS servers. Named MaginotDNS, the attack impacts DNS servers that work as recursive resolvers and forwarders at the same time, also known as conditional DNS (CDNS) servers. The MaginotDNS attack exploits gaps in how DNS software runs and controls what requests the server can respond. The attack allows threat actors to poison the DNS cache and have the server redirect legitimate traffic to malicious locations. An internet scan conducted by the research team found that more than a third of all CDNS servers worldwide are vulnerable to MaginotDNS attacks. To prevent exploitation, the researchers helped patch bugs in DNS software like BIND, Technitium, and the Knot Resolver.
Infosec industry
Secureworks layoffs: Cybersecurity firm Secureworks plans to lay off 15% of its workforce, the company announced in an SEC filing.
New tool—Citrix Scanner: Google's Mandiant division has released a tool that can scan Citrix NetScaler ADC appliances for signs of exploitation via the CVE-2023-3519 vulnerability.
New tool—Citrix NetScaler Triage: Same as above, but from NCC Fox-IT.
New tool—Veilid: The Cult of the Dead Cow has open-sourced Veilid, a protocol and framework for building encrypted social media applications.
New tool—gssapi-abuse: Ceri Coburn, offensive security dev at Pen Test Partners, has open-sourced a tool named gssapi-abuse for enumerating hosts that are open to GSSAPI abuse within Active Directory networks.
DEFCON CTF: Carnegie Mellon University's team, the Plaid Parliament of Pwning (PPP), won its seventh title in the yearly DEFCON Capture The Flag contest, the most in the competition's history.
DEFCON shenanigans: DEFCON attendees were evacuated on Sunday after a fake bomb threat.
More DEFCON shenanigans: A security researcher at the DEFCON hacking conference decided to prove that turning off Bluetooth from the iOS Control Center doesn't actually turn off Bluetooth by spamming conference attendants with a crafty pop-up asking them to connect to a fictitious Apple TV. [Additional coverage in TechCrunch]
"The researcher said that to stop these pop ups someone needs to turn off Bluetooth via the Settings app, not from the Control Center, which users can invoke by swiping down from the top right corner of the iPhone."

Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at why 'juice jacking' is a forever fear even though it's not a real-world threat.




