Risky Biz News: Ukraine wants Sandworm hackers tried at The Hague
In other news: Google fixes two Pixel zero-days used to unlock devices; Chinese devices multiplying on US and UK networks; Windows 10 ESU prices are out!

This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

The Ukrainian government is gathering evidence and intends to file a war crimes case against Russian military hackers at the International Criminal Court in The Hague.
The case will center around the December 2023 cyberattack against Kyivstar, Ukraine's largest mobile operator.
Russia hackers breached the company in May of last year, gathered data, and then wiped thousands of servers on December 12.
The attack disrupted mobile services for the Ukrainian population for days as the operator raced to rebuild affected systems.
Speaking at a conference in February this year, Kyivstar CEO Oleksandr Komarov said the hack could have been catastrophic, as Russian hackers attempted and failed to wipe more than 100,000 base stations. If these mobile towers would have been affected, it would have taken the company months to restore service.
In light of the incident's destruction and broad impact on its civilian population, Ukrainian officials hope to have the cyberattack labeled as a war crime. They are pinning their hopes on a statement from ICC prosecutor Karim Khan.
"There is an official statement by ICC prosecutor Karim Khan, where he says cyber attacks on civilian infrastructure, energy, gas supply stations, and telecom operators can be recognized as war crimes," Ilya Vityuk, head of the SSU Cybersecurity Department, told UkrInform in an interview this week. [machine translated quote]
Even if a hacktivist group named Solntsepek took credit for the Kyivstar incident, Ukrainian officials were quick to dismiss the claims and attributed the hack from the get-go to Russian military hackers, and specifically to a group known as Sandworm.
Specifically, Vityuk claims that Sandworm is operated by members of GRU Unit 74455.
Despite Ukraine's hopes, the case faces several major hurdles.
The first is reports from earlier this month that the Ukrainian military is using smartphones deployed on tall poles across the country to detect the loud sound of incoming Shahid drones. Ukrainians were doing this to use cheaper artillery options instead of expensive air-defense missiles to shoot down some of Russia's drone arsenal. This, while used for an honest defensive purpose, puts Ukraine's mobile network on a list of military targets, which may be a loophole Russia may use to have the case dismissed.
War crimes cases hinge on the notion that victims are not legitimate military targets during war time.
The second major hurdle in Ukraine's case is that, itself, retaliated with destructive cyberattacks against Russian ISPs.
In January, Ukraine's military intelligence service GUR said it worked with a group of "unknown cyber volunteers in Russia" to cripple the infrastructure of Akado-Telekom, an ISP used by the Putin administration, the FSB, the FSO, the Moscow local administration, and Sberbank.
Ukraine may argue the attack targeted Akado's Russian government customers. It was part of a larger offensive cyber campaign that also targeted Russia's federal tax service, a major defense contractor, and a Russian military system used to manage and control DJI drones.
Just like in Kyivstar's case, Akado was down for weeks, including for regular Russian customers, a simple argument and case Russia can easily bring up for itself as well.
It's Ukraine's right to bring the case, but it may not be as clear as it anticipates.
Ukraine's efforts add to a 2022 effort from a group of human rights lawyers who were also looking into bringing Sandworm hackers in front of the ICC for some of its older operations.
Obvious IANAL disclosure. This is a cybersecurity newsletter after all.
Breaches, hacks, and security incidents
Russia PGO hack: A hacktivist group named RGB-Team has taken credit for hacking Russia's Prosecutor General's Office. The group has leaked on Telegram more than 100,000 criminal records for crimes committed in Russia over the past 30 years. The RGB-Team is the latest hacktivist group to join in attacks targeting Russia. The group previously claimed it also hacked Russian security firm Kaspersky. [Additional coverage in Important Stories]
FixedFloat crypto-heist: Hackers have stolen $3 million worth of assets from the FixedFloat cryptocurrency exchange. The company claims the hackers exploited a vulnerability in a third-party service they were using. FixedFloat believes it was hacked by the same group that breached its systems earlier this year. It previously lost $26 million in February. [Additional coverage in ConDesk]
SurveyLama data breach: Paid survey website SurveyLama suffered a data breach that exposed the data of 4.4 million customers. Exposed data includes names, emails, home and IP addresses, and hashed passwords. The incident took place in February, and the data is now being sold on hacking forums.
Hoya cyberattack: Japanese optical products manufacturer Hoya went down this week following what the company described as an "IT system incident" that is likely a cyberattack. [Additional coverage from Piyolog]
Omni Hotels cyberattack: The Omni Hotels & Resorts chain has blamed a recent IT outage on a cyberattack [archived] that took place at the end of March.
NYCAPS/ESS incident: The payroll website for the city of New York has been down for more than a week following a phishing attack. [Additional coverage in Politico]
IxMetro Powerhost ransomware attack: A threat actor has compromised and deployed ransomware on the servers of Chilean cloud hosting provider IxMetro Powerhost. The attacker deployed a new ransomware strain named SEXi that encrypted the company's VMware ESXi servers and backups. The company's CEO declined to pay a ransom. The ransomware gang allegedly requested two bitcoins for each of the company's customers, which would have amounted to $140 million. [Additional coverage in BleepingComputer]
Jackson County ransomware attack: Government offices across Jackson County in Missouri were closed this week after the county suffered a ransomware attack. The incident took place on April 3, and officials shut down all systems to prevent a larger impact. Jackson County is the second-most populous county in the state, with a population of over 715,000.

General tech and privacy
Windows 10 ESU prices: Microsoft will offer security updates for Windows 10 past its end-of-life date for $61/system/year. The price will double for the second year and double again for the third year for $122 and then $244/system/year. Windows 10 will reach end-of-life on October 14, 2025. Organizations in the educational sector will only have to pay $1/system/year as part of a special offer.
Ubuntu release delayed: Canonical has delayed the release of Ubuntu Noble Numbat so its security team can look closer at the XZ backdoor incident. The release has been pushed back for a week, from April 4 to April 11.
Firefox+Qwant: Mozilla has announced support for the Qwant privacy search engine in its Firefox browser.
Government, politics, and policy
German Cyber Force: The German government is overhauling its military and plans to add a dedicated branch for cyberspace. Officials say the cyberspace branch will focus on hybrid threats such as disinformation campaigns. The overhaul is in response to Russia's invasion of Ukraine and ahead of a possible military conflict. [Additional coverage in Reuters]
MP spear-phishing attack: British police have launched an investigation into an apparent spear-phishing attack that has targeted multiple MPs. At least 13 MPs and Parliament staff workers received unsolicited WhatsApp messages from the same two phone numbers over the past six months. One of the victims has been identified as a serving government minister. [Additional coverage in The Guardian]
Ukraine rewards foreign hackers: The Ukrainian government has sent out official awards to a foreign hacktivist group named OneFist. The OneFist group has stolen data from Russian military firms and hacked cameras to spy on Russian troops. According to the BBC, the group is made up of hackers from eight countries, including the US and the UK. This marks the first official government award given out to foreign hackers for offensive cyber operations during a war.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely co-founder and CEO Travis McPeak about how the DevOps ecosystem has evolved and ushered the need for DevSecOps and how the company provides and manages its secure-by-default templates.

Cybercrime and threat intel
Google sues crypto-scammers: Google has filed a lawsuit against two Chinese nationals for developing and uploading crypto scam apps on the Play Store. The company says the two created 87 cryptocurrency trading apps that stole money from their users. Google says the apps were downloaded by more than 100,000 people since 2019. Victims lost between $100 to tens of thousands of dollars each. [Additional coverage in The Verge]
Threat/trend reports: BI.ZONE, the Cloud Security Alliance, Google TAG, and Sophos [1, 2] have recently published reports covering infosec industry threats and trends. The most interesting of these is the second Sophos report that claims that a third of ransomware attacks begin with attackers exploiting an unpatched vulnerability.
YouTube malware campaigns: Proofpoint has looked at one of the many YouTube videos promoting game cracks and cheats that actually contain malware. 2010 called, it wants its malware trends back!
P4x profile: Wired has published a profile on P4x, the hacker who took down North Korea's internet back in January 2022.
"P4x's real identity, revealed here for the first time, is Alejandro Caceres, a 38-year-old Colombian-American cybersecurity entrepreneur with hacker tattoos on both arms, unruly dark brown hair, a very high tolerance for risk, and a very personal grudge."
CoralRaider: Cisco Talos has published a report on CoralRaider, a new Vietnamese financially-motivated threat actor. The group has been active since 2023 and it focuses on stealing victims' credentials, financial data, and social media accounts, including business and advertisement accounts. The group's main tools are the XClient stealer and RotBot, a customized variant of QuasarRAT.
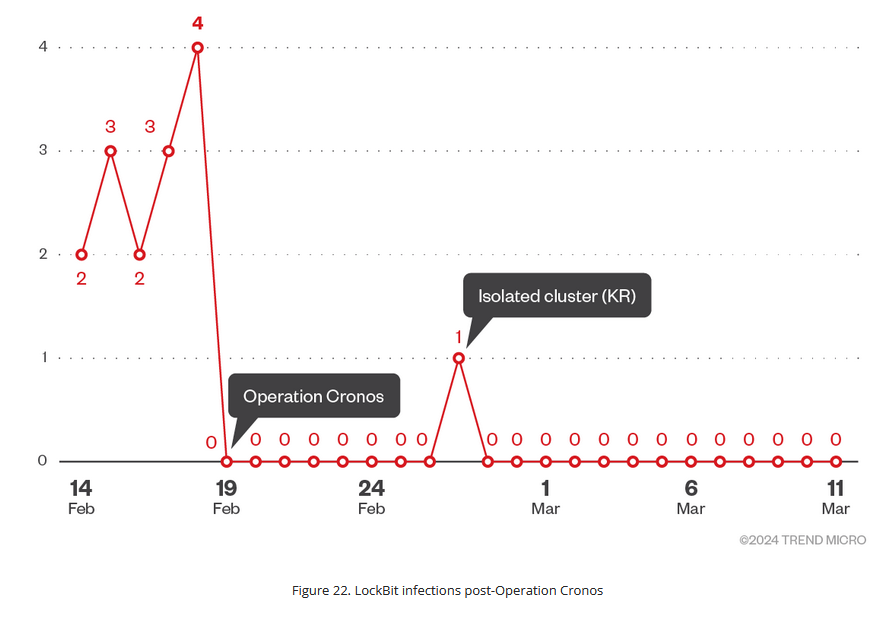
LockBit disruption was successful: A Trend Micro investigation has found that the LockBit ransomware gang has ceased almost all activity in the aftermath of a law enforcement takedown. Almost two months after Operation Cronos, the LockBit gang is rarely launching attacks and new victims to its leak site. The report contradicts the LockBit admins who repeatedly claimed the Europol and FBI takedown had minimal effects on their operations. Trend Micro says LockBit admins are now banned on major hacking forums and are relisting old victims on their leak site to simulate attacks.
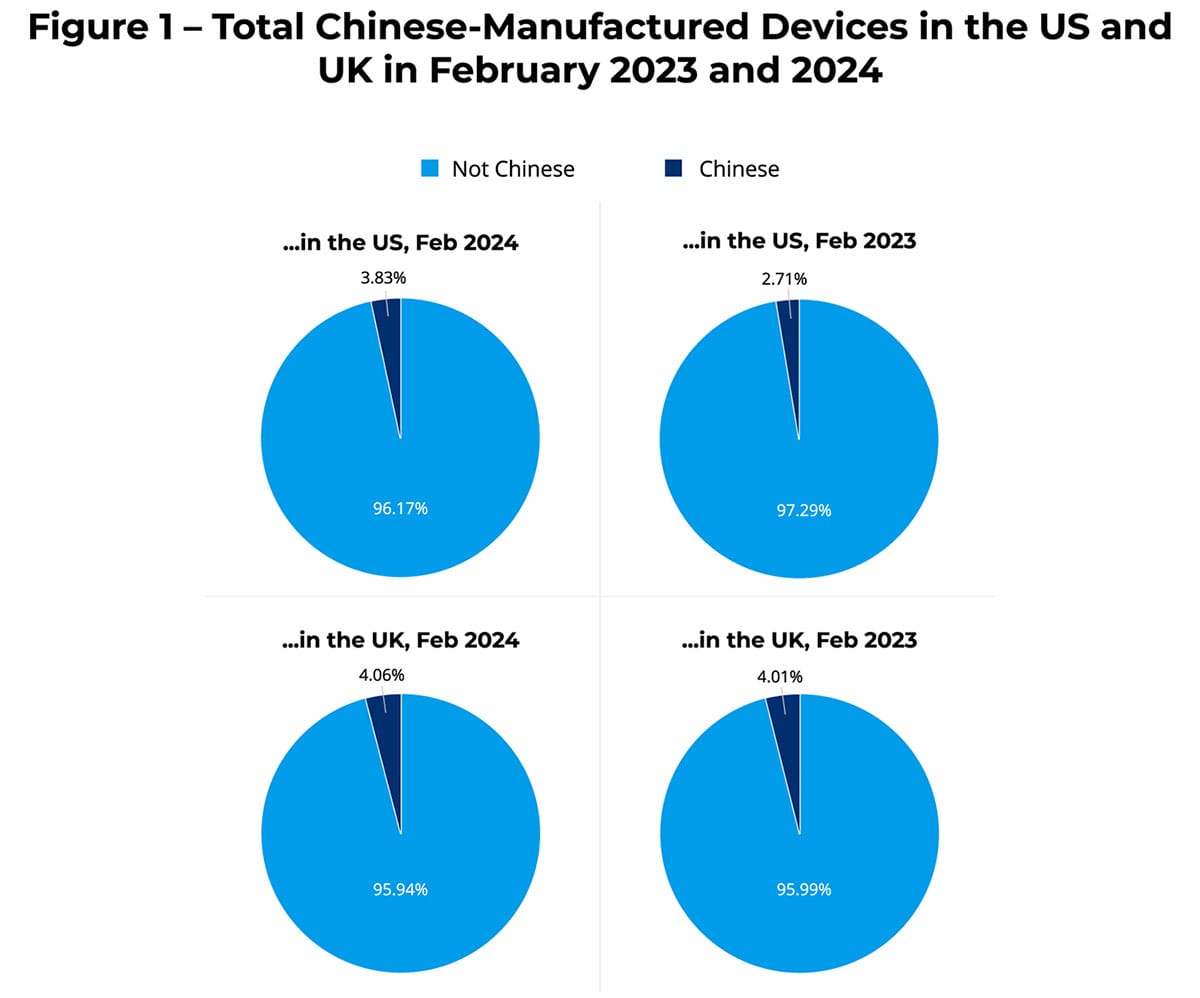
Chinese devices on US networks: The number of Chinese-made devices on US networks has increased the government's efforts to ban some devices. Forescout has seen close to 300,000 devices from 473 different Chinese companies. The number is up from 185,000 devices recorded in February of last year. Forescout saw a similar spike on UK networks, where the number of devices doubled to 20,000 devices this year.
Malware technical reports
XZ backdoor: Wiz researchers have reversed-engineered the XZ Utils backdoor and found artifacts and opportunities for detection.
Shoplift: Sucuri has published a report on Shoplift, a new card skimmer malware family that has been found on both Magento and WordPress e-commerce sites.
SilverFox: Qihoo 360 has published a report on new campaigns delivering the SilverFox trojan to Chinese users. This is a malware strain active primarily in China.
Qakbot: BinaryDefense takes a look at new Qakbot versions, another sign the malware botnet appears to have returned to its full strength after last year's takedown.
PikaBot: McAfee looks at the recent trends in malspam campaigns that distribute the PikaBot malware.
MatanBuchus: Embee researchers have identified new infrastructure used by the MatanBuchus malware gang after analyzing the malware's previous domain TLS certificates.
Latrodectus: Proofpoint has spotted a new advanced malware strain named Latrodectus being distributed in the wild. The malware has been active since November of last year, and campaigns have picked up this year. Proofpoint says two major threat actors (TA577 and TA578) have already adopted the malware. The company says Latrodectus infrastructure overlaps with old IcedID servers and was likely created by IcedID developers.
Rhadamanthys Stealer: Cofense looks at a campaign distributing the new and updated version of the Rhadamanthys Stealer. There's a report on the same malware from AhnLab, too.
Chaos ransomware: Sonicwall has spotted a new ransomware strain built on the leaked Chaos ransomware builder. The company contacted the author via Discord, and it appears this may not be the professional RaaS we thought it would be, as the author gave out the private decryption key following a short conversation.
Sponsor Section
Setting up infrastructure is complex, and improper configuration is a bane to developers, security teams, and DevOps/platform teams everywhere.
❌ Wasted development time
😢 Platform teams stuck in ops mode, support developers
🔓 Unnecessary incidents
See why your team is wasting thousands of hours and millions of dollars, and how Resourcely can help you avoid misconfiguration.
APTs, cyber-espionage, and info-ops
North Korea's Python payloads: Norfolk Infosec has published a technical report looking at payloads North Korean hackers have tried deploying on infected systems as part of their supply chain attacks targeting the Python and Node.js developer community.
"Many of the Python modules authored by this threat actor employ simple techniques. It is unclear if this is to maximize the speed and efficiency of developing new code, or if this was simply a choice the threat actors made in order to drop files that appear more legitimate onto impacted devices."
Sidewinder: StrikeReady researchers have a general report on Sidewinder, a suspected Indian APT group.
Lazy Koala: Russian security firm Positive Technologies has discovered a new APT group named Lazy Koala. The group began operations this year and has primarily targeted government employees in Russia, Belarus, and other CIS states. The group uses basic spear-phishing and a malware strain named LazyStealer to steal and send data to remote Telegram channels. Despite its low sophistication, PT researchers say the group's operations have turned out to be "productive."
Vulnerabilities, security research, and bug bounty
Pixel zero-days: Google has fixed two zero-day vulnerabilities impacting the company's line of Pixel smartphones. According to the makers of GrapheneOS, the two zero-days were being used by mobile forensics firms to bypass authentication and unlock Pixel devices. The two zero-days only impact Google Pixel devices and are not included in this month's Android monthly security update.
Major Flowmon vulnerability: Progress Software has patched a major vulnerability in the Flowmon network monitoring suite. The vulnerability (CVE-2024-2389) resides in the software's web management panel. It allows remote unauthenticated attackers to execute commands on unpatched systems. The vulnerability has a CVSS severity score of 10/10.
Apache Pulsar security update: The Apache Pulsar project has released a rare security update to patch a security issue. The vulnerability is tracked as CVE-2024-29834. Apache Pulsar is an open-source, distributed messaging and streaming platform built for the cloud.
Ivanti security updates: Ivanti has released patches for four vulnerabilities impacting its Connect Secure and Policy Secure products. The company says that none are exploited in the wild (for now 😁).
Older Ivanti attacks: Mandiant has published its fourth part of recent attacks that have targeted Ivanti Pulse Secure VPNs (with CVE-2023-46805 and CVE-2024-21887).
Cisco security updates: Cisco has released 12 security advisories for its products this week.
TeamCity vulnerability: CyFirma researchers have put out a report looking at attacks exploiting a recent vulnerability (CVE-2024-27198) in JetBrains TeamCity servers.
Magento attacks: Sansec researchers have spotted a threat actor exploiting a Magento bug tracked as CVE-2024-20720 being abused in the wild for the first time to backdoor e-commerce sites.
Kobold letters: Lutra Security has discovered a new attack that can hide email content based on the context it is viewed in. The attack is named Kobold Letters and takes advantage of the ability to use CSS code to stylize email content. Lutra researchers have found that email clients treat CSS differently, and some styles will be applied incorrectly when an email is forwarded, allowing attackers to hide or unhide malicious content. Vulnerable email clients include Gmail, Outlook on the Web, and Mozilla Thunderbird. None of the vendors plan to release fixes.
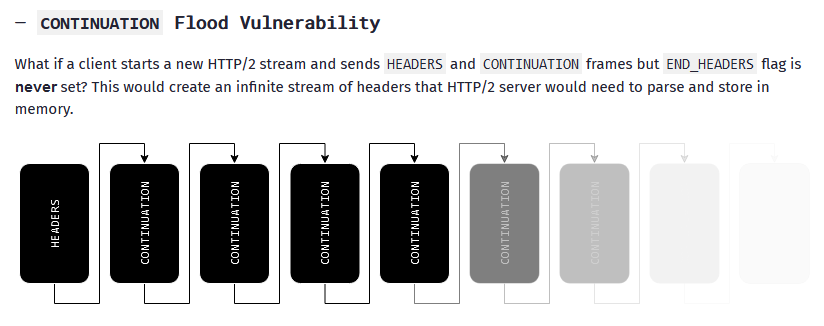
HTTP/2 CONTINUATION Flood attack: A security researcher has discovered a new DDoS attack vector in the HTTP/2 protocol. The attack is named HTTP/2 CONTINUATION Flood. It allows attackers to send an unending stream of HTTP/2 CONTINUATION frames that keep connections alive and flood servers. The new DDoS attack vector impacts HTTP/2 implementations across most programming languages and server technologies. At least nine CVE identifiers have been issued for impacted technologies so far.
CVE history & trends: In recent light of NIST's problems with keeping the NVD up to date, VulnCheck's Patrick Garrity looks at the database's evolution over the past few years.
Infosec industry
New tool—Access: Discord's dev team has open-sourced a tool named Access, a centralized portal for employees to transparently discover, request, and manage access to all internal systems needed to do their jobs.
NDSS 2024 videos: Talks from Network and Distributed System Security (NDSS) Symposium 2024, which place at the end of February, are available on YouTube.
Risky Business Podcasts
Listen to Resourcely CEO Travis McPeak talk with Risky Business Snake Oilers host Patrick Gray about the company's automagic Terraform cloud-provisioning technology.





