Risky Biz News: Cyber Partisans hack Belarus KGB
In other news: Avast gets a €14 million GDPR fine; new Pathfinder side-channel attack; Ukrainian hackers wipe another Russian telco.

This newsletter is brought to you by Socket, a developer-first security platform that prevents vulnerable and malicious open-source dependencies from infiltrating software supply chains. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Belarusian hacktivist group the Cyber Partisans claims to have hacked Belarus' national intelligence agency, the Belarusian KGB.
The group says it breached the agency in the fall of 2023 and exfiltrated data from its official website.
The intrusion went undetected for months until earlier this year, when the KGB put its website into maintenance mode—in which it remained to this day.
Over the weekend, the Cyber Partisans have leaked a copy of the site's database and its server logs.
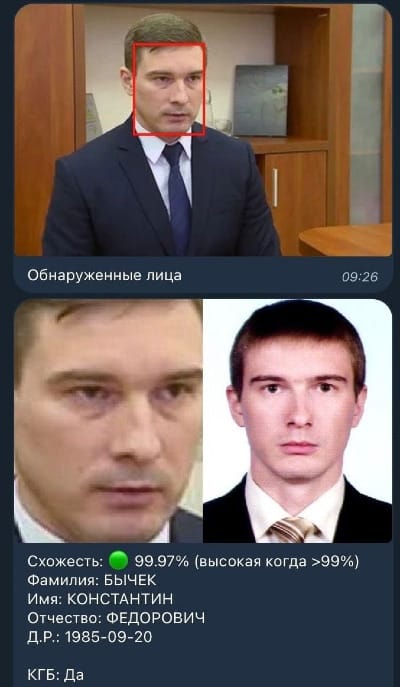
The Cyber Partisans also claim they obtained the personal details of over 8,600 current and former KGB employees. This data allegedly includes names, dates of birth, and photo IDs.
The group used the data to create a Telegram bot. The bot allows Belarusian citizens to upload photos and face-match it against the KGB database to detect if someone is part of the agency's staff.
The bot is still live, but Telegram is known to have cracked down on channels that provide this kind of LEA deanonymization services before.
The Cyber Partisans group launched operations in the fall of 2020 after the Lukashenko regime lost and refused to acknowledge the results of the 2020 elections and took forceful control of the country.
Since its launch, the group has launched cyber operations that were carefully planned to show dissent and disrupt the dictatorship's control over the country. Their activities intensified after Russia's invasion of Ukraine and after Russia used Belarus' territory to move troops and mount attacks.
Some examples of past operations include attacks that targeted the country's railway system (to disrupt Russia moving its troops through Belarus), the country's national news agency (to counter the spread of Russian propaganda), or the country's biggest fertilizer plant (as revenge after the plant's management was involved in political repression against employees who protested Lukashenko).
Occasionally, they also hit some Russian targets, such as the Russian General Radio Frequency Center (GRFC), a smaller sub-agency that's part of the Roskomnadzor, the Kremlin's telecommunications watchdog.
But the group's most known hack was its compromise of Belarus' passport database, with the group later releasing passport copies for the country's government officials as an NFT collection. A solid 10/10 on the troll scale.
Despite some solid efforts from Belarusian officials, the identity of Cyber Partisan members has remained a secret. If either Russian or Belarussian services know who the group's members are, they have not hinted of anything of the sort yet.
The only remark the Belarusian government has made was to call the group a "terrorist organization" or "NATO/foreign hackers"—a now-standard statement both the Russian and Belarusian governments use to describe anyone or anything that opposes them.
Breaches, hacks, and security incidents
Piping Rock: Online health products store Piping Rock had the details of 2.1 million customers dumped on a hacking forum.
StarWallets crypto-heist: A threat actor has stolen $9.6 million worth of crypto-assets from DeFi platform StarWallets. The incident took place on April 17, and the platform says it suffered "substantial liquidity losses." More than a week after the attack, the platform is still down.
Philadelphia Inquirer breach: The Philadelphia Inquirer newspaper says that the data of more than 25,500 subscribers and current and former employees was stolen in a May 2023 security breach.
MTT hack: Ukrainian hacktivist group the BO Team claims to have hacked MTT, a subsidiary of Russian telecom provider MTS. The attack took place on the night between April 26 and 27. The group says it wiped IT infrastructure and caused internet outages across multiple Russian cities, including Moscow and Sankt Petersburg. The BO Team says it conducted the hack together with Ukraine military intelligence agency GUR. [Additional coverage in RBC.ua/ English coverage in KyivPost]
United Russia cyberattack: Ukraine military intelligence agency GUR says it carried out a "large-scale cyberattack" on the server infrastructure of Russian political party United Russia. No other details were provided. [Additional coverage in Radio Svoboda]
General tech and privacy
Avast gets GDPR fine: The Czech data protection agency has fined cybersecurity firm Avast €14 million for violating EU GDPR rules. The agency says Avast lied to customers on multiple counts on how it dealt with their personal data. The UOOU says Avast told customers it was only collecting data for statistical analysis but secretly sold it to third parties. It also lied that data would be anonymized. This is Avast's second fine for this infringement. It was also fined $16.5 million in the US earlier this year.
Mastodon 501(c)(3): Mastodon has established a new US 501(c)(3) non-profit to be able to receive tax-deductible donations. One of the five members of its new Board of Directors is former Twitter co-founder Biz Stone. The move comes after German authorities withdrew the platform's non-profit status with no explanation or advanced notice.
New App Store policy: Apple will start enforcing a new App Store policy on May 1 with new rules for apps that use third-party SDKs. Developers will have to provide valid reasons why they access each API and sign any SDK they use. They will also have to use privacy manifests, which are files that describe the privacy practices of any third-party code used in their apps.
Government, politics, and policy
CISA RVWP 2023 results: US organizations patched vulnerable devices only half the time after receiving a security alert from CISA. The agency sent 1,754 notifications about unpatched devices to organizations last year, but only 49% of vulnerable systems were patched. The notifications were sent part of the Ransomware Vulnerability Warning Pilot. CISA established the program in March last year to warn companies about unpatched devices that are commonly exploited by ransomware gangs.
US mull DJI ban: The US government is considering legislation that would ban DJI drones from running on US telco networks. Officials say the company poses a national security threat as it can collect data on US critical infrastructure. The legislation is known as the Countering CCP Drones Act and would effectively kill the company's business in the US. The US government added DJI to its entity list in 2020. The designation bans US companies from exporting technology to the Chinese company. [Additional coverage in The Verge]
Google lays off Python team: There are reports that Google has laid off its internal Python team. This team maintained the company's custom version of the Python programming language, which Google uses for almost all of its major services. [Additional coverage in the Free Press Journal]
Meta threatens to leave India: Social media giant Meta has threatened to pull out of the Indian market if the government moves forward with a plan to force the company to break encryption on its messaging apps. Meta has said the first service to leave the country would be WhatsApp. The company and the Indian government are scheduled for a showdown in court related to India's 2021 IT rules for social media. According to the new rules, the Indian government is demanding that social media networks provide information on the source of information they deem "fake" or "hate speech." [Additional coverage in the Business Standard]
Belarus adds cyber to military doctrine: The Belarusian government has updated its military doctrine to allow for the use of military force in response to foreign cyber attacks. A similar provision exists in the NATO treaty but not in Russian military doctrine. [h/t Oleg Shakirov]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to CEO and founder of Socket, Feross Aboukhadijeh about the open source software and supply chain security. Feross says the software ecosystem has evolved in ways that make it more vulnerable to trust-based attacks (such as seen in XZ Utils) and discusses what can be done to defend against this type of supply chain subversion.

Cybercrime and threat intel
DraftKings hacker pleads guilty: A 21-year-old from Memphis, Tennessee, pleaded guilty to hacking-related charges. US prosecutors say Kamerin Stokes was part of a three-man group that launched credential-stuffing attacks against DraftKings in November 2022. Stokes went online as TheMFNPlug and operated an online shop where his co-conspirators sold the hacked accounts. Authorities charged Stokes in January this year, weeks after the gang's leader was sentenced to 18 months in prison.
USPS phishing campaign: Akamai has uncovered a massive phishing campaign targeting USPS customers. The campaign has been active since the 2023 holiday season and is still ongoing. Akamai says the campaign has sometimes generated more traffic to its phishing sites than all the traffic to the real USPS homepage.
UA campaign: DeepInstinct looks at a malspam campaign using Signal messages to spread boobytrapped Office documents to targets in Ukraine. The company didn't attribute this to any group.
New crypto scam: The SlowMist security team has discovered a new type of scam targeting cryptocurrency users. The scam involves temporarily modifying Ethereum node Remote Procedure Calls (RPC) to deceive users that funds have been deposited in their wallets. The scam is used in the real world, where users exchange services or products for cryptocurrency. By the time users realize a transaction is fake, the scammer has long disappeared.
Okta reports "unprecedented" attacks: Identity service provider Okta has reported seeing an "unprecedented scale" of credential stuffing attacks targeting its platform from residential proxy providers.
Research lab guidance: Canada's cybersecurity agency has published guidance on the cyber threats to the country's research laboratories.
New npm malware: Twenty-five malicious npm packages were discovered last week. Check out GitHub's security advisory portal for additional details.
Threat/trend reports: BeyondTrust, Coalition, Cyberint, Dragos, EAST (PDF), Honeywell, NCC Group, and Zscaler have recently published reports covering infosec industry threats and trends. Summaries of the most interesting ones are below.
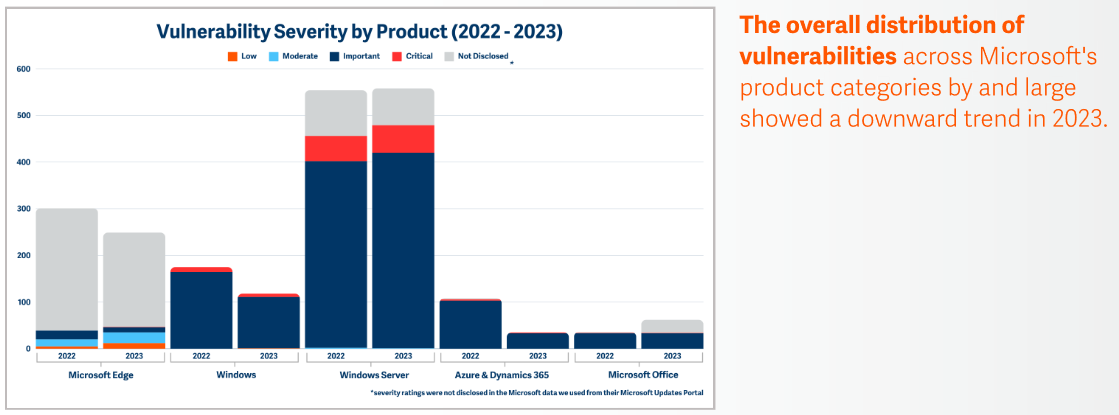
More than 1,200 vulnerabilities were reported and fixed in Microsoft products last year, according to security firm BeyondTrust. The number has remained steady around the 1,200 mark for the fourth year in a row. The most common vulnerability was Elevation-of-Privilege, which accounted for 40% of all security bugs. Another trend observed last year is a major drop in Azure vulnerabilities, which halved from the previous year.
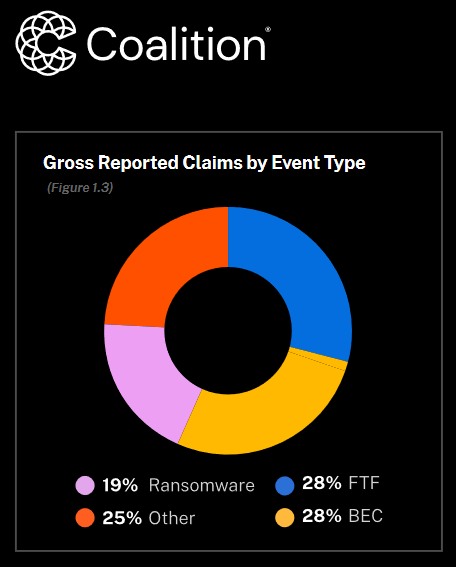
BEC scams and other types of funds transfer fraud accounted for more than half of cyber insurance claims last year, according to cyber insurance provider Coalition. Ransomware accounted for only a fifth of all claims but was the largest source of claims by severity. Coalition said that organizations using select boundary devices were at a greater risk last year. This included organizations running Cisco ASA, Fortinet devices, or RDP endpoints. The insurance provider says that businesses with internet-exposed Fortinet devices were twice as likely to experience a claim last year.
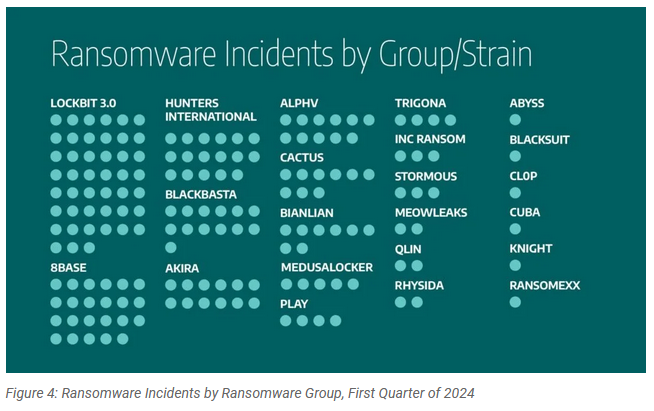
ICS security firm Dragos has observed a decline in ransomware activity targeting critical industrial sectors in the first quarter of the year. Of the 77 ransomware groups known to target ICS verticals, only 22 were active this year. Dragos recorded 169 incidents but none that caused any major disruptions to operational networks. LockBit was the most active group before its law enforcement takedown in February. The security firm says it spotted a significant shift in ransomware attacks from the ICS sector to healthcare at the start of this year.
Malware technical reports
Redline: ANY.RUN looks at the recent versions of the Redline infostealer that have been spotted using Lua bytecode to hide itself.
Fletchen Stealer: CyFirma researchers have published a report on v2 of the Fletchen Stealer, an infostealer that's been around since last year.
FakeBat: eSentire researchers warn of a Google malvertising campaign for fake browser updates that tries to infect users with the FakeBat malware. Zscaler also documented one of these campaigns, but this one with a more generic PowerShell infostealer.
KageNoHitobito and DoNex: Fortinet researchers have published a report looking at KageNoHitobito and DoNex, two lesser-known ransomware strains used in the wild.
Sponsor Section
This podcast episode is brought to you by Socket Security. Socket makes a security platform for developers that protects their software from vulnerable and malicious open-source dependencies. Find them at Socket.dev.
The `xz` package backdoor is just the tip of the iceberg.
— Feross (@feross) March 30, 2024
There's a CONSTANT low-level stream of malware and spyware being uploaded to npm, PyPI, and Go registries.
I want to share a few examples from the 20,000+ malicious packages we detected so far: pic.twitter.com/f0FqCeUPqC
APTs, cyber-espionage, and info-ops
DEV#POPPER: North Korean hackers are behind a social engineering campaign targeting software developers with via fake job interviews. Developers invited to interviews are asked to take tests and perform tasks that get them infected with malware. Securonix says the final payload is a Python-based remote access trojan that can be used to collect data from their systems.
APT-C-28 (ScarCruft): Qihoo 360 has analyzed an APT-C-28 cyber-espionage campaign delivering the RokRat malware. There are so many of these reports out. DPRK hackers going wild lately!
LightSpy's macOS malware: Huntress Labs looks at F_Warehouse, the new malware framework used by the LightSpy APT to target macOS systems. The malware was initially spotted by BlackBerry here.
Cyber in Ukraine: Former SSSCIP cyber official Victor Zhora has given an interview on all the cyber that happened in Ukraine since 2014. The interview is in Ukrainian, but English subtitles can be added automatically via YouTube.
Vulnerabilities, security research, and bug bounty
QNAP security updates: Taiwanese NAS vendor QNAP has released six security advisories for its products.
Google dependency confusion: Security researcher Michael Hyndman has gained access to Google's internal network through a dependency confusion attack.
1-click Azure takeover: FalconForce's Arnau Ortega has published details on a now-patched Azure bug that allowed threat actors to hijack Azure accounts just by having victims click on a link.
Postman leaks: Truffle Security has published research on how the Postman API testing platform is leaking thousands of secrets and API tokens from legitimate companies. Truffle has identified at least 4,000 secret tokens, "but thousands more likely exist."
Ant Media Server EoP: Praetorian researchers have published a technical write-up on an elevation of privilege vulnerability in the Ant Media Server. The bug is tracked as CVE-2024-32656.
WP plugin abused in the wild: A threat actor is exploiting a vulnerability in a popular WordPress plugin to create admin accounts and install malware. The attacks target WordPress Automatic, a commercial plugin that lets users import content into WordPress sites. They are exploiting an SQL injection vulnerability that was patched in March.
PS RCE: Years after their official launch, a security researcher has found a vulnerability in the PlayStation 4 and 5 gaming consoles that can allow for remote code execution attacks. The vulnerability's root cause is in the sppp Point-to-Point network driver, which apparently was still unpatched for CVE-2006-4304. The vulnerability can be exploited via malicious PPPoE servers. Sony awarded the researcher $12,500 for their finding.
Linux vulnerabilities: CyberArk researchers have found five vulnerabilities in the Linux OS' NVMe-oF/TCP subsystem. All are patched! Long live fuzzing!
Pathfinder CPU attack: Academics have discovered a new side-channel attack in the speculative execution feature of modern Intel processors. The new attack is named Pathfinder and targets the conditional branch predictor (CBP) mechanism of Intel CPUs. Academics say Pathfinder is a more refined and efficient version of past attacks that targeted the same mechanism, such as Spectre or BranchSchope.
Infosec industry
Acquisition news: Private equity firm Thoma Bravo has acquired UK threat intel company DarkTrace for a whopping $5.32 billion.
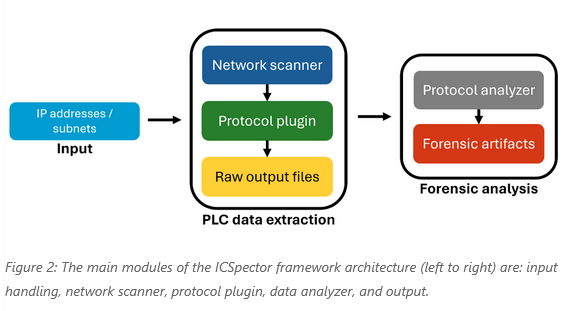
New tool—ICSpector: Microsoft has open-sourced a tool named ICSpector, an open-source framework for analyzing the information and configurations of industrial programmable logic controllers (PLCs).
Risky Business Podcasts
In this special edition of the Risky Business podcast, Patrick Gray chats with former Facebook CSO Alex Stamos and founding CISA director Chris Krebs about sovereignty and technology.




