Risky Biz News: PuTTY crypto bug exposes private keys, may lead to supply chain attacks
In other news: Cisco Duo discloses data breach; China tells telcos to ditch US chips; month-long brute-force campaign targets VPN devices.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

A team of German academics has discovered a crypto vulnerability in PuTTY, an extremely popular SSH and Telnet client for Windows users.
The vulnerability allows attackers who run malicious SSH servers to observe cryptographic signatures and recover a user's private key. This allows attackers to connect to systems where the private keys are being used for authentication.
But the vulnerability main impact is on source code repositories if they've been managed via a client that embeds PuTTY.
Attackers can look at a project's past signed public commits and then determine a developer's private key.
As the US NVD points out in its description of the vulnerability, this opens the door to supply chain attacks where threat actors can submit "signed" malicious code to legitimate projects.
The good news is that only ECDSA private keys that use the NIST P521 curve are affected. The bad news is that all PuTTY versions from 0.67 to 0.8 are affected. That's a lot of PuTTY versions, and more specifically, all PuTTY releases since March 2016.
The issue is tracked as CVE-2024-31497 and was fixed in PuTTY 0.81, released this week.
Besides PuTTY itself, the bug also impacts FileZilla, WinSCP, TortoiseGit, and TortoiseSVN—all of which embed PuTTY in their code.
PuTTY creator Simon Tatham says the root cause of the issue resides in how the software generated and used the random nonces—a random value that is used for signing operations. Tatham says he developed this system for PuTTY long before Windows had support for a cryptographic random number generator (RNG), using a custom method.
Instead, PuTTY-generated nonces used the message to be signed and the private key itself. This technique isn't bad, but it was later refined into its own standard (RFC-6979) more than a decade later in 2013. While PuTTY was an early adopter of this in 2001, it never switched to the more secure RFC implementation. Tatham says it has done now, after the two German researchers found this issue.
Breaches, hacks, and security incidents
Cisco Duo data breach: Cisco Duo says hackers breached one of its telephony suppliers at the start of April. The hackers stole MFA SMS message logs for some of its customers. Duo says the attacker didn't steal anything else. The telephony provider blamed the incident on one of its employees getting phished.
Israel radar system hack: A pro-Palestinian hacktivist group named Handala Hack claims to have breached Israel's national radar system. The incident took place before Iran's recent missile attack on Israel, and the group's claims have not been confirmed. [Additional coverage in the Jerusalem Post]
Albatross hack: Pro-Ukrainian hacktivist group Cyber Resistance has hacked and leaked data from Russian UAV maker Albatross. The group claims the hacked files confirm the company is manufacturing Iran-designed Shahed drones. The US sanctioned Albatross for its role in attacking Ukrainian civilian and critical infrastructure at the end of last year. [Additional coverage in InfoNapalm]
MGM sues FTC over hack: MGM Resorts has sued the FTC to stop the agency's investigation into a recent security breach. MGM claims the FTC is requiring too much data about the hack, and it's depriving the company of its due process rights—whatever that means. The company has also asked FTC chair Lisa Khan to recuse herself from the investigation because she was staying at the hotel when the hack happened. MGM also claims the FTC used regulations designed for financial institutions for its investigation. [Additional coverage in Bloomberg]
Zest Protocol crypto-heist: A threat actor exploited a vulnerability in the smart contract of the Zest Protocol cryptocurrency token. The attacker used the bug to orchestrate a flash loan attack and steal almost $900,000 worth of the project's tokens. Zest admins confirmed the attack and promised to reimburse users for lost assets.
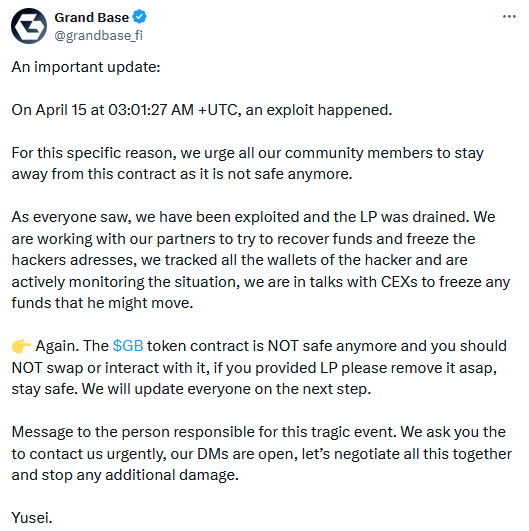
Grand Base crypto-heist: A threat actor has stolen almost $2 million worth of crypto assets from the Grand Base DeFi platform. The company says the hacker exploited a vulnerability in its platform and urged users not to interact with a specific smart contract. The exploit allowed the attacker to mint new tokens and immediately transfer them out. The price of the Grand Base token dropped 99% immediately after the hack. [Additional coverage in CoinGape]
General tech and privacy
FTC fines Cerebral: The US FTC has fined telehealth company Cerebral $7 million as part of its latest crackdown on companies that abuse healthcare data. The FTC says Cerebral shared the data of almost 3.2 million users with third parties like LinkedIn, Snapchat, and TikTok through analytics services embedded on its websites and apps. The fine also covers the company's shady practice of failing to act on service cancellation requests. The FTC says that $5.1 million of the fine will be used to provide partial refunds for customers who couldn't cancel Cerebral's online mental health services.
Twitter Blue disinfo: A report that looked at the recent disinformation and viral content surrounding Iran's missile attack on Israel found that 77% of the accounts posting fakes about the event were Twitter Verified paid accounts. I'm so glad Twitter is managing to make a profit from disinformation farms. At least that site is useful to someone these days.
Firefox 125: Mozilla has released Firefox 125. New features and security fixes are included. The biggest change is support for the new AV1 video codec.
Exchange Online rate limit: Microsoft will limit the number of recipients Exchange Online customers can send emails to. Starting with January 2025, Microsoft Exchange Online admins will only be able to send emails to 2,000 different recipients over a period of 24 hours. The new rate limit is part of Microsoft's attempt to limit the use of its email infrastructure for spam operations.
AI guidance: Cybersecurity and intelligence agencies from the Five Eyes countries have published joint guidance on the safe deployment of AI systems.
Government, politics, and policy
China tells telecoms to ditch US chips: The Chinese government has ordered local telcos to ditch equipment that uses foreign-made chips. Telcos are required to replace gear with domestic alternatives by 2027, the Wall Street Journal reports. The move specifically targets American chips like Intel and AMD. China introduced new procurement guidelines last December that blocks the use of foreign technology on government networks.
Russia wants to expand SORM to CDNs: The Russian government wants to expand its SORM internet surveillance system to content delivery networks (CDNs). Previously, only Russian telecom operators were required by law to connect SORM devices to their networks. The equipment allowed Russian authorities to intercept and spy on internet and mobile traffic. [Additional coverage in Vedomosti]
UK IoT law: The UK's new security law for smart devices will enter into effect later this month, on April 29. Per the new law, vendors must ensure that all smart devices meet basic cybersecurity requirements. They must provide a point of contact for the reporting of security issues and must specify for how long devices will receive security updates. Manufacturers must also not ship devices that use default passwords that can be easily found online. [PDF]
UK deepfake law: The UK government will make the creation of sexually explicit deepfake imagery a crime. Individuals who create such images can face a criminal record and unlimited fines. If the images are widely shared, the offender can also face prison terms. The new law is making its way through the UK Parliament.
Pegasus in Poland: Poland's General Prosecutor says the country's former ruling government has hacked 578 individuals with the Pegasus spyware. The hacks were carried out by three Polish services between 2017 and 2022. The findings are part of an investigation into abuses performed by the former government, controlled by the Law and Justice party. Previous reports have accused former Polish officials of using the spyware against opposition members, prosecutors, and journalists. [Additional coverage in Wiadomosci]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Daniel Schell and David Cottingham, the CTO and CEO of Airlock Digital. They discuss the security standard that drove innovation and the genesis of Airlock Digital and also how to make sure that standards don't become box-checking exercises.

Cybercrime and threat intel
Nebraska cryptominer detained: US authorities have arrested a Nebraska man for allegedly running a large-scale illegal cryptomining operation. Officials say Charles O. Parks III used fake companies to rent servers from two cloud providers but never paid his bills. Parks allegedly used $3.5 million worth of computing resources to mine $1 million in crypto. He used the money to buy NFTs, luxury cars, jewelry, and expensive hotels and travel.
FSB agent sentenced: A Russian court has sentenced an FSB officer to nine years in a maximum security penal colony. Russian authorities say Grigory Tsaregorodtsev took a bribe of $1.7 million from the Infraud cybercrime group. The bribe was to arrange the group's release from prison and dismissal of their criminal case. The court also fined Tsaregorodtsev with double the bribe he took. The Russian state will also confiscate some of his property, such as gold bars, real estate, and expensive cars. [Additional coverage in Kommersant]
Another Rescator hack: The individual who hacked Target (2013) and Home Depot (2014) also hacked the South Carolina Department of Revenue (2012) and stole the tax records of 3.6 million Americans. Infosec reporter Brian Krebs has linked the South Carolina incident to a hacker known as Rescator. Krebs previously identified Rescator after an investigation that lasted 10 years as Mikhail Borisovich Shefel, a 36-year-old man from Moscow.
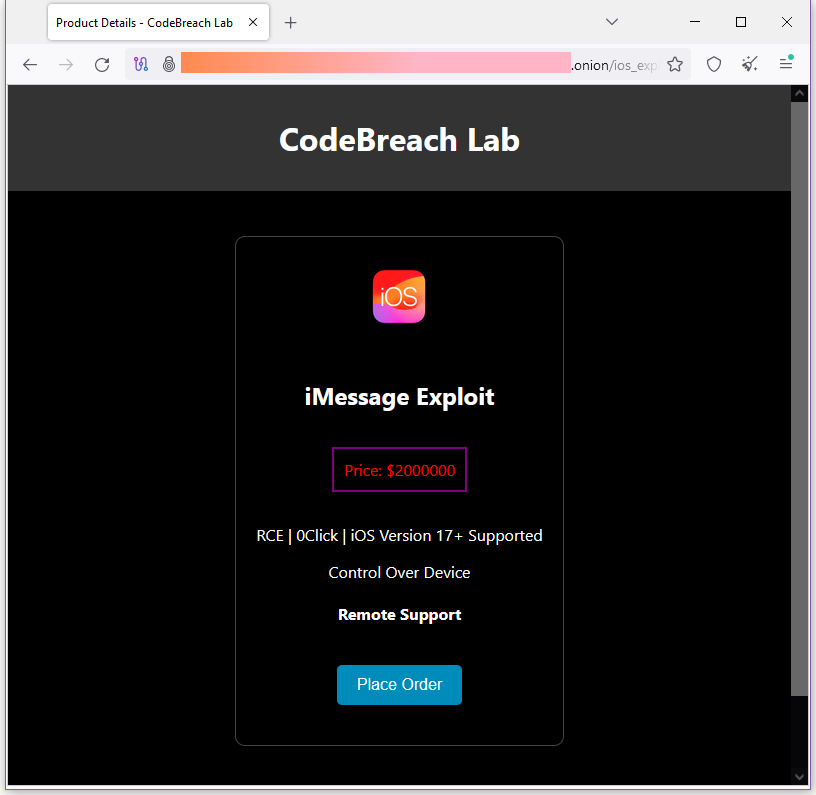
iOS zero-day: A threat actor is advertising (possibly scamming) a zero-click iOS zero-day on the dark web.
TA558: Positive Technologies looks at a malware distribution campaign orchestrated by the TA558 group, which the company tracks as SteganoAmor. The group has been active since 2018 and initially targeted hospitality and tourism organizations in Latin America. Recent attacks switched to North America and Western Europe, and used a lot more malware strains than before.
OpenJS supply-chain attacks: The OpenJS Foundation has reported three XZ-like social engineering attacks that tried to take over JavaScript projects. One incident targeted one of the Foundation's projects, while two others targeted "popular JavaScript projects." The Foundation says the social engineering attempts failed, and they've reported the incidents to CISA and the DHS.
Large-scale VPN brute-forcing campaign: Cisco says it's tracking a large-scale brute-forcing campaign that is targeting VPN devices from multiple vendors. The campaign started on March 18 and has targeted VPN web panels and SSH endpoints. Cisco says most attacks originate from Tor exit nodes and other anonymizing tunnels and proxies. The attacks have targeted VPN devices from Cisco, Fortinet, Check Point, SonicWall, Mikrotik, Draytek, Ubiquiti, and RD Web Services.
npm flood: An individual named One Dionys has flooded the npm portal with 15,000 projects as part of a scheme to generate Tea cryptocurrency tokens. These tokens provide rewards to developers based on the popularity of their projects.
Threat/trend reports: ANY.RUN, CERT-PL, Check Point, Cloudflare, CyberEdge, Imperva, and the NCSC-NZ have recently published reports covering infosec industry threats and trends.
Malware technical reports
XZ backdoor: The good reports on the XZ backdoor incident keep pouring in. The latest is from South Korean security firm S2W Talon.
Lockbit builder: Several security firms have published reports on the Lockbit ransomware itself, but Kaspersky has looked at the Lockbit 3.0 ransomware builder, which got leaked following an internal dispute back in 2022.
Evil Ant ransomware: Netskope has published a deep dive into the Evil Ant ransomware strain.
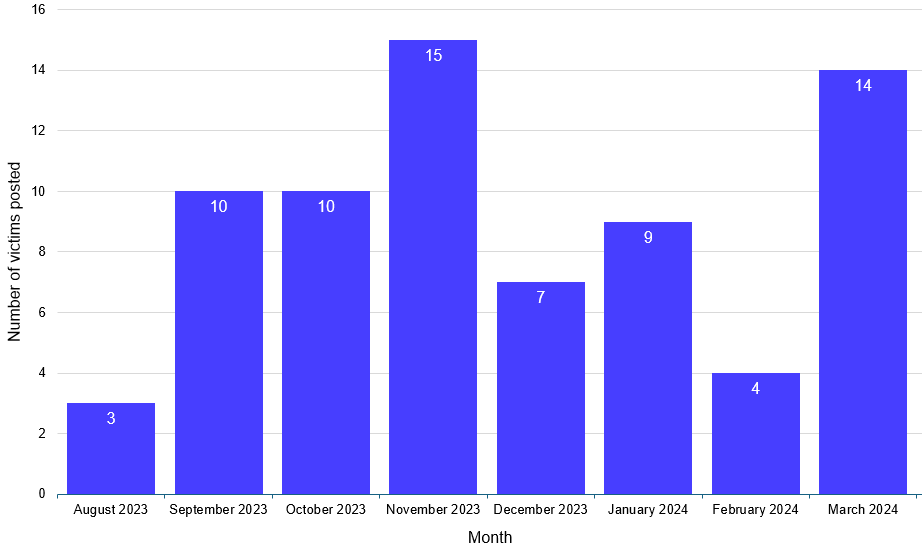
INC Ransom: Secureworks has published a report looking at the INC Ransom group. The group, which Secureworks tracks as GOLD IONIC, launched in August of last year and has made 72 victims.
Sponsor Section
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs, cyber-espionage, and info-ops
Volt Typhoon: The Chinese government has accused US officials of manufacturing the Volt Typhoon hacking group as part of an effort to defame China. Beijing officials claim US politicians, the US intelligence community, and cybersecurity companies have colluded to create the group as a way to boost their funding and steal taxpayers' money. In a 15-page report [PDF], the Chinese National Computer Virus Emergency Response Center claims Volt Typhoon is actually a cybercrime group named Dark Power. [Additional coverage and brain worms in the GlobalTimes]
Philippines faketivism: Resecurity has published profiles on the tens of hacktivist groups and threat actors that are currently hacking and leaking data from the Philippines government agencies and private companies. The company says that some of these groups are fake personas operated by Chinese state-sponsored entities. Resecurity says that cyberattacks and misinformation campaigns against the Philippines have tripled over the past year and since China has claimed sovereignty over the Philippines' Second Thomas Shoal territory.
APT31: HarfangLab has published an analysis of the US DOJ's indictment of APT31 members.
APT29's WINELOADER: Cisco's Splunk division has published a technical analysis of the WINELOADER malware, used by Russian cyber-espionage group APT29 in recent attacks against German political parties.
TA427 (Kimsuky): Proofpoint has published a profile on TA427, one of the three subgroups of the larger Kimsuky North Korean hacking group. More from Greg Lesnewich below.
"TA427 — one of three APT threat actors we track under the group broadly known as Kimsuky — is continuously soliciting foreign policy experts for their opinions as lures for engagement. You’d think it would be boring or unimpressive to see benign conversation campaigns going on for weeks to months between a threat actor and their targets, but it gives unique insight into what the DPRK is concerned about. The threat actor has established itself as a social engineering expert, ignoring the typos from time-to-time of course, and has also gotten creative in abusing DMARC to enhance the legitimacy of its campaigns, which isn’t something we commonly see being leveraged by APT actors in phishing activity. They often target users at small or under-resourced entities, as well as those users' personal addresses, so we are hoping awareness of this prolific activity can help targets identify that TA427 is targeting them."
Vulnerabilities, security research, and bug bounty
AWS Amplify bug: DataDog's Nick Frichette has found two variants of a vulnerability in AWS Amplify that exposed identity and access management (IAM) roles associated with Amplify projects.
"If the authentication component was removed from an Amplify project using the Amplify CLI or Amplify Studio built between August 2019 and January 2024, the IAM roles associated with the project were publicly assumable."
Unfixed Chirp smart locks: Chirp Systems has failed to patch a vulnerability in its smart lock system for almost three years. The devices contain hardcoded credentials that can be used to remotely open any of the company's locks. Despite the severity of the issue, the company has not responded even when contacted by CISA. According to infosec reporter Brian Krebs, the locks are installed in more than 50,000 homes across the US.
TP-Link exploitation: Fortinet says that several IoT malware strains (AGoent, Moobot, Mirai, Miori, Condi, and BASHLITE) have been seen exploiting CVE-2023-1389, a command injection vulnerability in TP-Link Archer routers.
PAN GlobalProtect zero-day: WatchTowr Labs has published a deep-dive into the recent zero-day (CVE-2024-3400) in Palo Alto Networks GlobalProtect firewalls. The company has not released a PoC, but it appears the bug is trivial to exploit, so it's not even needed. We covered it in our last edition here.
PHP security update: The PHP project has released a security update to fix the BatBadBut vulnerability, tracked as CVE-2024-1874. [h/t Simon Tsui]
Ivanti Avalanche vulnerabilities: Ivanti has released patches for 27 vulnerabilities in its Avalanche MDM product.
LeakyCLI returns: Orca security researchers say that the CLI components of AWS and Google Cloud are vulnerable to the same issue that they found in Azure last year—a vulnerability tracked as CVE-2023-36052, also known as LeakyCLI. The vulnerability can be used to leak sensitive secrets from environment variables.
Infosec industry
New tool—Elastic Universal Profiling: Elastic's security team has open-sourced the company's Elastic Universal Profiling agent. The code is on GitHub.
New tool—CVENotifier: Security researcher Shantanu Ghumade has published CVENotifier, a tool that parses CVE RSS feeds and sends Slack notifications based on certain vulnerability keywords.
0xCON videos: Talks from the 0xCON 2023 security conference, which took place last November, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Google's review of zero-days in 2023. They discuss what this kind of information tells us and how Google's perspective influences the report.




