Risky Biz News: Law enforcement thoroughly dismantle LockBit
In other news: Data from a Chinese contractor leaks online; China's MSS reveals hacking incidents in rare disclosure; and ConnectWise warns of major bug.

This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Law enforcement agencies from 11 countries have disrupted the LockBit ransomware operation in the most thorough and coordinated takedown of a cybercrime portal that has been seen to date.
As part of what they codenamed Operation Cronos, officials seized LockBit server infrastructure, froze cryptocurrency wallets holding past ransoms, released decryption tools, arrested members, filed additional charges, and imposed international sanctions.
The operation began months ago and was led by the UK's National Crime Agency (NCA). The agency claims it infiltrated the gang's servers, mapped out infrastructure, collected encryption keys, and accessed the LockBit backend, where admins and affiliates collected stats about attacks and negotiated with victims.
While official press releases from the UK NCA, Europol, and the US Department of Justice went out on Tuesday, February 20, the takedown began a day earlier when a seizure banner replaced the frontpage of LockBit's dark web portal where the gang typically listed its victims.
The banner teased the next day's press releases in what was just the first part of an elaborate law enforcement troll.

All of this was replaced on the next day with the second part of their troll—a clone of the original LockBit leak site but with various links related to Operation Cronos' achievements.
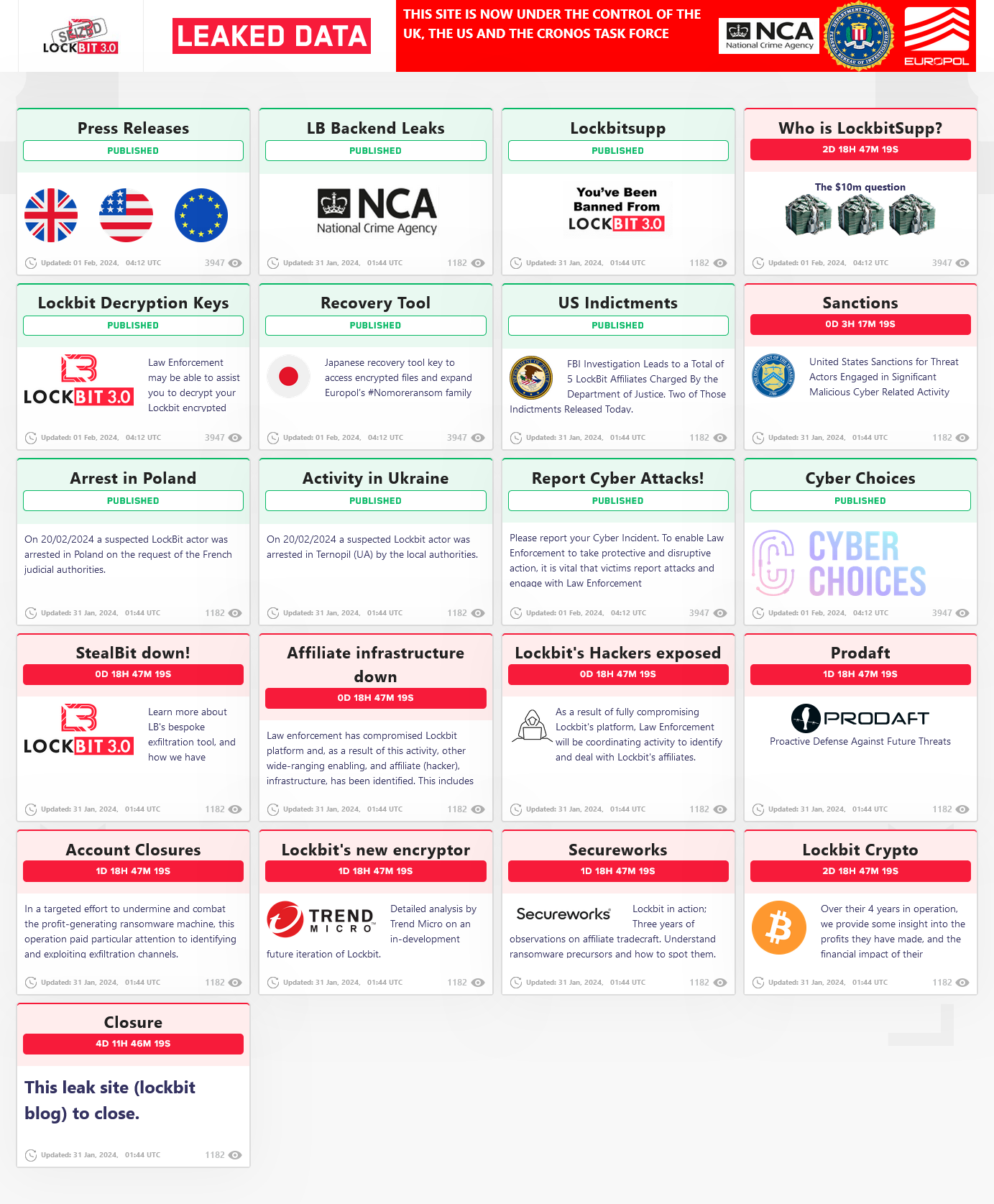
In total, officials say they have:
- Seized 34 LockBit servers;
- Identified and closed more than 14,000 online and web hosting accounts used in past LockBit attacks.
- Seized more than 200 cryptocurrency accounts holding past ransoms;
- Detained two affiliates in Poland and Ukraine;
- and indicted two other Russian nationals.
The two affiliates detained in Poland and Ukraine were not named, but the US identified the two Russian nationals as Artur Sungatov and Ivan Kondratyev. They charged and sanctioned.
They are the fourth and fifth LockBit affiliates charged in the US after similar indictments against Mikhail Vasiliev, Mikhail Pavlovich Matveev (aka Wazawaka), and Ruslan Magomedovich Astamirov.
Officials say Kondratyev operated inside LockBit under the monicker of Bassterlord. Kondratyev was one of LockBit's oldest and most prolific affiliates before retiring and going on the equivalent of a press tour.
There was no news on LockbitSupp, broadly believed to be the LockBit's top administrator. One of the posts on the NCA's "redesigned" LockBit front page suggests the US might offer a massive reward for information on LockbitSupp's identity. The US State Department has offered these types of rewards in the past for other ransomware gangs such as AlphV, REvil, DarkMatter, and Hive.
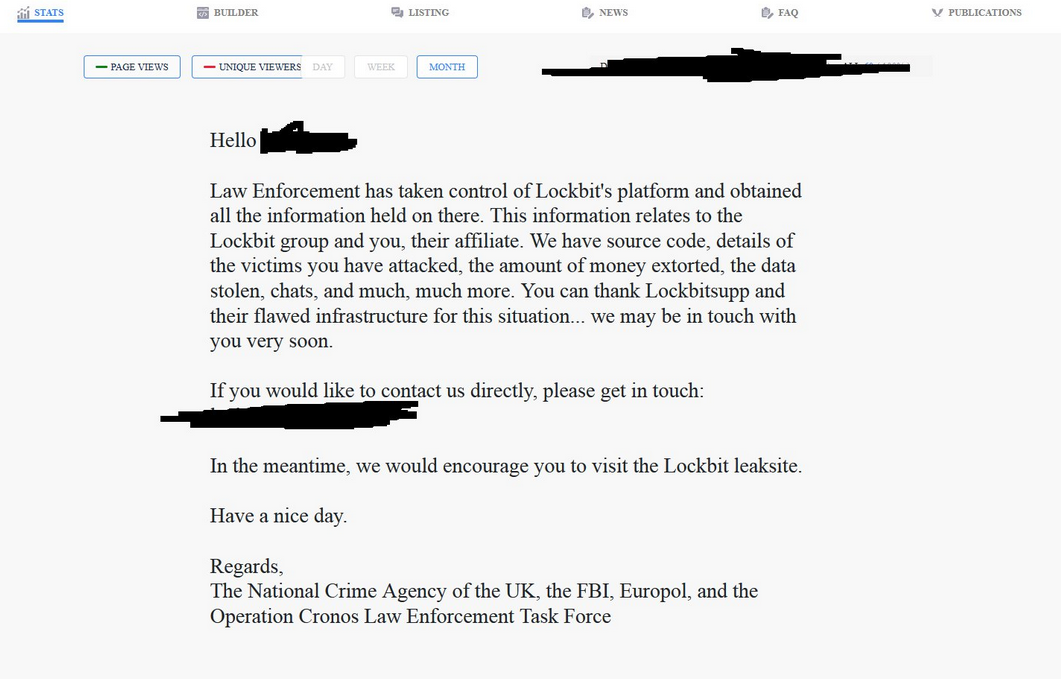
As spotted by vx-underground, affiliates who logged into their LockBit backend accounts on Monday were also greeted by a special message from the NCA blaming the takedown on "LockbitSupp and their flawed infrastructure." The message urged affiliates to rat on their former boss, somewhat confirming that law enforcement has yet to identify LockBit's creator.
A day later, officials also posted screenshots from various parts of the LockBit backend just to showcase all the places they had access to.
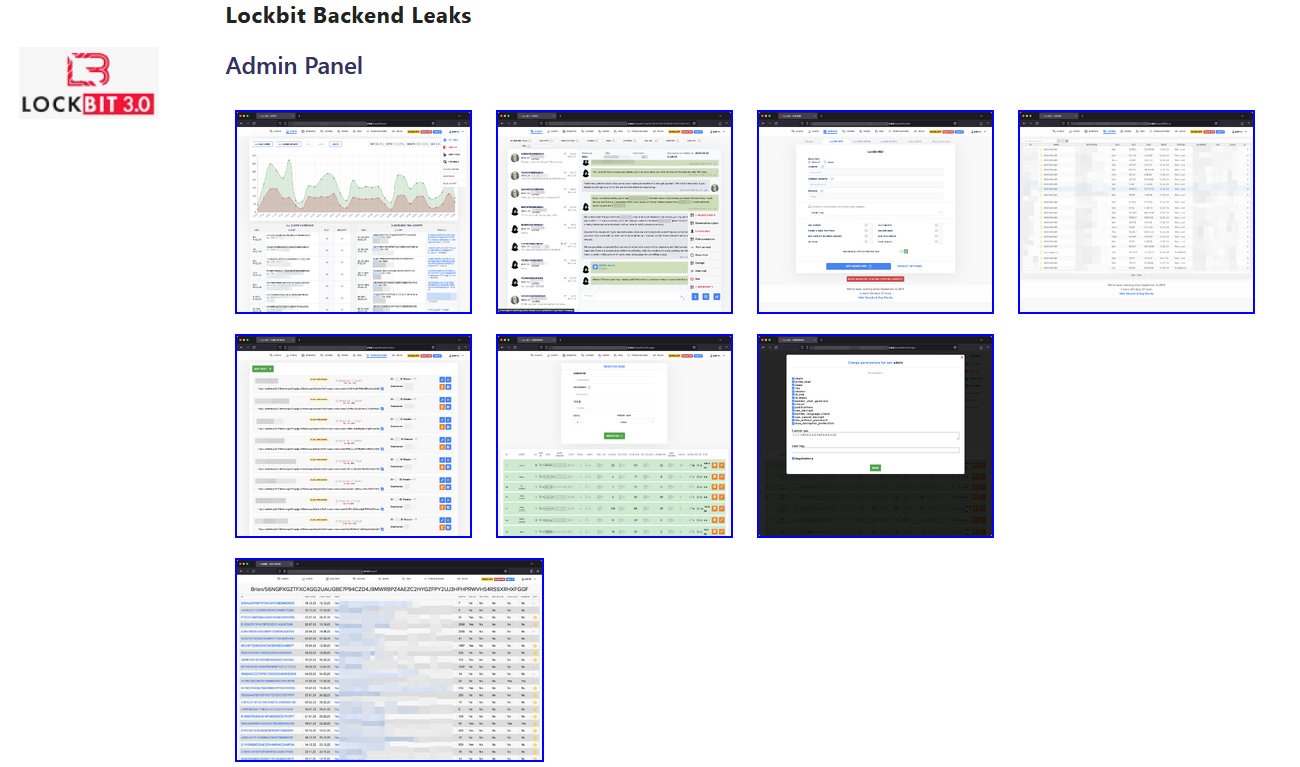
Just like they did in the recent cases of the Hive and AlphV disruptions, officials didn't just take down some servers. They also collected the most coveted and sensitive part of a Ransomware-as-a-Service (RaaS) backend—the encryption keys that were used to lock victim files.
Officials say the keys were handed over to a technical unit inside the Japanese national police, which created a decryption utility that can recover files from Windows systems. The utility is available through Europol's No More Ransom project.
In private chats and posts on hacking forums, LockbitSupp claimed law enforcement used an exploit for a PHP vulnerability tracked as CVE-2023-3824 to hack servers, but security researchers are skeptical about this claim, although exploitation is theoretically possible.
The impact of this takedown remains to be seen. Several ransomware operations that met a similar fate relaunched under new names. For example, the Hive gang never came back after the FBI hacked its servers and released decryption tools last January. On the opposite side of the spectrum, the operators of the AlphV RaaS sprung back online and started launching attacks from new infrastructure a month after the FBI took down servers and released decryption keys this past December.
LockBit's fate depends on what LockbitSupp decides next. They can either take it as a personal afront and come back with new servers, or they can just pack it in and attempt to enjoy what's left from their stolen ransoms.
And LockbitSupp has a lot of those.
Officials say that since its launch in 2019, the LockBit RaaS became one of the largest ransomware operations today, infecting more than 2,000 victims. The entire operation is believed to have collected more than $120 million in paid ransoms.
Secureworks, which was involved in Operation Cronos together with other security firms, published a blog post going over LockBit's entire history.
Breaches, hacks, and security incidents
FixedFloat crypto-heist: The FixedFloat cryptocurrency platform has halted operations after detecting massive outgoing transactions from some of its wallets. Blockchain experts believe the platform lost more than $26 million worth of Bitcoin and Ether. FixedFloat has not released any information about what happened. [Additional coverage in CoinTelegraph]
Zenlayer leak: Edge cloud service provider Zenlayer leaked more than 57GB of internal data via a publicly accessible database server. The data contained internal system and security logs, as well as customer data. The database has since been secured.
Cambridge DDoS: Cambridge University in the UK had to deal with a DDoS attack this week on some of its students' learning platforms. While you'd think some students were trying to avoid some exams, the attack was actually the work of pro-Kremlin group Anonymous Sudan. Because this makes perfect sense in 2024. [Additional coverage in Varsity]
General tech and privacy
Firefox 123: Mozilla has released Firefox 123. New features and security fixes are included. The biggest change is the addition of a Web Compatibility Reporting Tool that lets users report websites that don't work in Firefox but work fine in other browsers.
PlayStation Portal jailbreak: A group of Google engineers have jailbroken Sony's PlayStation Portal device to allow it to run local games. The device was previously limited to only streaming games running on a local PS5 console. [Additional coverage in Video Games Chronicle]
OG Xbox exploit: A universal dashboard exploit has been released for Microsoft's original Xbox console, the 2001 version.
Tinder expands verification: Dating app Tinder is launching a user verification service for its users. The feature is named ID Verification and will allow users to verify their Tinder dating account by providing a real-life identification document, such as an ID, driver's license, or passport. Tinder initially tested the program last year in Australia and New Zealand. It is now expanding it to the US, UK, Brazil, and Mexico.
Government, politics, and policy
EU to investigate TikTok: The European Union has launched an investigation into TikTok over the company's child protection features and the use of harmful and addictive app design practices. The inquiry will take place under the EU's new Digital Services Act (DSA). TikTok becomes the second company after Twitter to come under investigation for potential breaches of DSA requirements. The inquiry will also look at TikTok's ad transparency rules and how the company provides access to research data. The EU adopted the DSA rules last year to regulate large online platforms.
Joyce retirement: The US National Security Agency has announced that Roby Joyce will retire from the agency and his position as Director of Cybersecurity. Joyce will formally retire at the end of March. He retires after spending 34 years with the NSA, where he also led the agency's Tailored Access Operations team.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Rob King, runZero's Director of security research. The pair talk about the world of Operational Technology protocols and how Rob dissects these protocols to be sure that active discovery of OT devices is safe.

Cybercrime and threat intel
BEC money laundering group detained: US law enforcement has detained 10 suspects across the state of Maryland as part of a cybercrime investigation. The suspects allegedly laundered more than $9.5 million from at least 15 BEC incidents across the US. According to court documents, group members ran extensive networks of shell companies disguised as transportation and real estate businesses. They used the companies to break up stolen funds and send the money overseas.
Hacker arrested in Ukraine: Ukraine's Cyber Police has arrested a 31-year-old suspect on charges of running a malware operation. The suspect allegedly worked with multiple co-conspirators to create websites that offered free Windows and Android apps infected with malware. He used online ads to drive traffic to the sites and allegedly made at least $100,000 by selling victims' data on the dark web.
Formcrafts abuse: Threat intel analyst BankSecurity looks at how threat actors have been abusing Formcrafts' legitimate services to create phishing pages for online banks.
Google Cloud abuse in LATAM: Cisco Talos looks at how malware groups like Astaroth (Guildma), Mekotio, and Ousaban are abusing Google Cloud for their operations across LATAM.
PBX configuration guide: The UK NCSC has published a guide with the basics of securing PBX telephony systems.
Tycoon PhaaS: Trustwave has published a report looking at Tycoon, a Phishing-as-a-Service operation marketed on Telegram for as low as $120.
Malware technical reports
BackMyData ransomware: Malware analyst Vlad Pasca has reverse-engineered BackMyData, the ransomware strain used to attack Romanian hospitals earlier this month.
Akira ransomware: Morphisec has published a technical analysis of the Akira ransomware.
Anatsa: Mobile security firm ThreatFabric has discovered new versions of the Anatsa banking trojan that were specifically designed to infect Samsung devices. Researchers say the malware includes routines designed to interact with specific elements in the Samsung user interface. ThreatFabric says recent Anatsa versions can also bypass the stricter security features added in Android 13 devices. Anatsa joins a growing list of malware strains that can run on Android 13. ThreatFabric says that Anatsa-infected apps also regularly make it on the official Android app store, and that apps from the gang's latest campaign were downloaded more than 100,000 times from the Play Store alone.
SpyNote: Similarly to Anatsa, the Spynote Android RAT is apparently also capable of bypassing Android 13's Restricted Settings. According to malware researcher Cryptax, it does this by using an initial session-based installer that deploys a second malicious installer.
Migo: Cado Security has discovered Migo, a new cryptocurrency malware operation that is currently targeting Redis servers.
GateDoor: South Korean security firm S2W has discovered GateDoor, a Windows version of RustDoor, a backdoor strain targeting macOS systems. While the macOS version is written in Rust, the Windows one is coded in Go. S2W says both versions are distributed disguised as updates for popular Apple and Windows apps. S2W confirmed Bitdefender's assessment that RustDoor/GateDoor uses infrastructure previously linked to the AlphV (ShadowSyndicate) ransomware operation.
Sponsor Section
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs, cyber-espionage, and info-ops
STA-2201: Kazakhstan's cybersecurity agency STS says that a cyber-espionage group has breached the network of one of its telecom operators. The group used public exploits and living-off-the-land tools to gain access to the telecom's internal network and Microsoft Exchange servers. The agency tracks the group as STA-2201 and did not formally attribute it to a specific country. An STS technical report (PDF, page 43) mentioned the group deployed malware, such as PlugX and ShadowPad, which are typically associated with Chinese cyber operations. (via Oleg Shakirov)
MSS reveals foreign hacks: China's intelligence agency says foreign hackers have breached critical Chinese companies in a rare cybersecurity disclosure. The MSS says hackers breached a military-civilian integration enterprise after the company failed to update some of its software. The agency says the hack exposed information about China's military equipment and technology development. Hackers also stole data from a large state-owned enterprise after the company left a testing system unsupervised on its network. The MSS says it also detected efforts from "a foreign intelligence agency posing as a software developer" that attempted to bribe a Chinese network engineer to install malware on their employer's network. [Additional coverage in the South China Morning Post]
Earth Preta: Trend Micro has published a report covering a cyber-espionage campaign carried out by Chinese APT group Earth Preta. Trend Micro says its report covers attacks across Asia that are part of the same campaign documented by Check Point that hit Europe in 2023.
Chinese contractor leak: An unknown individual has leaked files from a Chinese company that allegedly develops malware and carries out cyber espionage operations on behalf of the Chinese government. The data allegedly belongs to i-SOON, a cybersecurity company based in the city of Chengdu. The leaked files include internal chats, business pitches, documentation describing the company's products, and what appears to be stolen victim data. No source code was included. One of the company's business pitches for Chinese government agencies specifically advertises the services of its "APT Team." Security researchers have yet to link the company to a particular APT. Previous reports have linked multiple Chinese cyber-espionage groups to the city of Chengdu. [More extended coverage of this leak in the Seriously Risky Business newsletter that goes out on Feb 22]
Turla: Lab52 researchers have published a report on Pelmeni Wrapper, a new malware strain used by the Turla APT group in recent campaigns. The malware has been spotted in the wild as a wrapper for Turla's more advanced Kazuar backdoor.
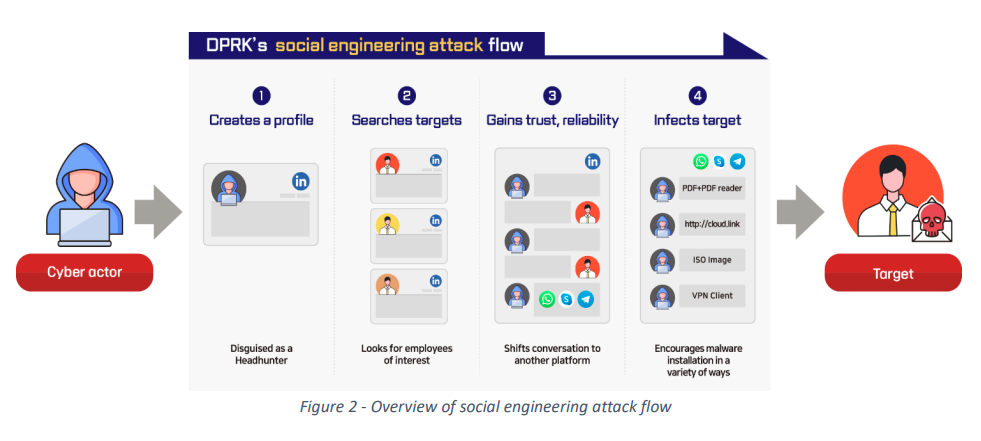
DE/KR warn of DPRK hacks: Germany and South Korea's intelligence agencies say North Korean hackers are targeting defense companies across the world. The attacks aim to steal advanced military technology to help North Korea develop new weapons. Officials say multiple North Korean APT groups are involved. Attacks range from spear-phishing to complex social engineering schemes and software supply chain attacks.
Vulnerabilities, security research, and bug bounty
ConnectWise security update: Software company ConnectWise has released a security update for its SmartConnect remote access utility. The patch fixes an authentication bypass that was assigned a severity rating of 10/10. Security firm Huntress says it was able to reproduce an exploit for the vulnerability within hours after the patch was released. Huntress urged companies to apply the security updates as soon as possible. Threat actors have exploited other SmartConnect vulnerabilities in the past to deploy ransomware. Huntress says that more than 8,800 SmartConnect instances are connected online and still running vulnerable versions.
Joomla XSS bugs: SonarSource has published a technical analysis of multiple XSS vulnerabilities they uncovered in the popular Joomla CMS. According to researchers, attackers who manage to trick administrators into clicking malicious links can gain remote code execution with admin rights on their sites.
Mirai on TP-Link: PermafrostSec looks at how a Mirai-based botnet is abusing a TP-Link pre-auth RCE patched last year (CVE-2023-1389).
COLD-Attack: US academics have published a paper on COLD-Attack, a jailbreak for some modern large-language models (LLMs).
"Our extensive experiments on various LLMs (Llama-2, Mistral, Vicuna, Guanaco, GPT-3.5) show COLD-Attack's broad applicability, strong controllability, high success rate, and attack transferability. Our code is available at this URL."
Browser cache poisoning: A security researcher has documented a new browser cache poisoning technique. Browser makers are slowly rolling out changes to mitigate attacks.
"The main browsers share their cache between Fetch requests and normal navigation. This means that any request that can be made with Fetch, which produces a cacheable response, can also be used to poison the browser navigation too. Given the right set of circumstances, this approach can unlock a raft of unexploitable vulnerabilities, and make them practical."
Infosec industry
New tool—Ransomania: Israeli cybersecurity firm Cyberint has opened its data on ransomware attacks for everyone via its new Ransomania portal. [via Yotam Gutman]
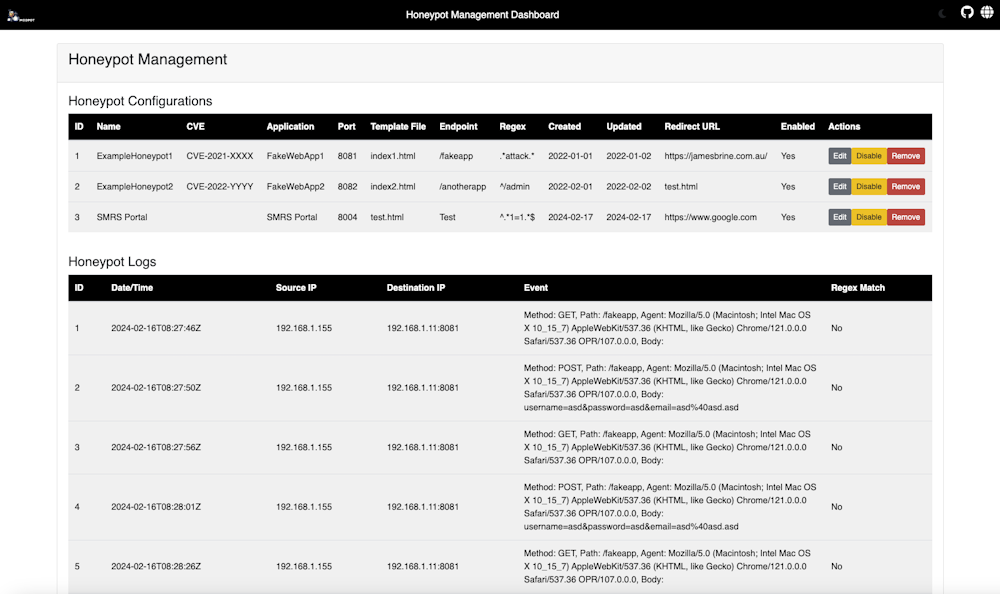
New tool—Modpot: Security researcher James Brine has open-sourced Modpot, a modular framework for deploying honeypots.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine Russian cyber doctrine and how it was applied in the early days of its invasion of Ukraine. They mention a Human Rights Watch report that examined how international humanitarian law was applied in the 2003 invasion of Iraq.





