Risky Biz News: Authorities take down LabHost, one of the world’s largest phishing platforms
In other news: Akira ransomware group made $42 million in a year; "highly profitable trader" found guilty at trial; Kubernetes clusters hacked via OpenMetadata bugs.

This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Law enforcement agencies from 19 countries have collaborated to take down a cybercrime service named LabHost that provided tools to easily set up and run phishing pages.
The service launched in late 2021 and was what you would call a PhaaS, or Phishing-as-a-Service platform.
For prices of $179/month and higher, it allowed threat actors to use templates and set up phishing sites imitating a legitimate service.
The platform provided phishing page templates, server hosting, and a tool named LabRat for organizing and tracking different phishing campaigns.
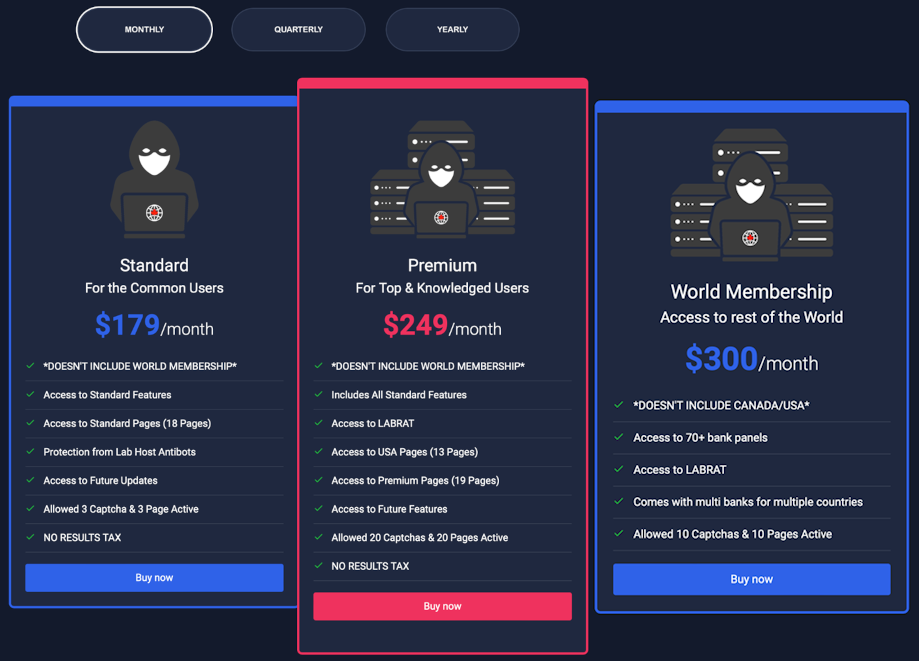
According to Trend Micro, it was one of the most sophisticated PhaaS platforms on the market today. Besides the standard features listed above, it could also allow threat actors to create custom phishing pages for any service they wanted to target, and also came with an SMS phishing (smishing) component named LabSend.
It was also one of the first phishing services to include solid support for bypassing MFA by supporting proxy-based AitM (Attacker-in-the-Middle) phishing techniques.
LabHost also had the ability to allow threat actors to interact with victims in real-time, which is a feature often used to request 2FA/MFA codes from victims and bypass account protections.
All of this made the platform incredibly successful. Europol says the platform had more than 10,000 registered users. The UK Met Police, which led the investigation into the platform, says 2,000 of these were still paying one of the monthly subscription fees when the platform was dismantled.
Authorities say LabHost had support for phishing more than 170 online services and was hosting more than 40,000 phishing domains.
Europol called it "the world's largest phishing-as-a-service platform," and the Met Police estimates the site made £1 million ($1,173,000) since its launch, which is quite the figure for a PhaaS.
The LabHost takedown took place over four days this week and resulted in 37 arrests. The Met Police says it also sent ominous messages to 800 LabHost users "telling them we know who they are and what they've been doing." The Australian Federal Police had a similar message for Australians registered on the site.
"Australians who have used LabHost to steal data should not expect to remain anonymous. Authorities have obtained a vast amount of evidence during this investigation and we are working to identify anyone who has used this platform to target innocent victims."
Authorities are now sifting through the phished credentials and are contacting and notifying victims. The US Department of Justice says the data of at least 500,000 credit cards has been phished through the service.
Officials also credited security firms such as Chainalysis, Intel 471, Microsoft, The Shadowserver Foundation, and Trend Micro for helping with the investigation.
Breaches, hacks, and security incidents
UNDP cyberattack: The United Nations Development Programme (UNDP) says that its Copenhagen branch fell victim to a ransomware attack. A ransomware group named 8Base previously claimed credit for the attack.
"On March 27, UNDP received a threat intelligence notification that a data-extortion actor had stolen data which included certain human resources and procurement information."
NY government cyberattack: A cyberattack on systems used by New York’s legislature to draft and print bills has hampered efforts to enact the state budget, according to New York Governor Kathy Hochul. [Additional coverage in The Record]
Cyber Court: Multiple pro-Palestinian hacking groups have launched a portal named Cyber Court, where they plan to aggregate and leak data from Israeli government agencies, companies, and various services. [Additional coverage in Haaretz]
Argentina hack: A threat actor has hacked and stolen Argentina's entire driver's license database. The hacker is selling the data for $3,000 on an underground cybercrime forum. The data contains the driver's license details of 5.7 million Argentinians, including the country's celebrities and politicians. [Additional coverage in Ambito]
World-Check extortion: A hacking group named GhostR claims it hacked the World-Check screening database. The group told TechCrunch they stole the data last month from a Singapore-based firm with access to the database. World-Check is used for security clearances in the public and private sectors. It contains the names of individuals believed to have ties to terrorist organizations, organized crime, or sanctioned entities. The London Stock Exchange Group is the current owner and maintainer of the World-Check database. GhostR is selling over 5.3 million World-Check records.
Void Interactive ransomware incident: A ransomware gang has breached and stolen the source code of gaming studio Void Interactive. The studio confirmed the hack and said that no user or staff data was taken in the intrusion. The D0nut Leaks ransomware group took credit for the attack, which they claim took place last month. Void Interactive is the studio behind the Ready or Not first-person shooter. [Additional coverage in Insider Gaming]
Le Slip Français breach: French underwear brand Le Slip Français has suffered a data breach after a hacker stole and leaked the data of 1.5 million customers.
Smoke Alarm Solutions leak: Australian software company Smoke Alarm Solutions has leaked 107GB of data from one of its servers, including past invoices. Based on the company's name, you can probably guess what it does and why it's bad. [Additional coverage in vpnMentor]
Recorded Future deepfake incident: After LastPass disclosed a deepfake phishing incident last week, we now have another one—this time, phishers tried to pose as Recorded Future's CEO, Christopher Ahlberg.
General tech and privacy
Gentoo bans AI code: Linux distribution Gentoo has banned project members from contributing AI-generated code.
"In other words, explicitly forbid people from using ChatGPT, Bard, GitHub Copilot, and so on, to create ebuilds, code, documentation, messages, bug reports and so on for use in Gentoo."
Chrome 124: Google has released version 124 of its Chrome browser. See here for security patches and webdev-related changes. The biggest change in this release includes support for the ML-KEM (Kyber) key encapsulation system, a post-quantum encryption safety feature. Chrome 124 also now lets users create desktop shortcuts for any website.
Tuta claims sabotage: Secure email provider Tuta (formerly Tutanota) claims that Google is intentionally burying the company in search results, even for direct search results, in violation of the new EU DMA rules.
Government, politics, and policy
US ransomware payment ban: Former acting national cyber director Kemba Walden has thrown a bucket of ice-cold water on a potential ban of ransomware payments in the US. A ban is highly unlikely at this point. [Additional coverage in CyberScoop]
FANSA passes House: The US House of Representatives has passed the Fourth Amendment is Not for Sale Act, a bill that bans US government and intelligence agencies from purchasing Americans' data from data brokers without a warrant. The White House criticized the bill, claiming it would slow down or block investigations while still leaving the data available to foreign states [PDF].
EU hypocrisy: The EU has been pushing for years for new legislation named Chat Control that would scan its citizens' secure private communications through the use of an encryption backdoor. According to a leaked copy of the upcoming law courtesy of Pirate Party MEP Patrick Breyer, EU officials want to carve out exceptions from the law for politicians and the staff of intelligence agencies, police, and military.
"The fact that the EU interior ministers want to exempt police officers, soldiers, intelligence officers and even themselves from chat control scanning proves that they know exactly just how unreliable and dangerous the snooping algorithms are that they want to unleash on us citizens. They seem to fear that even military secrets without any link to child sexual abuse could end up in the US at any time. The confidentiality of government communications is certainly important, but the same must apply to the protection of business and of course citizens communications, including the spaces that victims of abuse themselves need for secure exchanges and therapy."
Chinese arrests: The Chinese government has arrested more than 1,500 individuals for spreading disinformation online. The campaign targeted regular citizens but also influencers, bloggers, and live-streamers. Officials also banned 63,000 accounts and removed over 735,000 posts. [Additional coverage in SCMP]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Daniel Schell and David Cottingham, the CTO and CEO of Airlock Digital. They discuss the security standard that drove innovation and the genesis of Airlock Digital and also how to make sure that standards don't become box-checking exercises.

Cybercrime and threat intel
Mango Markets hacker convicted: A New York jury has convicted a Puerto Rico man who used software exploits to manipulate prices on cryptocurrency platform Mango Markets. The incident took place in late 2022 when cryptocurrency expert Avraham Eisenberg stole over $110 million worth of crypto assets from the platform. The cryptocurrency community identified Eisenberg shortly after the hack. Eisenberg did not deny his actions and tried to explain them as a "highly profitable trading strategy." This was the DOJ's first-ever cryptocurrency market manipulation case.
Moldovan hacker charged: US authorities have charged a Moldovan national for running a botnet that infected thousands of computers. Alexander Lefterov infected systems with malware, collected login credentials, and then stole money from his victims' online accounts. Officials say Lefterov also sold access to infected systems to other groups, including ransomware operators. Lefterov is still at large and has been added to the FBI's Cyber Most Wanted list.

"Junk gun" ransomware: Sophos has published a report on what it calls "junk gun" ransomware—a term it uses to refer to low-tier ransomware strains offered for sale on the criminal underground. The company points out that despite the attention to RaaS platforms, low-tier ransomware strains are still around and in large numbers. Coupled with reports about a loss of credibility in the bigger RaaS platforms, don't be surprised if the bigger players just adopt one of these smaller strains.
SIM swapping spam: Current and former employees of US mobile operators say they are receiving SMS messages from criminal groups. The messages offer $300 for those willing to perform a SIM swap. Employees at Verizon and T-Mobile have reported receiving messages on both their personal and work numbers. [Additional coverage in The Mobile Report]
FIN7 campaign: BlackBerry has seen the FIN7 cybercrime group run spear-phishing campaigns targeting the US automotive sector.
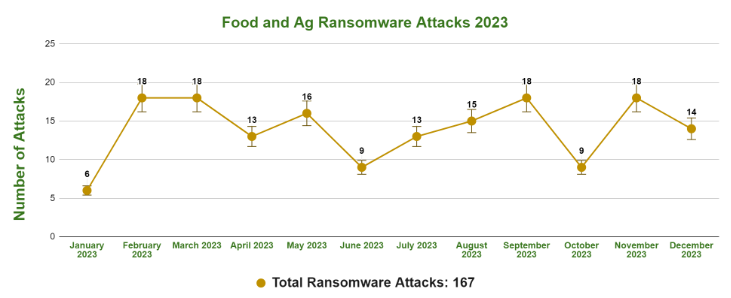
Threat/trend reports: Coveware, DataDog, Dr.Web, Dragos, Flashpoint & Onapsis, Food and Ag-ISAC [PDF], and Red Canary have recently published reports covering infosec industry threats and trends.
Malware technical reports
SoumniBot: Kaspersky looks at a new Android banking trojan named SoumniBot. For now, the banker only targets South Korean banks.
Cerber ransomware: Cado Security has published an analysis of Cerber, a ransomware strain that is being deployed on Confluence servers hacked using the CVE-2023-22518 vulnerability.
Akira ransomware: Cybersecurity agencies from the US and the Netherlands have published a joint malware analysis on the Akira ransomware. Officials say the group made at least $42 million from ransom payments since March 2023. The group is believed to be a Conti rebrand.
PupyRAT: AhnLab researchers look at PupyRAT, a cross-platform open-source remote access trojan that's been available on GitHub and has seen some adoption in the wild. Adopters include groups like APT35 and Decoy Dog.
Redline Stealer: McAfee looks at a new(er) version of the Redline Stealer they've spotted in the wild, leveraging Lua bytecode to perform malicious behavior.
DuneQuixote: Kaspersky has published a report on a malware campaign the company it calls DuneQuixote that targeted entities in the Middle East. The DuneQuixote dropper was distributed using tampered TotalCommander installers and was used to deploy a novel backdoor named CR4T.
"The 'DuneQuixote' campaign targets entities in the Middle East with an interesting array of tools designed for stealth and persistence. Through the deployment of memory-only implants and droppers masquerading as legitimate software, mimicking the Total Commander installer, the attackers demonstrate above average evasion capabilities and techniques. The discovery of both C/C++ and Golang versions of the CR4T implant highlights the adaptability and resourcefulness of the threat actors behind this campaign."
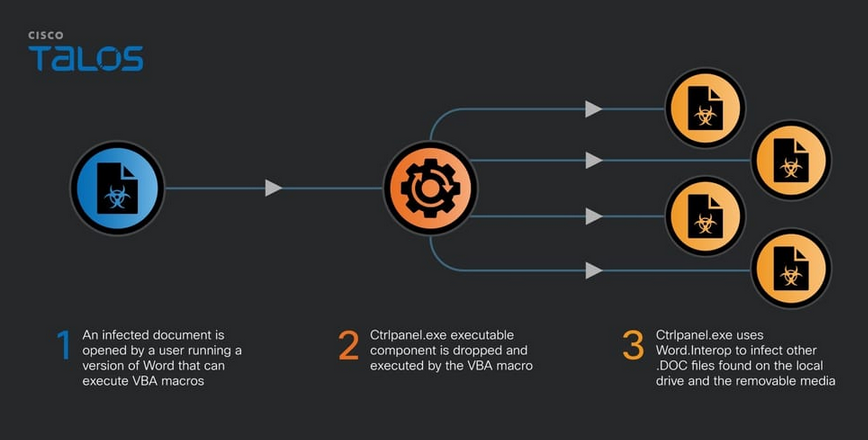
OfflRouter: Cisco Talos says it's tracking a computer virus named OfflRouter that has been spreading throughout the business environments of Ukrainian organizations. The malware has been live since 2015 and appears to be contained in Ukraine. It works by using malicious VBA code embedded in Word documents to spread to a victim's other Word files. Cisco researchers believe the malware is the work of an "inexperienced developer."
Sponsor Section
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs, cyber-espionage, and info-ops
Lazarus campaign: Avast has published additional details about a Lazarus APT campaign they first documented back in February. The campaign took place last year and targeted individuals in Asia with bogus job offers. It used a now-patched zero-day (CVE-2024-21338) and deployed a new RAT named Kaolin.
Core Werewolf: Russian security firm FACCT says that cyber-espionage group Core Werewolf tried to infect with malware staff at the 102nd Russian military base in Gyumri, Armenia. The group has been active since August 2021. Most of its operations have targeted Russia's military-industrial complex and critical information infrastructure facilities. In March this year, the group targeted a Russian research institute engaged in weapons development. This month, the group also targeted a Russian defense contractor.
Russian disinfo operations: Multiple Russia-affiliated influence groups are targeting the US electorate with anti-Ukraine and anti-NATO disinformation ahead of the upcoming election. The most prolific Russian groups are backed by or affiliated with the Russian Presidential Administration. Microsoft says this is a major change in Russian info-ops, which have shifted away from the Internet Research Agency and their intelligence services. The campaigns rely on using social media networks to boost and legitimize fake news stories. Many of these articles are amplified by Russian expats and politicians. Microsoft noted similar influence campaigns from China but not from Iran.
APT28's XAgent: BlackBerry's Dmitry Bestuzhev has published a technical breakdown of a new XAgent sample. XAgent is a piece of iOS spyware used by the ATP28 group. The recent sample appears to have been used in attacks targeting iOS devices in Western Europe.
UAC-0184: Ukraine's CERT team says that a Russian cyber-espionage group tracked as UAC-0184 has increased its activity since the start of the year. Recent operations have involved malware disguised as dating and messaging apps. Final payloads include an assortment of commercial malware strains, such as XWorm, RemcosRAT, or IDAT Loader.
Sandworm's Kapeka: WithSecure researchers have discovered a new backdoor named Kapeka used by the Sandworm Russian APT group in attacks against Eastern European organizations since at least mid-2022.
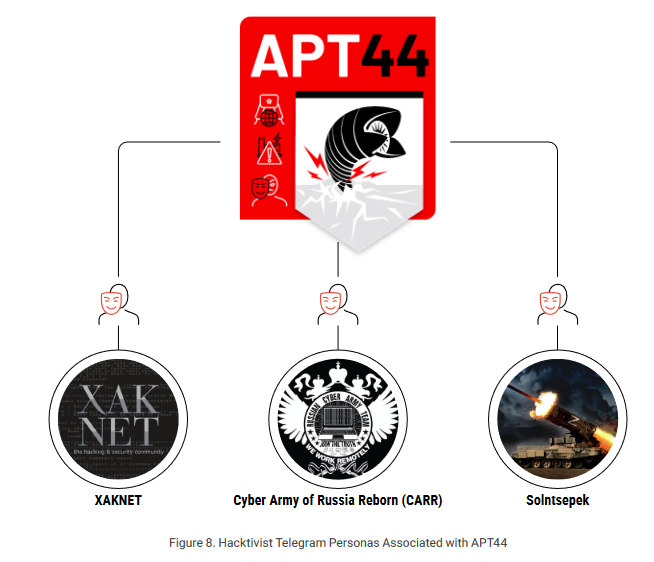
Sandworm is now APT44: Google and Mandiant have published a report this week on APT44, the new name the two companies have given to the Sandworm APT, aka Unit 74455 of the Main Centre for Special Technologies (GTsST) within the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GU), more commonly known as the Main Intelligence Directorate (GRU). The report looks at the group's past operations, and its current activities and role in the Ukranian war. The report also links (again) APT44 to pro-Kremlin fake-hacktivist groups XakNet, CyberArmyofRussia_Reborn, and Solntsepek. As these groups, Google says APT44 carried out attacks on a water utility in the US and a wastewater management utility in Poland.
Vulnerabilities, security research, and bug bounty
Element Android vulns: Researchers at Shielder have found two vulnerabilities in Element Android, the official Matrix client for Android.
"As an impact, a malicious application would be able to significatively break the security of the application, with possible impacts ranging from exfiltrating sensitive files via arbitrary chats to fully taking over victims' accounts. After private disclosure of the details, the vulnerabilities have been promptly accepted and fixed by the Element Android team."
Windows RCE write-up: ZDI has published a technical analysis of CVE-2024-20697, a remote code execution in the Windows Libarchive component. This was patched back in January.
Windows Registry research: Google Project Zero researcher Mateusz Jurczyk has published a two-part series on security bugs he found in the Windows Registry. Between May 2022 and December 2023, Jurczyk found 44 vulnerabilities. He since found another six since then.
OpenMetadata exploitation: A threat actor is exploiting vulnerabilities in the OpenMetadata app to take over Kubernetes clusters. OpenMetadata is an app that aggregates metadata from various sources and is often used in large Kubernetes-based infrastructure. The attacker is exploiting five OpenMetadata vulnerabilities patched in mid-March. Microsoft says the end goal of the attacks is to deploy a cryptocurrency miner on the compromised clusters.
PAN zero-day: After security researchers posted proof-of-concept code for a recent zero-day in Palo Alto Networks GlobalProtect firewalls, the company says it's seeing "an increasing number of attacks" targeting its devices. Rapid7 and Zscaler have also published pretty good reports of the zero-day and attacks over the past few days.
Oracle CPU: The quarterly Oracle security updates are out, with patches for 441 vulnerabilities.
Jenkins update: The Jenkins project has released a patch with a fix for the Terrapin Attack.
VMware security update: VMware has released patches to fix three vulnerabilities. [h/t Simon Tsui]
Cisco security update: Cisco has released patches for three vulnerabilities. The most urgent of these is a command injection bug (CVE-2024-20295) in the CLI component of the Cisco Integrated Management Controller (IMC) that can allow threat actors to gain root access. Cisco says it did not detect exploitation of this issue but that proof-of-concept code is available online.
Apex Legends hacks: Destroyer2009, the individual who hacked professional Apex Legends players during a tournament's live stream, says that Respawn Entertainment has finally patched his exploit. [Additional coverage in TechCrunch]
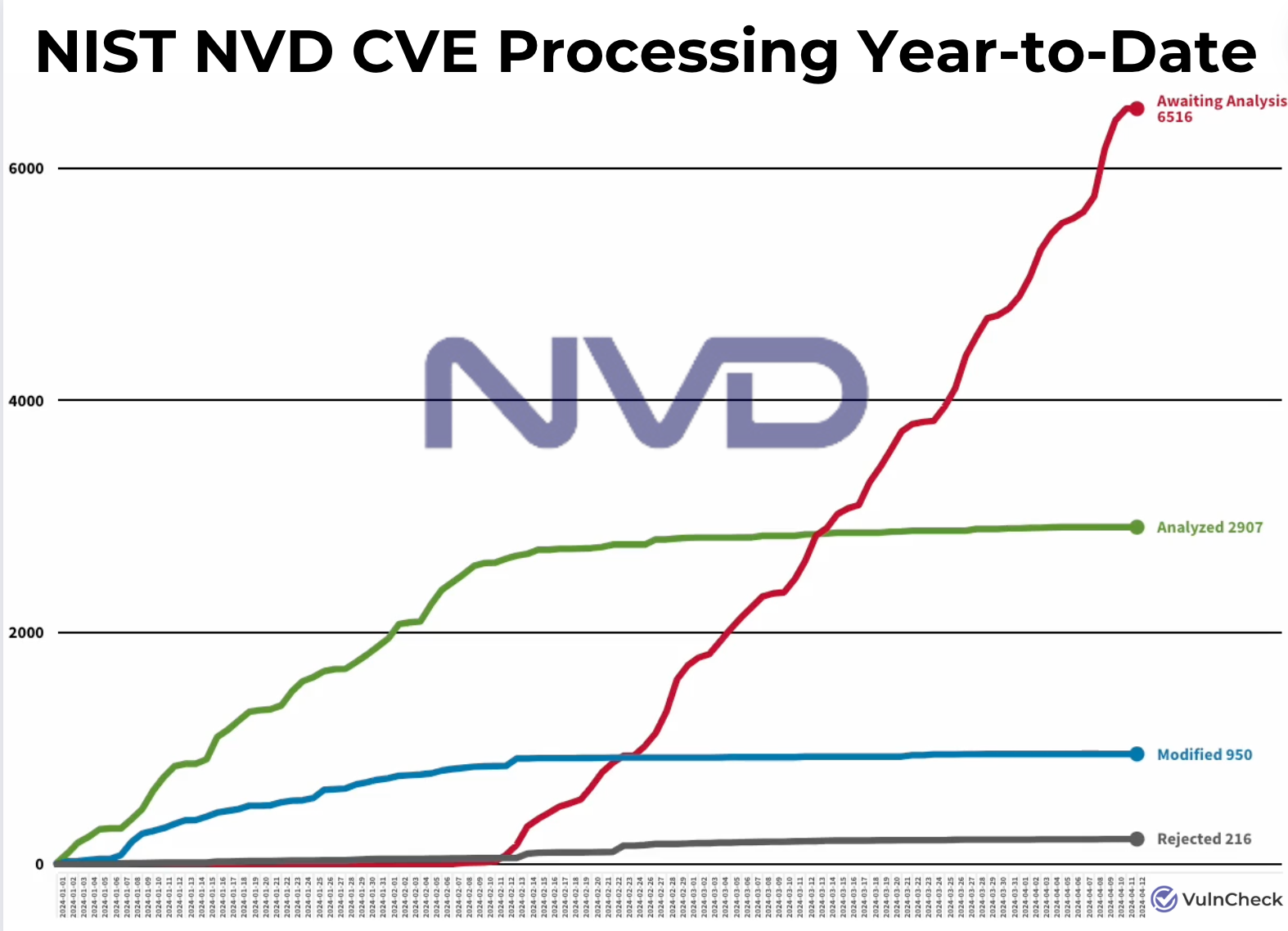
NVD paralysis: It has now been officially two months since the NIST NVD stopped enriching CVEs with additional metadata and details, and we still don't know what exactly happened. According to VulnCheck's Patrick Garrity, the infosec community isn't waiting for NIST to get its business in order, and unprocessed CVEs are piling up more each day.
Infosec industry
New tool—Protobom: The Open Source Security Foundation has open-sourced a new tool named Protobom. The tool allows IT teams to read and generate Software Bill of Materials (SBOMs) files. It can also translate data across multiple standard industry SBOM formats. OpenSSF developed the tool in cooperation with CISA and the DHS.
"Currently, multiple SBOM data formats and identification schemes exist, which makes it challenging for organizations wanting to adopt SBOM usage. Protobom aims to mitigate this issue by offering a format-neutral data layer on top of the standards that lets applications work seamlessly with any kind of SBOM."
New tool—Cloud Console Cartographer: Cloud security firm Permiso has open-sourced Cloud Console Cartographer, a framework for condensing groupings of cloud events and mapping them to the original user input actions in the management console UI. The code is available on GitHub.
New tool—BlauHaunt: A security researcher named cgosec has published BlauHaunt, a tool for filtering and visualizing logon events.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at Google's review of zero-days in 2023. They discuss what this kind of information tells us and how Google's perspective influences the report.




