Why the Snake Takedown Will Hurt the FSB
PLUS: Slowly, the CryptocurrencyScrews Are Tightening
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation, and this edition is brought to you by Material Security, the company that provides visibility, defence-in-depth, and security infrastructure for Office 365 and Google Workspace.
The US government disrupted a long-term Russian intelligence collection capability by attributing "Snake" malware to Russia's Federal Security Service (FSB), publishing a joint cybersecurity advisory on it and also booting it off US computers.
The action is a huge f**k you to Russian intelligence and the FSB. The operation took place on Victory Day and when the Department of Justice announced an FBI operation had wiped Snake off specified US computers it even released a Russian-language version of its press release.

The joint cybersecurity advisory on Snake, co-authored by the US government and Five Eyes cyber security authorities, is tremendous. It manages to cover the big picture while also drilling in to provide detailed technical information in a very readable way.
Per the report:
The Snake implant is considered the most sophisticated cyber espionage tool designed and used by Center 16 of Russia’s Federal Security Service (FSB) for long-term intelligence collection on sensitive targets. To conduct operations using this tool, the FSB created a covert peer-to-peer (P2P) network of numerous Snake-infected computers worldwide. Many systems in this P2P network serve as relay nodes which route disguised operational traffic to and from Snake implants on the FSB’s ultimate targets. Snake’s custom communications protocols employ encryption and fragmentation for confidentiality and are designed to hamper detection and collection efforts.
The report describes Snake as sophisticated because it is stealthy, modular, runs on different operating systems and is also well built, "with the implant containing surprisingly few bugs given its complexity". Initial versions were called "Uroburos" and included part of the historical illustration of an Uroburos (above) by German philosopher Jakob Böhme.
For example, one "uniquely sophisticated" aspect of Snake is that it can act as a server without opening new ports on a compromised system. It hijacks previously open ports and hides its own communications by mimicking legitimate network traffic as would appear on that port. It had a custom authentication mechanism to pick out Snake traffic on those ports and siphon it off rather than sending it to the legitimate destination.
Even though Snake is sophisticated, people make mistakes. The report says "various mistakes in its development and operation provided us with a foothold into the inner workings of Snake and were key factors in the development of capabilities that have allowed for tracking Snake and the manipulation of its data".
One critical error is that the FSB used OpenSSL to handle Diffie-Hellman key exchange but only specified 128 bits instead of 128 bytes. Although key generation was a multi-step process that also involved a pre-shared key, this key clanger allowed the Diffie-Hellman portion to be broken and was presumably a game changer for the Five Eyes understanding of Snake.
The report provides a byte-level description of how Snake works, including how it communicates in a peer-to-peer network, how it is controlled, and where it hides in a file system.
The FSB has been working on Snake since late 2003. It's gone through nearly constant upgrades and redevelopment since then. It seems that Snake is tightly integrated into FSB operations, so we think this exposure will really hurt:
We attribute Snake operations to a known unit within Center 16 of the FSB. This unit more broadly operates the numerous elements of the Turla toolset, and has subunits spread throughout Russia in a reflection of historical KGB signals intelligence operations in the Soviet Union. Snake has been a core component of this unit’s operations for almost as long as Center 16 has been part of the FSB. The extensive influence of Snake across the Turla toolset demonstrates its impact on practically every aspect of the unit’s modern era of cyber operations.
The report is impressively comprehensive and demonstrates just how much intelligence agencies can know about adversary activities at times. It is great to see this much detail published, including key details on how Snake was unravelled.
In addition to the cybersecurity advisory, the FBI also conducted a court-authorised operation (Operation Medusa) to disrupt the network by commanding US-based Snake implants to "overwrite its own critical components". Although the technical work carried out to be able to hijack the Snake malware is impressive, this portion of US government disruption feels like a bit of a letdown, as only eight US-based computers were in scope.
The report says "we have identified Snake infrastructure in over 50 countries across North America, South America, Europe, Africa, Asia, and Australia, to include the United States and Russia itself", so the network is bigger than just eight computers. The DoJ says that "for victims outside the United States, the FBI is engaging with local authorities to provide both notice of Snake infections within those authorities’ countries and remediation guidance".
This isn't the first time the US government has disrupted Russian intelligence botnets. Russian GRU networks known as VPNFilter and Cyclops Blink were disrupted in 2018 and 2022, respectively. Although the cybersecurity advisory described Snake targeting as "purposeful and tactical in nature", both VPNFilter and Cyclops Blink were indiscriminate. VPNFilter is thought to have affected over half a million devices and Cyclops Blink hundreds of devices in the US alone.
Although the networks were far bigger, the court-authorised actions against VPNFilter and Cyclops Blink were also globally effective because they seized command and control domains. That wasn't really possible here.
Even though only eight instances of the malware were "touched" by this FBI operation, Medusa feels like an important milestone. Let's hope we see more of this.
Cryptocurrency: Slowly, the Screws Are Tightening
Late last month the Al-Qassam Brigades (AQB), the military wing of Hamas, announced the shutdown of its cryptocurrency donation program, providing evidence that actions to clamp down on the illicit uses of cryptocurrency are working.
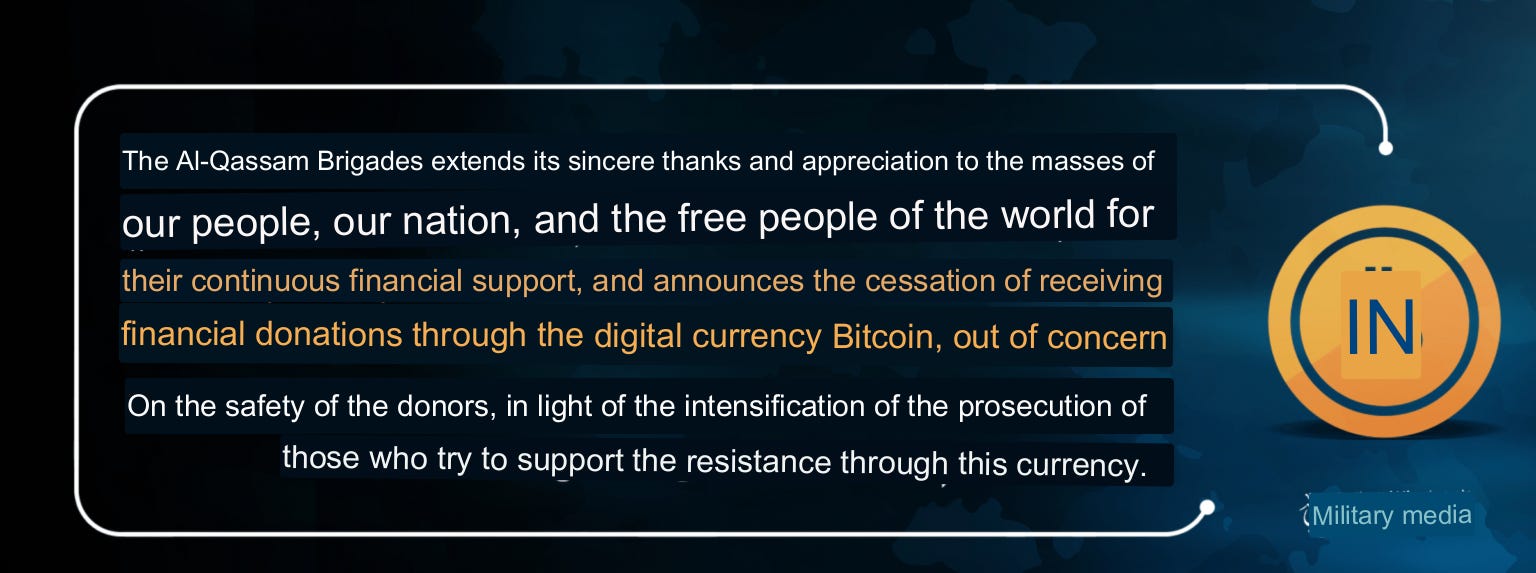
AQB's closing message says government efforts to identify and prosecute donors is the reason for the shutdown, but it's still seeking donations via other means.
Blockchain analysis firm Chainalysis described AQB's donation program as "one of the largest and most sophisticated cryptocurrency-based terrorism financing campaigns". This whole thing is an interesting case study.
AQB started the program in early 2019 by soliciting donations to a single bitcoin address hosted at a regulated US-based exchange. This didn't last long — the account was frozen and law enforcement investigated the individual who created it and also the transactions sent to it.
AQB pretty quickly adopted a system where each donor was provided with a unique Bitcoin address to send their contributions. This makes it harder to trace flows, but not impossible. Chainalysis describes how it was able to track currency flows by "using court documents from associated cases and analysis of transactions from the first two sub-campaigns, we were able to discover addresses that received donations as part of the third sub-campaign".
Thus, AQB's cryptocurrency donations have been the subject of successful US and Israeli law enforcement operations that have seized cryptocurrency.
The take-home message here is that an immutable public record is not that good for keeping crimes secret, and along with the blockchain comes seizures and arrests. Per Chainalysis:
Cryptocurrency isn’t crime-friendly. Thanks to the transparency of blockchains, law enforcement can trace funds used for illicit activity and eventually connect them to real world people and entities — and the immutability of blockchains means that these investigations can take place any time, regardless of how long ago the crime took place, as the transactions’ evidence will be available forever.
Although that transparency is a plus for law enforcement, cryptocurrencies also come with some pretty large downsides for law enforcement.
The Financial Action Task Force (FATF), an international body that sets standards to prevent money laundering and terrorist financing, recently noted that "many countries" have failed to implement virtual asset rules and this "lack of regulation of virtual assets in many countries creates opportunities that criminals and terrorist financiers exploit".
International regulation is always slow, but Russia is a particular concern. It was a FATF member but was kicked out in February of this year because of its invasion of Ukraine and it is hard to see that it will be motivated to implement or enforce any regulations.
In addition to threadbare regulation worldwide, there are also different cryptocurrency-related techniques or technologies that are used by cybercriminals to try to obscure money flows such as mixers or tumblers, DeFi protocols, and chain-hopping across blockchains. (DeFi is where decentralised software on a smart-contract provisioned blockchain provides financial services and many do not implement AML controls).
Here, the US government's idea here is to identify particularly risky entities and either seize or sanction them. Nine exchanges were seized last week and sanctions have been used against several high-risk exchanges and mixers such as Blender and Tornado Cash. Tornado Cash was particularly interesting because it is an ethereum smart contract and theoretically couldn't be stopped. The goal with sanctioning it wasn't necessarily to stop Tornado Cash so much as to deter people from using the service with 'clean' money — if it is only used by criminals it's not useful as a mixer.
US government actions overall form a three-pronged strategy: address criminals directly by mining blockchains to identify and prosecute them, raise international standards, and 'plug gaps' by punishing high-risk entities.
This portfolio approach seems about right, as each strand of effort addresses different aspects of illicit cryptocurrency use. Additionally, Andrew Fierman, head of sanctions strategy at Chainalysis, told this newsletter that it is "difficult to measure the impact of any one step in the fight against illicit activity".
In the case of AQB, what's fundamentally changed here is that the organisation has realised what the implications of a permanent public record really are. Fierman told us that despite the popularity of cryptocurrencies amongst some criminals "cash is more appealing for illicit activity including terrorism financing because it is more difficult to detect and trace".
Unlike Hamas donors, many ransomware criminals live in countries that just don't care about their crimes, so prosecution and arrest is not yet a significant risk. The screws are tightening, but ever so slowly.
Three Reasons to be Cheerful this Week:
- Google adds passkeys support: Google has rolled out passkeys for personal Google Accounts. It's a wondrous new world where you can access your account by authenticating to a local device with biometric rather than with password and second factor. Ars Technica has a good explainer about using Google's passkeys.
- WebAuthn Support for KeepassXC: Offline password manager KeePassXC is working on adding support for WebAuthn, basically the same thing as passkeys.
- Meta disrupts newly launched malware: Meta announced that it had disrupted a new malware family it calls NodeStealer within weeks of it being deployed and disrupted using takedown requests. [more coverage at Risky Biz News].
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and this edition is brought to you by Material Security, the company that provides visibility, defence-in-depth, and security infrastructure for Office 365 and Google Workspace.
Material Security: Keeping Email Safe at Rest
In this video demo Material Security co-founder Ryan Noon demonstrate's the company's email security solution to Risky Business podcast host Patrick Gray.
Shorts
Former Uber CSO avoids prison
Former Uber CSO Joe Sullivan was sentenced to probation, a fine and community service for covering up a data breach in 2016. This newsletter didn't have much sympathy for Sullivan when he was convicted and the judge, William Orrick, also issued a stern warning at the sentencing.
"When you go out and talk to your friends, to CISOs, tell them that you got a break not because of what you did, not even because of who you are," Orrick said. "But because this was just such an unusual one-off — the first of its kind. If there are more, people should expect to spend time in custody regardless of anything."
Adam and Patrick discuss this on this week's Risky Business podcast at the beginning of the show.
Schrodinger's Ransomware
The Institute for Security and Technology released a Ransomware Task Force progress report. This newsletter's high-level summary: more is being done, which is great, but ransomware is still a problem and we have no idea if we are winning or losing.
This gels with recent statements from officials. CISA director Jen Easterly said there was no authoritative body collecting statistics, so "it's hard to tell" if ransomware is up or down.
Dragos Extortion Attempt
Industrial cybersecurity firm Dragos disclosed an incident. A criminal group tried to extort the company after gaining employee-level access. The criminal group gained access by compromising the personal email address of a new hire then following the onboarding instructions sent to that inbox.
Dragos's preparation and response looks to be pretty good. The hacker was able to access documents including internal intel reports and contracts but didn't get any further. The incident occurred on Monday May 8 and by Wednesday Dragos issued a statement complete with a nice timeline.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunes or Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss how cyber insurance could improve security and whether it actually is.
From Risky Biz News:
Iran MoFA hack: A hacktivist group named "Uprising till Overthrow" hacked the server infrastructure of Iran's Ministry of Foreign Affairs, defaced 210 sites, and shut down associated online services. The defacements called for the death of Iran's supreme leader and showed support for the Mujahideen-e Khalq (MEK) party, whose members are currently living in exile in Albania. In a Telegram post following the hack, the group leaked data stolen from MoFA servers, such as hundreds of identification documents, minutes of meetings, the ministry's correspondence, phone numbers of ministry officials, and the names of 11,000 employees.
[much more at Risky Biz News]
China's Great Firewall can now block Shadowsocks, VMess, and Obfs4: A team of academics specialized in internet censorship systems has confirmed that China's Great Firewall can detect and block fully-encrypted protocols such as Shadowsocks, VMess, and Obfs4.
These protocols are far superior to TLS because all their traffic is encrypted, including handshakes, so there are no portions of data that can leak information about any part of the protocol or traffic destinations—and hence why they're called "fully encrypted protocols."
[much more at Risky Biz News]
Smashing Pumpkins extortion: Smashing Pumpkins lead singer Billy Corgan paid hackers a ransom to prevent the leak of nine songs from the band's latest album ATUM. Corgan says the hack took place around six months ago, last year, while the album was going through mixing and mastering. The artist says he paid the ransom out of his own pocket and then notified the FBI, which eventually tracked down and arrested the hacker. Corgan says the hacker obtained the files from a person who was also handling content for other artists but declined to name the individual.



