When Good Cyber Security Leads to Violence
PLUS: SEC’s Disclosure Demands a Halloween Horror for CISOs
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. This week's edition is brought to you by vulnerability management and analysis platform Nucleus Security.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Spotify:

Groups of young Lapsus$-style hackers are rapidly evolving their tradecraft and aggressively exploiting organisations in ways their victims don't expect.
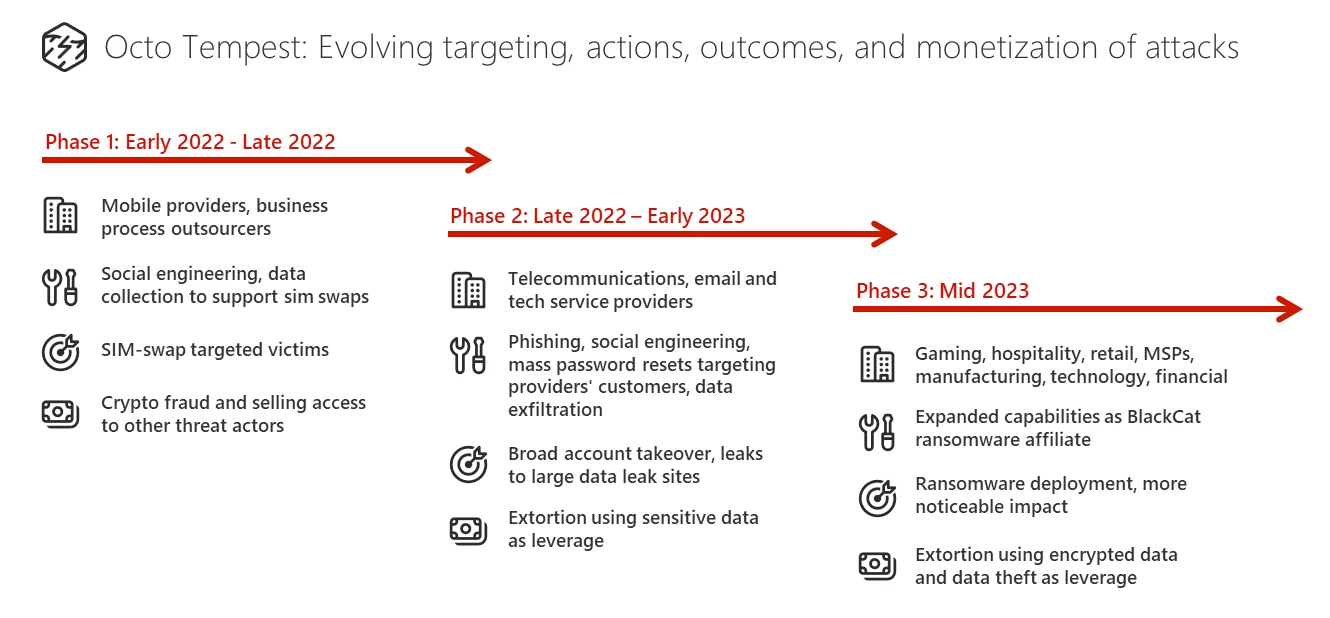
A new Microsoft report describes the evolution of a group it calls Octo Tempest and charts its increasingly aggressive tactics and the rapid change in its targets. In early 2022, Octo Tempest focused on social engineering and targeting mobile providers to enable SIM-swapping crimes such as cryptocurrency theft, and selling the access gained to other criminals.
However, by early 2023, the group was targeting telecommunications, email and tech service providers, and collaborating with the ALPHV/BlackCat ransomware-as-a-service operation to extort organisations by threatening to leak stolen sensitive data.
By June 2023, Octo Tempest had started to deploy encrypting ransomware payloads and, over the year, has expanded its targets to businesses in sectors such as resources, gaming, hospitality, consumer products, retail, managed service providers, manufacturing, law, technology, and financial services.
Although Microsoft refers to this group as Octo Tempest, other security researchers have tracked similar behaviour under entities with different names (Scattered Spider by Crowdstrike, UNC3944 by Mandiant and Oktapus (because of its targeting of identity provider Okta). These names, however, do not describe groups with well-defined and stable membership so much as subsets of a broader ecosystem of individuals that cooperate on different criminal activities using an ever-evolving set of effective and increasingly aggressive tactics.
Some individuals involved have been linked to the Comm, a particularly nasty online group a recent 404 Media article describes as a nebulous network of hackers, gamers, Discord adherents and others:
The Comm is large, with hundreds or thousands of participants in various Telegram channels and Discord servers, with many different subsections and subgroups focusing on their own priorities.
In many cases, members of the Comm are not limited to just performing SIM swaps, which is when a hacker takes over a phone number to then break into the target’s online accounts. Members also participate in and commission physical violence. Comm members, for example, have kidnapped one another to gain access to a rival’s cryptocurrency. Gunmen fire weapons at targets' houses or throw bricks through their windows. Violence only makes up a slice of Comm, but it carries significant cultural weight throughout the group: Discord and Telegram channels often quickly share videos of the latest robbery or attack. Members have also performed swattings against schools and universities.
A standout feature of Octo Tempest and related groups is their very effective use of social engineering to gain access to organisations. Microsoft says they do their homework:
Octo Tempest commonly launches social engineering attacks targeting technical administrators, such as support and help desk personnel, who have permissions that could enable the threat actor to gain initial access to accounts. The threat actor performs research on the organisation and identifies targets to effectively impersonate victims, mimicking idiolect on phone calls and understanding personal identifiable information to trick technical administrators into performing password resets and resetting multifactor authentication (MFA) methods. Octo Tempest has also been observed impersonating newly hired employees in these attempts to blend into normal on-hire processes.
Ransomware incident response firm Coveware wrote about Scattered Spider, a related group, in its latest quarterly report. Although the group is adept at social engineering, it appears that just a few individuals appear to have the right skills:
One of the most common overlapping tactics observed was the skillful social engineering of the IT support desk to subvert, reset or overcome multi-factor authentication. Not only did we consistently see this tactic, but voice recordings from impacted enterprises confirmed that this group was consistently using the same two or three individuals to perform the social engineering.
One of the more eye-opening details in Microsoft's report is Octo Tempest's use of threats of physical violence to try to coerce targeted individuals into sharing credentials for corporate access. This takes the personal information gathered in prior research and uses it to lend credibility to threats of physical violence, making use of home addresses and family names, for example.
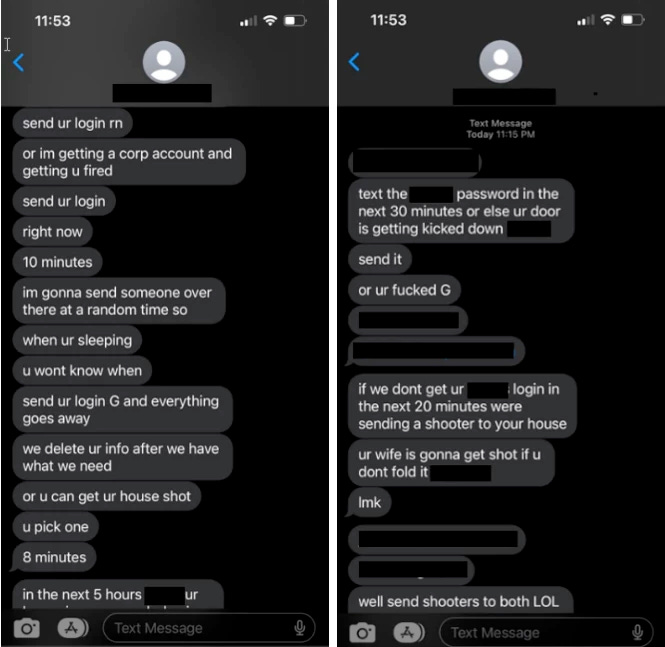
This is not new behaviour. The Cyber Safety Review Board's review of Lapsus$ and related groups published in July this year found some threat actors were targeting cybersecurity professionals and their families with swatting attacks.
Bill Siegel, Coveware's CEO, told Seriously Risky Business these threats were typically used as a last resort when quieter tactics such as social engineering had failed. He wasn't convinced that threats of violence were all that effective at gaining access, saying "in our experience, this tactic has the opposite of its intended effect".
"It hardens the resolve of the victim organisation to resist the attack and the extortion tactics," he continued. "It also opens the criminals up to a wide range of new potential criminal charges if they are ever caught."
However, threats of violence are among the tactics that current cyber security practice isn't prepared for — the rubber hose attack doesn't appear in the latest MITRE ATT&CK framework, for example. Microsoft's report says threats of violence are rare, but Siegel says these threats can escalate to swatting attacks.
While we hope swatting attacks remain rare, the potentially severe consequences mean CISOs should implement measures to minimise their risk and impact.
Coveware also describes a new extortion tactic which we are dubbing PITA extortion (Persistent IniTial Access extortion). Coveware writes:
The tactic involves persistence that is extremely deep and time consuming to cleanse. Once achieved, the threat actor then dangles the offer of "pay us and we will leave… Don’t pay us and we will continue to root around causing chaos".
Microsoft and Coveware have a series of recommendations on how to deal with these kinds of threat actors. Beyond expected recommendations such as using phishing-resistant MFA for administrators, Microsoft also advocates the use of "out-of-band" communications channels during incident response, because Octo Tempest often monitors corporate messaging networks to gain insight into defender’s plans. It often communicates on these networks to taunt defenders too.
Coveware recommends hardening IT helpdesk procedures when password reset or MFA change requests are made to confirm the identity of the calling party. These include calling employees back on numbers listed in the company's internal directory and asking for photographic proof of identity. However, Coveware points out that, especially when IT support is outsourced offshore, incentives that encourage the quick resolution of problems actually make social engineering easier.
Aggressive Lapsus$-style hackers are adapting the tactics they use very rapidly and the cyber security ecosystem needs to keep up.
SEC’s Disclosure Demands a Halloween Horror for CISOs
The US Securities and Exchange Commission has announced charges against US software maker SolarWinds and its CISO, Timothy Brown, "for fraud and internal control failures relating to allegedly known cybersecurity risks and vulnerabilities".
In other words, the SEC alleges Brown and SolarWinds defrauded investors by "overstating SolarWinds' cyber security practices and understating or failing to disclose known risks".
The formal complaint alleges that a SolarWinds 'Security Statement', as posted on its public website did not reflect the reality of the company’s operations. The security statement claimed that SolarWinds: followed the National Institute of Standards and Technology Cybersecurity Framework; followed a Secure Development Lifecycle; had implemented a strong password policy; and maintained strong access controls.
The SEC alleges that all these statements were untrue and also material to the company (important enough to affect the companies perceived value). In one example, SolarWinds used an Akamai server to distribute updates to customers whose password was 'solarwinds123'. Even worse, the credential was discovered by a security researcher who found it in a public github repository.
To be absolutely clear here, the SEC is not trying to punish SolarWinds' for poor cyber security practices or for being the victim of a security incident. Its beef is with the public statements that allegedly whitewashed the true state of SolarWinds security.
The SEC also takes issue with what it describes as SolarWinds' "boilerplate" cyber security disclosure that was filed with the SEC when the firm returned to being a publicly traded company in October 2018. The SEC says this text only contained "generic and hypothetical risks that most companies face", and excluded specific risks the company was aware of.
SolarWinds is far from the only company using generic boilerplate disclosures when it comes to cyber security risk. The SEC wants to use SolarWinds as an example to let companies know they should "do better" and more accurately reflect the specific cyber security risks they face.
The Risky Business podcast has an extensive discussion of this issue with Dmitri Alperovitch and former CISA Director Chris Krebs. Krebs thinks this case will have "massive implications". He said that if you are a CISO in a publicly-traded organisation "that is not fully empowered by the C-suite that is not fully resourced, equipped, with the appropriate personnel, then your risk tolerance just dropped a whole bunch".
Risky Business News has a more detailed write up that includes the reaction from a variety of security industry people.
Three Reasons to Be Cheerful This Week:
- Nigerian cybercrime training centre shut down: The Nigeria Police Force announced that its National Cybercrime Center had shut down a recruitment and mentoring hub run by a cybercrime syndicate. The syndicate is linked to romance scams, business email compromise and financial fraud.
- Countries move against ransom payments, a little: 40 countries in the International Counter Ransomware Initiative plan to commit to not paying ransoms when national government computer systems are affected. Stifling payments is clearly a focus of the group, and stopping government payments is a start.
- Good news everyone! Ransomware isn't ten times worse! In last week's Risky Business podcast NSA Cybersecurity Director Rob Joyce praised the FBI's efforts to disrupt ransomware actors. Joyce said that without the FBI's actions ransomware "would be 10x worse".
Sponsor Section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on the rise and evolution of vulnerability threat intel and how CISA KEV's new ransomware section will be a game changer.
Shorts
AI Safety and Security For All
US President Joe Biden has issued an Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence. It's very long but the fact sheet is far more accessible.
The cyber security-related aspects focus on making AI technology itself safe, secure and trustworthy and also using it to improve cyber security. This includes establishing a program to develop AI tools to find and fix vulnerabilities in critical software.
Another element of the EO aims to protect firms from the theft of AI-related intellectual property.
Apple Shuts the Door on Illicit (and Lawful) iMessage Access
Apple announced an upcoming feature called iMessage Contact Key Verification that allows users to verify they are only messaging the person or people they intend to.
The idea here is to protect against the compromise of Apple's key directory service, which could allow an adversary to decrypt messages.
This would also make impractical what is often called the GCHQ proposal for exceptional access. In this proposal, sometimes also known as the 'ghost user protocol', government's compel service providers to silently and invisibly add law enforcement personnel into ongoing conversations under warrant.
Breaking Open Operation Triangulation
Kaspersky has a good write up of its efforts to recover the malware used in what it calls Operation Triangulation, an iPhone and iPad malware campaign that targeted the devices of some Kaspersky employees. The Russian FSB security service attributed the operation to the NSA and said that thousands of devices belonging to Russian citizens had been affected.
The developers took many precautions to prevent recovery and analysis of their malware. It took Kaspersky several months but it was able to recover the exploits, implant and various modules used in the attack.
StripedFly Mystery
If you enjoy malware deep dives, Kim Zetter also examines the mystery of StripedFly, an espionage platform that masquerades as a cryptominer and uses a custom TOR implementation for communication.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq talk about what is really at stake with cyber security and why it is worth investing in.
From Risky Biz News:
CitrixBleed vulnerability goes from bad to disastrous: A Citrix vulnerability has entered the dangerous stage of mass exploitation as multiple threat actors are compromising unpatched devices all over the internet in a race with each other to steal their session tokens.
Known as CitrixBleed and tracked as CVE-2023-4966, the vulnerability impacts Citrix ADC and Citrix NetScaler, which are extremely complex networking devices used in large enterprise and government networks in multiple roles, such as gateways, proxies, caching, VPN servers, and a bunch of other stuff.
The vulnerability allows threat actors to send junk data to the Citrix OpenID component that will crash and leak a part of the device's memory. In some cases, this memory may contain session tokens that attackers can collect and then bypass authentication and access the device. For a more technical explanation, check this write-up from Assetnote researchers.
[more on Risky Business News including more on the bug's exploitation which has possibly been occurring since late August]
First Kazakhstan-based APT discovered, tries to disguise itself as Azerbaijan: In a blog post this week, researchers with Cisco Talos have formally linked a cyber-espionage group named YoroTrooper to Kazakhstan, making it the first official APT group operating out of the country.
First spotted in the wild in June 2022, the group has followed the pattern of most nascent cyber espionage programs, starting with run-of-the-mill commodity malware and slowly moving to custom capabilities in recent attacks.
[more on Risky Business News]
Spyware alerts in India: Apple has notified over a half dozen lawmakers from India's main opposition parties that their iPhones have been targeted by state-sponsored attacks. Victims included figures from India's main opposition parties, such as the National Congress, AIMIM, the AAP, and the Communist Party. The alleged hacking attempts took place weeks before Indians are set to elect members to its new Parliament. In a press conference, Rahul Gandhi, leader of the National Congress Party and Modi's main rival for the upcoming elections, accused the Indian government of the attempted hacks. Besides politicians, two Indian journalists and a member of an NGO also received notifications from Apple. [Additional coverage in TechCrunch]



