We Cannot Allow a Spy Balloon Gap!
PLUS: Iran Throws Epic Cyber Tanty
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and founding corporate sponsor Proofpoint.
Mr President! We Cannot Allow a Spy Balloon Gap!
The "spy balloon" that traversed the United States probably didn't achieve much for Chinese intelligence but it sure did manage to whip up some drama and, ahem, levity.

Our initial response to news that a spy balloon was merrily floating its way across the continental United States was scepticism. What could the PRC hope to achieve with a balloon that it couldn't achieve with other intelligence sources, such as space-based collectors?
Well, according to the Chinese government it wasn't a spy balloon at all. In a statement that leaves behind a truly hilarious amount of wiggle room, China's government claimed it was a civilian research airship used for "mainly meteorological" purposes.
The yanks aren't buying it. The US government is adamant that balloon was up to no good.
There are actually some scenarios where military balloons make sense — US and Chinese papers have described scenarios where they deliver unique capabilities. Being closer is better when it comes to collecting signals or taking photos, they can provide long "dwell times" over targets and they can also view targets from different "look angles", which can be important when targets are shielded from predictable satellite passes.
The whole thing is still pretty weird.
We think US intelligence assessments that it was a surveillance balloon are most probably right, but there is always the possibility that it was something more innocent.
Andrew Davies, a lecturer in Defence studies at the Australian National University and former Australian Defence intelligence official, was also open to the possibility it really was a research balloon. He told Seriously Risky Business that when it comes to intelligence assessments "people see what they expect to see".
Not that we'll ever know. If US forensic teams piece this thing back together and discover it was actually a friendly weather balloon we can't imagine there'll be a press release.
Davies also thinks the intelligence opportunities balloons can provide are incremental rather than game-changing. If it were a "real problem", Davies told this newsletter, the US government would have downed the airship sooner rather than allowing it to traverse the entire continental US. In other words, the intelligence value to the PRC was so low the US wasn't prepared to take "even a small risk of damaging something on the ground".
A senior US official made comments along similar lines in a post on the Defense.gov website.
"Currently, we assess that this balloon has limited additive value from an intelligence collective collection perspective," the official said. "But we are taking steps, nevertheless, to protect against foreign intelligence collection of sensitive information."
There were distinct advantages in allowing the balloon to continue across the US before it was downed. In addition to minimising the risk of civilian casualties it also allowed the US to take a good look at it. They spied! On the spy balloon!!
At a press briefing the National Security Council strategic communications coordinator John Kirby said "we turned the tables on China and collected against the balloon, so that we would learn more about China’s capabilities and tradecraft."
It also allowed the balloon to be brought down over water, which meant the US government could recover its payload — a hardware "collection" opportunity, if you will.
There has been serious diplomatic fallout over this thing. US Secretary of State Antony Blinken postponed a trip to China indefinitely until "conditions are right". China, meanwhile, is feigning anger after those crazy Americans shot down its sweet, innocent, "mainly meteorological" balloon.
In Washington DC, meanwhile, the US is briefing 40 foreign embassies on what it knows about Chinese balloon espionage. The balloon is part of an ongoing program that has operated for several years, officials say, partly out of Hainan island off China's south coast.
Three balloons apparently transited the US during the Trump administration without being detected. General Glen VanHerck, commander of the North American Aerospace Defense Command (NORAD) told the press that the US military "did not detect these threats" and described the lack of visibility as a "domain awareness gap".
We clearly cannot allow a spy balloon gap, so we're guessing a defence contractor is about to make some serious bank on that.
Despite the diplomatic fallout, we think most people will forget about all this in a week or two. But we won't forget. At Risky Biz HQ, that "mainly meteorological" spy balloon was our Ever Given.
Farewell, you magnificent bastard.
Iran Throws Epic Cyber Tanty
Last week Microsoft attributed a hacking operation that targeted French satirical magazine Charlie Hebdo to an Iranian state hacking group already sanctioned by the US government. It reminds us of North Korea's 2014 attack against Sony Pictures and it's a great example of how some leaders use cyber operations to protect egos instead of vital interests.
In early January a previously unheard of group calling itself "Holy Souls" claimed to have obtained the personal information of over 200,000 Charlie Hebdo customers. Per Microsoft's announcement:
As proof, Holy Souls released a sample of the data, which included a spreadsheet detailing the full names, telephone numbers, and home and email addresses of accounts that had subscribed to, or purchased merchandise from, the publication. This information, obtained by the Iranian actor, could put the magazine’s subscribers at risk of online or physical targeting by extremist organisations.
We believe this attack is a response by the Iranian government to a cartoon contest conducted by Charlie Hebdo. One month before Holy Souls conducted its attack, the magazine announced it would be holding an international competition for cartoons “ridiculing” Iranian Supreme Leader Ali Khamenei. The issue featuring the winning cartoons was to be published in early January, timed to coincide with the eighth anniversary of an attack by two al-Qa’ida in the Arabian Peninsula (AQAP)-inspired assailants on the magazine’s offices.
Microsoft calls the group it believes to be responsible NEPTUNIUM. This is the same group the US Department of Justice says is operated by an Iranian cyber company named Emennet Pasargad. The company and some of its employees have already been sanctioned by the US government over attempted interference in the 2020 election. Two of its employees were also indicted for cyber-related offences.
Now, apparently, they're striking a blow for Iran's critical interests by attacking a satirical magazine.
Microsoft says elements of the attack against Charlie Hebdo map nicely onto known Iranian tradecraft. "The pattern [of behaviour] seen here is typical of Iranian state-sponsored operations".
At a high-level, the criteria Microsoft uses to make this call are not all that convincing. These include the use of hacktivist personas, the leaking of private data, the use of inauthentic "sockpuppet" accounts, the impersonation of authoritative sources and contacting news media organisations.
However — and this is the good part — Microsoft bolsters these high-level summaries with a more detailed "Influence Operation Attribution Matrix" and links readers to its Framework for Attribution.
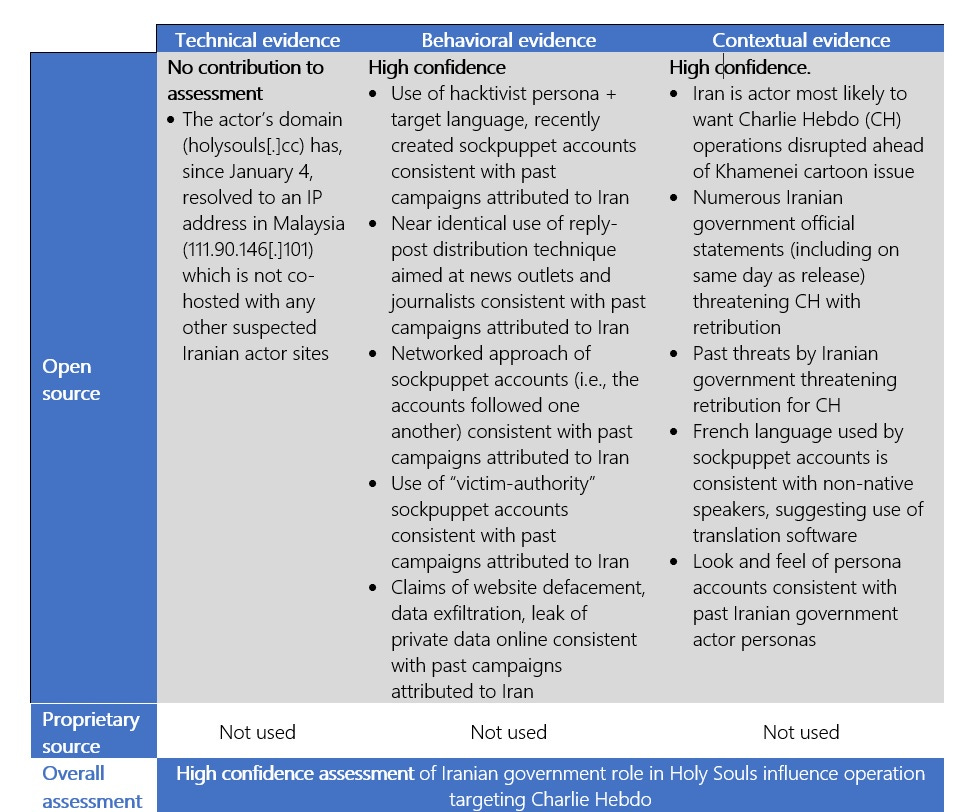
The framework describes a structured way of thinking about attribution and the matrix provides more detail about Microsoft's reasoning. It's a good way of presenting lots of strands of evidence which on their own are not convincing but, when presented together, seem reasonable enough. Showing your work is good stuff.
There's a broader lesson here, too. Assuming Microsoft's attribution is correct, this operation demonstrates how different types of governments use cyber operations for vastly different purposes. If the cyber domain is a playing field, states are playing different games.
The Five Eyes use cyber operations to collect intelligence on government and military targets and to advance military objectives through offensive cyber operations that degrade, disrupt or deny.
This is a very narrow vision of what cyber operations can be used for. Other countries — particularly those that make up what we'd call the "illiberal bloc" — use cyber operations for whatever takes their fancy. IP theft, crypto theft, bank theft, election interference and even this sort of "protect dear leader" stuff.
The main lesson here is you just can't expect your adversaries to act like you would, especially when said adversaries are ruled by tremendously insecure people with fragile egos.
The Best Ransomware Case Study in the World
The Conti ransomware crew's attack on the Irish national public health service (HSE) is becoming the best reported case study on the causes and impacts of a serious ransomware attack.
Reporting from Bloomberg this week does an excellent job covering the attack's effects on patients and complementing it with the inside view from criminals associated with Conti. This new reporting builds on a late-2021 PricewaterhouseCoopers (PwC) post-incident review commissioned by the HSE Board that focussed on the IT and management-related aspects of the incident.
The HSE employs over 130,000 staff in over 4,000 locations and 54 hospitals. Although ransomware attacks on healthcare providers happen all too frequently, the attack on the HSE is the largest ever recorded.
The PwC review describes the impacts dryly:
In the early hours of Friday 14 May 2021, the HSE was subjected to a serious cyber attack, through the criminal infiltration of their IT systems (PCs, servers, etc.) using Conti ransomware. The HSE invoked its Critical Incident Process, which began a sequence of events leading to the decision to switch off all HSE IT systems and disconnect the National Healthcare Network ("NHN") from the internet, in order to attempt to contain and assess the impact of the cyber attack. These actions removed the threat actor’s (the "Attacker") access to the HSE’s environment.
This immediately resulted in healthcare professionals losing access to all HSE provided IT systems - including patient information systems, clinical care systems and laboratory systems. Non-clinical systems such as financial systems, payroll and procurement systems were also lost. Significant disruption immediately occurred and many healthcare professionals had to revert to pen and paper to continue patient care. Healthcare services across the country were severely disrupted with real and immediate consequences for the thousands of people who require health services every day.
Bloomberg's reporting puts flesh on these dry bones.
Mary Brosnan, the National Maternity Hospital’s director of midwifery and nursing, recalls being "completely at sea." Hospital staff had to ask patients what they could remember about their medical histories and medication routines, then create new handwritten records. This was risky, given that not all patients can recall such information reliably and some have trouble communicating in English. “It was really frightening,” Brosnan says. "Our biggest worry was, if we do an operation on a woman, and we don’t know enough about her, and she dies in theater. God forbid, because of blood loss, or she has a stroke because we didn’t realise she had this or that wrong with her."
The hospital's drug dosage calculation systems were also affected, and Brosnan told Bloomberg that staff "were back to calculators and bits of paper trying to work out drug dosages".
"It is life-changing if you make a mistake — life-changing for the family and life-changing for the staff member, too," she said.
There was a litany of other impacts. Cancer treatment regimes were interrupted and radiation treatment for children was put on hold because the X-ray radiotherapy devices were inoperable. These are just two examples of many.
Bloomberg's report also examines the fallout within Conti itself. The attack sparked internal discord about whether attacks on hospitals and other critical public infrastructure were acceptable. Within the week Conti had released the decryption key for the HSE attack and although some ransomware operators avoid healthcare others just don't care. Just months after the HSE attack a Florida hospital was attacked by a Conti affiliate, resulting in further infighting in the group.
For whatever reason – and we really don't know why — Conti coughed up the decryption key about a week after the attack, which helped the HSE recover faster. The Irish Defence Forces cyber unit was involved in the recovery effort and Steven Keane, its commander, told Bloomberg it would have taken "magnitudes of time longer" to recover without the key.
Recently John Ward, the HSE's interim CTO, told a British national security committee that going public was a major benefit for the HSE's response. Although he didn't know why Conti released the decryption key, he implied that publicly stating that the attack had put lives at risk may have resulted in a "change of heart".
Seriously Risky Business previously examined the PwC review, which provides more detail on the organisational dysfunction that led to the HSE being vulnerable. There were actually several missed opportunities to prevent or disrupt the attack, but PwC's dissection of the organisation's cyber security posture made it feel that failure was inevitable.
Together, these separate reports provide a multi-faceted view of this ransomware attack — the management dysfunction, Conti's internal strife, and the human impacts of the disruption. It helps us all understand what went wrong, why it matters, and what others can do to avoid a similar fate.
Three Reasons to be Cheerful this Week:
- GoodRx penalised for sharing sensitive health info with advertisers: The US Federal Trade Commission (FTC) has fined prescription drug provider GoodRx for unauthorised sharing of its customer's health data with advertisers. According to the FTC's complaint, GoodRx shared sensitive health data — including users' prescription medications and health conditions — to advertisers such as Facebook, Google and others. The basis for the FTC action is that GoodRx didn't comply with the Health Breach Notification Rule — the company shared customer's data but didn't tell them of what was effectively a data breach.
- Dutch police dismantle Exclu crimephone service: Dutch police announced they'd cracked Excl, yet another encrypted phone service marketed to criminals. The police say they were able to read messages for five months and arrests include owners and administrators of the Exclu service as well as users.
- Stalkerware maker to inform victims: Patrick Hinchy, a New York-based spyware maker has agreed to notify device owners that they are being monitored, in a deal with the New York attorney general's office. Hinchy also agreed to pay USD$410,000 in civil penalties. He allegedly had a suite of 16 companies for illegally promoting spyware.
Sponsor Section
Seriously Risky Business is supported by the Hewlett Foundation's Cyber Initiative and corporate sponsor Proofpoint.
When it comes to phishing, it's Super Bowl season.
Have you clicked “Report Junk” lately on your #mobile device? Millions of these junk text messages are sent to our researchers each day for analysis.
— Proofpoint (@proofpoint) 12:05 PM ∙ Feb 6, 2023
In the 2-week period of the playoffs, #SuperBowl related spam, abuse, and #smishing reports increased by 860% across N America.
Okta and Passwordless Authentication
Risky Business publishes sponsored product demos to YouTube. They're a great way for you to save the time and hassle of trying to actually get useful information out of security vendors. You can subscribe to our product demo page on YouTube here.
In our latest demo, Brett Winterford and Harish Chakravarthy demonstrate to host Patrick Grey how Okta can be used for passwordless authentication. These phishing resistant authentication flows — even if they are not rolled out to all users — can also be used as a high-quality signal of phishing attempts that can be used to trigger automated follow-on actions.
Shorts
European Aviation Ransomware Snapshot
EUROCONTROL, a European civil-military organisation dedicated to supporting European aviation, has published a one-page "data snapshot" that looks at ransomware targeting the aviation supply chain.
Globally, EUROCONTROL says "we are aware of approximately 2.5 reported ransomware attacks per week on aviation-related organisations". The good news is that incident reporting is improving and since 2021 EUROCONTROL has a clearer idea of the scale of the problem as information about more incidents are being shared with its CERT.
Although it looks like there may be a small downward trend, the report cautions that this is likely just a side-effect of the invasion of Ukraine. EUROCONTROL expect to see an increase in ransomware incidents in 2023.
India Has Blocked over 300 Chinese Apps
The Indian Ministry of Electronics and Information Technology is moving to block some 232 apps that are offering betting and loans services. Techcrunch reports that the Indian government is concerned about both predatory loans and that these apps could be used for espionage and propaganda.
Some of these apps are linked to China and in recent years India has blocked over 300 apps with links to China.
Risky Biz Talks
In addition to a podcast version of this newsletter (last edition here), the Risky Biz News feed (RSS, iTunesor Spotify) also publishes interviews.
In our last "Between Two Nerds" discussion Tom Uren and The Grugq examine how states have different thresholds for compelling companies to act on their behalf. Where do those thresholds lie and is one approach better than another? Why do states have these different approaches?
From Risky Biz News:
Ransomware wave hits thousands of VMWare ESXi servers: A massive ransomware wave has hit VMWare servers over the weekend, encrypting thousands of unpatched and internet-exposed ESXi systems.
The attacks are exploiting a two-year-old vulnerability tracked as CVE-2021-21974, which allows the threat actors to execute remote commands on unpatched VMWare ESXi servers via their OpenSLP service (on port 427).
(more on Risky Biz News, including that many of the affected organisations were using ESXi servers rented from cloud providers).
Addendum: CISA has released a script to help affected organisations recover.
🚨We released an ESXiArgs ransomware recovery script on GitHub to allow organizations to attempt recovery of virtual machines affected by the ESXiArgs ransomware attacks: github.com/cisagov/ESXiAr… #StopRansomware
— Cybersecurity and Infrastructure Security Agency (@CISAgov) 11:49 PM ∙ Feb 7, 2023
Operation Magicflame: Interpol and Hong Kong police have dismantled the server infrastructure of an international cybercrime syndicate. The crackdown, part of what Interpol called Operation Magicflame, targeted a cybercrime group that used SMS phishing to redirect users to download one of 563 malicious apps they had hosted on servers around the world. Officials said the gang ran 258 servers, 192 of which were hosted across Hong Kong data centers. The gang used the malicious apps to steal data from infected devices and then steal funds from bank accounts. According to the South China Morning Post [non-paywalled version], the group appears to be made up of suspects from mainland China, the Philippines, and Cambodia and targeted users located mostly in Japan and South Korea.
OneNote abuse: Security firms Proofpoint, WithSecure, OpalSec, and Yoroi say that over the past few months, the number of threat actors abusing Microsoft OneNote documents to deliver malware via email has increased dramatically. (more on Risky Biz News)



