Risky Biz News: US warns space sector of hacks, spying, IP theft, and sabotage
In other news: Juniper releases out-of-band security update; TSSHOCK attack can steal funds from MPC crypto-wallets; and Tesla identifies Handelsblatt whistleblowers.
This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
As the US private space sector is growing into a global behemoth and as Starlink shows the crucial role private satellite networks can play in a military conflict, the US government is urging companies to bolster their defenses against foreign sabotage and espionage.
Three US intelligence agencies—the FBI, the National Counterintelligence and Security Center, and the US Air Force Office of Special Investigations—published a joint security advisory [PDF] last week describing the type of threats the commercial space industry could face from foreign intelligence agencies.
Officials warn of hacks, malicious insiders, employee recruitment efforts, and misleading investments and business partnerships.
All of these are designed to enable espionage, the theft of intellectual property, and sabotage of space infrastructure in the case of a military conflict.
Officials urge the commercial space industry to monitor IT infrastructure, employees, contractors, and suppliers alike. Possible indicators and signs companies are being targeted include:
• Unusually high cyber activity targeting your company from unknown parties.
• Requests to visit your company facilities from unknown or foreign entities.
• Specific and probing questions about sensitive, internal, and proprietary information.
• Elicitation at conferences or online fora.
• Unsolicited offers to establish joint ventures with companies tied to foreign governments or state-owned enterprises.
• Attempts to recruit your company's technical experts, including through invitations to travel to a foreign country, offers of employment (such as consultancy work), and provision of financial incentives in exchange for proprietary information.
• Acquisition or investment efforts by foreign companies via wholly-owned subsidiaries registered in third countries that are designed to obscure the parent company's connections.
The joint advisory doesn't name any country, but a previous ODNI report [PDF] called China the US' biggest cyber threat, including activities targeting US space programs and capabilities.
Russia's hack of American satellite operator Viasat on the eve of its Ukraine invasion also puts the Kremlin regime on the US' shortlist.
The Hak-a-Sat contest held at this year's DEFCON conference also proved hacking commercial satellite infrastructure is not the impossible task everyone thinks it is.
The threat of sabotage is not to military satellite networks, which are quite secure, but to network and infrastructure operated by the commercial space sector. A Viasat-like attack could cripple the operation of military-adjacent systems, possibly disrupting communications and transportation in time of need.
This very same thinking is why earlier this year, the Cyberspace Solarium Commission recommended that US space systems be designated a critical infrastructure sector.
That kind of designation brings a lot more government resources and reporting requirements to the table, but short of that, this joint advisory will have to do.

Breaches, hacks, and security incidents
DDOS attacks on JP's nuclear sites: The Anonymous Italy hacker collective launched DDoS attacks against the websites of various nuclear power organizations in Japan. Targets included the Japan Atomic Energy Agency, Japan Atomic Power, the Atomic Energy Society of Japan, and websites associated with the Fukushima facility. The attacks come after the group also targeted the International Atomic Energy Agency. [Additional coverage in Mainichi]
India's Independence Day cyberattacks: Indian officials say hacktivist groups attacked more than 1,000 websites during the country's Independence Day celebrations last week, on August 15. Most of the DDoS attacks targeted the websites of government agencies, banks, and financial services. The attacks were part of OpIndia and were conducted by hacktivist groups from Pakistan and other Muslim nations. [Additional coverage in the Business Standard]
Latitude cyberattack losses: Australian financial services company Latitude says it incurred costs of AUS$76 million (USD$49 million) relating to a cybersecurity incident the company suffered in March. The incident took place after a threat actor obtained an employee's login credentials and stole files containing the data of more than 14 million customers. In a document [PDF] filed with the Australian Stock Exchange, Latitude says they were making a profit in January and February before the hack and associated costs pushed the company into a 3% loss YoY. Despite the losses, Latitude says it is stable. [Additional coverage in itNews]
Tesla notifies employees of breach: American EV automaker Tesla is notifying more than 75,000 employees that their personal data was stolen earlier this year. The incident is related to a series of articles published by German news outlet Handelsblatt. The articles were based on more than 100 GB of confidential data leaked by a whistleblower and exposed that Tesla had failed to address complaints about its cars and driver assistance system. In a data breach notification filed with US authorities, Tesla says it identified and took legal action against two former employees that took and shared the data with Handelsblatt reporters.
"The investigation revealed that two former Tesla employees misappropriated the information in violation of Tesla's IT security and data protection policies and shared it with the media outlet. The outlet has stated that it does not intend to publish the personal information, and in any event, is legally prohibited from using it inappropriately. Tesla immediately took steps to contain the incident, understand the scope, and protect your information. Among other things, we identified and filed lawsuits against the two former employees. These lawsuits resulted in the seizure of the former employees' electronic devices that were believed to have contained the Tesla information. Tesla also obtained court orders that prohibit the former employees from further use, access, or dissemination of the data, subject to criminal penalties."
Exactly Protocol crypto-heist: A hacker has stolen $7.3 million worth of crypto-assets from DeFi platform Exactly Protocol. The company confirmed the incident and blamed the loss on a vulnerability in one of its smart contracts. Exactly says it already notified the police and is working to identify the hacker and recover its funds.
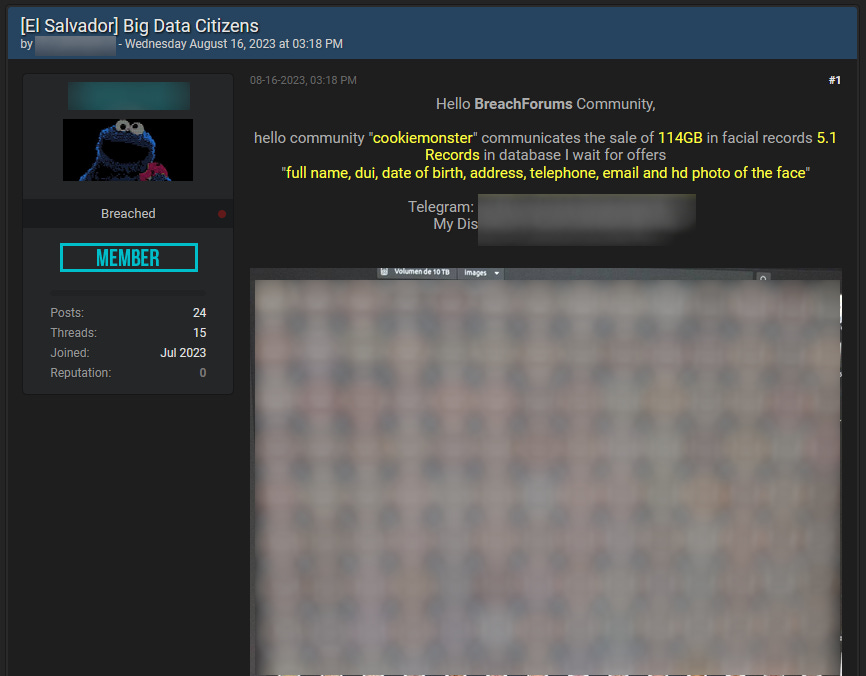
El Salvador database: A threat actor claims to have obtained and is now selling a database containing the personal information of more than 5.1 million El Salvador nationals. The database is said to contain full names, dates of birth, telephone numbers, home addresses, and headshot images. The seller did not from where they obtained the database, but this format seems to be specific to either a local government agency or companies specialized in real-world user verification services. (via FalconFeeds)
General tech and privacy
SUSE goes private: SUSE, the company behind the OpenSUSE Linux distro, has announced plans to delist itself from the Frankfurt stock exchange and go private.
Android getting emergency SOS feature: Google is testing a new Android feature that will let users send SOS messages via a satellite connection in the case of an emergency. The feature was spotted hidden inside the code of Android 14, scheduled for release this month. The new feature is similar to the Emergency SOS via Satellite feature that was added in iOS 14. According to Android OS expert Mishaal Rahman, the feature is not part of the main Android 14 OS and is tagged as demo code.
SanDisk sued for defective SSDs: A group of users is seeking class-action status for a lawsuit filed against SanDisk, claiming the company knowingly sold defective SSDs that lose or self-delete customer data. [Additonal coverage in ArsTechnica]
YouTube children's privacy: An Adalytics report found that advertisers are still tracking viewers of videos made for kids, despite a 2019 promise from YouTube to stop delivering personalized ads on these types of videos. Senators are now seeking a formal inquiry into the company for breaching the US' COPPA laws.
Twitch to enforce bans (finally): Video streaming platform Twitch will finally enforce bans as they should—by preventing a blocked user from viewing a broadcaster's stream. Currently, blocked users can't participate in the chat, but they can still view the stream. [Additional coverage in Mashable]
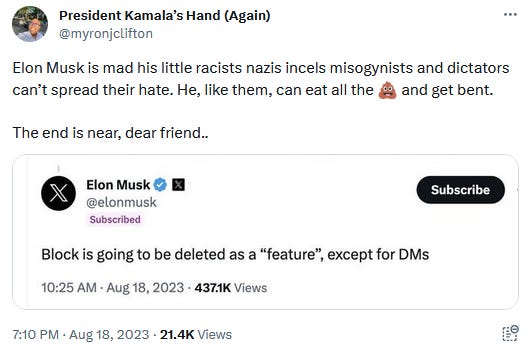
Twitter to remove block feature: Now completely to the other side of the spectrum, Twitter has announced plans to remove the ability for users to block other users, meaning trolls will be able to harass whoever they want. The block removal has not been implemented yet. There was a rumor over the weekend that Twitter risks having its app pulled from both Apple and Google's app stores once it removes the block feature, but that is false. Musk continues to re-shape Twitter into a safe haven for the spread of misinformation, conspiracy theories, violent threats, and state-sponsored propaganda.
Government, politics, and policy
Bolsonaro hacker drama: A Brazilian security researcher says he was asked by former Brazilian President Jair Bolsonaro to hack into the country's electronic voting system. Walter Delgatti Neto claims the entire thing was supposed to be part of a political stunt to show that the results of the 2022 Brazilian Presidential Election could not be trusted. Bolsonaro lost the election, rallied its supporters to attempt a coup, and then fled to the US. His legal team claims Neto is lying and threatened to sue the researcher if he did not provide any evidence for his claims. [Additional coverage in the Associated Press]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Dan Guido, CEO of Trail of Bits, about AI. Dan thinks AI technologies will be a "game changer." But he also thinks the conversation around AI is not very sophisticated just yet.
Cybercrime and threat intel
Africa Cyber Surge II arrests: Interpol and Afripol have detained 14 suspects across six African nations suspected of being members of cybercrime groups. The suspects were involved in cyber extortions, phishing campaigns, BEC operations, and online scams. Officials say the suspects are responsible for financial losses of over $40 million. The arrests were part of what Interpol named Operation Africa Cyber Surge II.
8Base RaaS problems: The 8Base ransomware operation says it lost all the data it stole from victims after the AnonFiles services shuttered operations out of the blue last week.
New npm malware: Twenty-four malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
New PyPI malware: Fortinet has identified eight malicious packages on the PyPI portal.
SAP threat landscape: A RedRays study found that of around 10,000 SAP systems exposed on the internet, 3,094 are vulnerable to one or more vulnerabilities, exposing their organizations to attacks.
Faint crypto-scammer: Blockchain security firm CertiK says that a group of Canada-based scammers is responsible for stealing millions of dollars in recent years. The group's members operate by hacking the Discord servers of cryptocurrency communities and posting phishing links to hijack users' wallets. The company claims to have identified the real-world identity of one of the group's members. Going by the pseudonym of Faint, the individual is believed to have stolen more than $1 million worth of assets since late 2022. Faint is the group's second publicly-identified member after another blockchain investigator exposed a hacker named Soup last month.
EVLF unmasked: Security researchers from CyFirma claim that a Syrian national is behind EVLF, a well-known malware coder that has been active on underground hacking forums for more than eight years. He is primarily known for creating and renting the CypherRAT and CraxsRAT malware strains. Of these, researchers say CraxsRAT is the most advanced, coming with both Android and Windows versions.
Malware technical reports
Trash Panda ransomware: Fortinet researchers have spotted a new ransomware strain named Trash Panda.
BlackCat ransomware: Microsoft has a thread on a recent AlphV/BlackCat ransomware campaign. This appears to be the AlphV Sphynx variant.
Abyss ransomware: Security researchers from ShadowStackRE have reverse-engineered the Linux/ESXi encryptor of Abyss (or Abyss Locker). The Abyss RaaS launched earlier this year, in May.
New Cuba group tools: Blackberry's security team has published a report on new malware tools used by the Cuba ransomware group in recent attacks against US organizations in the critical infrastructure sector. These include BUGHATCH, a custom downloader, and BURNTCIGAR, an antimalware killer.
LimeRAT: Some IOCs on LimeRAT, what OALABS describes as a "trash RAT."
NestJS Stealer: ThreatMon has published a report on the new NestJS infostealer.
ObserverStealer: Antiy researchers took a look at ObserverStealer, a new infostealer spotted in the wild.
PerlJam: Security researchers have published a proof-of-concept Linux virus written in Perl.
dotRunpeX: Check Point has an update on the operations of a new loader named dotRunpeX, which the company first spotted back in March.
Malvertisers update: Malwarebytes has a short report on the various cloaking techniques that search engine malvertisers have recently started using to avoid detection and analysis by security researchers.
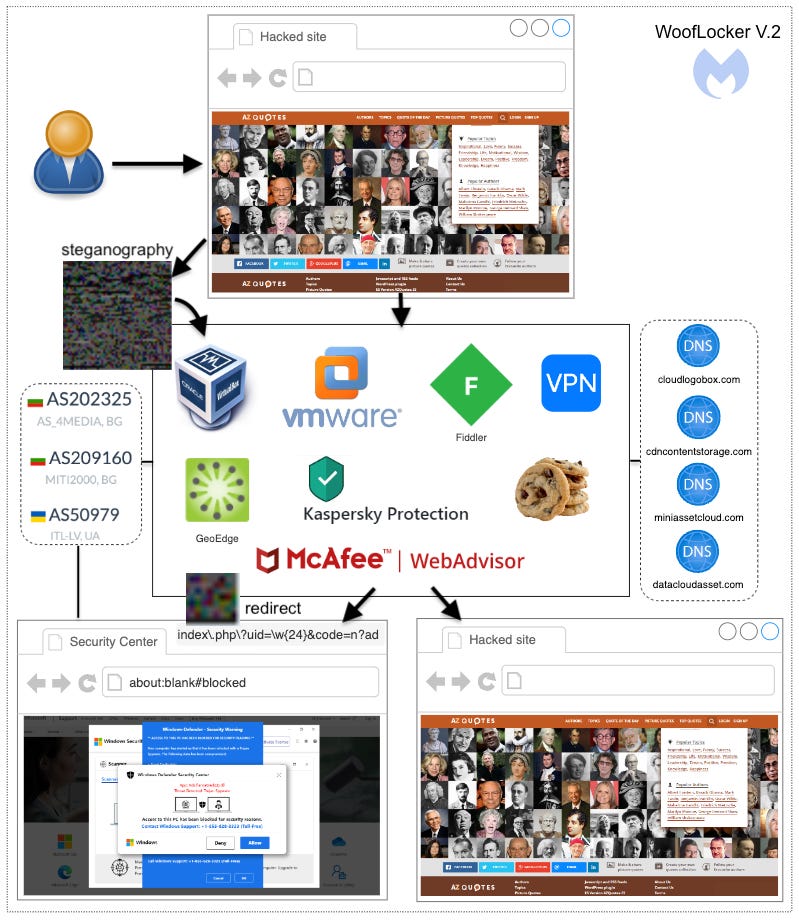
WoofLocker: Malwarebytes has an update on WoofLocker, a traffic-redirection scheme that has been running strong since 2017. Back in 2020, WoofLocker was redirecting users to browser lockers. Now, it was redirecting users to tech support scams managed through call centers in South East Asia.
Sponsor Section
Trail of Bits co-founder and CEO Dan Guido was asked to provide feedback on the effects of AI on modern technology at a meeting of the Commodity Futures Trading Commission's Technology Advisory Committee (TAC) on July 18. His comments are summarized in the company's blog here and are available in full in the video below.
APTs and cyber-espionage
HiatusRAT: Lumen's Black Lotus Labs says that a covert cyber-espionage operation that it's been tracking since March this year has changed its objectives, moving away from Latin America and European organizations to performing reconnaissance against Taiwan-based organizations and a US military procurement system. The group doesn't have an official name, but it's known for operating the HiatusRAT. It's a stealthy backdoor that's installed on business-grade edge routers, where it can passively intercept internet traffic.
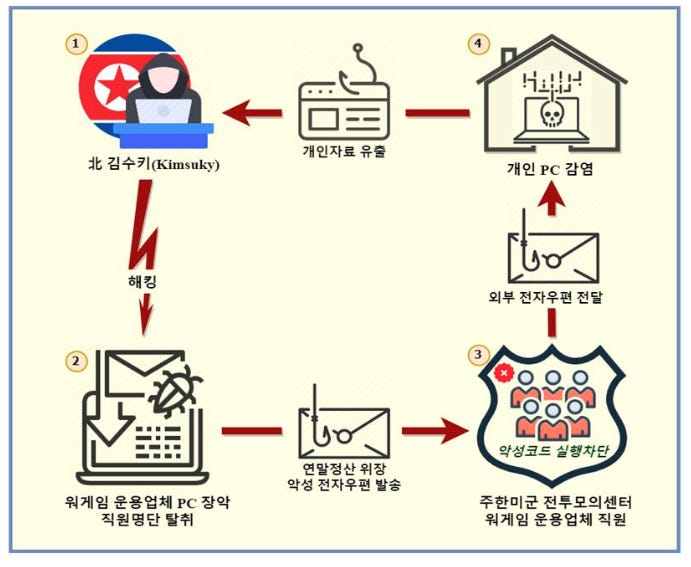
Kimsuky: North Korean hacking group Kimsuky has compromised the email accounts of individuals participating in a joint US-South Korea military exercise set to take place this week. Officials say Kimsuky operators posed as DOD personnel in emails sent to contractors supporting the South Korean military. In a press conference, South Korean police said some attacks were successful but that hackers didn't gain access to any classified information. [Additional coverage in the Korean Broadcasting System/English coverage in Reuters]
Vulnerabilities, security research, and bug bounty
WinRAR vulnerability: RARLAB has published a security update for its WinRAR compression utility to fix a vulnerability that could be used to run malicious code on user devices. Researchers say the vulnerability can be triggered when performing mundane tasks like unzipping a RAR file. The vulnerability resided in WinRAR's code responsible for the RAR4 recovery volumes process.
Atlassian security update: Atlassian has released its monthly security updates for the month of August. This month, the company has patched just one vulnerability.
Juniper security update: US networking equipment vendor Juniper has released an out-of-band security update to patch four vulnerabilities. Juniper says the four bugs can be combined to allow threat actors to run malicious code and take over its devices without needing to authenticate. Vulnerable products include the company's SRX firewalls, and EX network switches.
TSSHOCK vulnerability: At the Black Hat security conference, security researchers from Verichain disclosed three vulnerabilities in TSS, a cryptographic scheme implemented by multi-party crypto-wallets (MPCs). Named TSSHOCK, the vulnerabilities exploit some MPC wallet implementations of the threshold-ECDSA algorithm. Exploiting TSSHOCK can allow threat actors to steal cryptocurrency from individual users or major institutions while leaving no trace of the attack on the client side. Major companies like Binance, ZenGo, Multichain, THORChain, and ING Bank use vulnerable tECDSA software implementations. TSSHOCK is the second major MPC wallet vulnerability disclosed this month after BitForge.
SAMLjacking: Researchers from Push Security have published details about a new cloud/SaaS exploitation technique named SAMLjacking. The technique involves an attacker using SAML SSO configuration settings for a SaaS tenant they control in order to redirect users to a malicious link of their choosing during the authentication process. The technique can be used for phishing attacks.
Infosec industry
Arm copyright claim: Arm's legal team is trying to take down a domain used to promote a book about reverse-engineering Arm code.
New tool—TTPForge: Facebook's security team has open-sourced a tool named TTPForge, a framework to provide an interface to execute TTPs across various targets and mediums.
New tool—Kunai: Luxembourg-based security firm RawSec has open-sourced Kunai, a new threat-hunting framework for Linux systems. The company describes its new project as "a Sysmon equivalent for Linux."
New tool—LOFLCAB: Security researcher Arris Huijgen has launched a new project named LOFLCAB (Living off the Foreign Land Cmdlets and Binaries). The project aims to document cmdlet, binary, script, and WMI classes that can be used for Living Off the Foreign Land techniques—where local files can be abused to perform attacks on remote systems. The project is similar to other initiatives that track benign binaries that can be abused for attacks on Windows (LOLBAS and LOLDrivers), Linux (GTFOBins), and macOS (LOOBins).
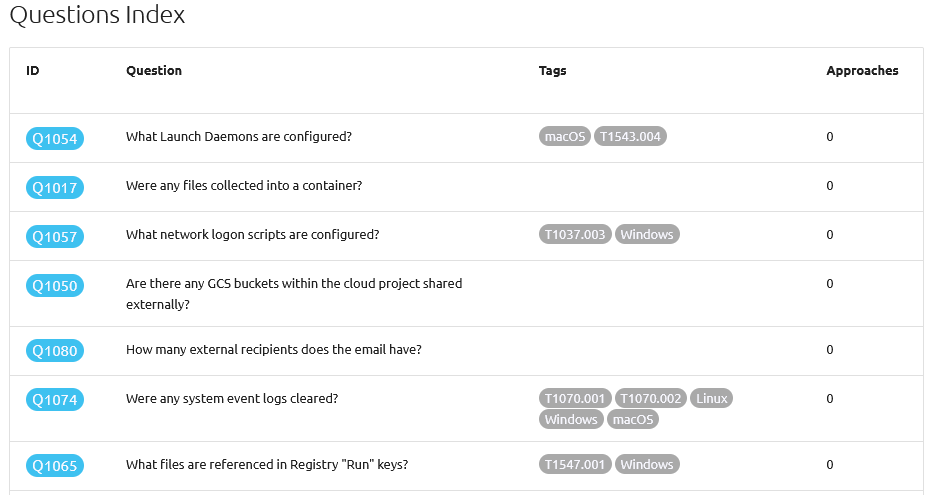
New tool—DFIQ: Google's security team has put together a new project named DFIQ, a collection of questions IR teams should be asking during an incident response engagement.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at why 'juice jacking' is a forever fear even though it's not a real-world threat.




