Risky Biz News: US sanctions Russian woman for laundering money for Ryuk gang, Russian elites
In other news: Apple warns Armenians of state-sponsored attacks; Okta hackers pivoted to five customer networks; and Oracle makes MFA mandatory for cloud tenants.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US Treasury has sanctioned a Russian businesswoman named Ekaterina Zhdanova for helping Russian oligarchs and cybercrime gangs evade sanctions and launder stolen cryptocurrency.
Officials say Zhdanova worked as an intermediary in order to obfuscate the real nature of various illegal transactions.
She disguised operations using traditional businesses operating overseas but also used accounts at cryptocurrency platforms that did not enforce anti-money laundering (AML/CFT) controls.
Officials say Zhdanova operated a luxury watch company with offices around the world in order to maintain access to the global financial system. She was also a customer of Garantex, a Russian cryptocurrency exchange the Treasury sanctioned in April 2022 for laundering more than $100 million in cybercrime proceeds.
According to US officials, Zhdanova was involved in laundering more than $105 million for her customers.
She allegedly helped Russian oligarchs evade sanctions imposed shortly after Russia's invasion of Ukraine.
Zhadonva allegedly helped one client move $2.3 million to Western Europe in the form of real estate purchases and investment accounts and helped another customer move $100 million from Russia to the United Arab Emirates.
Officials also believe Zhadonva is running a scheme to help Russian oligarchs obtain tax residency in the UAE and conceal their identities.
But before the war began and Zhadonva's services would be in high demand with Russian elites, officials say she worked with cybercrime groups, with one customer being one of the affiliates of the Ryuk ransomware gang, for whom she laundered more than $2.3 million in victim payments.
An article in Russian media claims Zhadonva is a former business partner of Irina Shoigu, the wife of Sergei Shoigu, Russia's Defense Minister, which may explain her connections to Russia's oligarch scene.
Zhadonva was also interviewed by one of Russia's social life magazines, where she claimed to have "conquered Moscow" after growing up in Altai, a region in Southern Siberia.
Per the US officials, Zhadonva is most likely still in Moscow. The Treasury's sanctions division has sanctioned three of Zhadonva's blockchain addresses and added her name to the OFAC list.

Breaches, hacks, and security incidents
Okta hack update: Okta has finished its investigation into the September hack of its customer support system, and the company says the intruders gained access to the data of 134 customers, representing less than 1% of its total customer base. Of all these, the hackers pivoted and accessed the networks of only five Okta customers. Three of the five customers are already known after publicly disclosing their breaches and include BeyondTrust, Cloudflare, and 1Password. Okta also blamed the hack on an employee who used a personal Google account on a work laptop. The company says the employee accidentally synced their work credentials to the personal account from where the Okta work credentials were later stolen.
Mr. Cooper cyberattack: Mortgage and lending company Mr. Cooper has shut down its IT systems in the aftermath of a cyberattack. The incident took place on October 31 and has caused a days-long outage for the company, including for its public website and payment systems. The company is the US' leading lending service.
Ace Hardware cyberattack: Almost 200 servers and 1,000 systems have been impacted by a cyberattack at Ace Hardware, one of the US' largest hardware store chains. The incident took place on October 30 and has impacted the company's ability to pick up new customer orders. Other impacted systems include warehouse management systems, reward points program, tech support call center, and the company's mobile assistant. Despite the attack, the company's 5,700 stores have remained open, although with reduced activity. [Additional coverage in BleepingComputer]
General tech and privacy
Drupal 9 EoL: Version 9 of the Drupal CMS has reached End-of-Life status on November 1, 2023.
Mandatory MFA on Oracle Cloud: Oracle has enabled multi-factor authentication by default for all its Oracle Cloud customers. The policy has been enforced for all new cloud tenants and retroactively applied to all existing customers. Oracle's move comes after Amazon also made MFA mandatory for new AWS root accounts.
Google abandons Web DRM plan: Google has abandoned its plan to develop the Web Environment Integrity API, a system that many experts believe would have created a DRM for the entire web and allowed websites to block anyone from modifying their code when rendered in a browser.
Google joins eIDAS protest: Google has joined the ranks of more than 300 companies, cybersecurity, and privacy experts that have called on EU officials to revise its upcoming eIDAS (Electronic Identification, Authentication and Trust Services) regulation. Experts have called attention to a new article added to the eIDAS regulation that will mandate web browsers to automatically trust certificates issued by EU states. Experts say the article was added to eIDAS behind a closed-door meeting and without any public review. The new requirement will allow member states to easily intercept web traffic.
VPN security audit labels: Google has started showing a special label on the Play Store pages of VPN apps that have conducted a security audit of their code. The new label reads "Independent security review" and is listed in an app's Data Safety section. Eight VPN providers have already received the label, but any VPN app maker can obtain it by submitting itself to a security review through the Mobile App Security Assessment program.

Government, politics, and policy
Domestic tech abuse bill reintroduced: US senators reintroduced a new version of the "Tech Safety for Victims of Domestic Violence, Dating Violence, Sexual Assault and Stalking Act." The bill aims to help prevent domestic abusers from using technology to stalk, harass, or control survivors. A first version was introduced last December, but the bill died in the Senate Judiciary Committee. The new bill would fund 15 clinics across the US to support victims of tech-enabled abuse and fund educational programs to train individuals to help victims.
Apple warns Armenians about state-sponsored attacks: Apple has sent private notifications to Armenians warning of state-backed hacking activity targeting their devices. This marks the fifth wave of state-backed notifications that Apple has sent to Armenian users. The first wave was sent out in 2020 during the second Nagorno-Karabakh war. The last was sent in March this year during the latest round of fighting. In past cases, security experts found traces of the Pegasus spyware on the infected devices. [Additional coverage in ArmenPress]
Greece's Predatorgate scandal: A Mediapart investigation found that the Predator spyware was deployed to the devices of Greek politicians after victims received SMS messages from a former secretary of Kyriakos Mitsotakis, the country's current prime minister. Grigoris Dimitriadis, the former secretary, denies any involvement.
Moldova's report on Russia's hybrid warfare: Moldova's intelligence agency has published a 32-page report describing the "hybrid warfare" Russia has been using in attempts to destabilize and overthrow its government. The report is in Romanian and covers everything from hack-and-leaks to disinformation campaigns and from bribery of state officials to actual paramilitary coup attempts.
NCSC post-quantum guide: The UK's NCSC agency has published guidance to help organizations prepare for the migration to post-quantum cryptography (PQC).
ACSC translates cybersecurity guides: The Australian Cyber Security Centre has translated its five basic cybersecurity guides into 27 languages.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Huxley Barbee, Security Evangelist at runZero, about finding the unknown unknowns and what is a security evangelist.
Cybercrime and threat intel
Phisher detained in Indonesia: Indonesian authorities have detained a 36-year-old man for developing and selling access to a phishing kit. The suspect was detained following a joint investigation between US, UK, Australian, Canadian, and Indonesian authorities. He faces up to 12 years in prison. The suspect is the second Indonesian arrested this year for developing and selling a phishing kit. Authorities previously arrested the owner of the 16Shop phishing kit in August. [Additional coverage in AccountingWeb]
Phisher detained in Belgium: Belgian prosecutors are asking for two years in prison and a €5,000/day fine for an 18-year-old suspect who is refusing to provide passwords to his phone, computer, and servers. Officials arrested the teen in October on suspicion of being part of a phishing gang. The prosecution says the teen is ignoring a judge's order to release the passwords to investigators. The teen's camp argues that the passwords are part of his right to remain silent. [Additional coverage in NieuwsBlad]
Umbreon sentenced: Dutch authorities have sentenced a 21-year-old man from Zandvoort to four years in prison on hacking-related offenses. Named Pepijn Van der Stap, the suspect was known on hacking forums as Umbreon. Officials say Van der Stap was the leader of a trio of hackers that broke into corporate networks, stole sensitive data, and extorted the companies by threatening to publish their data. The group asked between €100,000 and €700,000 from each victim, and officials believe Van der Stap earned more than €2.5 million through extortions or by selling the hacked data. Van der Stap also worked as a security researcher for Hadrian Security and was a volunteer for the Dutch Institute for Vulnerability Disclosure, a Dutch cybersecurity collaboration group. [h/t PogoWasRight]
JFK hackers charged: The US Department of Justice has charged two Russian nationals with hacking the taxi dispatch system at the JFK airport in New York. The duo worked with two Americans who helped promote a scheme where drivers could pay a $10 fee and skip the airport's taxi waiting line. The two Americans were charged and arrested in December 2022, and both pleaded guilty last month.
BEC recovery: The DOJ recovered $2.4 million stolen from a company in April 2021 following a BEC scam.
MFA smishing alert: The Romanian cybersecurity agency has detected a smishing campaign that targets Romanian citizens with attempts to intercept 2FA/MFA codes. The attackers claim their 2FA/MFA code was sent to the victim by accident and ask the user to send over the code, leading to their account getting compromised.
New npm malware: Six malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
More npm malware: DevSecOps company Phylum has discovered 48 JavaScript packages passing as legitimate libraries on the official npm portal. Researchers say the malicious libraries are designed to initiate a reverse shell when the package is installed. Although the first wave of packages was removed, the attack is still ongoing.
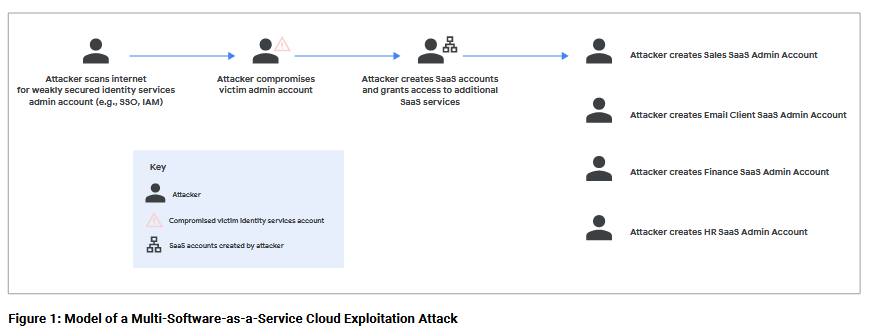
Google Cloud Threat Horizons Report #8: In the eighth edition of its threat and trends report [PDF], the Google Cloud security team highlighted a tactic it calls Multi-Software-as-a-Service Cloud Exploitation, where threat actors take credentials from one compromised cloud system to expand to multiple SaaS platforms an organization might be using.
RTF global ransomware: The Ransomware Task Force has published its yearly report on ransomware attacks for 2022. Last year, the organization says it tracked 2,600 ransomware incidents, down from the 3,000 it tracked the year before.
"This finding is consistent with the findings of other research institutions throughout 2022. While it is unlikely that a single force is driving this decline, the Russian invasion of Ukraine, law enforcement action, and continued efforts within the security community have almost certainly been contributing factors in this decline. Yet, early indications are that ransomware incidents in 2023 will reverse this decline."
SWAT USA Drop Service: Infosec reporter Brian Krebs takes a look at SWAT USA Drop Service, an online service used by money laundering gangs to buy expensive products with stolen funds and ship them overseas to be resold and re-monetized by hackers. Krebs got a copy of the site's database after the service was recently hacked. Hooray for hackers! [Additional coverage in KrebsOnSecurity]
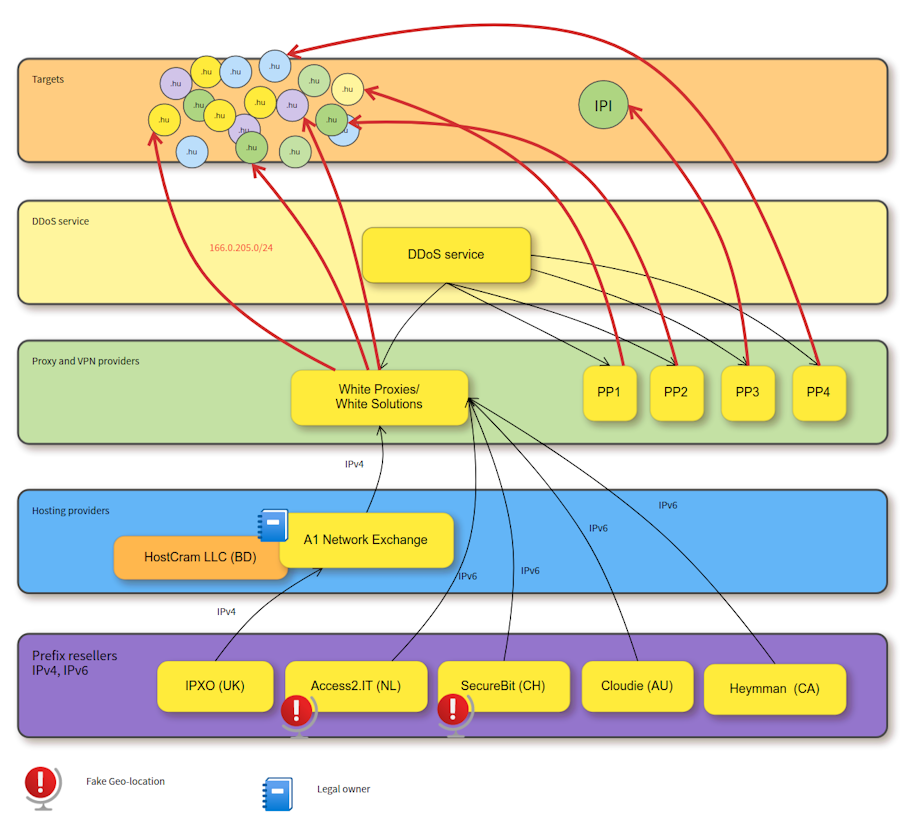
White Proxies: An investigation by the Qurium Media Foundation has found that proxy provider White Proxies (or White Solutions) has provided the server infrastructure used in DDoS attacks against independent news outlets in Hungary. The attacks took place in August and targeted more than 40 Hungarian news outlets that criticized the country's government and the ruling party. The biggest attacks took place in August, shortly after journalists at several outlets exposed government corruption. The International Press Institute says that more than 40 Hungarian independent news outlets faced DDoS attacks since April this year. Shortly after this report, IPI itself was targeted by a DDoS attack.
Malware technical reports
Megazord: Chinese security firm Qihoo 360 analyzes Megazord, a new version of the Akira ransomware. Another report is also available via Rising.
Knight ransomware: Fortinet researchers look at Knight, a ransomware gang that started operations in August this year and has had quite an impact in Italy. The ransomware is a rebrand of the old Cyclops gang.
GhostLocker: Uptycs looks at GhostLocker, a RaaS created by the GhostSec "hacktivist" group.
"By executing the specified C2 hunting query on Shodan, the Uptycs threat intelligence team uncovered additional IP addresses associated with GhostLocker's Affiliate Login panel."
There goes their anonymity, I guess!
Kinsing: AquaSec has spotted the Kinsing crypto-mining botnet exploiting the Looney Tunables vulnerability to elevate privileges on compromised Linux boxes.
BadCandy: Cisco Talos has published a technical analysis of BadCandy, the implant deployed on Cisco IOS XE routers via the two recent zero-days CVE-2023-20198 and CVE-2023-20273. Talos says the malware is now at v3, showing that threat actors are still actively modifying their attacks and malware to maintain access to the compromised boxes. The latest v3 modifications appear to have worked, as the Shadowserver Foundation has stopped detecting infected systems.
Socks5Systemz: A malware strain named Socks5Systemz has infected more than 10,000 Windows systems as part of a proxy rental service. The Socks5Systemz malware is typically installed as a second-stage payload on systems previously infected with the PrivateLoader or Amadey malware. According to security firm BitSight, the botnet has been live since 2016 and appears to be operated out of Russia.
DarkGate: eSentire researchers have spotted a new version of the DarkGate malware loader. Also, see a similar report from Netskope.
AsyncRAT: McAfee looks at a campaign spreading the AsyncRAT using a new infection chain.
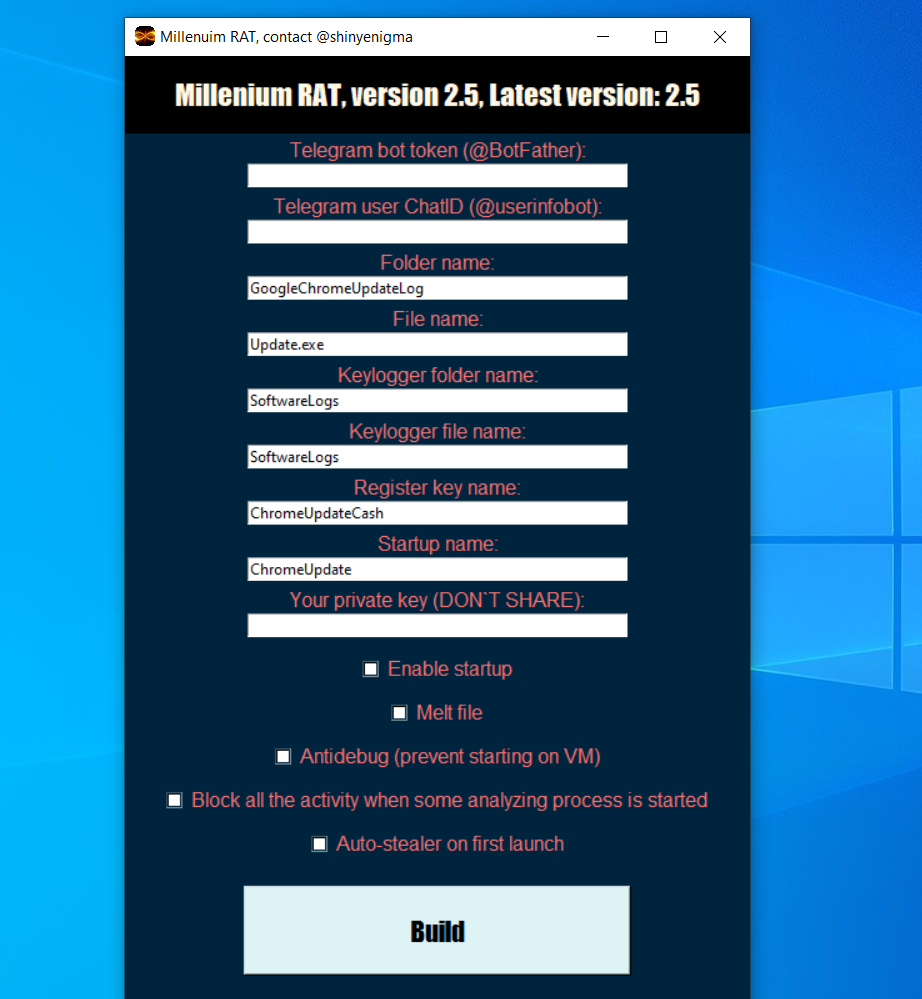
Millenium RAT: CyFirma published a report on Millenium, a Windows remote access trojan derived from the ToxicEye RAT open-source project.
Sponsor Demo
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
APTs and cyber-espionage
Operation Covert Stalker: AhnLab has published a technical report [English] on Operation Covert Stalker, a Kimsuky spear-phishing campaign that lasted for roughly 17 months and targeted people and organizations working in North Korean politics, diplomacy, and security.
APT35 and Emennet Pasargad bounty: The US State Department has put up $10 million rewards for information on two Iranian cyber groups. The first reward is for information on members of APT35, a known cyber-espionage group that has carried out ransomware attacks against US critical infrastructure. The second reward is for Emennet Pasargad, an Iranian cybersecurity company that spread disinformation and tried to influence voters in the 2020 US Presidential Election.


Vulnerabilities, security research, and bug bounty
LLM prompt injection attacks: WithSecure and Nettitude go over various LLM prompt injection attacks that can poison AI models to modify agent output.
TeslaMate exposure: A security researcher has found ~1,000 TeslaMate dashboards exposed on the internet.
Atlassian data-wiping bug mass-exploitation: The Shadowserver Foundation warns that mass internet scans are underway for Atlassian Confluence servers that may be vulnerable to a major data-wiping vulnerability (CVE-2023-22518). The scans began after a public exploit was posted online last week. Atlassian has confirmed the exploit and urged customers once again to apply patches. In a rare statement last week, Atlassian CISO Bala Sathiamurthy urged customers to patch their Confluence servers as soon as possible and avoid potential data loss.
ActiveMQ bug was a zero-day: Security researchers at ArcticWolf and Huntress Labs say that a recently patched Apache ActiveMQ vulnerability had been under attack for more than two weeks before a patch was available. The two companies say they've found attacks against ActiveMQ servers as far back as October 10, long before Apache patched the vulnerability on October 25. Several security firms have seen hacked ActiveMQ servers encrypted with a version of HelloKitty, a ransomware family that was leaked online in October. ArcticWolf says it has also seen some servers encrypted with the TellYouThePass ransomware.
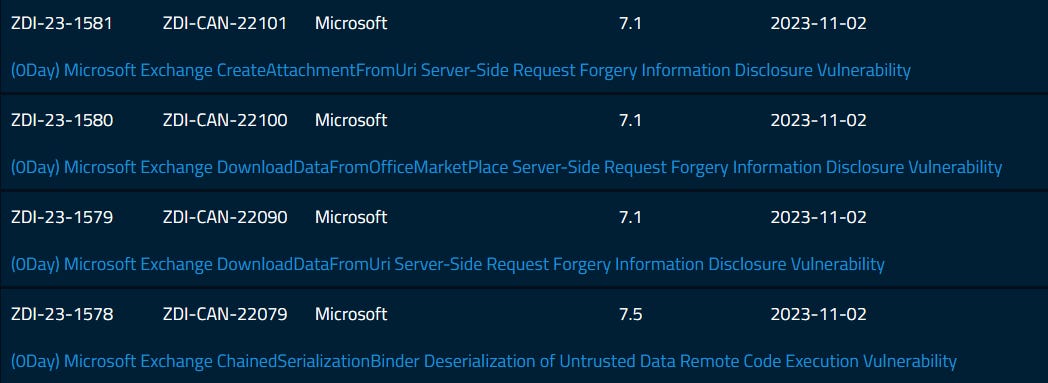
Unpatched Exchange vulnerabilities: ZDI security researcher Piotr Bazydlo says Microsoft has declined to patch four vulnerabilities in its Microsoft Exchange email server. The vulnerabilities include three SSRF issues and one remote code execution bug. Bazydlo says that given the nature of the four security flaws and Microsoft's refusal to release patches, the only mitigation he can recommend is to restrict access to Exchange servers. Microsoft did not elaborate on why it chose not to patch the issues, but ZDI bug reports contain some pretty strict exploitation requirements, such as access to an email account's credentials.
Infosec industry
BlackHatEurope keynote: UK NCSC CTO Ollie Whitehouse and former Uber CISO Joe Sullivan will keynote the Black Hat Europe security conference in December.
New tool—Cuddlephish: Security researcher Forrest Kasler has open-sourced a tool named Cuddlephish that can be used to execute Browser-in-the-Middle phishing attacks.
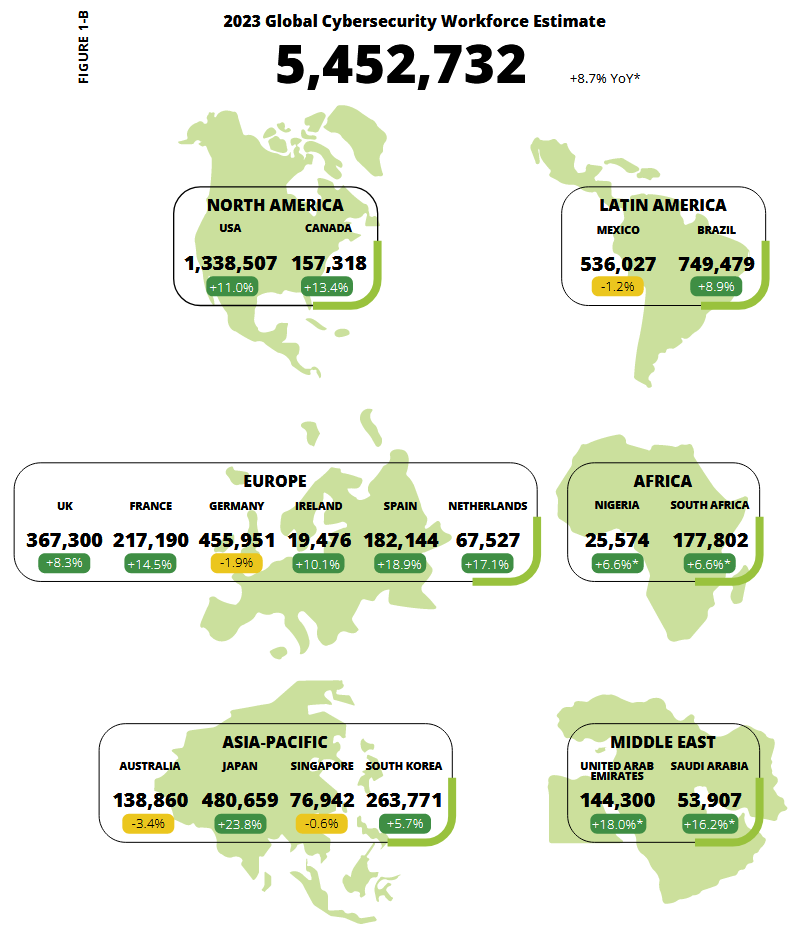
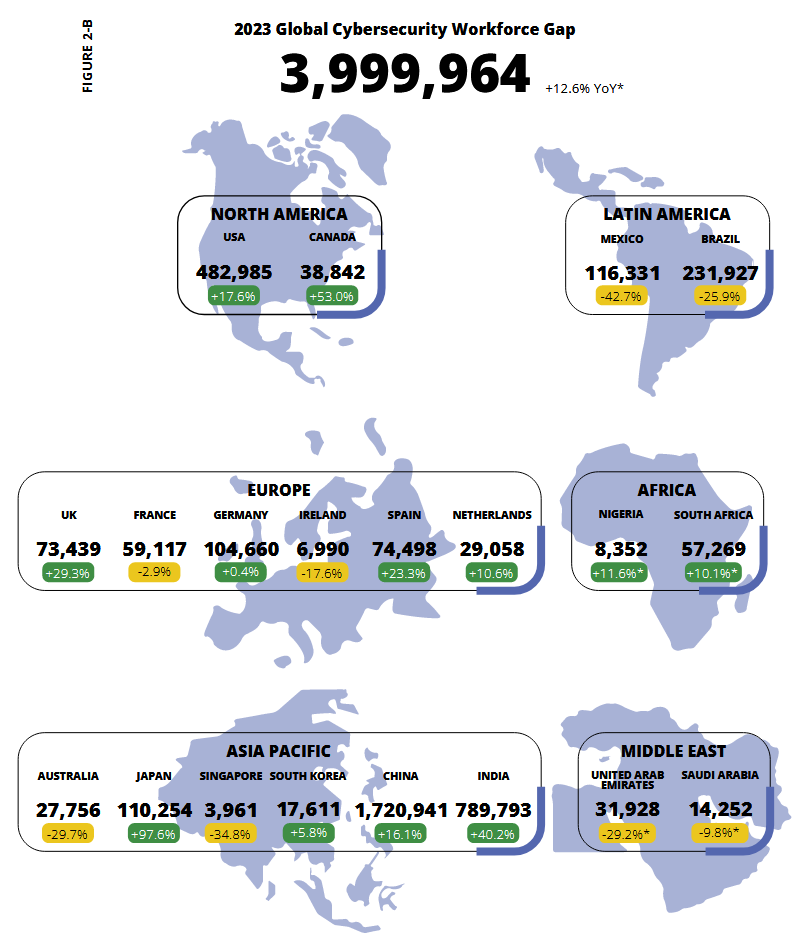
Global cybersecurity workforce: The global cybersecurity workforce is estimated to have reached more than 5.5 million professionals. Even if the number is 9% higher than last year, 4 million experts are still needed worldwide to fill open positions across the industry. Latin America, Australia, and the Middle East have the biggest cybersecurity workforce gaps to fill, according to a study from cybersecurity certification platform ISC2 [PDF]. [Additional coverage in CybersecurityDive]
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what is really at stake when it comes to cyber security.




