Risky Biz News: US and UK dox and sanction 11 more Trickbot/Conti members. Charges included too.
In other news: China bans iPhones for government work; Microsoft explains how it lost its signing key; and Apple patches zero-days used to install NSO Group's Pegasus spyware without user interaction.
This newsletter is brought to you by enterprise browser Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US and UK governments have revealed the real-world identities and imposed sanctions on 11 additional members of the Trickbot/Conti cybercrime operation. The new sanctions come after both governments doxed and sanctioned seven members earlier this year in February.
The new batch includes:
- Andrey Zhuykov - a central actor in the group and a senior administrator. Known by the online monikers "Defender," "Dif," and "Adam."
- Maksim Galochkin - led a group of testers with responsibilities for the development, supervision, and implementation of tests. Known by the online monikers "Bentley," "Volhvb," and "Max17."
- Maksim Rudenskiy - a key member of the Trickbot group and was the team lead for coders. Known by the online monikers "Buza," "Silver," and "Binman,"
- Mikhail Tsarev - a mid-level manager who assisted with the group's finances and overseeing of HR functions. Known by the online monikers "Mango," "Frances," and "Khano."
- Dmitry Putilin - was associated with the purchase of Trickbot infrastructure. Known by the online monikers "Grad" and "Staff."
- Maksim Khaliullin - was an HR manager for the group. He was associated with the purchase of Trickbot infrastructure, including procuring Virtual Private Servers (VPS). Known by the online moniker "Kagas."
- Sergey Loguntsov - was a developer for the group. Known by the online monikers "Begemot," "Begemot_Sun," and "Zulas."
- Alexander Mozhaev - was part of the admin team responsible for general administration duties. Known by the online monikers "Green" and "Rocco."
- Vadym Valiakhmetov - worked as a coder, and his duties included backdoor and loader projects. Known by the online monikers "Weldon," "Mentos," and "Vasm."
- Artem Kurov - worked as a coder with development duties in the Trickbot group. Known by the online moniker "Naned."
- Mikhail Chernov - was part of the internal utilities group. Known by the online monikers "Bullet" and "m2686."
This adds to the February batch of sanctioned Trickbot/Conti members, which includes:
- Vitaly Kovalev - was a senior figure within the Trickbot group. Vitaly Kovalev is also known by the online monikers "Bentley" and "Ben."
- Maksim Mikhailov - involved in development activity for the Trickbot Group. Maksim Mikhailov is also known by the online moniker "Baget."
- Valentin Karyagin - involved in the development of ransomware and other malware projects. Valentin Karyagin is also known by the online moniker "Globus."
- Mikhail Iskritskiy - worked on money laundering and fraud projects for the Trickbot group. Mikhail Iskritskiy is also known by the online moniker "Tropa."
- Dmitry Pleshevskiy - worked on injecting malicious code into websites to steal victims' credentials. Dmitry Pleshevskiy is also known by the online moniker "Iseldor."
- Ivan Vakhromeyev - worked for the Trickbot group as a manager. Ivan Vakhromeyev is also known by the online moniker "Mushroom."
- Valery Sedletski - worked as an administrator for the Trickbot group, including managing servers. Valery Sedletski is also known by the online moniker "Strix."
Back in February, the US Justice Department filed official charges only against Kovalev.
This week, the DOJ charged two more from the February batch (Karyagin and Mikhailov) and seven from the newer batch (Galochkin, Rudenskiy, Tsarev, Zhuykov, Putilin, Loguntsov, and Khaliullin). Charges differ based on their involvement in various attacks against US organizations, and one of the indictments covers the May 2021 attack on Scripps Health, one of the largest healthcare providers in the US.
Also known as Wizard Spider, the Trickbot gang is known for operating the eponymous Trickbot malware botnet. The gang primarily made its money by infecting Windows systems around the world and then renting access to infected hosts to other cybercrime groups.
The group started diversifying in the late 2010s when payments from ransomware attacks skyrocketed and reached tens of millions of US dollars. The group helped deploy the Ryuk ransomware, before they also created their own ransomware strains, first with Diavol and then with the highly successful and effective Conti family.
The UK's NCA says that even if the Conti group disbanded last year, former members have moved on and are now involved in other ransomware operations, continuing to orchestrate new attacks.
All 18 sanctioned individuals are Russian nationals, and both US and UK officials said some of the group's key members "highly likely maintain links to the Russian Intelligence Services from whom they have likely received tasking," which explains why the Conti crew was one of the first cybercrime groups to come out and support Russia's invasion of Ukraine.
The sanctions imposed in February and this week mean the 18 Trickbot/Conti members are now subject to travel bans and asset freezes.
Past sanctions have proved successful in hampering some ransomware operations, with victims being wary of paying ransoms to any ransomware group that may be associated with any of the sanctioned individuals.
Breaches, hacks, and security incidents
LastPass hack thefts: Multiple security researchers believe the hackers who breached LastPass last year are now cracking stolen password vaults, recovering crypto-wallet seed phrases, and stealing money from crypt accounts. The hackers are estimated to have stolen more than $35 million worth of crypto assets from more than 150 victims. One of the largest identified hacks is a multi-million dollar heist from an employee of blockchain tracking company Chainalysis. [Additional coverage in KrebsOnSecurity]
See Tickets skimming incident: The See Tickets event ticketing company says that more than 320,000 customers might have had card data stolen after its website was infected with an e-skimmer.
Seville ransomware attack: The city of Seville in Spain has shut down its IT network after getting hit by a ransomware attack. City officials said they don't plan to pay a $1.5 million ransom requested by the attackers. Unconfirmed rumors claim the attack was carried out using the LockBit ransomware. Seville is Spain's fourth largest city by population. [Additional coverage in The Record]
General tech and privacy
Cars are a privacy nightmare: A new Mozilla study has found that major car brands violate user privacy by collecting vast amounts of information on their drivers. The study found that 23 of 25 car brands collect data and sell it to third parties without giving users a way to opt-out. Only Renault and Dacia allowed users to opt out, while Tesla and Nissan were found to have the most egregious privacy. Mozilla says that of all the products they analyzed, modern cars had the worst privacy practices they ever reviewed.
Emsisoft critical update: Antivirus maker Emsisoft has released an urgent out-of-band security update asking customers to reboot all their devices after GlobalSign flubbed the company's certificate renewal process.
"Yesterday, GlobalSign reached out to us letting us know that they made a mistake with our certificate: namely, they entered our business number incorrectly. This means they must revoke the certificate on September 8th and re-issue a new one with the correct business number."
Adobe Creative Cloud Sync EoL: Adobe will discontinue its Creative Cloud Synced service on October 1. Customers won't be able to access their files after that date.
Android 14 security: The upcoming Android 14 operating system will block all changes to system certificates, even changes made using the root user. This happens because Google has moved the management of a device's certificate root store into a separate component that can be updated via the Google Play Store. The downside is that this new mechanism prevents reverse engineers from adding certificates to their own devices for security and research work that requires intercepting HTTPS traffic.
"In the meantime, if you want to debug your own HTTPS traffic, you'll need to stick to Android 13."
Chrome to get a new UI: On its 15th anniversary, Google Chrome is slated to get a new user interface.

Government, politics, and policy
China bans iPhones for govt employees: China has banned the use of iPhones and other foreign-branded devices by government workers. Officials cited the need to secure government environments against foreign espionage. Russia also banned government workers from using iPhones in June after claiming the NSA worked with Apple to spy on devices in Russia. [Additional coverage in the Wall Street Journal/non-paywall]
China weaponized its vulnerability disclosure program: An Atlantic Council report argues that Beijing has used a law passed in 2021 that mandates companies disclose security flaws to the government in two days to gain access to vulnerabilities its hackers can use in the wild.
"This report demonstrates that the mandated vulnerability and threat-intelligence sharing from the MIIT's new database to the CNCERT/CC's CNVD facilitates access to reporting by a regional MSS office, a known PLA contractor, and a university research center with ties to PLA hacking campaigns and which conducts offensive and defense research. These organizations with ties to offensive hacking activities would be negligent if they did not utilize their access to CNVD vulnerability reports to equip their operators. The observable increase in the number of zero-days used by PRC hacking teams, as indicated by the 2022 Microsoft' Digital Defense Report,' suggests that these organizations' access is resulting in vulnerabilities being used by offensive teams."
FCC IoT security project: FCC commissioner Nathan Simington held an AMA on HackerNews about the agency's recent IoT labeling scheme and encouraged the site's highly technical userbase to leave comments on the standard and help improve its usability.
Verizon fined for lying about cybersecurity: A Verizon division was fined $4 million for lying to the US government that one of its products met cybersecurity standards. The DOJ charged Verizon Business Network Services for claiming that its managed gateway device MTIPS met government cybersecurity standards in order to secure contracts with the US government between 2017 and 2021. The DOJ says that after learning of the issues, Verizon took "substantial remedial measures."
Polish Senate investigation into Pegasus scandal: The Polish Senate has recommended that the country's Prosecutor's Office launch an inquiry into five current and former government officials involved in acquiring and using the Pegasus spyware. The spyware was used by the previous Polish government to spy on opposition members and prosecutors investigating acts of corruption. The Senate Commission said the use of the Pegasus spyware was unconstitutional and made the country's 2019 election unfair. The Commission likened the government's actions to those of Russian hackers spying on US and EU elections.
ICC cyber war investigations: The lead prosecutor of the International Criminal Court says the organization plans to investigate cyber operations that violate human rights and can be interpreted as war crimes. The official didn't mention Russia's invasion of Ukraine. [Additional coverage in Wired]
Internet censorship in Russia: Russia's telecommunications watchdog is blocking access to more than 885,000 websites, up 85% from the same period last year, according to Kommersant.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Mike Fey, CEO and co-founder of Island, about the idea of an "enterprise browser." Tom and Mike discuss what an enterprise browser actually is, what problems it solves, and why browsers focused on business requirements haven't been a product category until now.
Cybercrime and threat intel
Russian businessman sentenced for hacking: A 43-year-old Russian national was sentenced to nine years in prison. Vladislav Klyushin was found guilty of hacking into companies and using stolen documents to trade shares using non-public information. Officials say Klyushin and four other accomplices made $93 million from illegal stock trades. Klyushin was arrested in March 2021 in Sion, Switzerland. He is the owner of M-13, a Russian IT firm that contracts for the Russian government. All of Klyushin's accomplices are still at large, and one of them is Ivan Ermakov, a former officer in Russia's GRU military intelligence agency. Ermakov is on the FBI's "Cyber most wanted" list and has already been charged in the USA with offenses related to interference in the 2016 US Presidential Election.
Raspberry Pi ATM hacks: Three suspects were detained in a Texas town on charges of hacking ATM devices. Officials in Lubbock say the trio used a Raspberry Pi board to deactivate an ATM's security features and remove the cash drawer. Several Raspberry Pi devices were found in the suspects' hotel rooms. [Additional coverage in Tom's Hardware]
LEO hacks: Threat actors are intentionally targeting and breaching law enforcement email accounts in order to abuse them and file data requests with online tech companies. [Additional coverage in 404 Media]
Knight ransomware: Security firm Group-IB claims to have gained access to the backend panel of the Knight RaaS (recently rebranded from Cyclops).
Clop gang: FalconFeeds has a deep look at how the Clop gang has been operating in recent weeks.
GDPR gangs: KELA looks at AlphV, NoEscape, and Cloak, three ransomware and extortion groups that use the threat of GDPR fines to threaten and coerce companies to pay their ransom demands.
Google Looker Studio abuse: Check Point says it is seeing phishing and BEC groups abuse the Google Looker Studio service to host phishing infrastructure.
Crypto-phishing campaign: A threat actor is targeting the customers of the bankrupt Voyager and Celsius crypto platforms with phishing emails touting full asset recovery. The phishing pages use malicious redirects to steal assets and harvest credentials from local crypto wallets by spoofing legitimate domains. Stay safe out there, crypto-bros! I know you're not the smartest bunch around.
W3LL: A threat actor named W3LL has made more than $500,000 over the past 10 months from selling a phishing kit that can bypass MFA and hijack Microsoft 365 accounts. Named the W3LL Panel, the phishing kit has been linked to more than 8,000 hacked Microsoft accounts. Security firm Group-IB says the W3LL Panel is one of the 3,800 hacking tools sold on the W3LL Store, together with vulnerability scanners, email senders, and tools to perform BEC attacks.
MENA scam group: Group-IB researchers have discovered a cybercrime group operating 900 web pages hosting online scams and primarily targeting users in the MENA region. The group started operations in June of last year and is believed to have made at least $280,000 from their operations. The vast majority of scam pages focus on investment scams, posing as financial or insurance companies.
AdSense fraud campaign: More than 24,000 websites have been hacked as part of a campaign to redirect legitimate traffic to shady Q&A sites. The campaign has been going on since September of last year when it was present on only 2,500 hacked sites. The group behind the hacks is focused on generating revenue using Google ads displayed on the Q&A sites.
Citrix exploitation: CISA has updated an advisory with new TTPs and IOCs seen in attacks on Citrix servers using CVE-2023-3519.
Tsunami DDoS attacks rise: Check Point is seeing a rise in large-scale DDoS attacks being conducted using a new attack method named Tsunami. The method is hard to detect and mitigate without blocking legitimate traffic, and while used in the past decade, its usage exploded with the rise of hacktivist groups that rose after Russia's invasion of Ukraine. The Check Point report echoes similar findings from the Dutch National Internet Providers Management Organization (NBIP) and US-based DDoS mitigation provider Radware. On the other hand, Nexusguard also reports a rise in bit-and-piece, or carpet-bombing, attacks.
Rayobyte's role in DDoS attacks: An investigation by the Qurium Media Foundation has found that the infrastructure of US-based proxy provider Rayobyte is being used to carry out DDoS attacks against independent news outlets in oppressive countries. Qurium says Rayobyte servers have been used to attack news agencies in Kosovo, Kyrgyzstan, Nigeria, Somalia, Turkmenistan, and the Philippines. The attacks took place shortly after those agencies exposed government corruption. Qurium says Rayobyte is only one of the many similar proxy and VPN providers that host DDoS attack infrastructure.
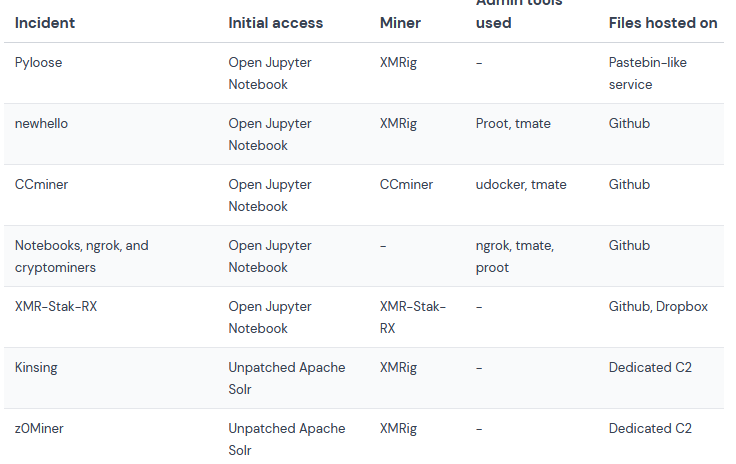
Crypto-miners in the cloud: Cloud security firm Wiz has published a summary of all the cryptomining payloads it spotted in the wild over the past three months.
Malware technical reports
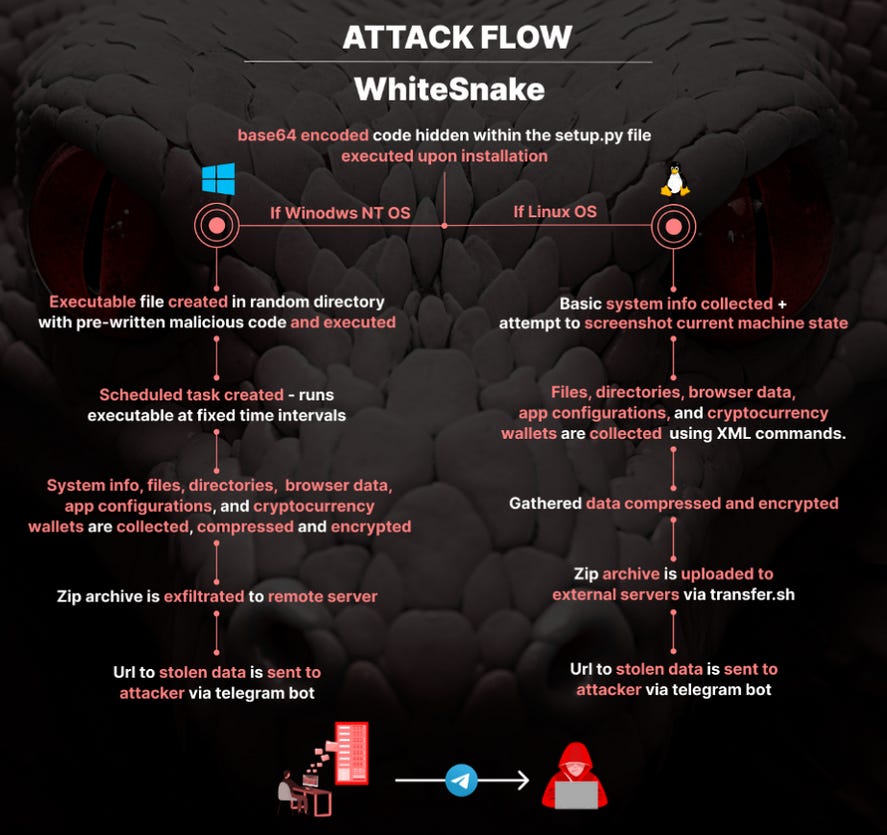
PYTA31's PyPI campaign still going: A threat actor tracked as PYTA31 is uploading malicious libraries to the PyPI portal infected with the WhiteSnake malware. The group has continued its activities unabated even after its operations were exposed in April this year. The malware has been on sale on underground hacking forums since early 2022 and has both Windows and Linux versions.
Pandora malware impacts Android TVs: A new malware strain named Pandora has been spotted infecting Tanix Android-based TV set-top boxes. The malware contains backdoor functionality and the ability to carry out DDoS attacks using the infected devices. Security firm Dr.Web says the malware is a new version of the old Pandora backdoor from 2014 combined with the Mirai DDoS malware. Devices are typically infected either through tainted firmware updates or via malicious apps. The malicious apps appear to target Spanish-speaking users.
Crypto-mining campaign: A threat actor is packing cryptominers in legitimate graphic design software. The campaign has been live since December 2021, per Cisco Talos, and appears to target French-speaking audiences. The final payloads are typically the PhoenixMiner and lolMiner open-source miners—configured to mine Monero for the attacker's account.
RegStealer: Broadcom's Symantec division has spotted a new malware strain named RegStealer. The malware is written in Python, operates as an infostealer, and has been seen in campaigns targeting South Korea.
Atomic Stealer: Malwarebytes is seeing malvertising campaigns deliver the Atomic Stealer malware to macOS systems.
Agent Tesla: Fortinet's security team has a look at an Agent Tesla campaign.
Raspberry Robin: Huntress takes a look at a recent campaign involving the Raspberry Robin USB worm.
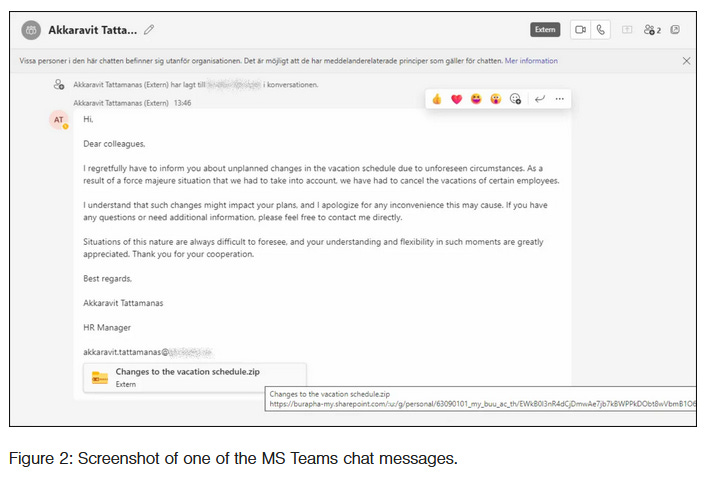
DarkGate: A threat actor is contacting employees via Microsoft Teams messages and delivering HR-themed files containing the DarkGate malware. The campaign has been going on since late August. It is a change in DarkGate operations that previously used to rely on email spam campaigns to infect their victims. The DarkGate malware operates as a loader, similar to Emotet and Qakbot, and allows other threat actors to deploy additional payloads on infected hosts and networks.
Sponsor Section
Island CEO Mike Fey and CSO Brian Kenyon talk about how the Island enterprise browser came to be and its early days.
APTs and cyber-espionage
APT attacks on Fortinet and Zoho systems: CISA, the FBI, and CNMF say that multiple nation-state groups are exploiting recent vulnerabilities in Fortinet (CVE-2022-42475) and Zoho ManageEngine (CVE-2022-47966) devices to gain access to corporate and government networks. The agencies says the groups deploy malware to establish persistence and then move laterally inside networks. The attackers often reactivate disabled admin accounts to move through networks. Officials say at least one company in the aeronautical sector has been compromised.
APT28: Zscaler looks at a campaign it calls Steal-It that the company believes may be the work of APT28 based on some similarities to a previous CERT-UA report.
Gamaredon infrastructure: SilentPush has published details about a fast flux network used by the Russian Gamaredon cyber-espionage group.
BlueShell: AhnLab takes a look at BlueShell, a Go-based backdoor used in attacks targeting South Korea and Thailand. Researchers say this is an APT attack but did not attribute it to any group.
ScarCruft's RedEyes: The same AhnLab also takes a look at RedEyes, a backdoor operated by North Korean hacking group ScarCruft.
ScarCruft's Chinotto backdoor: Chinese security firm Anheng analyzed the ScarCruft group's Chinotto backdoor and the recent spear-phishing campaigns that used it.
North Korean hackers on Mastodon: Google has spotted another online persona operated by North Korean hackers used to target and trick security researchers into infecting themselves with malware. For the first time, the fake persona also operated accounts on Wire and Mastodon.
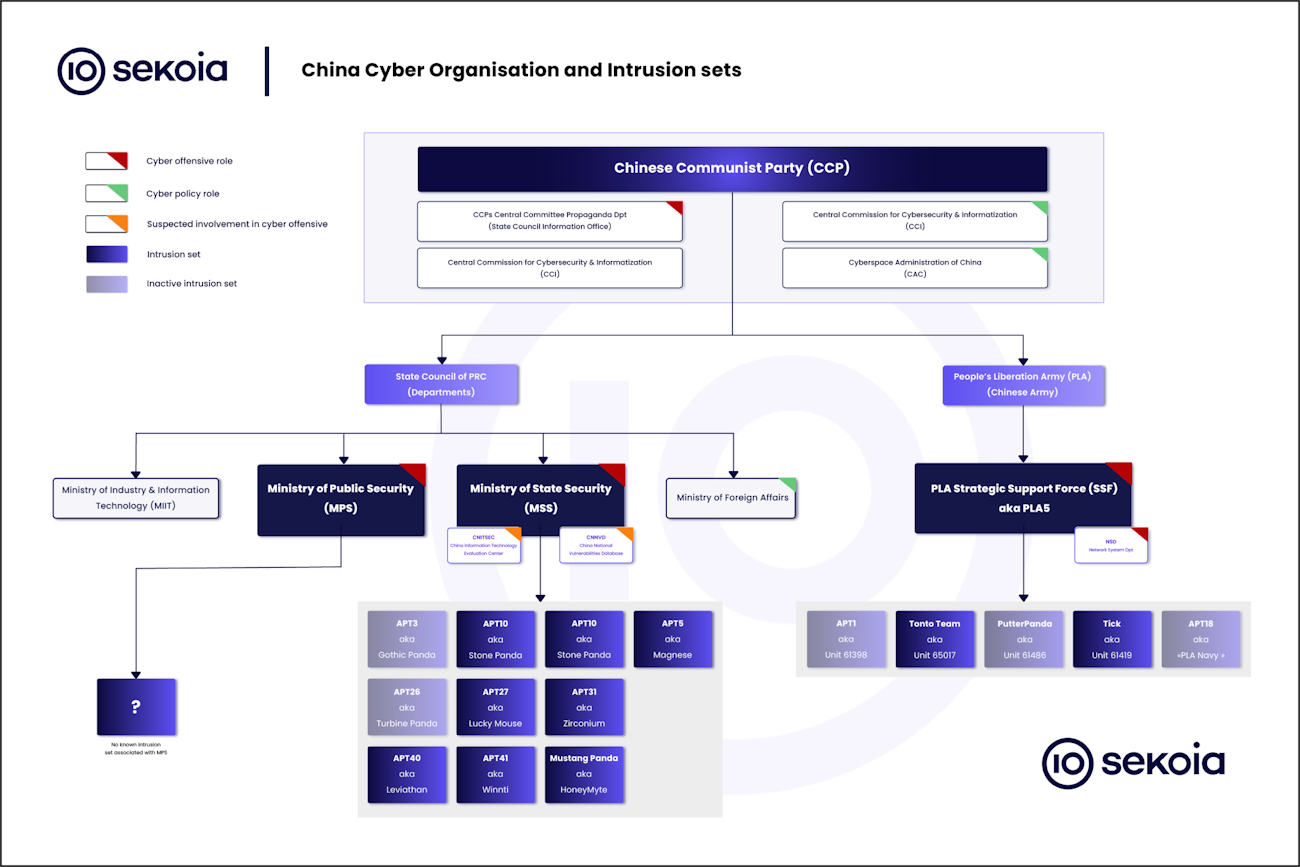
Chinese APT map: Security firm Sekoia has published a map of China's offensive cyber operations, its APT groups, and their respective affiliations.
Storm-0558 intrusion update: Microsoft has provided additional details on how Chinese hacking group Storm-0558 gained access to one of its signing keys. Microsoft says that the group gained initial access to its internal network after compromising an engineer's corporate account. The account allowed access to a debug network where the hackers found a crash dump from one of Microsoft's authentication servers. The crash dump contained a copy of the signing key, which Storm-0558 used to gain access to the email accounts of several US officials and government agencies. Microsoft says it fixed several issues in its internal network that failed to remove the plaintext version of the signing key from crash logs. Although the company has been more candid than usual, ArsTechnica's Dan Goodin points out that many other questions remain unanswered.
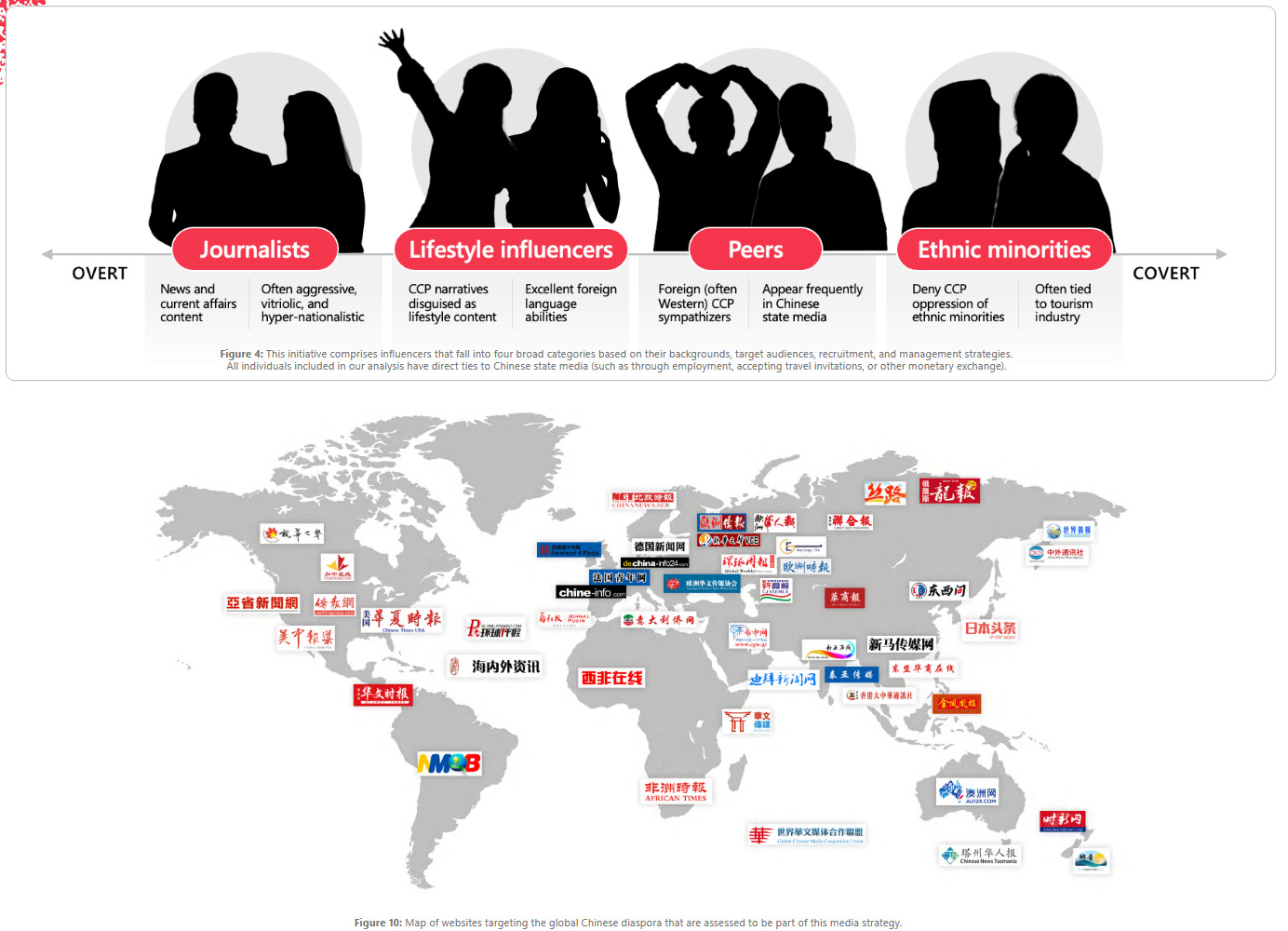
Chinese IOs improve dramatically: A Microsoft report [PDF] has found that Chinese influence operations have increased their effectiveness and engagement rates dramatically in recent months. Despite better engagement, Microsoft says these accounts are also easy to spot because of the fact they used to post in Mandarin in their earlier phases and because of the common "US iz bad, Chine iz da best" trope. Most of these campaigns seem to target audiences in Asia and Africa, where China wants to build a more favorable image for its oppressive regime and denigrate the US and Western democracies. To do this, the CCP seems to have also built a network of news sites in several countries designed to push its propaganda.
"Since approximately March 2023, some suspected Chinese IO assets on Western social media have begun to leverage generative artificial intelligence (AI) to create visual content. This relatively high-quality visual content has already drawn higher levels of engagement from authentic social media users. These images bear the hallmarks of diffusion-powered image generation and are more eye-catching than awkward visual content in previous campaigns. Users have more frequently reposted these visuals, despite common indicators of AI-generation—for example, more than five fingers on a person's hand."
Vulnerabilities, security research, and bug bounty
shelLM: Academics from Argentina and Czechia have created an LLM-powered honeypot that dynamically generates synthetic data as requested by a "trapped" user. The new system is named shelLM.
"Preliminary results indicate that LLMs can create credible and dynamic honeypots capable of addressing important limitations of previous honeypots, such as deterministic responses, lack of adaptability, etc. We evaluated the realism of each command by conducting an experiment with human attackers who needed to say if the answer from the honeypot was fake or not. Our proposed honeypot, called shelLM, reached an accuracy rate of 0.92."
Cisco security updates: Cisco has released six security updates.
K8s security updates: Security updates have rolled out to Google's Kubernetes project to fix three vulnerabilities.
"Three vulnerabilities (CVE-2023-3676, CVE-2023-3955, CVE-2023-3893) have been discovered in Kubernetes where a user that can create Pods on Windows nodes may be able to escalate to admin privileges on those nodes. These vulnerabilities affect the Windows versions of Kubelet and the Kubernetes CSI proxy."
Ivanti vulnerabilities: Yahoo's security found and helped patch four vulnerabilities in Ivanti (formerly MobileIron) Endpoint Manager (EPM). A breakdown of the most dangerous one, an RCE, is included in the blog post.
Jenkins security updates: Security updates are available for the Jenkins project and some of its plugins, including several AzureAD, AWS, Google, and BitBucket plugins.
2023 zero-days: Eight months into the year, we had 58 zero-days discovered and exploited in the wild this year.
Apple zero-days: Apple has released security updates for iOS and macOS to fix two actively exploited zero-days. Both issues were discovered by CitizenLab. The organization says both zero-days were part of a zero-click no-user-interaction exploit chain named BLASTPASS. The exploit was used in the wild to install the NSO Group Pegasus spyware on the latest version of iOS (16.6).
IRM Next Generation zero-days: Bitdefender has discovered five vulnerabilities in the IRM Next Generation online booking system that were exploited in the wild to drop malware on IRM servers. The vulnerabilities include different sets of hardcoded credentials and improper input validation. All five zero-days remain unpatched after the vendor did not respond to Bitdefender's emails. Bitdefender believes the same zero-days were also used to hack the vendor itself back in 2021 [PDF].
Apache Superset vulnerabilities: Horizon3 has published details on two new Apache Superset vulnerabilities, tracked as CVE-2023-39265 and CVE-2023-37941. The vulnerabilities are linked to CVE-2023-27524, a vulnerability they initially found back in April that allowed them to forge authentication tokens to any Superset server by using a SECRET_KEY value that was supposed to be random but was the same for every server. Researchers scanned the internet and said that despite their report, very few Superset servers were patched for that issue, with the number of vulnerable systems going down from 2,124 to 2,076.
Firefox DoS: Security researcher Georgi Guninski disclosed a DoS bug that can flood Firefox's Downloads window with random files.
"The user is notified about this in a small dialog, but there is no option to stop the downloads. The potential denial of service is that the user must manually delete the created files and this might be PITA."
E2EE email vulnerabilities: SonarSource researchers have identified vulnerabilities in three encrypted email providers—Proton Mail, Skiff, and Tutanota. The vulnerabilities were privately disclosed and patched before they could have been exploited in the wild. They impacted web clients and could have allowed attackers to steal emails and impersonate victims if they interacted with malicious messages. The Proton Mail write-up is live, while the rest will go live later.
Infosec industry
IronNet furloughs workers: Cybersecurity firm IronNet has furloughed the vast majority of its employees as the company explores options, including a possible bankruptcy. [Additional coverage in SecurityWeek]
Acquisition news #1: Tenable has announced its intention to acquire cloud security firm Ermetic for $240 million in cash and $25 million in restricted stock and RSUs.
Acquisition news #2: Check Point has acquired SaaS security vendor Atmosec.
Acquisition news #3: Netskope has acquired French cybersecurity firm Kadiska. The company is known for its Digital Experience Management (DEM), Application Performance Monitoring (APM), and Network Performance Monitoring (NPM).
New tool—OpenTF: The Open Terraform foundation has formally launched OpenTF, a framework for building, changing, and versioning cloud infrastructure safely and efficiently. The project is also on GitHub.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how companies often make unilateral decisions that constrain states' behavior, for better and worse.




