Risky Biz News: Two Iranian cyber groups get doxed in a week
In other news: CIA Vault7 leaker gets prison time; Gen. Haugh takes over as NSA and Cyber Command lead; AnyDesk grapples with security breach.

This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The identities of two Iranian cyber groups have been exposed over the course of seven days last week.
The US government linked the Cyber Av3ngers group to six individuals working for the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC), while a report from Iran International linked the Black Shadow group to an Iranian IT company named "Raahkarha-ye Fanavari-e Etela'at-e Jahatpardaz" (or Jahatpardaz Information Technology Solutions).
The "doxing" events come as Iranian cyber activity entered a new and more aggressive stage after Iran-backed Hezbollah attacked Israeli territories on October 7 last year.
Iranian cyber groups launched operations to DDoS and deface Israeli websites, mass-wipe systems, and leak sensitive data from Israeli organizations, with attacks growing in sophistication with each passing week.
While Cyber Toufan's data-wiping campaign had arguably the most destructive impact, it went under the radar because it primarily and exclusively hit Israeli organizations.
On the other hand, Cyber Av3ngers had the biggest impact on an international level after the group gained access to PLC equipment used in critical infrastructure and defaced their screens with anti-Israel and pro-Gaza messages.
The group only targeted PLCs from Israeli company Unitronics, which they breached using the device's default password of "1111".

The Cyber Av3ngers attacks took place at the end of November, and one of their victims was the water authority in Aliquippa, Pennsylvania. The hack spurred a security assessment spree around the globe, with national CERTs urging critical infrastructure operators to make sure critical infrastructure equipment is secured with strong passwords or placed behind VPN gateways and firewalls.
But while Cyber Av3ngers has effectively been an Iranian intelligence op posing as grassroots hacktivism, Black Shadow has been the opposite.
The group is one of the many IT companies that provide cyber capabilities to the Iranian government. Its activities go back years, with Western cybersecurity companies tracking the group under names such as Agrius, DEADWOOD, SharpBoys, and Americium/Pink Sandstorm. It is a legitimate APT, and back in May 2023, Microsoft linked it to Iran's Ministry of Intelligence and Security, or the MOIS, the country's main intelligence service [see PDF, page 6, or graph below].
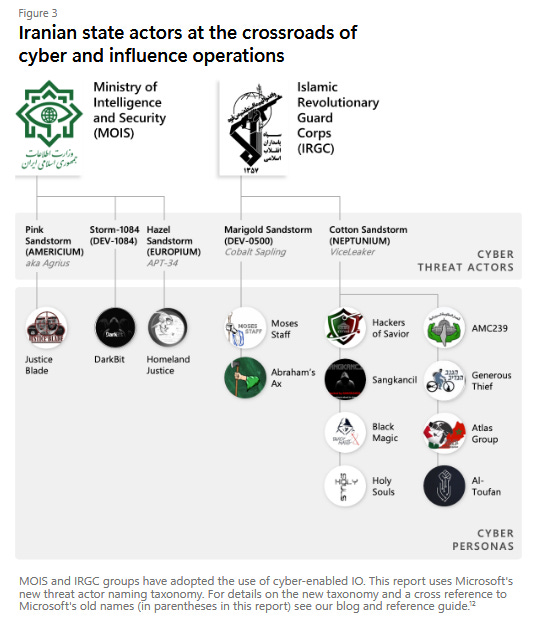
Iran International claims it identified nine of the group's members, who operate from two offices in Tehran. [archive 1, archive 2]
The report has had minimal traction online, so we couldn't gauge its validity from other industry experts. Those who we contacted declined to comment, citing the need for more time to investigate it further. While it is a report from a non-government and non-threat intel source, the report is very likely to be accurate. Iranian cyber operations have been doxed more times than any other major cyber power, primarily due to the regime's oppressive hand that has indirectly led to the rise of silent dissenters and leakers among its ranks.
Breaches, hacks, and security incidents
Cloudflare security breach: Cloudflare says that a state-sponsored threat actor gained access to its Atlassian servers during the Thanksgiving holiday last year. The attackers used legitimate server credentials that Cloudflare failed to revoke after the Okta security breach from a month earlier, in October. Cloudflare says the compromised server had no customer data, and the breach was immediately detected and contained. The company did not make a formal attribution but says the threat actor sought to obtain persistent and widespread access to its network.
Football Australia leak: Australia's soccer federation exposed AWS access keys in its website's source code, allowing threat actors easy access to more than 127 of its storage buckets. The organization is currently investigating the impact of the breach. [Additional coverage in the Sydney Morning Herald]
Abracadabra Money crypto-heist: A threat actor stole $6.5 million worth of crypto-assets from DeFi protocol Abracadabra Money. The platform says the threat actor exploited a vulnerability in its platform to borrow the funds illegally. The company has sent the attacker a blockchain note asking for its funds back in exchange for a white-hat reward—in yet another shady attempt to hide a malicious hack as vulnerability research. [Additional coverage in DailyCoin]
Clorox ransomware attack: Cleaning products maker Clorox has reported losses of $49 million in connection to a cyberattack the company suffered in August of last year. The figure covers incident response costs, third-party consulting services, and operating costs from the resulting business disruption. In SEC filings last year, Clorox said it expected sales to drop by $356 million as a result of the same incident. The company's CISO also departed weeks after the incident. [Additional coverage in SecurityWeek]
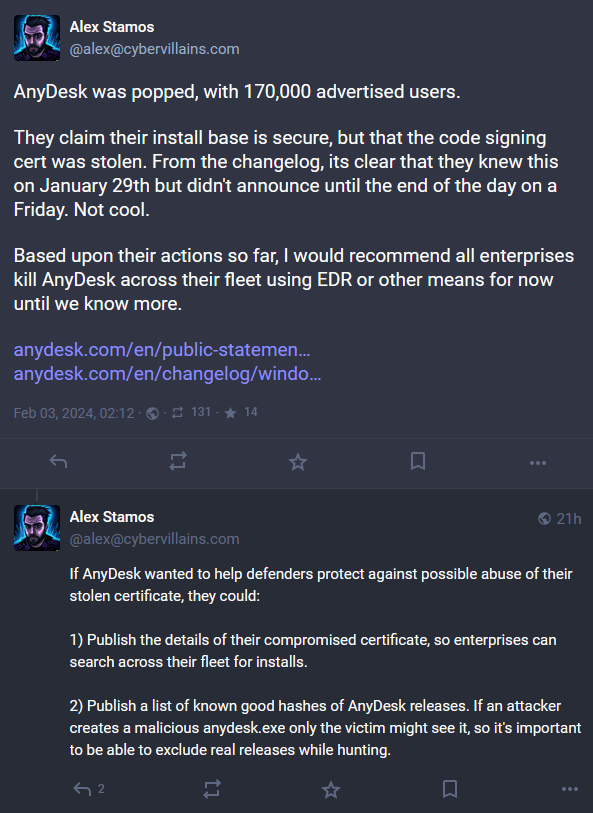
AnyDesk breach: Remote access software company AnyDesk suffered a security breach [archived] on January 29. Hackers accessed internal systems and stole AnyDesk's source code and code signing certificates. The company says that it does not store tokens or keys for accessing remote AnyDesk installs. It did initiate a password reset for customer accounts on its website and support portals. AnyDesk claims it serves more than 170,000 customers, including some of the world's largest companies. The company says the incident is not ransomware. [Additional coverage in BleepingComputer]
General tech and privacy
FTC Blackbaud order: Cloud service provider Blackbaud will be required to delete user data that it does not need for its operations. The requirement is part of a settlement with the US Federal Trade Commission, which sued the company in the aftermath of BlackBaud's 2020 security breach. The company previously also paid a $3 million fine to the SEC for making misleading disclosures about the same incident.
Post-quantum crypto in Firefox: Mozilla has added support for post-quantum cryptography protections in Firefox Nightly. This can be enabled by going to about:config and enabling security.tls.enable_kyber.
RCS protocol: The EFF has published a blog post looking over the new RCE protocol and its downsides and security weaknesses.
Google Search Cache button: Google plans to remove the "cache" feature from its search engine. The feature allows users to view an archived version of a web page as it was recorded by Google during its most recent visit. The company has already removed the "Cache" button from search results and plans to remove the ability to prepend URLs with the "cache:" prefix to view their cached versions. The feature has been used in the past during malware investigations and to bypass paywalls and geo-filters. [Additional coverage in Search Engine Roundtable]
New Teams feature: Microsoft has added a new feature to its Teams application that can allow administrators to disable copying text or forwarding messages from an active chat. The feature is meant to prevent data leakages from sensitive meetings.
Games in Russia: Sony is blocking users from Russia and Belarus from activating its games on the Steam platform. Sony previously stopped PlayStation sales in Russia in March 2022, shortly after its invasion of Ukraine.
Hulu cracks down on password sharing: Following Netflix's move, Hulu has also banned password sharing. Only users in the same household will be allowed to share an account. Users in different locations will need their own accounts. [Additional coverage in The Hollywood Reporter]
Government, politics, and policy
UN Cybercrime Treaty: Royal Hansen, Google's Vice President of Privacy, Safety and Security Engineering, warns that the current version of the UN Cybercrime Treaty criminalizes vulnerability and cybersecurity research.
Tesla car ban: The Chinese government has banned Tesla cars from entering government-affiliated buildings and adjacent premises. According to messages posted on social media by Chinese Tesla drivers, the ban appears to have entered into effect at the end of 2023. Chinese officials cited Tesla's sentry mode feature and its extensive data collection practices. Beijing banned Tesla cars from entering military bases shortly after the carmaker entered the Chinese market. [Additional coverage in Nikkei]
Russia's internet censorship: A third of Russian websites are at risk of getting blocked inside the country after their foreign web hosting providers have not registered with officials. The providers are in violation of a new Russia law that requires all cloud and web hosting providers to register with the Roskomnadzor, Russia's telecommunications watchdog. The new law entered into effect on December 1 of last year, and providers that did not register risk having their servers blocked inside Russia. Only 266 web hosting providers have registered with the Roskomnadzor, and all are local companies. [Additional coverage in Ria Novosti]
New NSA & CYBERCOM head: US Air Force General Timothy Haugh has officially taken over the position of Director of the National Security Agency and Commander of US Cyber Command. Gen. Haugh replaces US Army General Paul Nakasone, who led both agencies since May 2018. Haugh previously served as the deputy commander of US Cyber Command and was the inaugural head of the 16th Air Force, the branch's first cyber unit.
FTC to make cloned voice calls illegal: The Federal Communications Commission plans to vote to make AI-generated voice calls illegal. The agency says robocalls using cloned voices have escalated over the past years. Scammers have used AI technology to clone the voices of family members, celebrities, and politicians to defraud users.
Robocall success: The US government says it recorded a reduction in the number of illegal robocalls across US mobile networks. The decline comes three months after the FCC and FTC sent letters to seven of the US' top telephony network providers. Companies like CenturyLink, Bandwidth, and TeleCall allegedly worked to detect and block common sources of robocall spam.
FETTA: CERT teams from Poland and Luxembourg have launched the Federated European Team for Threat Analysis, or FETTA, a project aiming to create a federated team to provide CTI products and tooling to EU partners.
Sponsor section
In this Risky Business News sponsor interview Tom Uren talks to Haroon Meer of Thinkst Canary. They discuss how network attackers win, how their tactics have changed over time and what this means for network defenders.
Cybercrime and threat intel
Vault7 leaker sentenced: A US judge has sentenced a former CIA employee to 40 years in prison for leaking classified information to WikiLeaks. The leaked documents are known as Vault7, and they revealed extremely sensitive information about the CIA's hacking capabilities. Joshua Schulte was arrested and has been in jail since 2018. Schulte's sentence covers espionage, hacking, contempt of Court, making false statements to the FBI, and child pornography.
SIM swapper sentenced: A judge has sentenced an Oregon man to three years in prison for stealing millions of dollars in cryptocurrency through SIM swapping. According to court documents, Daniel James Junk stole more than $3 million from dozens of victims between December 2019 and March 2022. Officials say Junk was a member of an online community specialized in SIM swapping attacks.
FTX SIM swappers charged: The US has charged three suspects for allegedly stealing more than $400 million from cryptocurrency exchange FTX. US prosecutors allege the three suspects used SIM-swapping attacks to take control of an FTX employee's phone number and move crypto-assets from its official accounts. The hack took place in November 2022 as the company was collapsing into bankruptcy and was initially thought to be an inside job. [Additional coverage in Elliptic and ArsTechnica]
"A recent indictment alleged that Robert Powell—using online monikers "R," "R$," and "ElSwapo1"—was the "head of a SIM swapping group" called the “Powell SIM Swapping Crew.” He allegedly conspired with Indiana man Carter Rohn (aka "Carti" and "Punslayer") and Colorado woman Emily Hernandez (allegedly aka "Em") to gain access to victims' devices and "carry out fraudulent SIM swap attacks" between March 2021 and April 2023."
BEC scam recovery: The US Secret Service has recovered more than $3 million stolen by BEC scammers from the North Carolina Housing Finance Agency in April 2023. [Additional coverage in The Record]
Spyware maker shuts down: Two phone surveillance solutions named PhoneSpector and Highster appear to have shut down operations shortly after getting fined $410,000 by New York's OAG. [Additional coverage in TechCrunch]
Spyhide profile: NZZ reporters have published a profile on Spyhide, a now-defunct Iranian spyware vendor. The service had shut down after getting hacked by a Swiss hacker.
Wikipedia scams: The Wikipedia editorial team has published an article on how "reputation companies" are scamming users and companies across the world with so-called Wikipedia page creation or page editing services.
New npm malware: Thirty-three malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
TeamTNT doppelgänger: DataDog's security team has tracked a cryptomining campaign that has targeted servers with exposed Docker APIs. This blog post seems to cover a threat actor that Cado named Command Cat.
DangerDev: Invictus IR has published a report on DangerDev, a threat actor seen hijacking AWS infrastructure for cryptomining. The threat actor seems related to what DataDog covered here.
AlphV operations: Security firm AreteIR is reporting that the AlphV ransomware group has returned with new attacks despite a US takedown in mid-December of last year.
Shadow rebrand: The Shadow ransomware gang has rebranded under the name of DARKSTAR. The gang has a history of primarily attacking Russian organizations. It was previously also known as Comet.
REF0657: Elastic's security team looks at REF0657, a threat actor that hit a financial services organization in South Asia in December 2023.
DeFi scams: Sophos' Sean Gallagher looks at the recent "DeFi mining" and "DeFi Savings" crypto scams that have flooded social media over the past months.
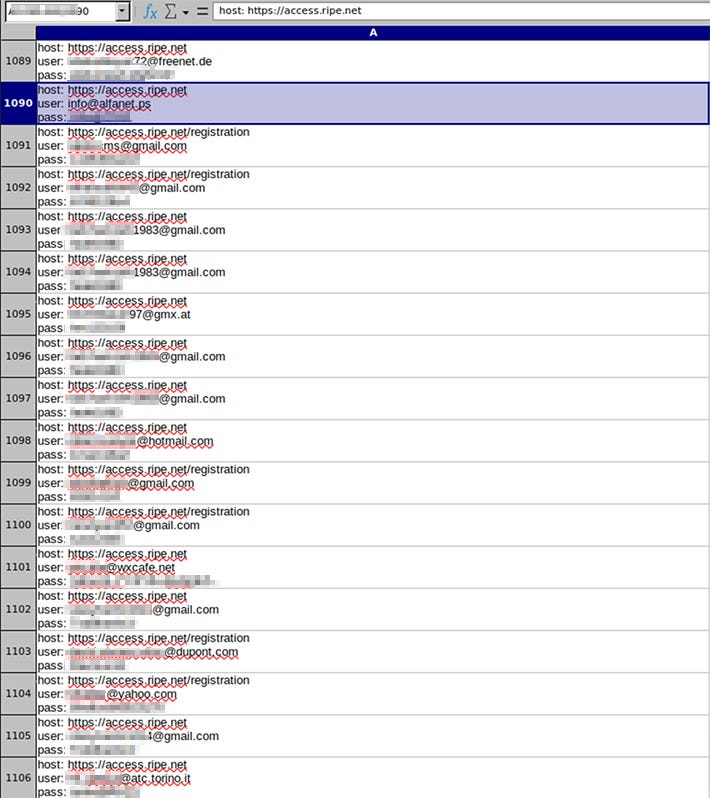
NetOps exposure: Threat intel company Resecurity has identified more than 1,500 compromised network operator accounts that are currently being sold on the dark web. The accounts provide access to RIPE, APNIC, LACNIC, and AFRINIC management portals, where threat actors can hijack BGP routes and hijack internet traffic. Resecurity says account credentials were stolen after operators had their systems infected with infostealers.
Malware technical reports
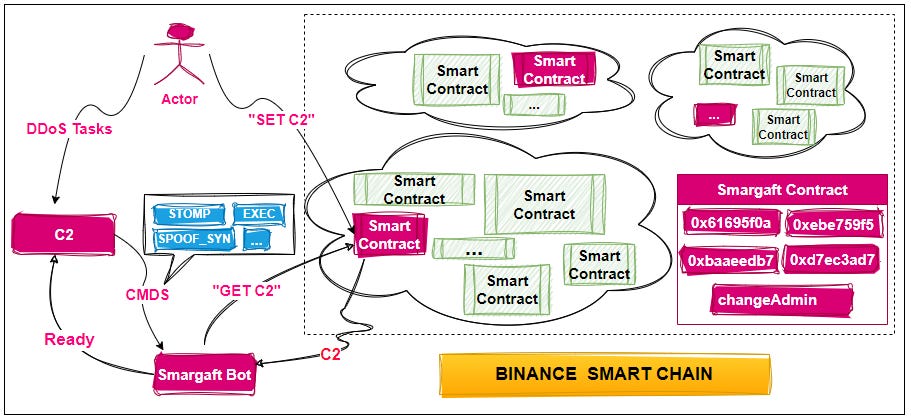
Smargaft technique: A new IoT botnet named Smartgaft is abusing Binance smart contracts to host and hide information about the location of its command and control servers. Chinese security firm QiAnXin first spotted the botnet in October of last year and said Smartgaft is being used to launch DDoS attacks and run a malicious proxy network. The botnet is the second threat actor to hide information about its infrastructure in Binance smart contracts after the ClearFake gang. The technique is known as EtherHiding.
Backdoor Activator: SentinelOne's Phil Stokes looks at Backdoor Activator, a novel macOS malware currently distributed via pirated macOS apps. With macOS gaining ground in the enterprise market, we are now seeing more and more malware gangs focusing on macOS systems.
Zephyr: AhnLab researchers look at Zephyr, a cryptominer distributed via phishing campaigns.
AZORult: CyberInt researchers have published a technical dive into the AZORult infostealer.
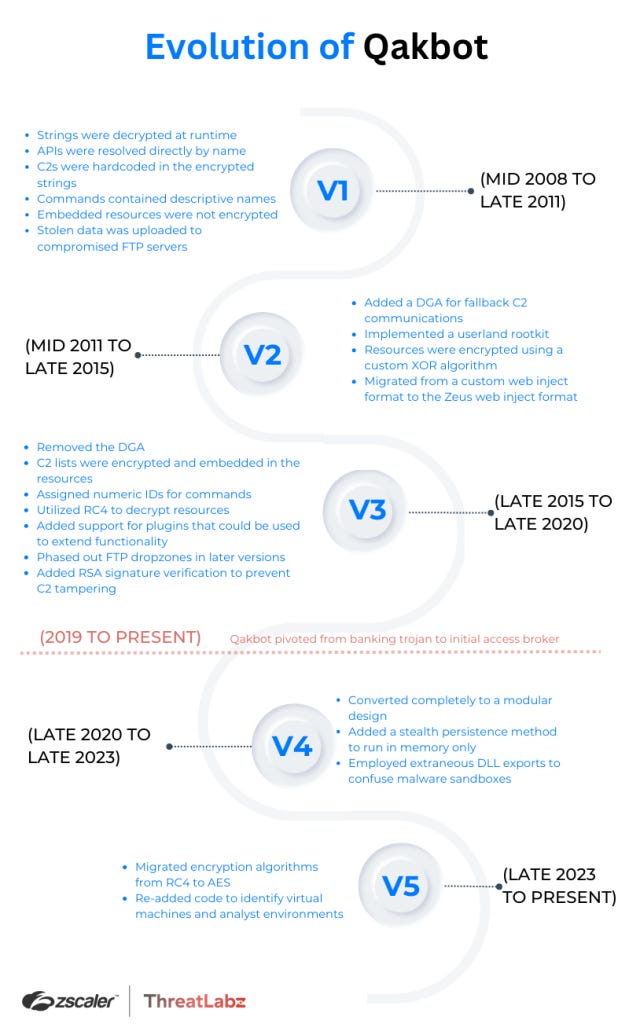
Qakbot: Zscaler analysts look at how the Qakbot malware has evolved over the past 15 years since its creation.
Sponsor Section
Most companies discover they've been breached way too late. Thinkst Canary fixes this: just 3 minutes of setup, no ongoing overhead, nearly 0 false positives, and you can detect attackers long before they dig in. Check out why our Hardware, VM, and Cloud-based Canaries are deployed and loved on all 7 continents.

APTs, cyber-espionage, and info-ops
Stately Taurus: CSIRT-CTI has published details on more Stately Taurus campaigns targeting the Myanmar military regime, attacks the company documented in a previous blog post.
Kimsuky: Chinese security firms Sangfor and QiAnXin have published reports on Kimsuky's recent operations targeting South Korean organizations with the Xeno RAT.
APT-K-47 (Mysterious Elephant): Chinese security firm KNOW Chuangyu has published a report on new tools used by APT-K-47 (Mysterious Elephant), an APT they believe might be tied to the Bitter group.
STEADY#URSA: Securonix has published details on STEADY#URSA (aka Shuckworm), a Russian threat actor targeting Ukrainian military personnel with a new PowerShell-based backdoor named SUBTLE-PAWS. The backdoor can spread via infected USB devices.
2023 APT report: Chinese security QiAnXin has published its year-in-review report for APT activity observed in 2023.
Vulnerabilities, security research, and bug bounty
Confluence honeypot spam: VulnCheck researchers say the internet has been flooded with Atlassian Confluence honeypots, which is making the discovery of real servers a much harder operation. The company has found that only 4,000 of the 240,000 Confluence systems are legitimate servers. The number of Confluence honeypots has exploded after several highly critical vulnerabilities have been disclosed and exploited in the wild over the past months. Currently, CISA's KEV database lists nine Confluence vulnerabilities exploited in the wild.
ModSecurity vulnerability: SicuraNext's Andrea Menin has published an analysis of CVE-2024-1019, a vulnerability in the ModSecurity open-source WAF that allows threat actors to bypass the firewall.
QNAP security updates: Taiwanese NAS vendor QNAP has released 23 security updates for its products.
Juniper security updates: Juniper has released a security update to patch 20 vulnerabilities in its JSA (Juniper Secure Analytics) series.
Zyxel security updates: Zyxel has released a security update to fix a post-auth command injection vulnerability in its NAS products.
Flysmart+ Manager vulnerabilities: Pen Test Partners have found vulnerabilities in Flysmart+ Manager, a mobile app developed by Airbus and used by pilots to manage their flight schedules.
Vinchin vulnerabilities: LeakIX has published a write-up on five vulnerabilities in the Vinchin Backup & Recovery solution. The bugs—from CVE-2024-22899 to CVE-2024-22903—can be chained for RCE attacks.
Infosec industry
PAN loses patent lawsuit: A judge awarded cybersecurity company Centripetal Networks $151.5 million in damages in a patent infringement lawsuit filed against Palo Alto Networks. A jury trial found that Palo Alto Network infringed on four of Centripetal's "threat intelligence gateway" patents. Centripetal was previously awarded $2.75 billion in a 2020 lawsuit against Cisco, the largest patent infringement penalty in US history. Cisco had the record-breaking award invalidated in an appeal last year. [Additional coverage in MarketScreener]
New tool—DCV Inspector: Security researcher Andrew Ayer has open-sourced DCV Inspector, a tool to inspect the DNS, HTTP, and SMTP requests made by a certificate authority during domain validation.
New tool—OSS-Fuzz-Gen: Google has open-sourced OSS-Fuzz-Gen, a new LLM-driven fuzzing framework based on its OSS-Fuzz toolkit.
New tool—Deluder: Software engineer Michal Válka has released Deluder, a tool for intercepting traffic of proxy-unaware applications. It currently supports OpenSSL, GnuTLS, SChannel, WinSock, and Linux Sockets.
New tool—ThievingFox: Security researcher Slowerzs has open-sourced a red-team tool named ThievingFox, a collection of post-exploitation tools to gather credentials from various password managers and Windows utilities.
New tool—DIFFER: Security firm Trail of Bits has open-sourced a tool named DIFFER that can find bugs and soundness violations in transformed programs.
"We used DIFFER to evaluate 10 software debloating tools, and it discovered debloating failures or soundness violations in 71% of the transformed programs produced by these tools."
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the war in Ukraine is showing how useful mobile devices are in a war. Using them is risky, but those risks need to be managed.




