Risky Biz News: Tech companies and security firms rally against EU vulnerability disclosure rules
In other news: Apple and Atlassian patch zero-days; Supermicro patches BMC bugs; PEACHPIT ad fraud botnet goes down.
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
A group of more than 50 tech experts and organizations have signed an open letter asking EU officials to rethink Article 11 of the upcoming EU Cyber Resilience Act.
The article introduces a mandatory requirement for all software vendors to disclose vulnerabilities to the ENISA, the EU's cybersecurity agency, within 24 hours of becoming aware of in-the-wild exploitation. ENISA will then relay this information to national CSIRT teams and stock market watchdogs across its member states.
The open letter's signatories argue that the CRA's Article 11—in its current form, at least—greatly expands the number of organizations that will have first-hand and real-time immediate knowledge of actively exploited vulnerabilities, which, in turn, increases the risks to product vendors, their customers, and the general public.
Signatories raise three main issues with Article 11's broadened zero-day disclosure spectrum.
First, they fear that information on actively exploited bugs will eventually make its way into the hands of some intelligence agencies and be abused for intelligence and surveillance operations. Not a bad argument, especially after some EU member states have been caught abusing spyware in obvious cases of human rights abuse and illegal surveillance over the past 3-4 years.
Second, signatories argue that with so many new parties involved in dealing with zero-day information, there is now the risk of more leaks and accidental disclosures. Such cases would provide details about active exploitation to threat actors, who could then (re)create the exploits and abuse the same bugs in their own campaigns.
Third, experts also fear the new EU zero-day disclosure rules will interfere with existing coordinated disclosure procedures, which, in some cases, tend to keep ongoing exploitation secret until they can prepare and test patches.
"As a result, the CRA may reduce the receptivity of manufacturers to vulnerability disclosures from security researchers, and may discourage researchers from reporting vulnerabilities, if each disclosure triggers a wave of government notifications."
I'm not sure about this particular point, but the first two have their merits.
The open letter criticizes the CRA Article 11 but also proposes a set of modifications.
- Agencies should explicitly be prohibited from using or sharing vulnerabilities disclosed through the CRA for intelligence, surveillance, or offensive purposes.
- The CRA should not require reporting of vulnerabilities that are exploited through good faith security research.
- Require reporting to agencies of mitigatable vulnerabilities only, within 72 hours of effective mitigations (e.g., a patch) becoming publicly available.
The letter's signatories include representatives from Google, Arm, the EFF, and many of today's top security vendors like Bitdefender, ESET, Trend Micro, Rapid7, HackerOne, BugCrowd, and Tenable.
Breaches, hacks, and security incidents
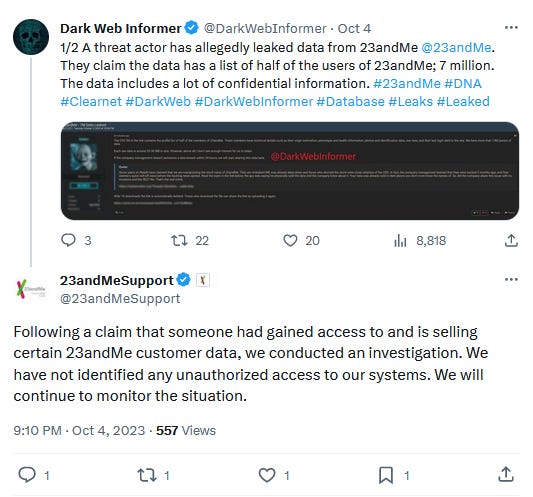
23andMe denies breach: DNA and genetic testing service 23andMe denies having suffered a security breach after a threat actor claimed to have hacked the company and stole the DNA-related data of more than seven million registered users.
Sony breach: Sony Interactive Entertainment has joined the list of more than 2,300 companies impacted by the MOVEit hacks. The company says the hackers stole data on current and former employees and their families. The breach took place in late May, according to a letter Sony filed with US authorities. Almost 7,000 people are impacted.
Lyca Mobile cyber attack: A cyber attack has impacted the network of British virtual mobile operator Lyca Mobile. The company says the incident disrupted national and international calling and prevented customers from adding new minutes to SIM cards. Lyca says the incident impacted 56 of 60 countries the company is active in. Unaffected markets included the US, Australia, Ukraine, and Tunisia. [Additional coverage in SecurityWeek]
Xiaomi outage: A massive outage has hit Xiaomi devices across Russia and Belarus. The incident prevented user devices from connecting to the Mi Home service. The outage impacted security cameras, vacuum cleaners, and other smart devices. [Additional coverage in RBC]
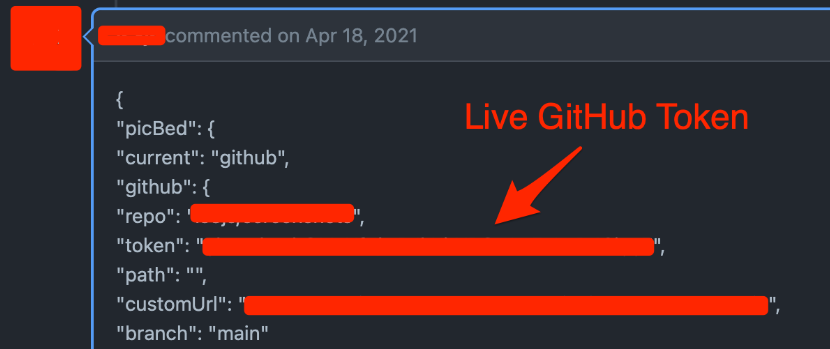
Major API keys leak: Truffle Security has identified more than 700 live API keys and passwords that were included in GitHub comments. The comments were filed with pull requests and issue trackers. Researchers say human users authored 97% of all the comments and that most commenters had no relation with the projects.
General tech and privacy
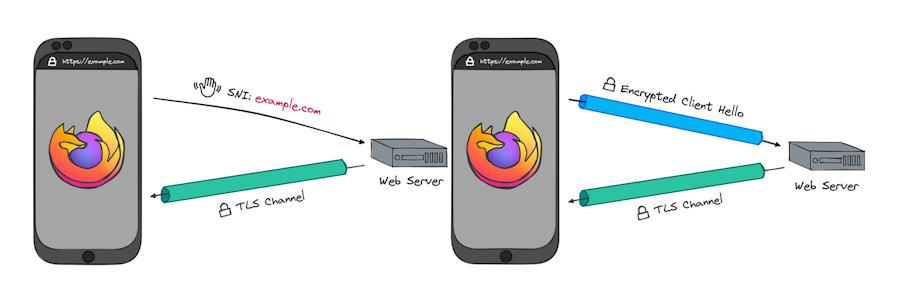
ECH in Firefox: Support for Encrypted ClientHello (ECH) has been enabled for all Firefox 118 users. ECH is a new TLS extension that fully encrypts web traffic and doesn't leak a user's website destination. Google rolled out support for ECH in Chrome last month with the release of Chrome 117.
Yahoo anti-spam features: Earlier this week, Google announced a set of new rules for email bulk-senders. Yahoo has announced the same rules. The rules will require bulk senders to authenticate their emails and provide easy ways for users to unsubscribe. The new Yahoo anti-spam rules will come into effect in the first quarter of 2024.
Android 14 is out: Google has announced that its newest Pixel 8 smartphone will receive seven years of software and security updates. Prior to the announcement, Pixel devices were only supported for five years. Google announced the new Pixel 8 extended support on the same day the company released Android 14, the latest version of the Android mobile operating system.
Government, politics, and policy
MACE Act: The US House of Representatives has passed a bill that would remove minimum education requirements on federal cybersecurity jobs. Named the Modernizing the Acquisition of Cybersecurity Experts Act, the bill is the latest in a long series of US legislation aimed at addressing a shortage of cybersecurity experts in federal agencies. The bill passed with an overwhelming 394-1 vote and is now headed to the Senate floor, where it is expected to pass as well. [Additional coverage in FedScoop]
CISA social media ban reinstated: A US federal appeals court has reinstated a ban on CISA from interacting with social media companies as part of the agency's efforts to combat online dis/misinformation. The suit, filed by two Republican Attorneys General, argues CISA is limiting fReE sPeEcH. [Additional coverage in CNN]
Russia tests social scoring system: A Russian university has developed and is testing a social scoring system inspired by the one in use in China. Named We (Мы), the platform has been developed by the Russian State Social University in Moscow. The We system will produce a social score for Russians based on their personal life, education, financial status, criminal record, public life, and internet activity. Work on the platform began last year in July 2022, and the first version is now being tested with the university's students. Back in 2018, Russian officials described a Chinese-style social scoring system as "a threat to Russia." [Additional coverage in the Moscow Times]
Cyberattacks on Ukraine power grid: Ukraine Energy Minister German Galushchenko says cyberattacks are a bigger threat to the country's power grid than rockets and drones because the repercussions of a cyber incident can paralyze whole systems rather than impact small substations—as rockets usually tend to do. [Additional coverage in The Economist/non-paywall]
Hacktivism "rules": Two legal advisers for the International Committee of the Red Cross (ICRC) have published a set of eight recommendations/rules for "civilian hackers" (aka hacktivists) involved in an armed conflict. The rules are clearly inspired by the activities of pro-Russian and pro-Ukrainian hacktivists in the recent Russo-Ukrainian conflict. Those groups don't seem to be impressed or care about the new rules. Despite some media reporting that the "ICRC" formally published the new rules, it did not. They were published on a legal blog, and both authors described it as their own opinion. The eight rules are:
- Do not direct cyber attacks* against civilian objects.
- Do not use malware or other tools or techniques that spread automatically and damage military objectives and civilian objects indiscriminately.
- When planning a cyber attack against a military objective, do everything feasible to avoid or minimize the effects your operation may have on civilians.
- Do not conduct any cyber operation against medical and humanitarian facilities.
- Do not conduct any cyber attack against objects indispensable to the survival of the population or that can release dangerous forces.
- Do not make threats of violence to spread terror among the civilian population.
- Do not incite violations of international humanitarian law.
- Comply with these rules even if the enemy does not.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Selena Larson, Senior Threat Intelligence Analyst at Proofpoint, about the state of play in the cybercrime ecosystem. People and organizations are getting better at protecting themselves from scams and compromises, but criminals will use every possible avenue to reach people and scam them.
Cybercrime and threat intel
PEACHPIT botnet takedown: Human Security has disrupted the operations of PEACHPIT, a vast ad fraud botnet operated by the BADBOX threat actor. BADBOX assembled the PEACHPIT botnet by selling backdoored Android TV streaming boxes on popular online stores and by spreading malicious Android and iOS apps. The purpose of the botnet was to secretly install apps on the infected devices that would show and play unwanted ads. At its peak, researchers say PEACHPIT was communicating with more than 121,000 Android devices and more than 159,000 iOS devices a day. Human says the BADBOX group operates out of China and most likely has access to hardware supply chains.

Casinos are laundering cybercrime profits: A ProPublica investigation has found that casinos in Cambodia, Laos, and Myanmar are helping local cybercrime groups launder funds obtained through online scams.
Bentley servers: An investigation has linked servers hosting LockBit stolen data to Bentley, a former member of the Conti gang. Researchers say the server is hosted in Moscow. A Palo Alto Networks investigation last week also found that the Clop gang has been hosting some of its servers in Moscow as well.
Qakbot gang: The threat actors behind the recently dismantled Qakbot botnet have now switched to distributing the Remcos RAT and the Knight ransomware, per Cisco Talos.
SpyNote evolution: Mobile security firm Pradeo says it is seeing the SpyNote spyware evolve from a RAT to a banking trojan.
Stream-jacking attacks: Bitdefender says it's seeing threat actors hijack popular YouTube channels to push Musk-themed crypto-scams. Welcome to 2016!
Polymorphic EDR Killer: CyFirma security researcher Kaushík Pał has discovered threat actors advertising a new EDR killer app that can mutate its code in order to avoid detection.
ICS exposure: Bitsight says it identified more than 100,000 industrial control systems (ICS) exposed on the internet. This includes equipment like sensors, tank gauges, building management systems, actuators, valves, relays, and more.
Dwell time plummets: Threat actors are deploying ransomware on breached networks faster than ever before. In just 12 months, the median dwell time of ransomware groups on hacked networks has fallen from 4.5 days to less than one day. According to security firm Secureworks, ransomware is being deployed within one day of initial access in more than 50% of engagements and within five hours of initial access within 10% of cases.
Rootkits on npm: ReversingLabs has discovered a malicious package on the npm repository that infected developer workstations with a rootkit and a remote access trojan. The package was live for several days and downloaded more than 700 times.
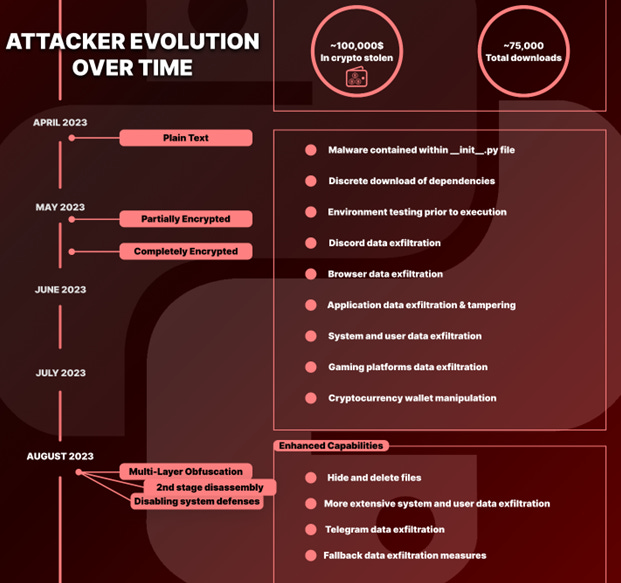
PyPI crypto hacker: A threat actor has stolen more than $100,000 worth of cryptocurrency from Python developers this year. The attacker used hundreds of malicious Python libraries uploaded to the official PyPI portal. The libraries contained a Windows infostealer that collected passwords and other valuable data from infected developer machines. Security firm Checkmarx says the campaign began in April this year, and its sophistication grew each month with more layers of obfuscation and encryption.
Malware technical reports
GoldDigger: Group-IB has discovered a new banking trojan named GoldDigger that specifically targets users of over 50 Vietnamese banking, e-wallets, and crypto-wallet apps.
Snake keylogger: ANY.RUN has a breakdown of the Snake keylogger.
RevengeRAT: Embee Research explains how to extract configuration data from RevengeRAT samples.
New Mirai variants: Chinese security firm NSFOCUS takes a look at three recent versions of the Mirai DDoS malware—hailBot,kiraiBot, catDDoS.
Sponsor Demo Section
Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view of it.
APTs and cyber-espionage
Semiconductor spying: A Chinese cyber-espionage group has launched a campaign against semiconductor companies in Taiwan, Hong Kong, and Singapore. The attack involves a spear-phishing campaign with a TSMC lure that tries to infect targets with a version of the HyperBro loader. The malware was previously used in attacks carried out by the Iron Tiger group, also known as APT27, Budworm, LuckyMouse, or Emissary Panda.
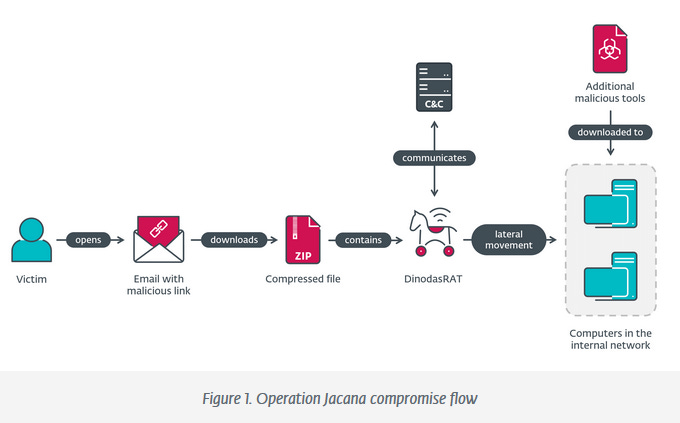
Operation Jacana: ESET researchers have identified a cyber-espionage campaign targeting a governmental entity in Guyana. While ESET has not formally attributed the attacks, they believe the campaign was the work of a China-aligned threat group.
Vulnerabilities, security research, and bug bounty
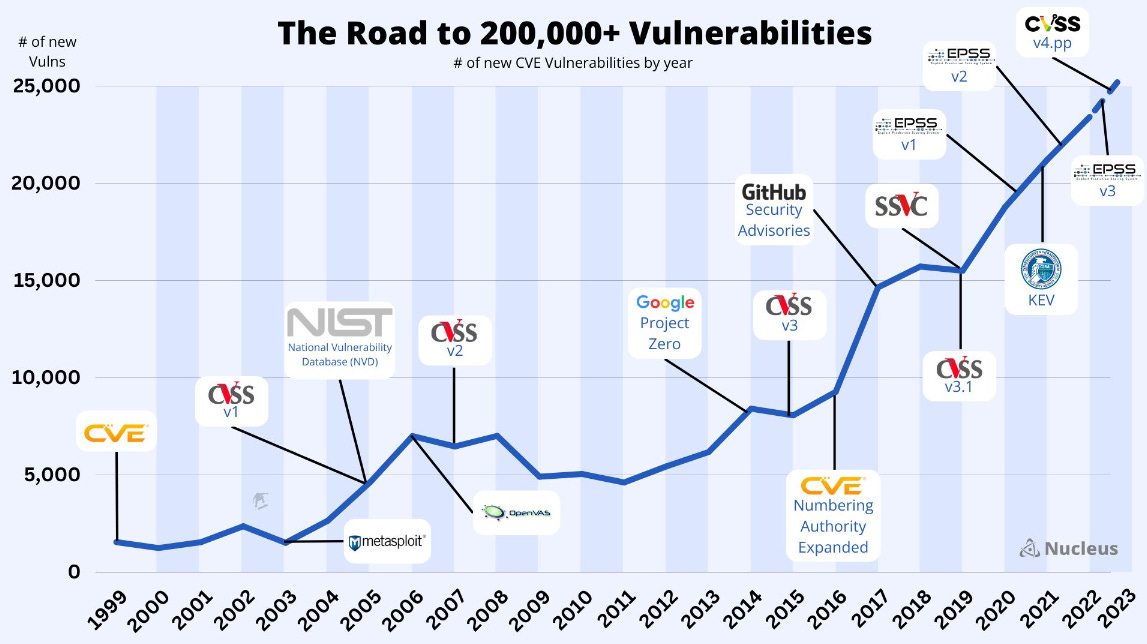
NVD milestone: The US NIST National Vulnerability Database (NVD) is now storing information on more than 200,000 vulnerabilities. (h/t Patrick Garrity)
Top 10 misconfigs: The blue and red teams at CISA and the NSA have published a list with the top 10 most common misconfigurations they have encountered in large organizations. The shortlist is below, and a full breakdown is in the joint document.
- Default configurations of software and applications
- Improper separation of user/administrator privilege
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Weak or misconfigured multi-factor authentication (MFA) methods
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
Apple zero-days: Apple has released a security update for iOS devices to patch two actively exploited zero-days. The first is a vulnerability (CVE-2023-42824) in the iOS kernel that Apple says was exploited against older iPhones using iOS 16.6 or lower. The second is a zero-day (CVE-2023-5217) in the Libvpx library that Google discovered last week, and Apple also ported and fixed in iOS.
Confluence zero-day: Atlassian has released a security update to patch an actively exploited zero-day in Confluence "Data Center" and "Server" appliances. Tracked as CVE-2023-22515, the vulnerability can be used to create unauthorized admin accounts and access Confluence resources. The vulnerability has a severity rating of 10/10.
macOS DirtyNIB vulnerability: Security researcher Adam Chester has discovered a vulnerability that allows malicious processes to hijack macOS app entitlements. Chester named the vulnerability DirtyNIB as the exploit relies on replacing NIB files inside app bundles while not breaking an app's entitlements and Gatekeeper verification.
cURL security fix coming: The cURL library will receive a security fix on October 11; a high-rated vulnerability and described as one of the most severe issues patched in cURL in recent years.
X.org vulnerabilities: The X.org team has patched five vulnerabilities in two of its component libraries.
Cisco security updates: Cisco has released five security updates, including a patch to remove credentials for the root account from some of its firmware.
Printer vulnerabilities: Devcore has published a detailed write-up on three printer vulnerabilities it used at the Pwn2Own hacking contest back in 2021. The vulnerabilities are pre-auth RCEs and impact Canon, HP, and Lexmark printers.
Looney Tunables PoCs: Several PoC exploits have been published for Looney Tunables, a recently disclosed LPE in the glibc library.
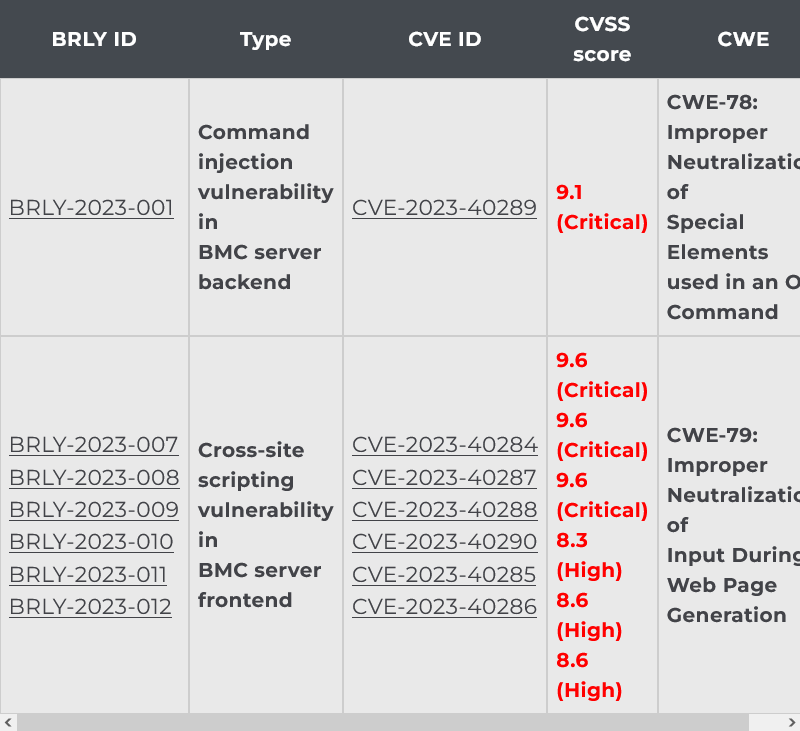
Supermicro BMC bugs: Supermicro has released a security update to patch seven vulnerabilities in the IPMI firmware of its BMC products. Several of the patched vulnerabilities can be exploited by unauthenticated attackers to gain root access to remote systems via the BMC web-facing frontend. More than 70,000 Supermicro IPMI BMC systems have their web interfaces exposed on the internet. Researchers at Binarly say Supermicro tried to reduce the severity of its bugs during the disclosure process and encourages companies to apply the available patches as soon as possible.
"Unfortunately, as usually happens during the disclosure process, the vendor tried to reduce the final impact of the documented vulnerabilities. We believe this to be an extremely wrong position, since end customers will have incorrect information when assessing the severity of a particular update. We encourage system administrators to keep their BMC systems up to date and follow NSA and CISA hardening guidelines."
Infosec industry
BlackBerry split: BlackBerry plans to separate its IoT and cybersecurity services into two independently operated entities and then file for an IPO for its IoT subsidiary.
Free cybersecurity help for NGOs: A consortium of cybersecurity organizations will provide free cybersecurity services to more than 200 NGOs around the globe.
CISA Security Planning Workbook: CISA has published a new free resource named the Security Planning Workbook, a document meant to help organizations create basic security plans.
IAM guidance for vendors: CISA and the NSA have published guidance for software vendors and developers on how to properly implement multi-factor authentication (MFA) and single sign-on (SSO) technologies in order to develop better Identity and Access Management (IAM) systems. The two agencies say the new guidance is complementary to guidance it published earlier this year in March that targeted IT admins.
New tool—OpenPubkey: The Linux Foundation has open-sourced OpenPubkey, an open-source cryptographic protocol designed to secure software supply chains.
"OpenPubkey enables users to securely and accurately bind cryptographic keys to users and workloads by turning an OpenID Connect Identity Provider (IdP) into a Certificate Authority (CA)."
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine whether offensive cyber operations against ransomware groups have succeeded or failed. And how would we even know?




