Risky Biz News: SVR hackers also breached HPE
In other news: New Chinese APT caught performing AitM attacks; Ukraine hacktivists wipe Russian satellite imagery processing center; major RCE bug patched in Jenkins.

This newsletter is brought to you by Material Security, the company that secures the cloud office with unified email security, user behavior analytics, and data loss prevention for Microsoft 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Days after Microsoft revealed a security breach by a Russian state-sponsored hacking group, Hewlett Packard Enterprise disclosed a similar breach at the hands of the same group.
In a document filed with the US Securities and Exchange Commission (SEC), HPE blamed the breach on Midnight Blizzard, a hacking group believed to be one of the cyber units operating inside Russia's Foreign Intelligence Service (SVR).
HPE says the group breached its cloud infrastructure in May of last year.
The company learned of the hack for the first time in June, but an initial investigation revealed the group only managed to collect and steal a limited number of SharePoint files.
HPE says that despite its initial containment, the group appears to have maintained access to its cloud infrastructure.
The tech giant was notified again in December, and a new investigation revealed the group managed to steal emails from some of its employees in the company's cybersecurity, go-to-market, and business departments.
The incident marks the second time that a major company spotted Midnight Blizzard stealing emails from their cybersecurity team. In its SEC disclosure, Microsoft said the group searched the emails of its cybersecurity team to look for information on itself in an attempt to learn what Microsoft knew about them.
The two SEC filings come on the heels of new SEC cybersecurity regulations that entered into effect in December and which mandate that companies listed on the stock market disclose any cybersecurity incident that may have a "material" impact on share prices and shareholders.
As legal and infosec commentator Brian in Pittsburgh points out, the new rules appear to have changed the entire cybersecurity landscape.
Both SEC disclosures paint a picture where two major tech companies hid major APT intrusions from authorities, the public, and shareholders.
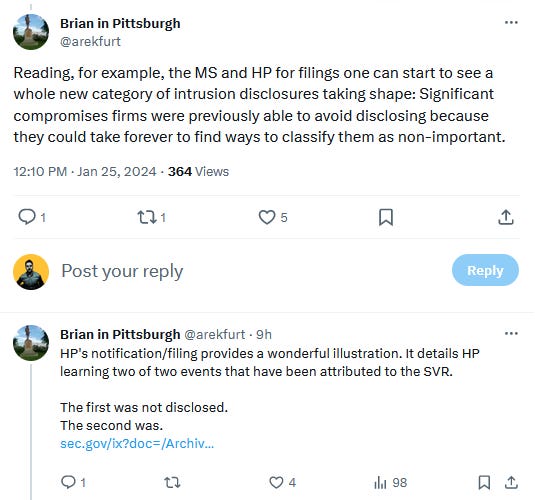
Although the new SEC breach disclosure rules have been criticized by the private sector and some US lawmakers because they might overlap with other breach disclosure requirements, they appear to be more effective, as we've learned of an HPE APT intrusion the company easily buried last year.
In addition, the same SEC breach disclosure rules are also making companies disclose ransomware attacks much faster than last year. Instead of waiting for weeks, we now usually see an SEC filing days after an attack, along with additional follow-ups containing far more details about what happened than we've seen in previous years.
It's quite clear that many companies are erring on the side of caution, until they learn how they can manipulate and push on the SEC's new rules.
Breaches, hacks, and security incidents
Israeli movie theaters defacements: A Turkish hacktivist group has defaced screens inside Tel Aviv movie theaters to show images from the October 7 Hamas attack. [Additional coverage in Ynet]

Monobank DDoS attacks: A massive DDoS attack has disrupted the activities of Monobank, Ukraine's largest mobile banking operator. Disruptions were recorded over the weekend and linked to Russian "hacktivist" groups. The bank was also targeted on December 12 of last year, on the same day that Russian military hackers wiped systems at Kyivstar, the country's largest mobile operator. [Additional coverage in the Kyiv Independent]
NoName DDoS attacks: After getting absolutely ignored by the Romanian government, the pro-Kremlin "hacktivist" group NoName has spent the last two days harassing the IT teams responsible for government sites for France, Finland, and Poland.
EquiLend cyber incident: Securities lending EquiLend has shut down its IT systems in the aftermath of a cybersecurity incident. The incident took place on January 22. The company told customers it may take several days to restore services. EquiLend serves some of the world's largest banks and stock markets, and its NGT platform handles more than $2.4 trillion in securities transactions each month.
Veolia ransomware incident: The North American branch of water and waste management company Veolia has suffered a ransomware attack [archived].
AerCap ransomware incident: Aircraft leasing company AerCap has confirmed that it suffered a ransomware attack on January 17. In documents filed with the SEC, the company says it regained full control over its IT systems, and it's in the process of investigating what data was stolen. The company is the first victim listed on the dark web leak site of a new ransomware gang named Slug. AerCap is the world's largest aircraft leasing company, operating out of the US and Ireland.
Planeta hack: A pro-Ukrainian hacktivist group named the BO Team has hacked and wiped 280 servers at one of Russia's space and meteorology research centers. Ukraine's Defence Intelligence Main Directorate (GUR) says the hack crippled the center's activity of processing satellite data for Russia's Defense Ministry and Ministry of War. Ukrainian officials say the hackers destroyed 2 PB of data and crippled the activity of the center's expensive supercomputers.
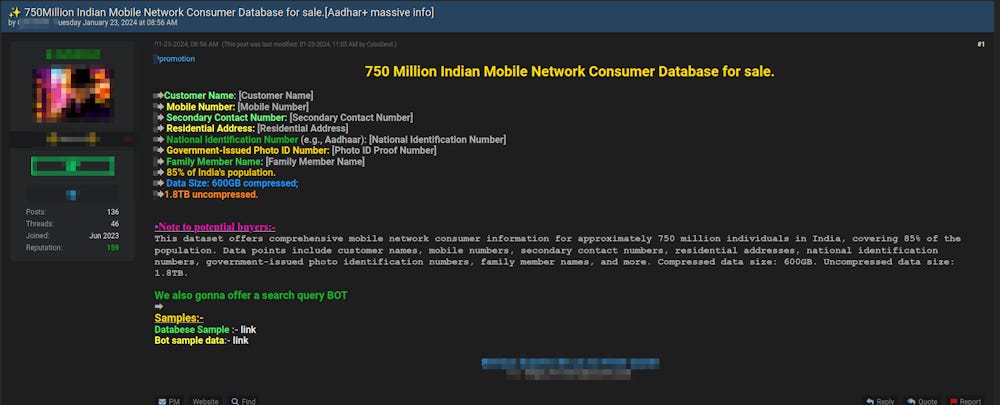
Major Indian mobile data leak: A threat actor named CyboDevil is selling a giant database that allegedly contains the data of more than 750 million Indian nationals. According to security firm CloudSEK, the data appears to have been aggregated from multiple Indian mobile operators. The threat actor claims the database contains the personal details of 85% of India's population. The data is being advertised in several places, such as Telegram and underground hacking forums. [Additional coverage in Scroll.in]
General tech and privacy
Firefox 122: Mozilla has released Firefox 122. New features and security fixes are included. The biggest updates are improvements to the browser's built-in translator and support for passkeys on macOS.
Passkeys on Twitter: Twitter has announced support for passkeys on iOS devices. This is available for both free and paid users alike.
Pixel update issues: Google paused the January 2024 Google Play system update after the patch started causing storage issues on Pixel devices. [Additional coverage in AndroidPolice]
New Meta teen protections: Meta is rolling out an update to its Instagram and Facebook Messenger services to block strangers from sending direct messages to underage children (under 16/18, depending on the country). Starting this week, accounts for children will only be able to receive messages from individuals in their friend list or phone address book. Meta is rolling out the changes two days before its executives are set to testify in front of a US Senate hearing that will address child safety on social media.
Ring: Amazon's Ring security camera service announced that it will stop honoring law enforcement requests to access data without a court warrant.
Telegram, criminal's safe haven: Dutch TV station NOS reports, citing Dutch police sources, that Telegram is barely responding to requests to take down Telegram channels advertising drugs.
Apple-v-NSO lawsuit: A US judge has denied an NSO Group request to dismiss a lawsuit filed by Apple. The American company sued the Israeli spyware maker in November 2021 in an attempt to obtain a court order to prevent NSO from developing iPhone exploits. A US judge shot down NSO Group's attempts to dismiss the US lawsuit and move it to its home turf in Israel. [Additional coverage in 9to5Mac]
Apple EU changes: With the upcoming release of iOS 17.4, Apple will allow alternative app stores to be installed on EU devices. The update is part of the company's larger set of changes designed to comply with the EU Digital Markets Act (DMA). Other changes include free access to the iPhone's NFC chip to support third-party payment solutions and the ability for browser makers like Google, Mozilla, and Microsoft to use their own browser engines instead of Safari's standard WebKit. Users will also have for the first time, the ability to side-load apps on iOS, similar to Android.
Government, politics, and policy
Incoming Bideo EO on personal data transfers: Bloomberg reports that the White House is preparing to issue an executive order to ban data aggregators from selling American citizens' data overseas. We'll have more when the EO comes out.
NSO lobbying in Washington: Israeli spyware maker NSO Group has amped up its Washington lobbying efforts in an attempt to get itself off the US sanctions list. The company has recently released a transparency report and is using its role in the Hamas war as a way to prove its usefulness for government operations. NSO officials say that as part of their compliance work, they have terminated six customer accounts following reports of human rights abuse and product misuse. [Additional coverage in Wired]
NCSC warning on AI: The UK's NCSC has published an advisory warning that over the course of the next two years, AI technologies will lead to an increase in the efficacy of cyber operations, such as ransomware, social engineering, reconnaissance, and others.
ACSC guidance on AI: Australia's ACSC, together with its Five Eyes counterparts, has published guidance on how to use AI systems securely.
BabakovLeaks fallout: Back in August 2023, a pro-Ukrainian hacktivist group named Cyber Resistance hacked and leaked emails from Oleksandr Babakov, deputy chairman of the Russian State Duma. Months later, journalists from InfoNapalm have sifted through the data and found Russian insiders in Serbian politics and a Russian campaign to influence EU news media.
Belarus changes military doctrine: The Belarusian government is updating its military doctrine to allow for the use of military force in response to destructive cyber attacks. A similar provision exists in the NATO treaty. Russian policy expert Oleg Shakirov points out that no such provision currently exists in Russian military doctrine. The new Belarusian military doctrine also includes a provision to allow the country to use nuclear weapons. Russia sent tactical nuclear weapons to Belarus in May 2023. [Additional coverage in Belarus News]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Ivan Dwyer of Material Security about how it makes sense to view office productivity suites as an organisation's critical infrastructure.
Cybercrime and threat intel
Trickbot author sentenced: A US judge has sentenced a Russian national to five years and four months in prison for his role in developing and deploying the Trickbot malware. Vladimir Dunaev developed browser modifications that aided Trickbot in stealing browser credentials and deploying additional malware on infected computers. Dunaev was arrested in late 2021 after getting stuck in South Korea due to COVID-19 travel restrictions. He was extradited to the US and charged a month later.
Scattered Spider member detained: US authorities have detained a 19-year-old from Florida on charges of wire fraud, aggravated identity theft, and stealing $800,000 worth of cryptocurrency from five victims. Noah Michael Urban operated online under nicknames such as "Sosa," "King Bob," and "Anthony Ramirez." One source has told Risky Business that Urban is suspected to be an affiliate of the Scattered Spider group.
TLO admin charged: US prosecutors have charged and filed an arrest warrant for a Baltimore man suspected of running an underground cybercrime service. Chouby Charleron allegedly ran TLO, a Telegram bot that allowed other threat actors to purchase the personal data of any American citizens for prices between $15 and $25. The service gained a reputation in underground circles for its accuracy and was widely used for doxxing, financial fraud, and swatting.
GitLab exposure: More than 5,300 GitLab servers are currently exposed on the internet and are vulnerable to a vulnerability that allows threat actors to reset passwords and hijack admin accounts. Tracked as CVE-2023-7028, the vulnerability was patched on December 11, last year. Most of the vulnerable servers are located in the US, Germany, Russia, and China, according to a scan performed by the Shadowserver Foundation. GitLab admins and users can mitigate the attack without patching by enabling 2FA for their accounts. Proof of concept code has been available online since the day of the patch, and exploitation has already taken place.

Qwiklabs abuse: Indian security firm CloudSEK looks at a payment scam operation that abuses the Qwiklabs cloud platform for its infrastructure.
Malvertising network: The same CloudSEK team looks at a massive malvertising campaign that is redirecting users to a network of more than 9,000 malicious domains.
Game hacks: AhnLab researchers have found several gaming-related hacks that secretly install a crypto-miner on users' devices. 2011 called! It wants its malware distribution tactics back.
Insider threats report: Security firm Securonix has published its 2024 Insider Threat Report, based on a survey of 450 cybersecurity professionals on the nature of insider threat challenges faced by organizations.
2023 malware report: ANY.RUN has published a report on the malware trends of 2023. The awards go to loaders (for the most popular malware family) and Redline (for the most popular malware).
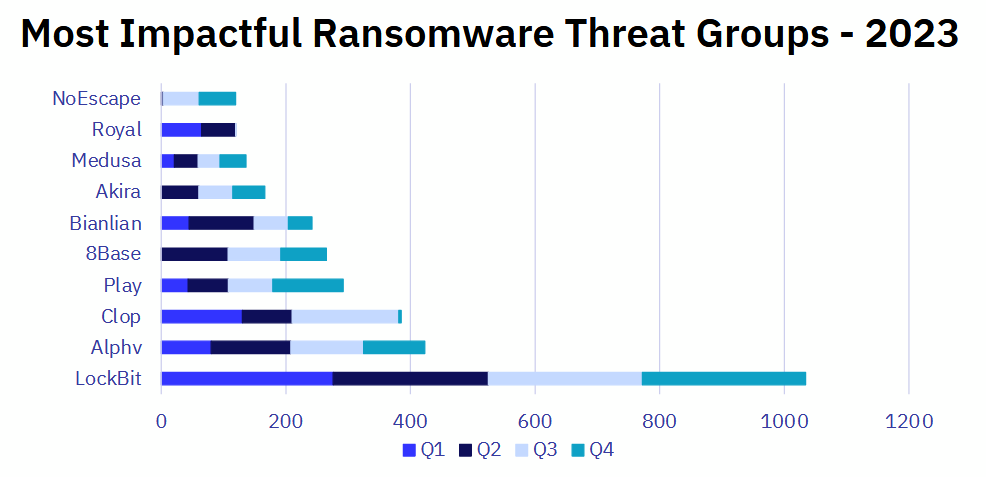
2023 ransomware report: The number of victims listed on ransomware portals grew by 80% in 2023, with ransomware operations returning to their 2021 levels before Russia's invasion of Ukraine. The most prolific group last year was the LockBit gang, which listed more than 1,000 victims on its leak site. This marks the second year that LockBit topped the chart after it took the title from the now-defunct Conti gang in 2022. According to GuidePoint Security, US-based organizations accounted for 49% of all observed ransomware attacks in 2023. (Broadcom's Symantec also has one of these reports out, but they have AlphV on top over a different time period.)
Malware technical reports
CherryLoader: Arctic Wolf has observed a new loader, dubbed CherryLoader, written in Go and used in recent intrusions.
AllaKore RAT: BlackBerry looks at a recent AllaKore RAT campaign targeting Mexican banks and Cryptocurrency platforms.
Faust ransomware: Fortinet researchers have discovered a new ransomware strain named Faust. The ransomware appears to be another variant of the old Phobos ransomware, whose source code was leaked online years ago.
Sponsor Section
A deep dive into what's new with Material Security's Phishing Protection product: New detections, response UX boosters, and more actionable reports.
APTs, cyber-espionage, and info-ops
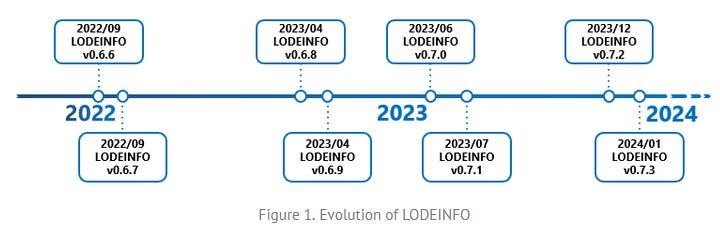
APT10: Japanese security firm Itochuci has published a report on APT10's LODEINFO malware.
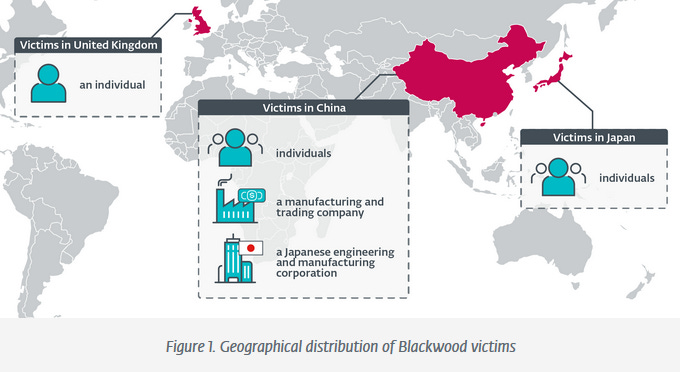
Blackwood: A Chinese cyber-espionage group named Blackwood has used adversary-in-the-middle (AitM) attacks to hijack updates for legitimate software applications. The AitM attacks intercepted and modified updates for Chinese software such as Tencent QQ, Sogou Pinyin, and WPS Office to deliver a new backdoor named NSPX30. Security firm ESET says the group has been active since 2018 and has targeted organizations and individuals in China, Japan, and the UK. Blackwood is now the third Chinese APT that was observed in recent years with AitM traffic interception capabilities, after LuYou and Evasive Panda.
IRGC groups: Recorded Future has published a report providing a summary of four organizations with links to Iran's Islamic Revolutionary Guard Corps (IRGC) and how some of their contractors have been linked to espionage, cybercrime, and influence operations overseas—eventually also landing on the US sanctions list.
Predatory Sparrow: Wired's Andy Greenberg has published an article covering all the Predatory Sparrow hacks that targeted Iranian organizations over the past two years.
DPRK operations in SK: South Korea's NIS intelligence agency says they've seen North Korean groups attempt to incorporate AI in their operations. Officials also said that the DPRK accounts for 80% of all cyberattacks targeting South Korean government networks. [Additional coverage in KBS and Yonhap News]
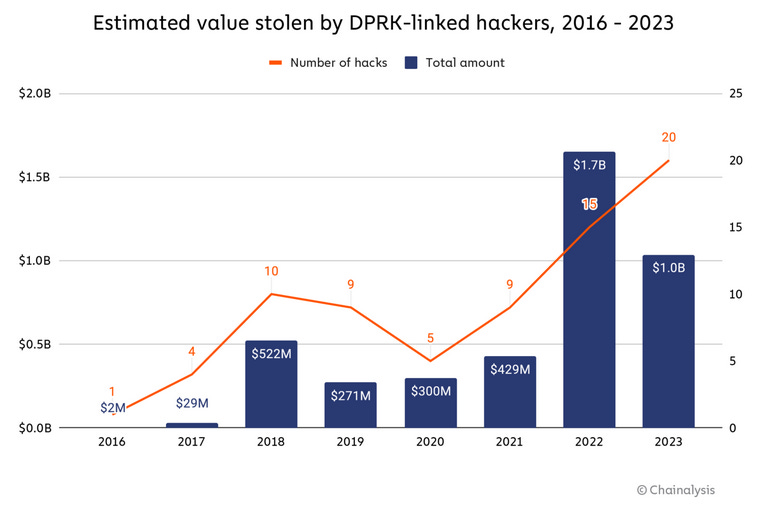
DPRK crypto-hacks: In 2023, North Korean hackers stole $1 billion worth of crypto assets from 20 organizations, according to data collected by Chainalysis. DPRK groups stole less money than the year before, but they conducted more intrusions, down from $1.7 billion stolen assets stolen across 15 incidents in 2022. Overall, 2023 was a bad year for all crypto thieves, who only stole $1.7 billion across 231 incidents, way below the $3.7 billion stolen in 2022.
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released or updated five security advisories for various products.
Jenkins RCE: The Jenkins automation server has released a security update to patch a major vulnerability. Tracked as CVE-2024-23897, the vulnerability has a severity rating of 9.8/10 and impacts the app's CLI component. The Jenkins team has confirmed various attack scenarios that can allow attackers to retrieve cryptographic keys, delete files, or run malicious code through various methods. If patches can't be installed, the vulnerability can be mitigated by disabling the CLI component. The vulnerability was discovered by Sonar researcher Yaniv Nizry.
GKE Sys:All: Cloud security firm Orca has discovered a security flaw in the Google Kubernetes Engine (GKE) that could be abused to hijack GKE clusters. Named Sys:All, the issue arises from admins misunderstanding the role of the system:authenticated user group in GKE deployments.
"The loophole is not exactly a vulnerability but more an extremely prevalent misconfig stemming from widespread misconception around GKE – many seem to assume that the system:authenticated group in Google Kubernetes Engine includes only verified and deterministic identities. It actually includes any Google-authenticated account, even those outside the organization. This basic misunderstanding leads administrators to regularly enable the group with overly permissive roles, something they wouldn’t do if they realized what the system:authenticated group actually was."
"Orca conservatively estimates that as many as 1 million GKE clusters are vulnerable solely because of this loophole. A brief scan by the team uncovered over 250,000 vulnerable GKE clusters in the wild, some of which contain secrets that would enable lateral movement."
Leaky API keys: API security platform Escape says it found more than 18,000 API keys exposed on the internet after scanning 189.5 million URLs.
35-year-old vulnerability: JFrog researchers look at a duo of libX11 vulnerabilities (a DoS and RCE) that can be used to attack Linux environments. The two bugs impact all libX11 versions dating back to 1989.
GTB vulnerabilities: A group of security researchers going by the "Adepts of 0xCC" have published a write-up on two vulnerabilities that can be used to hack into GTB Central Console, a data loss prevention platform.
Triton vulnerability: Security firm ProtectAI has found a vulnerability in the API of Triton, a type of inference server used by the AI/ML industry. PoC code is available on GitHub.
Chrome zero-day PoC: A proof-of-concept exploit was released for CVE-2022-4262, a Chrome zero-day patched back in December 2022.
Zyxel PoC: SSD has published proof-of-concept for a pre-auth RCE in Zyxel routers. SSD didn't say if the bugs were reported or patched.
Infosec industry
Industry moves: Former NSO Group executives, including the former CEO Shalev Hulio, launched a new company named Dream Security. The new company allegedly hired 13 former NSO Group employees and secured a $33 million round of venture capital funding. According to Hulio, Dream Security will provide cybersecurity defenses for critical infrastructure entities. Hulio first touted Dream Security back in October 2022, shortly after leaving NSO in August 2022. [Additional coverage in The Intercept]
New tool—SECurityTr8Ker: Security researcher Pancak3lullz has released a tool named SECurityTr8Ker that can monitor the SEC's RSS feed for 8K and 6K filings for cybersecurity incidents. The script currently powers a Twitter account here. There's also another account that tracks these things here and a different web portal for tracking SECdisclosures here.
New tool—cvemap: Project Discovery has open-sourced a tool named cvemap, a CLI utility designed to provide a structured and easily navigable interface to various vulnerability databases.
Risky Business Podcasts
In this podcast episode of the Seriously Risky Business series, Patrick Gray and Tom Uren talk about how the SEC’s new disclosure rules that mean companies have four days to report cyber security incidents once they’ve formally decided that they are material. So far, companies are very much erring on the side of caution.
They also look at the criticism of the CSRB’s board composition. Tom thinks these critiques are misguided. The cyber security landscape is so fractured that if the board were made up of faceless bureaucrats it would get very limited traction.




