Risky Biz News: South Korea is investigating "spy chip" in Chinese weather measuring equipment
In other news: Ecuador's election disrupted by cyberattack; Baghdad closes LED advertising screens after hack; and Ivanti patches another zero-day.
This newsletter is brought to you by Trail of Bits. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
South Korea's National Intelligence Service (NIS) has found malicious code embedded in the chips of weather-measuring instruments made in China and used by the Korean Meteorological Administration.
The malicious code was described as a "spy chip" that can eavesdrop on its surroundings and "steal information through radio frequencies," South Korean TV network Channel A reported this week.
A representative for the Korean Meteorological Administration told KBS, South Korea's national broadcaster, that the malicious code was found four months ago but didn't elaborate on how it was discovered.
NIS says that while it dealt with Chinese malware (software-based backdoors) in the past, the incident marks the first time it found a "hardware backdoor" in Chinese-made equipment.
In the aftermath of the discovery, NIS is currently conducting a massive security audit on more than 10,000 pieces of equipment made in China and used by government agencies. It said it plans to publish the results of its investigation later this year.
The two reports confirm early reporting from last month about mysterious malicious code in "measuring equipment used by government agencies." The initial report was widely dismissed or ignored because officials didn't share enough information.
In recent months, South Korea as a whole seems to have turned on the idea of blanketing its territory with insecure Chinese-made equipment.
After footage from a Seoul plastic surgery clinic that used Chinese security cameras showed up on Chinese adult forums, NIS forbade government agencies from using any CCTV or IP security cameras that have not gone through a formal "security verification" process, with the directive specifically taking aim at Chinese made equipment.
Risky Business featured interview
In this joint Risky Business and Geopolitics Decanted feature interview, Patrick Gray and Dmitri Alperovitch talk to Illia Vitiuk, the Head of the Department of Cyber and Information Security of the Security Service of Ukraine (SBU), about the cyber dimension of Russia's invasion of Ukraine.
Breaches, hacks, and security incidents
Ecuador's election disrupted by cyberattack: A cyberattack has disrupted Ecuador's online voting system. Officials say the attack prevented Ecuadorians living abroad from casting their votes in the country's presidential election. The attack did not alter votes, but the incident was the least of everyone's worries as Ecuador was also rocked by an earthquake on the day of the vote. In addition, the voting took place under a heavy police and military presence after one of the presidential candidates was assassinated earlier this month. [Additional coverage in CBS News]
Baghdad closes LED advertising screens after hack: Iraqi officials have ordered street marketing companies to shut down LED advertising screens across the city of Baghdad. The order comes after a hacker defaced a screen and showed an adult movie in one of the city's largest intersections. The movie ran for minutes until someone cut the board's power cable. Iraqi security forces say they arrested a suspect believed to have orchestrated the hack. [Additional coverage in IraqiNews]
Bern police hack: Hackers have exploited a vulnerability in an Ivanti (formerly MobileIron) server and stolen the personal details of more than 2,800 police officers from Bern, Switzerland's capital. The breach took place in mid-July and was most likely carried out using a zero-day in the Ivanti EPMM server. This same zero-day was also used to hack and steal data from 12 Norwegian government agencies. [Additional coverage in SRF/English coverage in SwissInfo/ via m:Kensan]
BabakovLeaks: Pro-Ukrainian hacktivist group Cyber Resistance has hacked and leaked data from the email account of Oleksandr Babakov, deputy chairman of the Russian State Duma. Journalists from InfoNapalm claim the leaked files expose Babakov's corruption and call him a "master of primitive money laundering schemes." The leak also shows Babakov's role in establishing ways for the Russian government to evade Western sanctions by working with African and Asian countries to import sanctioned goods. This is the fourth major hack-and-leak operation orchestrated by the Cyber Resistance group. They previously doxxed Russian pilots who bombed civilian infrastructure in Ukraine, doxxed the leader of the APT28 cyber-espionage group, and dumped the email correspondence of former Duma member and Russian propagandist Semyon Bagdasarov.
AUR data leak: Romanian right-wing political party AUR has exposed the personal details of more than 20,000 donors who signed up for the organization's official mobile app. The leak occurred through the app's donor leaderboard section, which was retrieving each member's entire data through an unencrypted JSON file. Exposed data included sensitive details such as real names, home addresses, emails, phone numbers, and ID card numbers. [Additional coverage in Digi24]
auDA denies data breach: Australia's national domain administrator auDA has published a post-mortem of an investigation into an alleged data breach. auDA says its systems were never breached and that hackers stole data on Australian domains from an Australian sole trader and then tried to pass it as auDA's data. The incident has been linked to a new ransomware operation named NoEscape, which launched in June this year.
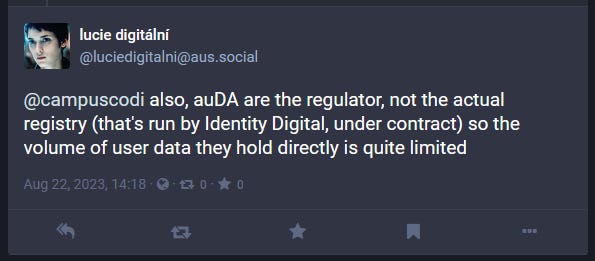
Seiko confirms ransomware attack: The AlphV (BlackCat) ransomware group has taken credit for the attack on Japanese watchmaker Seiko. The group published samples of the company's data on its dark web leak site earlier this week after Seiko refused to pay the ransom. Seiko said it was hacked on July 28 and confirmed that some customer information might have been stolen. AlphV claims to have more than 2 TB of the company's data.
General tech and privacy
Excel adds Python support: Microsoft has released a public preview of its Excel app that can now run Python code inside Excel spreadsheets. The feature is only available for Microsoft 365 cloud customers. Microsoft says all the Python code will run inside its own hypervisor-isolated container to prevent malicious abuse.
Chrome's Project Sandbake: Since the start of the year, Google's security team has been participating in Project Sandbake, an internal Google effort to improve Chrome's C++ codebase by removing dangerous code paths and patterns. So far, Google says its engineers have shipped "improvements to the dangling pointer detector" and investigated improvements to raw_ptr flags."
"We also revisited some of the memory limits on renderers and were able to unblock some Web Assembly use-cases without impacting memory usage or performance. In addition, work was done on hardening the renderer process against attacks on kernel devices such as \device\cng and some general continued sandbox refactoring including adding a generic capability to preload DLLs needed by sandboxed processes before the sandbox fully engages."
Government, politics, and policy
Joint PCQ advisory: CISA, NIST, and the NSA have published a joint guide meant to help critical infrastructure organizations prepare and migrate to post-quantum cryptographic algorithms.
UA warning for news agencies: Ukraine's SSSCIP is warning local news agencies to prepare for cyber-attacks from Russian hackers. The agency cites past attacks on news organizations, such as a June incident at the national public broadcaster, a May attack on Gordon Media, a July 2022 attack on TAVR Media, and the cyberattack on Channel 24 right after the invasion started.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Dan Guido, CEO of Trail of Bits, about AI. Dan thinks AI technologies will be a "game changer." But he also thinks the conversation around AI is not very sophisticated just yet.
Cybercrime and threat intel
SIM swapper sentenced: A US judge has sentenced a prodigious SIM swapper to three years in prison for hacking and stealing more than $20 million from cryptocurrency owners. The DOJ says 26-year-old Anthony Francis Faulk was part of a hacking trio that robbed more than a dozen individuals between 2016 and 2018. The trio operated by tricking cellphone operators into transferring a victim's phone number to a SIM under their control. Faulk and his co-conspirators would then reset passwords for email and cryptocurrency trading accounts and empty wallets before the victim could notice the SIM swap.
npm malware: ReversingLabs has a report on a dozen malicious packages targeting Roblox API users that install a version of the LunaGrabber infostealer on their systems.
Neo_Net campaign: Cyberint researchers have published more details on the smishing operations of a Mexico-based threat actor named Neo_Net.
Malware technical reports
XLoader: SentinelOne takes a look at the updated macOS version of XLoader, a known MaaS infostealer.
RedGoBot: QiAnXin has published an update on RedGoBot, a new IoT malware strain that was spotted earlier this year.
REM Phishing RAT: ThreatMon has a report on REM Phishing RAT, a new remote access trojan being used in attacks.
Sponsor Section
Trail of Bits co-founder and CEO Dan Guido was asked to provide feedback on the effects of AI on modern technology at a meeting of the Commodity Futures Trading Commission's Technology Advisory Committee (TAC) on July 18. His comments are summarized in the company's blog here and are available in full in the video below.
APTs and cyber-espionage
Russia's NATO info-op: Graphika researchers have published a report detailing the online influence operations that took place around the recent NATO Summit in Vilnius, Lithuania. Graphika linked the efforts to two groups it tracks as Doppelganger and Secondary Infektion. The organization says the two groups didn't collaborate but appeared to have the same objectives.
"Despite this persistence, the operations appear to have had a limited impact on the online conversation about the Vilnius summit. Their content received minimal shares from authentic users, and what online traction they did generate was largely in existing pro-Kremlin communities. Graphika also observed social media users, including influential pro-Kremlin figures, calling out the activity as fake, suggesting the actors often failed in their efforts to deceive online audiences."
Carderbee APT: A new Chinese APT group named Carderbee has conducted a supply chain attack that deployed backdoors to computers running a Chinese security app named Cobra DocGuard. The incident took place in April and involved malware named KorPlug or PlugX, known to be the go-to tool of many Chinese state-sponsored espionage groups. Symantec says the attack was highly targeted, and the backdoor was only deployed on roughly 100 of DocGuard's 2,000 total customers, with most of the infected computers being located in Hong Kong. The same DocGuard app was also used to push malware to selected victims in two other supply chain incidents in 2021 and 2022 as well. ESET attributed the two incidents to a different Chinese APT known as Budworm, or APT27.
GroundPeony (UNC3347): NaoSec has published a report on a new Chinese APT group they've named GroundPeony. The report covers the group's attacks against Taiwanese government organizations.
Vulnerabilities, security research, and bug bounty
New Ivanti zero-day: American software maker Ivanti released a security update on Monday to fix an actively exploited zero-day in its Ivanti (formerly MobileIron) Sentry secure mobile gateway product. The zero-day (CVE-2023-38035) is an authentication bypass for the Sentry API that allows threat actors to access the secure gateway's administration section. Ivanti says the vulnerability has been used against "a limited number of customers." The company is urging customers that exposed port 8443 of their Sentry mobile gateways on the internet to apply the security update.
Researcher dumps macOS zero-day: Security researcher Jeff Johnson has published details about a macOS vulnerability after Apple failed to address the issue for more than ten months. The vulnerability resides in App Management, a new feature that Apple added to macOS Ventura last year that protects notarized apps from unauthorized modifications. Johnson says this feature can be bypassed by using other notarized apps to modify the settings of other apps. For example, apps like Terminal and TextEdit can be used to modify browser settings without App Management triggering a warning.
"In retrospect, I regret participating in the Apple Security Bounty program. It has been a giant, frustrating waste of time, and I wish I had just dropped this 0day on October 24 of last year when Ventura was released. I suspect that if I had done so, Apple would have found a way to address the issue already in Ventura. Thus, I feel that my prolonged silence has not protected Mac users. The standard practice in reporting a security vulnerability is to give the vendor 90 days to address the issue, and I've given Apple vastly more time than expected."
IBM Facsimile Support vulnerability: Security researchers from Silent Signal have published details on CVE-2023-30988, a vulnerability in IBM Facsimile Support.
Valimail vulnerability: Email security company Proofpoint has helped patch a vulnerability in Valimail's SPF macro solution.
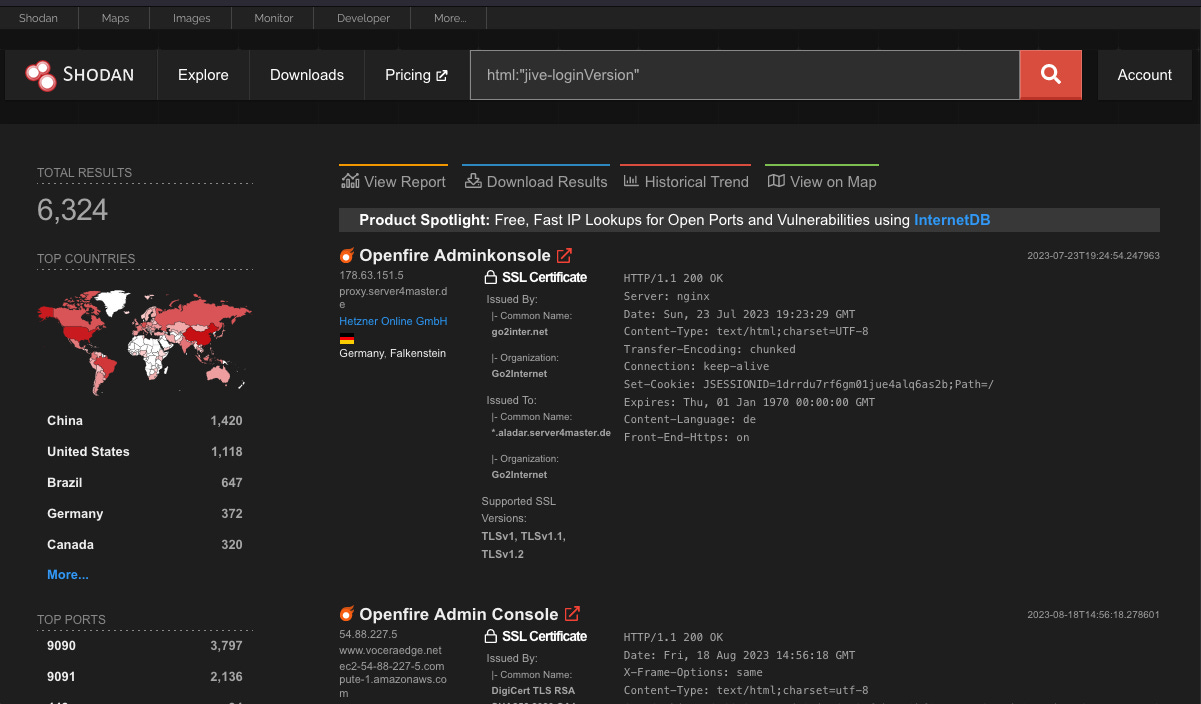
Openfire exploitation: VulnCheck and Surevine researchers say a vulnerability in Openfire RTC instant messaging servers is being exploited in the wild. Tracked as CVE-2023-32315, the vulnerability is an authentication bypass in the server's web administration panel. Attacks have been going on since at least June 9 this year, with some intrusion being linked to a "well-known botnet." More than 6,300 Openfire instances are currently reachable online, and server admins are advised to install available patches. Making matters worse, VulnCheck says it found a way to exploit the same vulnerability to compromise Openfire servers without leaving traces in logs, needing to create admin panel users, or triggering plugin installation notifications.
Infosec industry
SentinelOne sale: Cybersecurity firm SentinelOne is exploring a possible sale after its shares lost 80% of their value in the last two years. The company has a market value of about $5 billion. [Additional coverage in Reuters]
404 Media: Four reporters from Vice's old Motherboard section have started their own tech news outlet named 404 Media.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the history of CCTV hacking and what different groups get out of these hacks.




