Risky Biz News: SEC charges SolarWinds and its CISO
In other news: Russia is developing its own VirusTotal clone; Magniber ransomware gang members detained in South Korea; and Atlassian warns of data wiping bug.
This newsletter is brought to you by vulnerability management and analysis platform Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US Securities and Exchange Commission has filed fraud charges against software company SolarWinds and its chief information security officer, Timothy Brown.
The agency says it reviewed internal communications and security assessments and found that SolarWinds lied about its cybersecurity posture to investors for years before it was hacked in 2020.
The SEC says that for at least two years before the hack, the company—through its CISO—had learned and discussed its cybersecurity deficiencies but misrepresented the risks to investors.
Gurbir S. Grewal, the Director of the SEC's Division of Enforcement, says SolarWinds and Brown ignored "repeated red flags" and mentioned "only generic and hypothetical risks" in its public documents.
The SEC's lawsuit [PDF] comes with tens of pages listing a long list of SolarWinds cybersecurity and risk assessment deficiencies that paint an extremely grim picture of the company's internal culture.
- Failure to consistently maintain a secure development lifecycle (SDL) for its software
- Failure to enforce the use of strong passwords on all systems
- Failure to remedy access control problems that persisted for years
- Failure to fix vulnerabilities in its software in time
- Understaffing of its cybersecurity roles

The SEC lawsuit points the finger at Brown for the company's cybersecurity issues. It also reveals that Brown lied to cybersecurity firms investigating the hack. This may not be a crime, but it obviously helped the SEC understand how SolarWinds was treating its cybersecurity obligations.

The company's hack eventually came to light in December 2020 after Mandiant's and Microsoft's security teams discovered suspicious activity coming from their SolarWinds Orion servers.
The two companies started investigations and discovered that hackers linked to Russia's SVR intelligence agency—known as the APT29 group—broke into SolarWinds network in early 2019 and inserted malware into the company's Orion software. Through the Orion software update mechanism, the malware made its way to more than 18,000 corporate and government networks across the world, including several US federal agencies.
The SEC is not suing SolarWinds for bad security practices—otherwise, many companies and their CISOs would be already fined into the ground—but for lying to its investors.
The agency says investors lost money after SolarWinds' share price dropped by 25% when it disclosed its hack—a financial risk none were aware of at the time because SolarWinds never shared a real picture of its cybersecurity issues.
This week's charges are not a surprise since the SEC notified SolarWinds about its intention to bring charges on two separate occasions, in November 2022 and June 2023. The surprise came from the content of the SEC's complaint, which may spur a new wave of lawsuits against the company.
In the SEC's press release, Grewal says the lawsuit should be interpreted as a "strong message" to other companies to get serious about their cybersecurity practices.
The agency is seeking relief and disgorgement from SolarWinds and a bar for Brown from serving as an officer or director in other companies.
In cybersecurity circles, the case is expected to have an impact, but not the one the SEC is expecting. Because the SEC case revolves around many of SolarWinds' internal documents and chats, security experts expect to see companies record cybersecurity issues far less and only when they have to.
We've seen this in ransomware-related incidents already. Following a string of class-action lawsuits, legal teams hired to advise ransomed companies are now telling victimized orgs to not produce incident response or similar cybersecurity reports. Any such reports are to be delivered in spoken form and kept off any electronic or paper documents as much as possible since they can be subpoenaed in future lawsuits and may reveal the company to be at fault.
Having your internal security audits, emails, and Slack chats appear in an SEC lawsuit is a good reason not to have them lying around—unless some regulations and contracts specifically require a security audit to be carried out once in a blue moon.
Brown's inclusion in the SEC lawsuit is also having an impact across the CISO/CSO space, raising the same issues we've heard before about having the right person in the role and that security compliance does not mean security—both good points that have been made before. Unfortunately, these opinions and the SEC lawsuit miss one important detail, namely, if Brown had any significant power or sway inside SolarWinds' board. He probably did not.
SolarWinds CFO Barton Kalsu, who was targeted in one of the Wells notices, was not charged this week.
Breaches, hacks, and security incidents
MOVEit victim count passes 2.5K: The number of companies impacted by Clop's MOVEit hacking spree has formally surpassed 2,500, according to security firm Emsisoft. The latest organizations to be added to this list are Avast's CCleaner app and the US Justice and Defense departments. The US DOJ and DoD incidents are not as bad as they look, though, as officials say the hackers only gained access to the email addresses of 632,000 US federal employees and nothing more.
Major ransomware incident in Germany: A suspected ransomware attack on a German IT company has crippled local government systems across western Germany. According to German officials, the attack hit a company named Südwestfalen IT. The number of affected municipalities is unknown, but most are small towns located in Germany's North Rhine-Westphalia region. [Additional coverage in BILD]
NSPK hack: A hacking group named DumpForums claims to have breached the Russian National Payment Card System, a division of Russia's Central Bank and the operator of MIR payment cards. The group claims it gained access to customers' personal data and the NSPK's internal projects. The organization denied any hack and said that only its website was impacted. The DumpForums group has a history of targeting Russian organizations and dumping their data. [Additional coverage in RBC]
British Library incident: A cyber-attack has knocked out the IT network of the British Library for almost five days. The incident has impacted book orders and manual collections.
General tech and privacy
Microsoft cracks down on Xbox cheating: Microsoft will start blocking unauthorized Xbox controllers and accessories starting on November 12, 2023. The block will impact every Xbox owner who uses a third-party controller that did not obtain a Microsoft license for its product. The move will also have a huge impact on the game cheating scene and will likely spell the end for cheating devices such as XIM and Cronus Zen. [Additional coverage in Xfire]
Meta introduces paid tier in the EU: Social media company Meta is introducing a paid subscription for European users that will remove ads from its Facebook and Instagram services. The tier will cost €9.99/month on the web or €12.99/month for mobile users. Meta says it is introducing the new tier in response to the EU's GDPR regulation. The company says that by making users choose between the free and paid subscription, users are effectively making a conscious choice to have their personal information used for ad targeting.
Samsung Auto Blocker: Samsung has launched a new security feature for its latest line of smartphones. Named Auto Blocker, the feature prevents users from installing apps downloaded from outside the Samsung Galaxy and Google Play stores. The new feature can also block app side-loading operations from both the user interface and via automated commands sent via a USB debugging port. The feature is available for all Samsung phones running the One UI 6 home screen software.
Government, politics, and policy
Spyware alerts in India: Apple has notified over a half dozen lawmakers from India's main opposition parties that their iPhones have been targeted by state-sponsored attacks. Victims included figures from India's main opposition parties, such as the National Congress, AIMIM, the AAP, and the Communist Party. The alleged hacking attempts took place weeks before Indians are set to elect members to its new Parliament. In a press conference, Rahul Gandhi, leader of the National Congress Party and Modi's main rival for the upcoming elections, accused the Indian government of the attempted hacks. Besides politicians, two Indian journalists and a member of an NGO also received notifications from Apple. [Additional coverage in TechCrunch]
Russia is developing a multiscanner: Russia's Minister of Digital Development says it is working on developing a multi-scanner solution for Russia's internal market. The project is named the "National Multiscanner," is modeled after Google's VirusTotal service, and is expected to enter testing this year. Officials say the service will operate at full capacity in 2025. [Additional coverage in the Rossiyskaya Gazeta]
Canada bans WeChat/Kaspersky: The Canadian government has banned the use of WeChat and Kaspersky applications on government-issued mobile devices. Officials say the apps present an "unacceptable level of risk to privacy and security" for government workers. Canadian officials stopped short of calling the apps espionage tools. The ban has entered into effect this week on October 30.
CRI pledge: Officials from 48 countries attending the third edition of the International Counter Ransomware Initiative (CRI) are expected to sign a pledge to not pay ransoms demanded by ransomware gangs. This year's meeting is focused on improving information-sharing mechanisms surrounding ransomware attacks. To help get things moving, a White House official says the CRI plans to publish a list of cryptocurrency wallets associated with ransomware operations that can be tracked and blacklisted across member states. [Additional coverage in CyberScoop]
US Facial Recognition Act: House Democrats have introduced a bill named the Facial Recognition Act that would require law enforcement agencies to obtain a warrant before using facial recognition technology to identify a suspect.
WH AI EO: The Biden Administration signed an executive order that sets a national strategy and introduces new rules and standards for the development of artificial intelligence (AI) technologies. The executive order covers a lot of areas:
- Companies developing AI models that have national security, economic, or health risks will have to notify the US government of their efforts and safety tests.
- The executive order calls on Congress to pass legislation to protect Americans' privacy from AI technologies and laws to prevent AI from being used to discriminate against certain groups.
- Orders NIST to develop AI safety standards.
- Orders the DHS to investigate potential (ab)uses of AI and protect US critical systems from those threats (such as AI used for weapons of mass destruction, IP theft, cybersecurity, etc.).
- Orders the DHS to use AI tooling in its daily operations, such as threat detection, prevention, and vulnerability assessments.
- Orders AI-generated content to be labeled appropriately.
Besides the US, the G7 group also agreed on a Code of Conduct for AI companies, while the European Union is still working on AI legislation.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on the rise and evolution of vulnerability threat intel and how CISA KEV's new ransomware section will be a game changer.
Cybercrime and threat intel
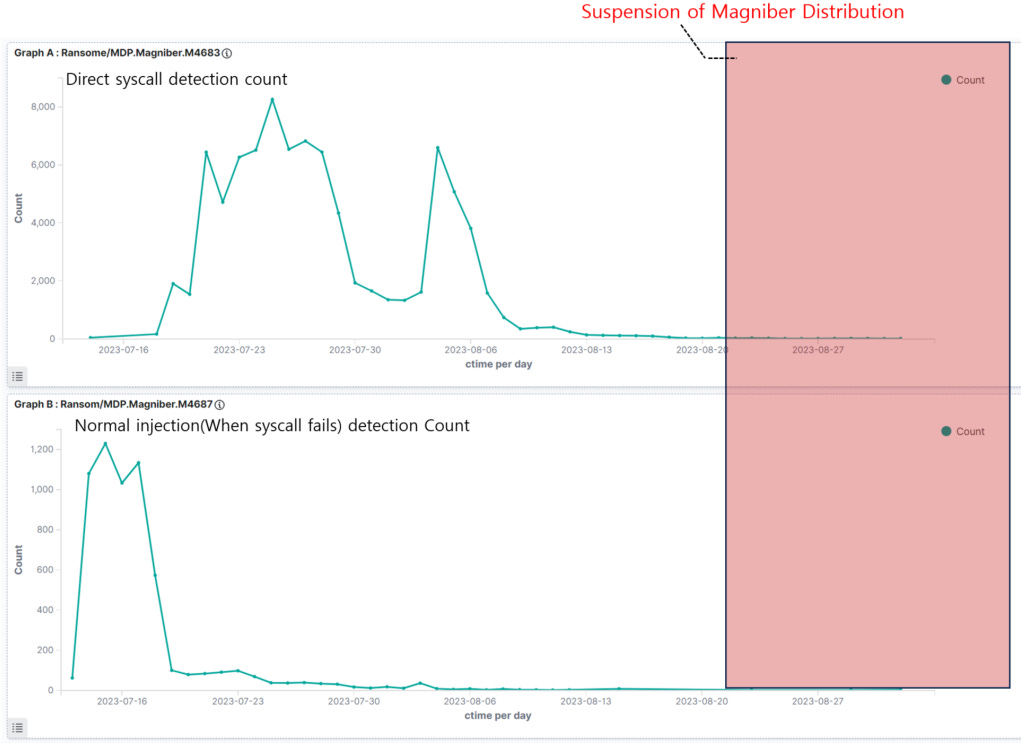
Magniber members detained: South Korean authorities have detained five employees of a data recovery company on suspicion of working with North Korean hackers. Officials say the company collected more than 3.4 billion won ($2.5 million) in data recovery services from 778 companies hit by ransomware. South Korean police say the company conspired with North Korean hackers via email and Telegram and received a manual on how to recover encrypted systems. The company used targeted search keyword ads to advertise its services to impacted companies. While officials have not named the ransomware, several sources have told RiskyBusinessNews that the company was working with the Magniber gang, a ransomware strain that only targeted South Korean companies. According to South Korean security firm AhnLab, the Magniber crew has been inactive since August 25, representing the longest period of inactivity for the group since its launch in 2016. [Additional coverage in Chosun]
SIM swapper sentenced: A US judge has sentenced a 20-year-old Florida man to 30 months in prison for stealing almost $1 million from online cryptocurrency accounts using SIM swapping attacks.
Facebook malvertising: Bitdefender looks at a Facebook malvertising campaign deploying the NodeStealer malware.
DSA malvertising: Malwarebytes has discovered a novel malvertising campaign that abuses a Google feature named Dynamic Search Ads. Threat actors are abusing the feature for the bulk creation of malicious ads that automatically pull text from the pages they want to lure users to.
NuGet malware: ReversingLabs researchers have found a new wave of malicious packages uploaded on the NuGet portal. Researchers say the new packages appear to be connected to the campaign spotted by Phylum early last month. ReversingLabs believes the campaign has been going on since at least August this year and involved several hundred malicious packages.
Caffeine PhaaS: Cofense looks at the recent infrastructure used by the Caffeine Phishing-as-a-Service.
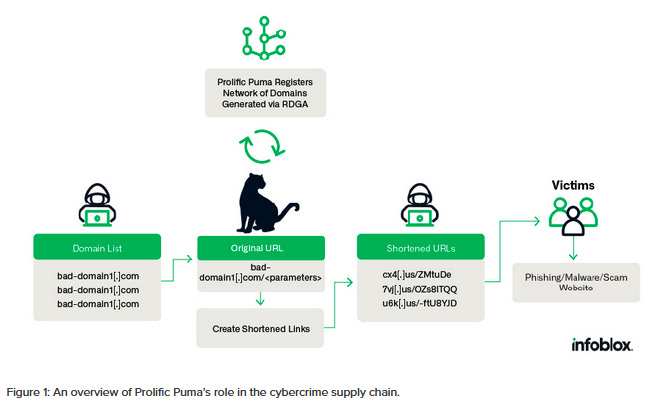
Prolific Puma: A new threat actor named Prolific Puma is running an on-demand URL-shortening service for malware gangs as part of a novel Cybercrime-as-a-Service offering. The primary purpose of the service is to provide shortened URLs that get blacklisted by security firms instead of a customer's actual infrastructure. Discovered by Infoblox, the service has been operating since at least January 2020 and has been primarily used in smishing operations.
Malware technical reports
EleKtra-Leak: A threat actor named EleKtra-Leak has been spotted scanning GitHub repositories for accidentally leaked AWS IAM tokens in order to gain access to AWS infrastructure and perform crypto-mining operations. Palo Alto Networks says this is one of the oldest crypto-mining operations known to date, going as far back as December 2020.
FakeUpdateRU: Sucuri researchers have looked at a malware distribution campaign named FakeUpdateRU that used compromised websites to distribute a fake update for the Chrome browser that infected user systems with RATs.
IcedID: Proofpoint looks at recent TA471 campaigns distributing a forked version of the IcedID malware. The two campaigns were extremely small and ran for only a week but contained a new IcedID version that Proofpoint described as "unique."
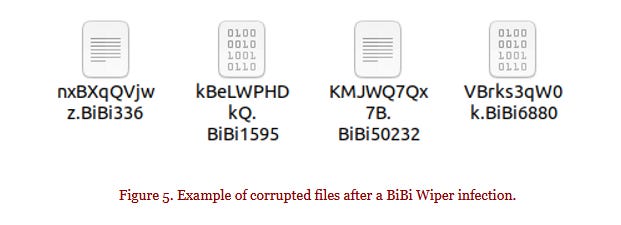
BiBi-Linux wiper: A pro-Hamas hacktivist group is deploying a new Linux data wiper in attacks targeting Israeli organizations. The wiper works by overwriting almost all of a local system's files with random data. The malware has been named BiBi-Linux because it renames all destroyed files with a file extension that begins with BiBi, the nickname of Israel's prime minister, Benjamin Netanyahu.
Sponsor Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
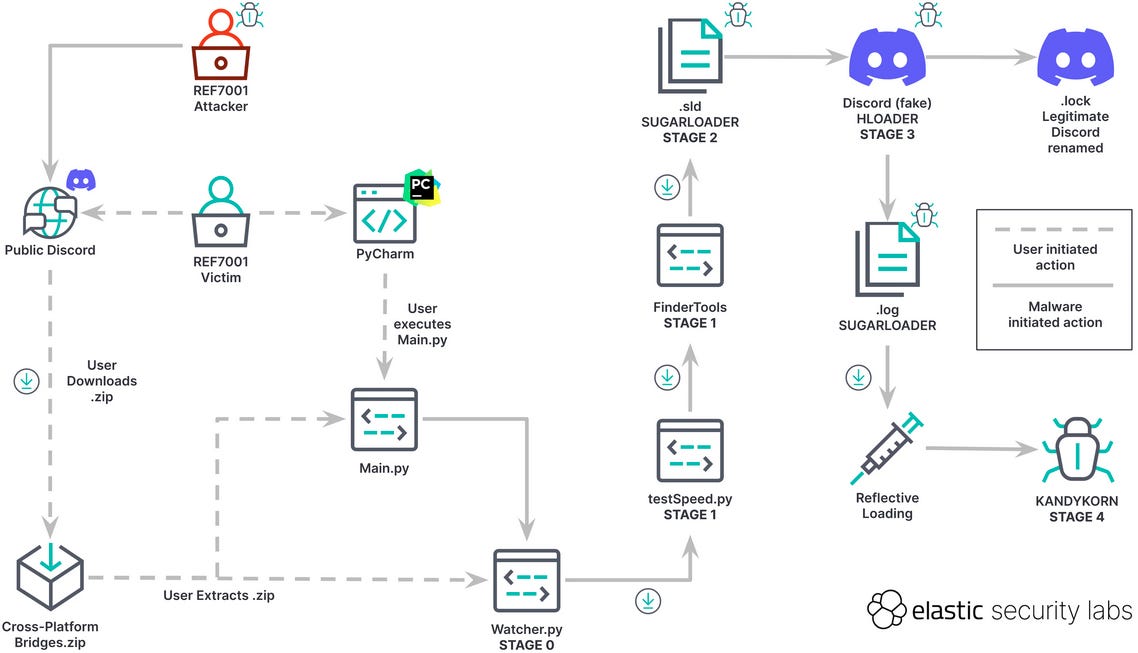
Lazarus KANDYKORN: Elastic's security team has published a breakdown of KANDYKORN, a macOS malware strain used by North Korean hacking group Lazarus in attacks targeting blockchain engineers working for a cryptocurrency exchange platform.
"Attackers impersonated blockchain engineering community members on a public Discord frequented by members of this community. The attacker social-engineered their initial victim, convincing them to download and decompress a ZIP archive containing malicious code. The victim believed they were installing an arbitrage bot, a software tool capable of profiting from cryptocurrency rate differences between platforms."
Pensive Ursa: PAN's Unit42 looks at a new version of Kazuar, a malware typically used by the Pensive Ursa (aka Turla, Uroburos) APT.
"The Ukrainian CERT reported in July 2023 that this version of Kazuar was targeting the Ukrainian defense sector. The threat group behind this variant was going after sensitive assets such as those found in Signal messages, source control and cloud platforms data."
Blind Eagle: Qihoo 360 looks at another wave of Blind Eagle (APT-C-36) operations. The report covers the Latin American APT trying to use the Amadey malware for recent operations.
AridViper: Palestinian APT group AridViper has been seen disguising spyware inside updates to non-malicious Android applications. Published by Cisco Talos, the report covers campaigns that predate the recent Hamas-Israeli conflict, as the vendor was "performing the due diligence with law enforcement."
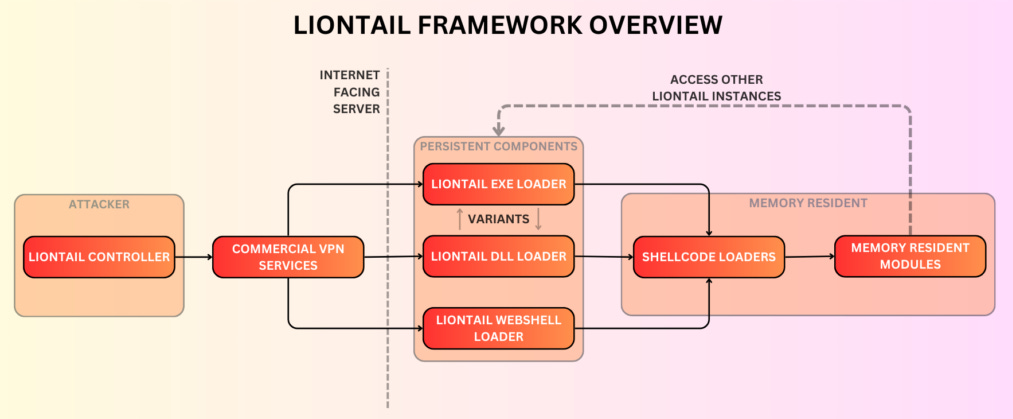
Scarred Manticore: Check Point has a report on Scarred Manticore, an Iranian cyber threat group linked to MOIS (Ministry of Intelligence & Security). The report covers campaigns targeting government, military, telecom, IT, finance, and NGOs in the Middle East. The report also focuses on LIONTAIL, the group's latest malware framework. The group is linked to the Iranian actor DEV-0861 and, to some degree to, OilRig.
"Scarred Manticore's playbook has evolved from basic web shell attacks on Windows Servers to an advanced framework with diverse and powerful toolset that utilizes both custom-written and open-source components. A clear sign of Iran's cyber game leveling up."
Vulnerabilities, security research, and bug bounty
New Atlassian bug: Software company Atlassian has released a security update for a vulnerability (CVE-2023-22518) in Confluence servers that can be used to wipe customer systems. The patch notes include a rare message from the company's chief information security officers, a sight you don't usually see in software updates. Atlassian CISO Bala Sathiamurthy urged companies to "take immediate action" and install the software update to avoid data loss scenarios. Sathiamurthy says the vulnerability is extremely dangerous because it can be exploited remotely by unauthenticated attackers. Atlassian says that all versions of Confluence Data Center and Server are affected but that no attacks have been observed in the wild so far—although the bug's data-wiping capabilities will most likely entice some threat actors.
Cisco IOS XE PoC: Security firm Horizon3 has published fully working PoCs for the recent Cisco IOS XE zero-days tracked as CVE-2023-20273 and CVE-2023-20198. According to Censys, around 29K Cisco systems remain infected with backdoors after a threat actor exploited these zero-days last month.
F5 BIG-IP PoC: Quite a few proof-of-concept exploits have been posted online for the latest F5 BIG-IP vulnerability tracked as CVE-2023-46747. F5 confirmed active exploitation shortly after they went live.
Wyze PoC drama: Security researcher Peter Geissler has published a proof-of-concept exploit for Wyze IP cameras. Geissler says he published the exploit because Wyze released security updates for the Wyze Cam v3 model days before the Pwn2Own 2023 Toronto hacking contest, where he was scheduled to use the exploit. Geissler claims Wyze did it on purpose and only patched the camera model used in the contest and did not release patches for other models. The Wyze Cam v3 was hacked by four other researchers, regardless.
Infosec industry
ATT&CK v14: MITRE has released v14 of the ATT&CK framework. This new update comes with updates to the Enterprise and Mobile, Assets in ICS, and Mobile Structured Detections sections.
Acquisition news: Palo Alto Networks says it plans to acquire cloud security provider Dig Security.
New tool—Cascade: Academics from ETH Zurich have released Cascade, a RISC-V CPU fuzzer.
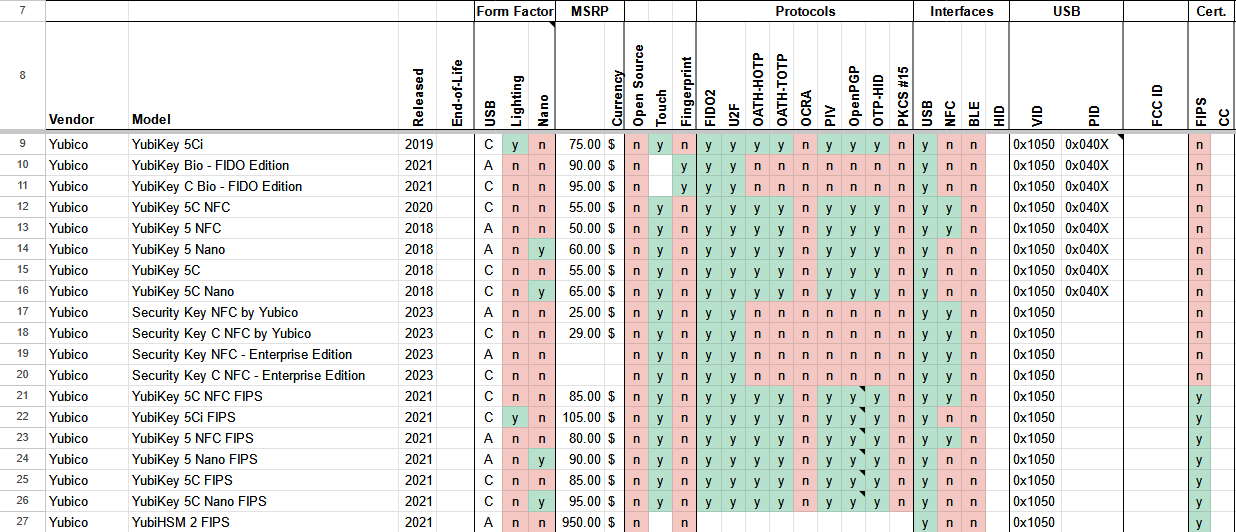
New tool—USB security tokens: Software developer Steffen Vogel has put together a spreadsheet comparing all the major USB security tokens.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss what is really at stake when it comes to cyber security.




